So, you’ve securely deployed tens of thousands of smartphones and tablets to your employees. Congratulations! Now how would you like to take things a step further? Protecting mobile devices is just table stakes in 2016. Employees want more than just basic messaging apps and email, while your boss is pressing you on how to maximize the return on your mobile investment.
So, you’ve securely deployed tens of thousands of smartphones and tablets to your employees. Congratulations! Now how would you like to take things a step further? Protecting mobile devices is just table stakes in 2016. Employees want more than just basic messaging apps and email, while your boss is pressing you on how to maximize the return on your mobile investment.
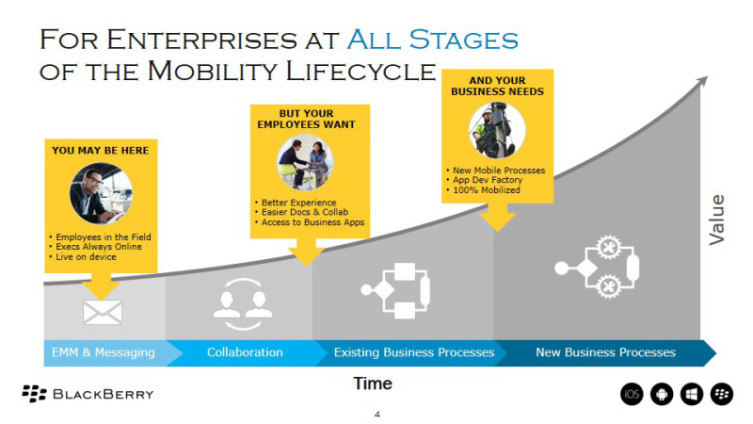
You won’t be able to reach either of these goals overnight. Instead, it’ll be more of a gradual evolution – one that’s best visualized through something known as the Mobile Maturity Curve, outlined below. Understanding it will help you gear up for your own mobile journey, and move from the early stages of mobile adoption to full business process mobilization.
Stage One: Basic Mobility (MDM, Email, & Messaging)
The first investments an organization typically makes into mobility are mobile device management (MDM) and email. At this point, most enterprises understand that mobility is critical to their business objectives, but they aren’t sure how to tap into it – they lack the tools and expertise to do so.
Moving past basic mobility requires that you:
- Implement an enterprise mobility management (EMM) solution that lets you secure and control both devices and content.
- Begin researching mobile security best practices and developing in-house mobile expertise.
- Acquire knowledge of how mobile devices are used within your business.
- Build on that knowledge to think about how mobile devices could be used – how might departments collaborate more effectively through mobility?
Stage Two: Mobile Collaboration
Once your users have gotten a taste of mobile email and messaging, they’ll naturally want to start doing more with their phones. They’ll demand business applications that help them work and collaborate more efficiently. Should you fail to deliver what they require, they’ll seek their own solutions.
The biggest threat at this stage is data leakage, as employees share sensitive files through both first- and third-party apps (often carelessly). User privacy is also an issue, with personal devices being used more and more frequently in the workplace.
There are three key challenges here:
- Ensuring the applications your employees rely on will work with their mobile devices.
- Implementing a document control solution that allows you to protect sensitive files against mishandling.
- Looking beyond company-wide collaboration to think about how mobility slots into key business processes – for example, a sales department’s CRM platform or a hospital’s communications system.
Stage Three: Mobilization of Existing Business Processes
In stage three, you’ve moved beyond simple collaboration, and there’s a push for mobile apps and initiatives to improve the operations of specific departments. IT, meanwhile, has begun identifying efficiency bottlenecks that could be solved with mobile apps. You may also be looking into internal application development.
The hurdles you’ll face in stage three include:
- Storing, managing and securing the new forms of data that emerge as a result of mobilization.
- Protecting business-critical files and data from criminals and unscrupulous competitors by ensuring mobile employees have a secure means of accessing corporate systems/records.
- Incorporating mobile applications into existing infrastructure.
- Ensuring your mobility initiatives keep with both security regulations and your own security baselines.
