News about a new Microsoft Word vulnerability—one that opens the door for remote code execution—has been making the rounds in the security community. We decided to pit our CylanceINFINITY ™ platform against it to see what would happen.
Microsoft Security Advisory (2953095)
Vulnerability in Microsoft Word Could Allow Remote Code Execution (CVE-2014-1761)
https://technet.microsoft.com/en-us/security/advisory/2953095
In testing CylancePROTECT™ against the malicious Word document—which is designed to exploit the vulnerability disclosed in CVE-2014-1761—we found a few interesting points.
First, the file was submitted to malwr.com on 4/1/14, and at the time had only 4 detections:
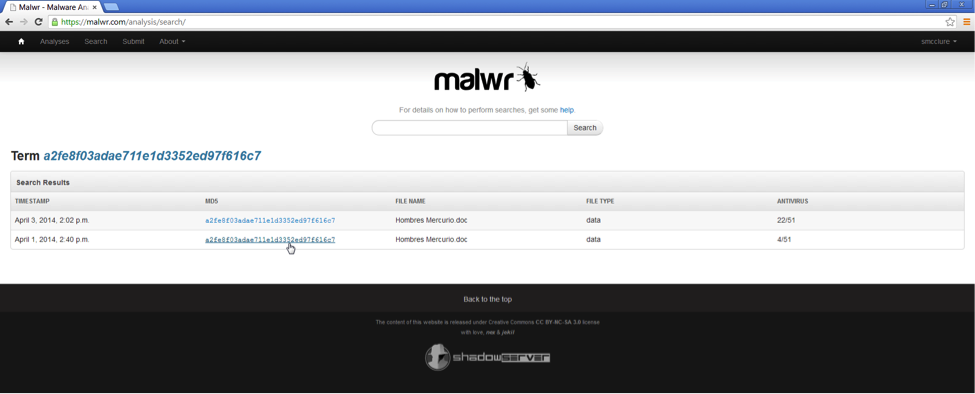
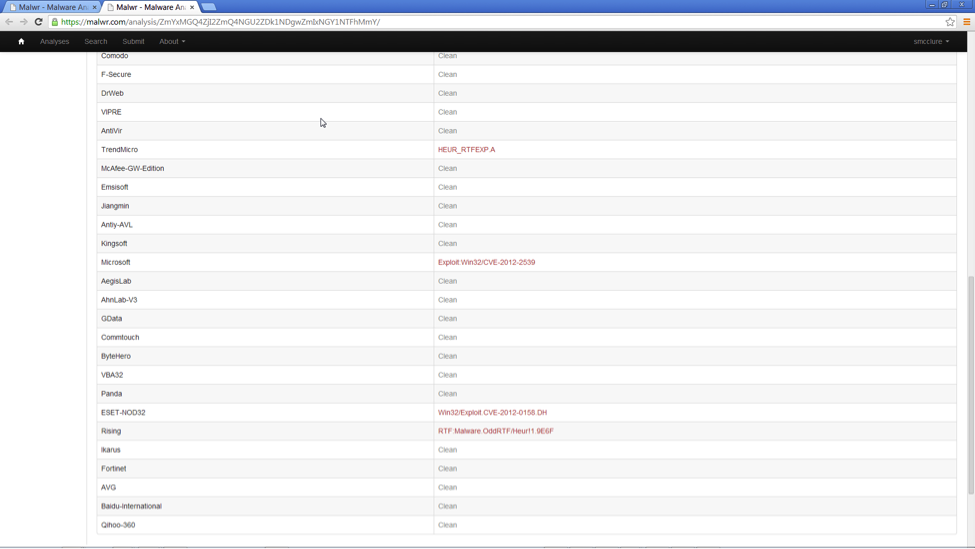
With only TrendMicro, Microsoft, ESET, and Rising AV correctly detecting it as malicious:
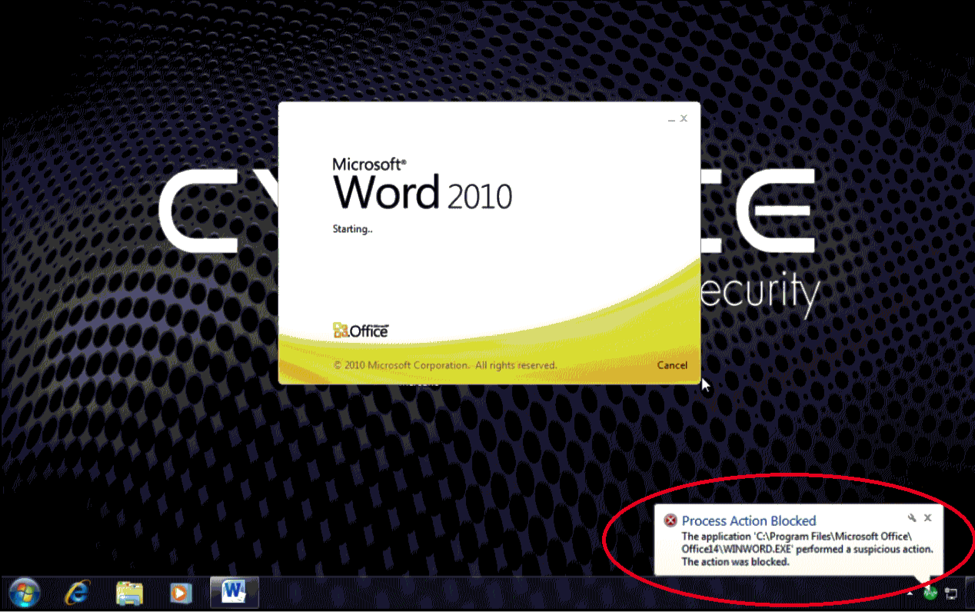
Trying to open the file on a vulnerable system—but with CylancePROTECT running on it—results in it being instantaneously detected and blocked.
