The following emerging threat (CVE-2014-4114) has been analyzed by Cylance's research team.
During last week’s Patch Tuesday, Microsoft patched vulnerabilities related to the following identifiers:
• CVE-2014-4114 (MS Advisory 14-060)
• CVE-2014-6352 (MS Advisory 3010060)
• Sandworm
• BlackEnergy
Microsoft released MS14-060 to patch the vulnerabilities described in CVE-2014-4114. This patch left open some avenues of attack that still allowed remote code execution. On October 21, 2014, Microsoft followed up by releasing security advisory (3010060). This security advisory makes some recommendations for workaround and provides a Fix-IT download. CylancePROTECT™ provides protection for the known files downloaded during exploitation.
Observed files include:
70b8d220469c8071029795d32ea91829f683e3fbbaa8b978a31a0974daee8aaf (PPT) 4b2b9c147ed28b8f908f96f0c0db8bf8a0da0ac47864bbe0b31c976a4229a2ea (doc) 30175747dda628bc4ad8353d8e71f17e44ec8dde36c81891ff539dcec5693420 (PPT) 2baba003ef1858b22c1968a2699269cb12d1c3ec117c4951d9775466eb4c7f76 (PPSX) 65a8bf996bfc23405be764266d7409a65fa936d19cee52b61ef83e29dcdd6230 (PPSX) bd2176b239d240232cdced2da9fc930e627a27190e7216142db93f6538b21006 (PPSX) 6732379efe230b522185cde9c186bc2640a5dfc7e154a6037ee3bbe067d6e705 (PPSX)
Examining the Threat
For a little more information,we'll examine one hash that happens to be a PowerPoint file.
30175747dda628bc4ad8353d8e71f17e44ec8dde36c81891ff539dcec5693420
The 2 packager shell objects in slide1.xml:
<p:oleObj spid="_x0000_s1026" name="Packager Shell Object" r:id="rId4"
<p:oleObj spid="_x0000_s1027" name="Packager Shell Object" r:id="rId5"
<Relationship Id="rId5" Type="https://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject" Target="../embeddings/oleObject2.bin"/>
<Relationship Id="rId4" Type="https://schemas.openxmlformats.org/officeDocument/2006/relationships/oleObject" Target="../embeddings/oleObject1.bin"/>
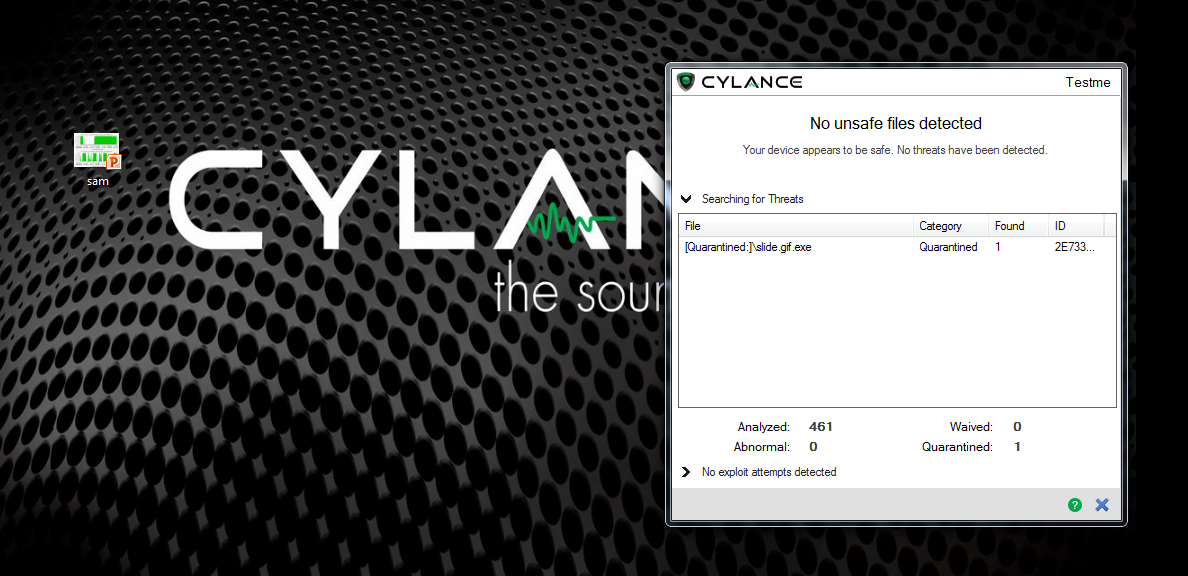
When slide1 is opened a slides.INF and a slide1.GIF file are copied locally.
Then based on parameters if slides.inf is loaded, it will install the .INF file. After that the .INF file will rename the .GIF file to .GIF.EXE and add the Trojan to the registry RUNONCE.
Known, in-the-wild executables that have been dropped as part of exploitation, are detected and prevented with CylancePROTECT. These include:
f6a4c241b38226a8ba5cc7a954faef6d7dc0c308534722860d38f7b7aaadad75 2731d7cfcde172e6dde879f9c26bddaa0d2b1beba9a27680fbd2fa37f9bf12b7 ea72c79d15fb1b7765d40733a251f8e3b8aeb278cd2bbf429d64921155214b36 980d577d3448477dbfe65316b42f2b970c3972e5b01be9abe7abba3568aa1de7 0fda6c118fb7dc946440cb9225e32ab1825d87d4f088bb75a6eab7cef35433bc 0f63c8f8f080aff491ffb5bb4fcbb23a4719f86df9435e06af42f835b31dc79b 2E73379DAB7819B3C8A1956EA1E7CB647763E96DAF65024E05314BDA8044DF0B
Recommendations
Cylance recommends the following threat mitigation steps:
Cylance VS. CVE-2014-4114
For questions or comments, please contact us at alerts@cylance.com.
References:
https://technet.microsoft.com/en-us/library/security/ms14-060.aspx
https://technet.microsoft.com/library/security/3010060
https://www.wired.com/2014/10/russian-sandworm-hack-isight/