 Stage Four: Creation of New Business Processes
Stage Four: Creation of New Business Processes
By now, you’re re-engineering your business around mobility. New revenue streams have begun to emerge, and you’re constantly seeking ways to further improve existing business processes, lowering costs, improving efficiency, and heightening customer satisfaction. An example of this in practice can be seen with Canadian insurance firm Northbridge Financial, which equips its claims professionals with the Encircle platform to better enable them in the field.
Mobility at this stage is pervasive. Mobile devices have become so widespread that managing them individually is inefficient, and your business is flooded by hundreds of different applications – including custom, internal apps. Corporate data, meanwhile, is everywhere.
To ensure you enjoy all the benefits of mobile maturity, there are a few goals you must accomplish:
- Set up a platform that enables your business to quickly and securely build and deploy any apps it requires without having to reinvent the wheel.
- Implement file-centric digital rights management (DRM) that gives you complete control over sensitive documents.
- Shift from device-centric to user-centric authentication through an identity and access management solution, with single sign-on authentication for mobile apps.
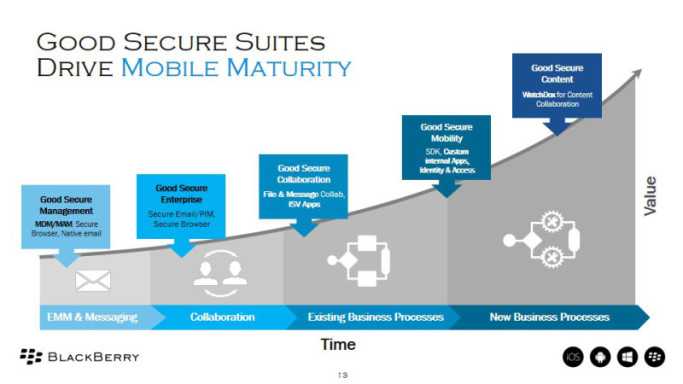
A Solution for Every Stage: BlackBerry/Good’s Secure EMM Suites
With BlackBerry’s acquisition of Good Technology, we’ve developed Good Secure EMM Suites, the most complete EMM solution on the market. By combining Good’s leading productivity apps and robust security platform with BlackBerry’s enterprise-level mobile security, Suites empowers organizations with the ability to optimize worker productivity while protecting both corporate and private data. Through a tiered subscription model, it offers a solution for businesses at every phase of the mobile maturity curve:
 Good Secure Management Suite: For businesses entering stage one, our Secure Management Suite combines the EMM capabilities of BES12 with the Good Access Secure Browser.
Good Secure Management Suite: For businesses entering stage one, our Secure Management Suite combines the EMM capabilities of BES12 with the Good Access Secure Browser.- Good Secure Enterprise Suite: The Secure Enterprise Suite adds Good Work email/personal information management to the Secure Management Suite, providing employees with enterprise-class secure productivity.
- Good Secure Collaboration Suite: For organizations that are just beginning to mobilize existing business processes, the Secure Collaboration Suite builds upon the Enterprise suite with Good Docs file access, native Microsoft Office editing, Good Connect enterprise IM and deployment of ISV apps. Good apps work together so Good Work can access documents seamlessly and initiate IM sessions based on a co-worker’s presence status.
- Good Secure Mobility Suite: The Secure Mobility Suite adds developer tools and unlimited deployments of custom-built apps to the Secure Collaboration Suite, allowing internal developers to leverage Good’s development tools to add security, mobility and platform features to custom apps. These apps are then easily deployed to end users alongside Good and ISV partner apps.
- Good Secure Content Suite: Our top-tier offering, the Secure Content Suite, provides everything in the Secure Mobility Suite plus a fully functional Enterprise File Sharing and Synchronization (EFSS) system with complete digital rights management for file-level security policies.
To learn more about what Good Secure Suites can do for your enterprise, you can view an archived version of our webinar Introducing Good Secure EMM Suites. You can also read The CIO’s Guide to Enterprise Mobility, check out the official Suites product page, or view a demo of Suites in Hands-on with Good Secure EMM Suites.
Finally, if you’re interested in learning about the current EMM landscape, sign up for our upcoming webinar, Making Sense of the EMM Alphabet Soup – a detailed look at MDM, MAM & MCM on Tuesday, April 19, 2016 at 11:00 AM EDT.