A decision is only as good as the information that informs it, and the value of that information no better than the decider's ability to comprehend what they are seeing. So it is with Microsoft's User Account Control, or UAC, that notorious security feature introduced in Windows Vista:
This UAC prompt looks straightforward, but what's under "Show details"? Why, the devil of course.
ShameOnUAC
When the Cylance SPEAR Team was formed late last year we started looking into an area that we had long wanted to study: the potential for subverting programs during privilege elevation through UAC. We created proof of concept malware that attacks Windows Explorer, which we dubbed ShameOnUAC.
ShameOnUAC injects itself into the unprivileged Explorer process, where it hooks SHELL32!AicLaunchAdminProcess and waits for the user to ask to run a program as administrator. It then then tampers with the elevation requests before they're sent to the AppInfo service. (This is a downside of having an unprivileged process submit elevation requests for you.)
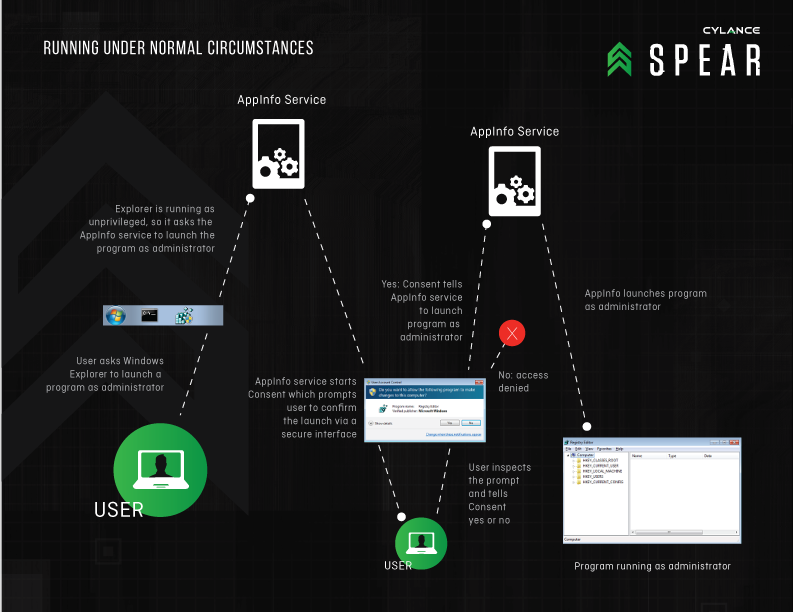
Here's how UAC works normally:
And here it is with ShameOnUAC:
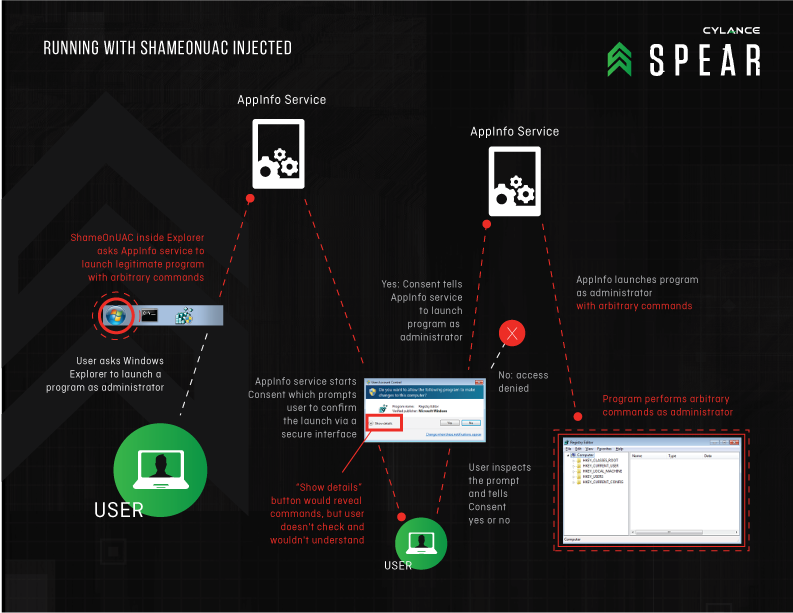
If you don't click the consent prompt's "Show details" button, you'd see no difference between the two scenarios. Users who review that box must understand what they see.
Technical Details
ShameOnUAC's AicLaunchAdminProcess hook currently targets requests to elevate cmd.exe and regedit.exe, though more targets are surely possible. It only replaces the command line, since pointing the request to a different application would visibly alter the prompt and tip off the user.
For cmd.exe, ShameOnUAC appends a "/C" argument so that the user gets the expected administrator command prompt when they click on "Yes." But ShameOnUAC gets to run a command of its choosing first. At that point, it has attained administrator privileges.
The regedit.exe case is more interesting because getting from command line to compromise is less direct. Regedit's supported arguments naturally involve the registry, so ShameOnUAC causes Regedit to silently install a .reg file via a "/S" argument. If that were the extent of it, the user would never get their expected Regedit window and might wonder what happened. ShameOnUAC's solution is to cause the .reg file to register a library in AppInit_DLLs and then issue a second elevation request. That request causes AppInfo to run a new consent.exe process (as SYSTEM), which loads the ShameOnUAC library before displaying anything to the user. The library then tweaks the parameters consent.exe receives from the AppInfo service to suppress the consent prompt. The user gets the expected Regedit window—after ShameOnUAC gets SYSTEM privileges.
Be Informed
ShameOnUAC adds a new trick to an arsenal of widely known privilege escalation methods, demonstrating an opportunistic privilege elevation from medium to high integrity when UAC is in use.
It's important to point out that UAC is working as designed. ShameOnUAC is creepy to watch in action because it shows users could have been unintentionally elevating malware from "dangerous" to "game over" all along, each time ignoring the information that would have allowed them to catch it.
Now that I've played with ShameOnUAC, I always click the "Show details" button, because if I don't it could be shame on me.
Editor's Note:
ShameOnUAC is the latest in a bag of tricks that can be played on users with UAC. For more, check out http://www.room362.com/blog/2012/01/03/uac-user-assisted-compromise/ and http://www.pretentiousname.com/misc/win7_uac_whitelist2.html .
Derek Soeder
Senior Threat Researcher