Since the allegations started being levelled against North Korea for potential involvement in the compromise of Sony Pictures Entertainment, there has been a stark increase in focus on North Korean cyber capabilities from the information security community. This includes, but is certainly not limited to, the outage of North Korea's network blocks and the security vulnerabilities discovered in the custom Linux distribution named Red Star. Recently, a security researcher has pointed out malware which is hosted on the Korean Central News Agency website.
Korean Central News Agency
The Korean Central News Agency at kcna.kp has been described as the primary news website for North Korea. The slow to respond website appears to host a number of news stories related to North Korea with a strong focus on Kim Jong Un. A perceptive reader may notice that every picture below contains Kim Jong Un.
This site provides a number of stories (with questionable degrees of truth) in a number of languages. When we view the English version of the site, we can see that a number of these stories appear to be focusing on negative aspects of South Korea, while others focus on Kim Jong Un walking around and looking at things.
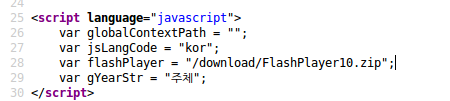
As a security researcher pointed out, if we look at the HTML source of the root page of the website, we can see that a path, "/download/FlashPlayer10.zip", is stored in a Javascript variable. If we check Archive.org, we can see that this Javascript was on the site as far back as January 2013.
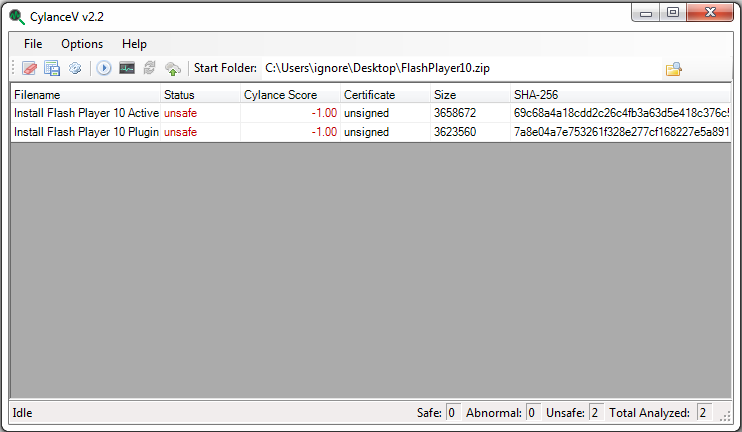
Once this ZIP file is downloaded and opened, we can see two executable files inside it.
Install Flash Player 10 ActiveX.exe Install Flash Player 10 Plugin.exe The Malware
These executables are intended to be run by an unsuspecting user attempting to install the correct version of Flash in order to get full enjoyment out of the news stories. Without much surprise, these Flash installers being served up on servers not belonging to Adobe are malware.
If we look at these with CylanceV, we can see that our machine learning based detection engine identifies these samples as threats with no doubt in its conviction.
Both these executables were compiled in March of 2012. The antivirus industry's detection of this malware is also strong, likely due to the age of this malware, and how long ago it was submitted to public and private malware feeds. When executed, a legitimate installer for the Adobe product is executed in parallel with malware. The malware binded with these installers injects itself into an instance of Explorer.exe and then proceeds to drop and execute a sequence of other malware samples.
During the execution of these samples, the domain a.gwas.perl.sh is resolved by the malware. The WHOIS information for perl.sh has only changed slightly over time, and appears to have only pointed to the one IP address (211.233.75.83).
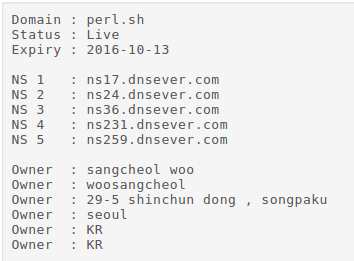
If we search for other domains related to this owner, we find the following domains:
dnserver.com 211.233.75.80 None, None, Korea, Republic ofdnsever.co.kr 211.233.75.80 None, None, Korea, Republic ofdnsserver.co.kr 211.233.75.80 None, None, Korea, Republic ofdnsever.kr 211.233.75.80 None, None, Korea, Republic ofmyhome.tv 211.233.75.83 None, None, Korea, Republic ofperl.sh 211.233.75.83 None, None, Korea, Republic ofwo.tc 211.233.75.83 None, None, Korea, Republic of
The resulting IP address of the DNS query of a.gwas.perl.sh (211.233.75.83) is then sent a DNS query, where the target domain is a string which presumably identifies features about the infected victim. One detonation of these samples resulted in the following DNS queries.
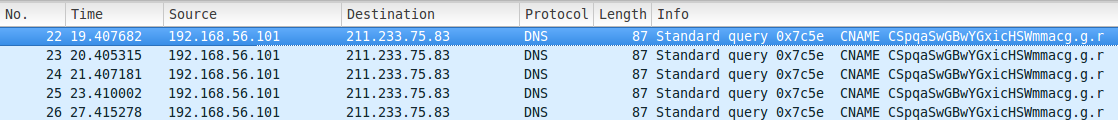
There have not been any responses observed from 211.233.75.83 for these requests. This IP points to a server in South Korea which appears to have at one point hosted a DNS server and HTTP server. There are a number of other domains which refer to this IP address either now, or during 2014:
|
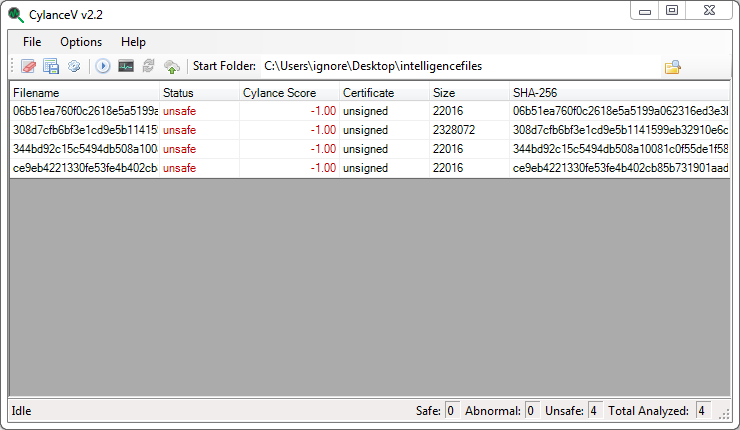
When searching for other malware samples that reference this IP address, we also see the domains wakaoo.wo.tc and mbkorean.wo.tc as well as another reference to a.gwas.perl.sh being used in a similar fashion with malware samples going back to 2010. As we can see with CylanceV, our machine learning models detect this malware as well.
Conclusion
This North Korean news site is serving malware with no sign of compromise. This has presumably been the case for at least two years. After some digging into details related to the malware's operation, we can see that this is not the only malware developed by this author, and that they use similar techniques for command and control communications across different samples. If you want to stay safe from this malware, as well as almost all other malware, I highly suggest using CylancePROTECT.
Samples
Samples are available on VirusShare.com
06b51ea760f0c2618e5a5199a062316ed3e3b5d1723d4aac6288d2f3da81a516308d7cfb6bf3e1cd9e5b1141599eb32910e6caa897ff3054e00368a1a6d7076f344bd92c15c5494db508a10081c0f55de1f583b9fb4830214d3e792273bb4bac69c68a4a18cdd2c26c4fb3a63d5e418c376c57591f18dd63628410fad81857547a8e04a7e753261f328e277cf168227e5a891bb418aaeb6cbb562da500354cadce9eb4221330fe53fe4b402cb85b731901aadd38e8cbcd7f9576e0c9988aae65