With our Memory Defense (MEMDEF) technology:
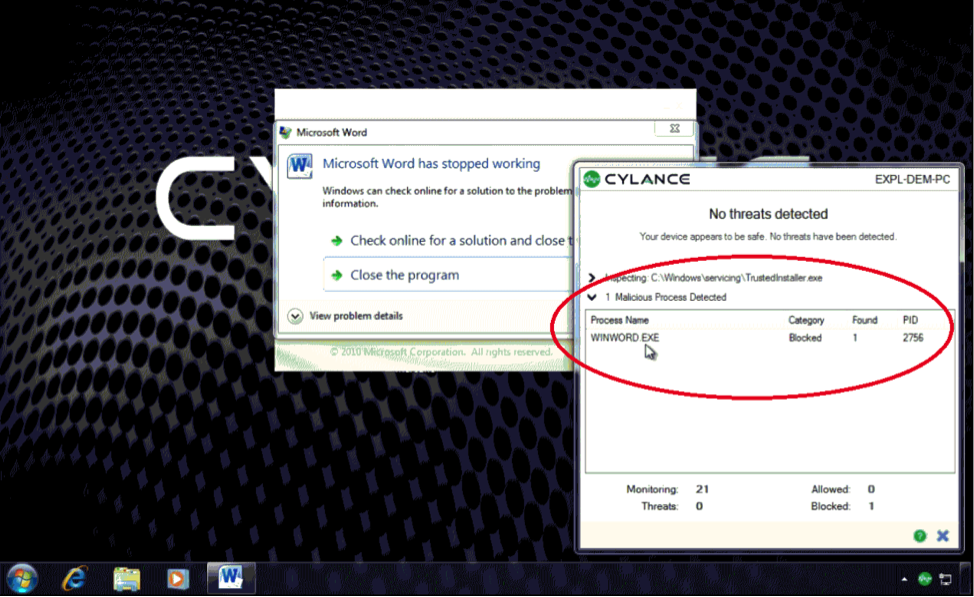
CylancePROTECT in action
But not only do we block the exploit itself, we also block the executable file (cf89602d6cd2327bb7fa2627e5d46052) that gets dropped to c:\Users\%user%\AppData\Local\svchost.exe in the event that we configure MemDef to not block exploitation.
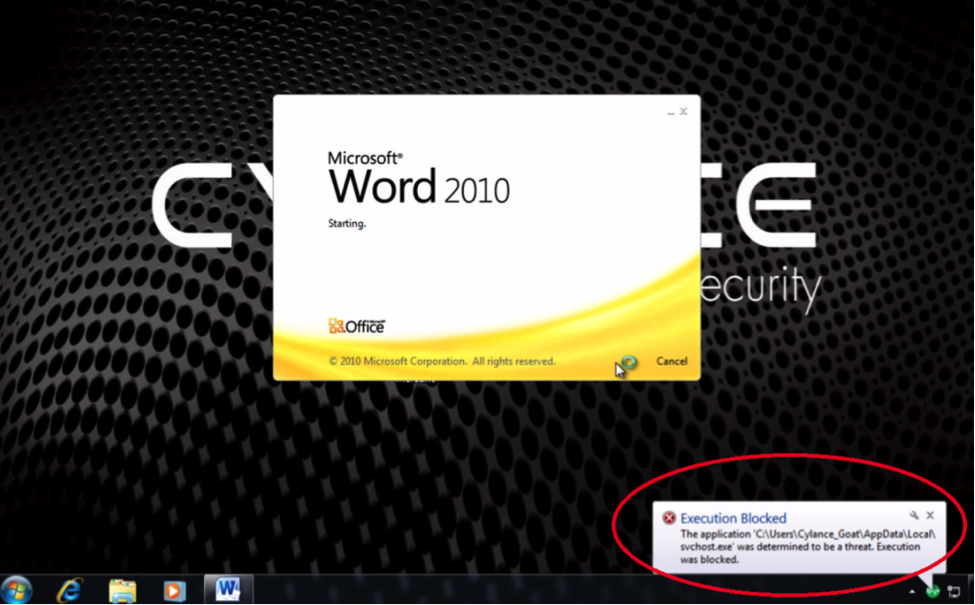
CylancePROTECT detecting—and blocking—the dropper
And with CylancePROTECT, the dropped file gets blocked but the document still opens for the user to view/edit. Of course with this particular Word file you would NOT want to view the contents as they're quite inappropriate, at least to some people.
The “first submit” of this file was on 4/3/14 @ 2:29:30AM where the signature world had only 11 detections.
And of course, in the hours that followed the signature based world had added 9 more detection engines.
But Cylance? Well, we detected it before the world even knew it was malicious. Detecting another zero-day, in yet another application, in yet another vulnerable version of the Windows platform. Again, no signatures, no heuristics, no behavioral analysis, no sandboxing, no micro-virtualization – just pure math!
That’s the power of CylancePROTECT.
- Stuart McClure
CEO, Cylance

