Threat groups vastly increased the scope and sophistication of their attacks in 2021. They claimed a string of high-profile successes, hitting critical infrastructure systems and targets in the private sector particularly hard. High-profile breaches like HAFNIUM Group’s exploitation of the Microsoft® Exchange Server and the supply chain attacks on Kaseya and SolarWinds made headlines. Meanwhile, the rampant growth of ransomware continued unabated, even as the U.S. Department of Justice established a Ransomware and Digital Extortion Task Force.
Misuse of Cobalt Strike
In 2021, BlackBerry collected insights and trends from over 7,000 Cobalt Strike Team Servers and 60,000 Beacons. The resulting threat intelligence is in the BlackBerry® 2022 Threat Report and further detailed in our eBook Finding Beacons in the Dark: A Guide to Cyber Threat Intelligence.
Recent discoveries include:
- Threat actors are increasingly turning to legitimate cloud providers for Cobalt Strike hosting
- Ports 80, 443, and 8080 are typically open in most environments, making them an obvious choice for command-and-control (C2) traffic
- Cobalt Strike Beacons were used in 2021 to execute C2 injection attacks through domain fronting, DNS redirectors, process spawning, malleable profile masking, and leaked public keys
Surging Supply Chain Attacks
Threat actors focused on supply chains in 2021 and met with considerable success. The supply chain is an appealing target for threat groups for several reasons, including:
- Supply chains are complex and expansive, making them difficult to secure effectively
- A successful supply chain attack can severely impact multiple targets at once
- Many organizations still implicitly trust their supply chain, allowing these attacks to bypass cybersecurity measures
- A lack of supply chain visibility represents a significant challenge for threat monitoring and forensics
Advanced persistent threat (APT) groups claimed responsibility for 50% of recent supply chain attacks. Their success rate may indicate more of these attacks on the horizon.
Log4j/Log4Shell Exploits
Log4j is an open-source logging package used by countless frameworks and applications. Last year, it was discovered to contain a crippling vulnerability. The vulnerability can be exploited by feeding susceptible applications a specially crafted text snippet, which may allow attackers to perform remote code execution.
Log4Shell is troubling for several reasons:
- Shortly after being revealed, attacks targeting the vulnerability numbered several million per hour
- It’s difficult to tell which applications or services are at risk
- The exploit does not leverage malicious software and is undetectable by many security tools
- The widespread use of Log4j means the vulnerability could be a problem for years to come
Exotic and Obscure Programming Languages
Threat actors often use obscure languages to develop, rewrite, or create a wrapper or loader for malware families. This technique was used heavily over the past year for several reasons:
- Enhancing performance
- Bypassing security tools
- Thwarting signature-based antivirus detection
- Cross-compiling to target multiple operating systems
BlackBerry has observed threat actors recently adopting Go, D, Nim, and Rust in their attacks.
Initial Access Brokers (IABs)
The BlackBerry Research and Intelligence team identified a previously undocumented IAB dubbed Zebra2104. IABs gain unlawful access into an organization’s network, then sell the access on the dark web. Through comprehensive investigation, we discovered links between Zebra2104 and MountLocker, Phobos, and StrongPity aka Promethium.
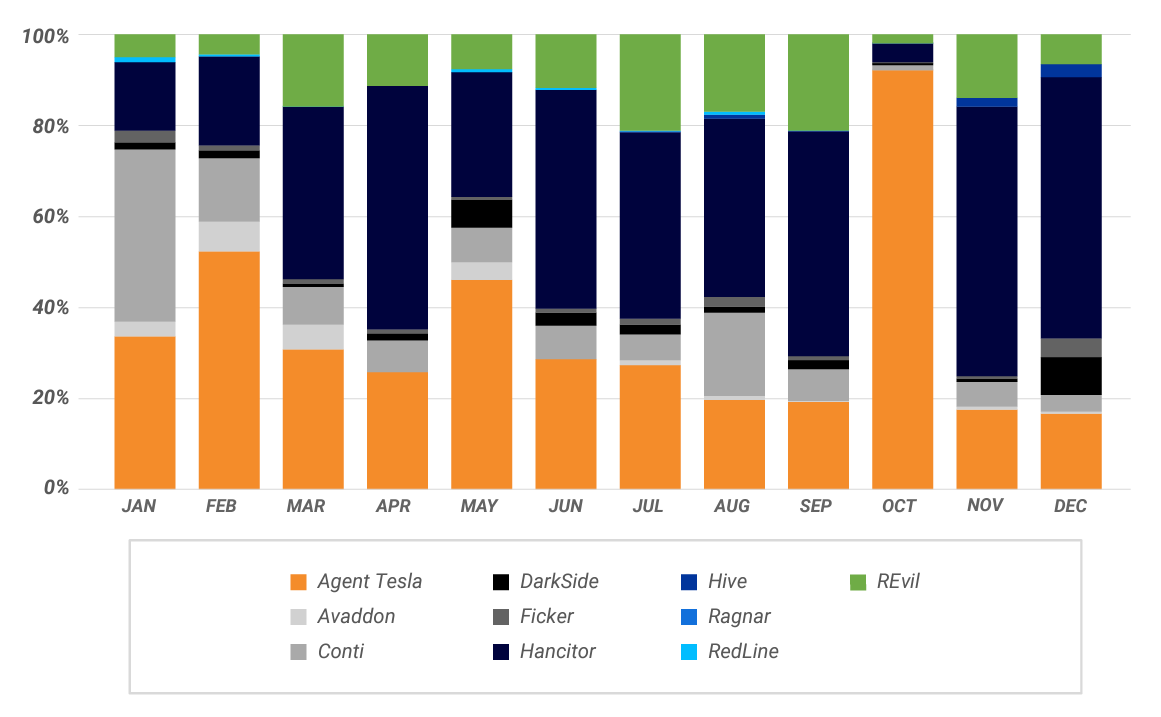
Major Attack Types in 2021
Ransomware
Ransomware-as-a-service (RaaS) providers have been behind some of the highest-profile cyberattacks of 2021. Several groups were shut down after the Colonial Pipeline attack, yet others have risen to take their place. Modern ransomware is often provisioned to clients as a service and may use a double extortion scheme by exfiltrating encrypted data and threatening its release.
The most common ransomware strains in 2021 included:
- REvil (aka Sodin or Sodinokibi)
- Conti
- DarkSide (Defunct)
- Avaddon
- Ragnar Locker
- Hive
Infostealers
Infostealers vary in terms of the information they collect, which may include web data, authentication details, credit card information, crypto wallets, and FTP data. The most prominent infostealers of 2021 were:
- RedLine
- Agent Tesla
- Ficker
- Hancitor (aka Chanitor)