Botnets, Zero-Day Exploits, Phishing Emails, Waterholes, Honeydrops, Trojan RAT's, Dropper/Downloaders, Proxy Backdoors, TORnet, FakeAV, Worms, Viruses... Which of these are "APT"?
What about Organized Crime, Catalog Operators, Malware As a Service Providers, Foreign (and Domestic) Governments, and Industry Competitors?
The short answer - all of the above. The more specific answer is the latter. Advanced Persistent Threats are referred to by the tools used in many instances, but they are more accurately described as the activities conducted by interested parties - whether third parties for hire (like OC, Operators, or Service Providers), or first parties like Government or Industry Competitors.
The reason that APT often refers to the tools used is that they provide indicators that can alert organizations to the related activities. Later stage APT activities as performed by first parties who have actual purpose for breached environments and data (competitive market or operational purposes) don't rely upon the same types of "malware" as earlier third party access creators/monitors, though sometimes trojan backdoors or proxies may continue to facilitate administrative accesses to ensure a "quality of service". Earlier stage APT activities involve more creative malware, to gain a foothold in the environment (exploits and dropper/downloaders) and to manipulate or bypass the defensive or management controls (RAT backdoors/proxies), in order to develop platform access (botnets).
The third parties are a growing and organizing into service economies in the Internet domain - as obviated by the Carder forums, Malvertisers, Spammers, Phishers, and etc. Advertising revenues are being attached to the forums, and currency created (Bitcoins, WMZ etc.) to service the unique security needs of those operators. Service providers even offer terms of service including quality and conditional use.
Attribution becomes increasingly difficult in this environment. The identity of an attacker is different from the identity derived from markers in the tools used. The tools are created, distributed, and commercialized in Internet forums - in digital methods not dissimilar to True Value sales of wrenches, or Home Depot tile grout. The identity of the perpetrator is different from the service provider in much the same way that a thief makes use of a phone - but AT&T is not involved. Even the seller of stolen information is not reflective of the burglar - in much the same way that burglars sometimes today make use of Ebay to fence stolen goods.
What is important about APT is what was done, how it was done, and potentially why it was done (who benefits). APT describes a set of activities performed over time that makes use of various tools for an intended outcome that serves the perpetrators' objectives. There are several perpetrators in the scope of activities - the third party scanner/hackers who identify vulnerabilities in corporate networks that can be exploited and sell that information to other third party agents who package that information and provide access as a service; the developer/operators of those catalogs who perform reconnaissance and administration of the compromised environment and sell the access as a platform for first parties to exploit the commercial or intellectual properties of; and the first parties who steal the information in order to sell it to others or for their own competitive purposes.
APT is not incidental, it is targeted and exploited. Watch for the indicators provided by malware, but investigate the attributes of its use in order to understand how it is being used. The tools can help to describe the stage of compromise as well as the nature of the risk involved - unrestricted access, unmanaged control, or unmitigated loss.
The news about the recent retail breaches have focused on identifying a perpetrator by tool marks in the wrenches used by the mechanics involved. There has also been focus on the forums used by burglars to fence stolen information. Some sanity has to come into the conversation. "Kaptoxa" does mean potato in Russian; however in phonetic English it sounds like "Card(ha)" and refers to "Cards" as in the utility of the information being harvested by the malware used - that "Rescator" apparently edited in his/her Visual C++ project. The more interesting aspect of the BlackPOS malware is that it utilizes a file infector that has been associated with Russian-language affiliated malware since at least 2003 - called "Neshta", which makes it possible for assorted utility to be added to the code in order to create a functional use. The BlackPOS malware was created from available source code and sold to others for use. This is not a very different situation from Hacktivist use of PoisonIvy code to create backdoors during Anonymous breaches, or "Chinese government" use of Gh0st code to create backdoors during government and industry breaches. The tools are not sufficient to describe who the perpetrators are; but the use helps to identify the activities and related intent.
Cylance Infinity tools (V and Protect) can identify these APT tools that others cannot. Antivirus and Antimalware or "APT" tools look for known signatures of files, or behavioral attributes from reverse engineering or VM analysis. Those methods are unfortunately becoming obsolete as malware creators incorporate anti-analytics and polymorphism. What they cannot obfuscate though is their characteristics. When comparing a file against a common body of knowledge (of good files and bad files), the characteristics of a bad file emerge. That is what Infinity does. The ability to recognize a file and associate it through clustered characteristics- efficiently by using math, not mechanics, is what makes Infinity accurate. The malware itself doesn't matter, but its intent or purpose helps to distinguish the nature of its use - and describes the APT activities that the tool is part of.
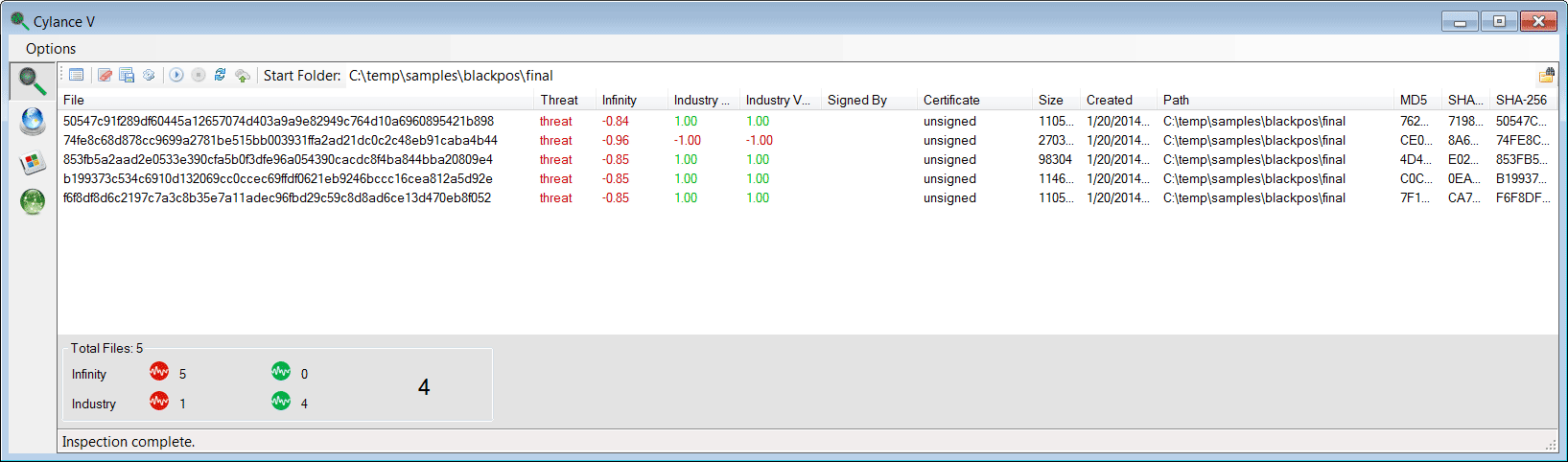
As an example, recently several samples of BlackPOS have been identified through submissions to a variety of public and private malware feeds. They are all composed of the same functionality and based upon the same code; however signature technologies fail to consistently identify them – because the specifics that the signatures look for (hash, heuristics) are modified – or antivirus and reverse engineering bypass code has been used. Cylance Infinity does not have these limitations however, and as demonstrated each of the samples is recognized by their characteristics by the Cylance math models in near-real time. Note the only sample that was recognized by industry antivirus sources is the sample from May 18th, 2013.
Dr. Shane Shook
PhD/CKO, Global VP of Consulting
Cylance, Inc.

