Malware authors and attackers are constantly using new methods in efforts to bypass security controls. At Blackstone we use multiple technologies to keep pace with these efforts, including tools for fighting malware that do not rely on signatures or other historical data about known malware.
[Editor's note: Mauricio Velazco works in Vulnerability Management and Threat Intelligence for Blackstone. Blackstone is an investor in Cylance.]
Last month we encountered a campaign seeking to infect users with the Dridex banking trojan, which bypassed our email security controls, content filtering proxies, dynamic analysis sandboxes and traditional signature-based AV detection engine. Fortunately Cylance identified it, giving us an opportunity to analyze the campaign.
We learned that it was part of a massive campaign seeking to infect users with Dridex, which steals online banking credentials and can also be used to drop other malicious software, such as ransomware, onto infected machines. While the campaign was not specifically targeting Blackstone, hackers using off-the-shelf malware like Dridex sometimes sell access to other actors who use infected machines as a beachhead for launching targeted attacks that can be far more troublesome than ordinary crimeware.
On the first day of this campaign, our firm received hundreds of malicious emails coming from different mail transfer agents, using different sender addresses and different subject lines. Our email gateway identified and blocked most of them, yet dozens made it to user mailboxes due to the distributed campaign that succeeded in getting some malicious emails past that system.
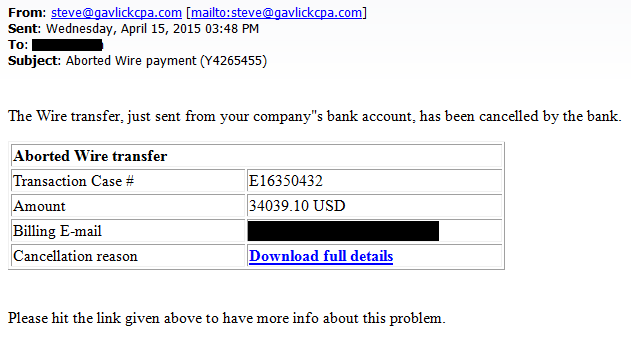
The email presented a supposed wire payment notification including a link in it, which is a common tactic used in malware campaigns.
What is interesting about this campaign is that it abuses two different companies -- Google and Dropbox -- in order to deliver its payload. This method successfully bypassed Web content filtering solutions. The link used Google’s redirection functionality using the URL parameter to trick users into downloading a malicious file stored in Dropbox.
https://www.google.com/url?q=[MALICIOUS_DROPBOX_LINK]
In this case, the actual payload stored in Dropbox was a Windows binary with an SCR extension. At the time of the incident, this sample was not identified by most of the signature-based AV companies.
Three days later, we identified another campaign targeting our users that used the same distributed approach to bypass email controls and the same redirection scheme using Google and Dropbox to store the payload and bypass content filtering. However, in this case the payload was different.
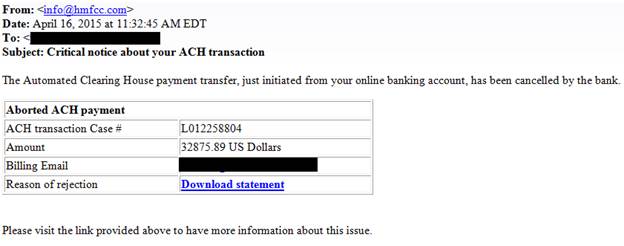
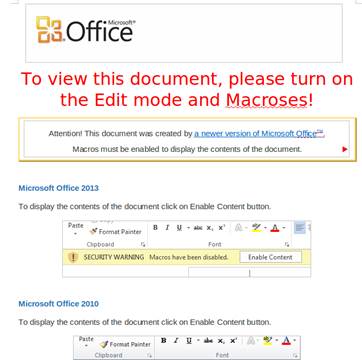
This time, the payload was a Microsoft Word document with an embedded macro. When executed, the obfuscated macro would reach out to the Internet, fetch the actual malware and execute it. As three days earlier, this malicious payload also bypassed signature based detection.
Attackers will continue to innovate to try to bypass security controls. As defenders, we should be on top of these new tactics, understand the limitations of our security controls and deploy extra controls to detect and prevent these new tactics.
By Mauricio Velazco
Threat Vulnerability and Intelligence, Blackstone

