The rise of the Internet has given birth to a million shady 'get rich quick' schemes, but among the most intriguing and concerning trends to emerge from the dark web in recent years is the rising popularity of turnkey ransomeware kits, known as ‘Ransomware as a Service’, or RaaS for short.
Ransomware as a Service is something near and dear to my heart. I followed it very closely in a past life [1] and continue my ‘obsession’ to this date. Essentially, RaaS malware kits enable anyone with an Internet connection to sign up and build/ deploy a piece of unique ransomware in just a few easy steps. No technical knowledge is required beyond the ability to set up a Bitcoin or similar account to collect the ransom.
In most cases, the RaaS site owner collects a percentage of the ransom as payment, and/or charges a small fee for the initial setup service. Tox'and many other RaaS offerings have come and gone, but a handful are still around, despite the lack of stealth and the ‘obviousness’ of their operating model.
Encryptor RaaS has been around for nearly a year, since mid-2015. This piece of ransomware is available exclusively on an .onion domain on the TOR network. The ransomware author charges a 20% fee for every infected victim who pays the ransom, which is made in Bitcoin.
The Encryptor RasS numbers to date are as follows:
Total Number of Victims = 1818
Total Number of Victims Who Have Paid = 8 (0.44% of total users infected)
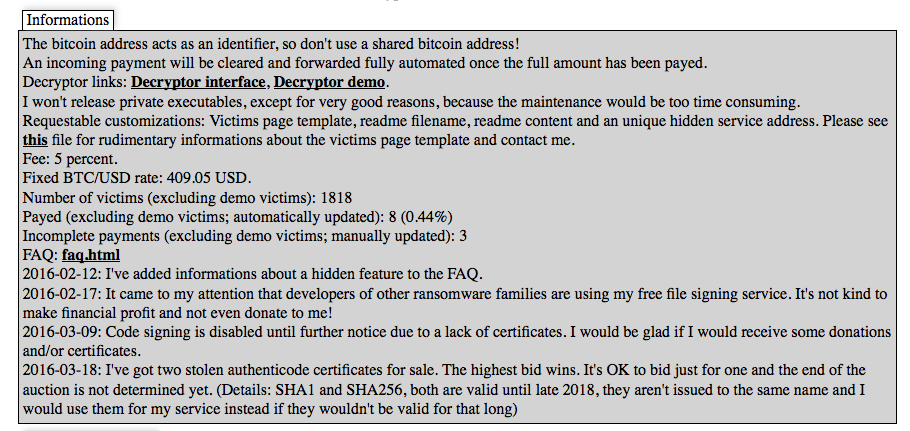
Figure1: Encryptor RaaS screenshot (March 2016)
In the grand scheme of things, these are not impressive or successful numbers when compared with, say CryptoWall, which infected over 625,000 machines in its first five months of operation. But the fact that the Encryptor site is still up and the model is still working is worth noting.
This is especially concerning considering the fact that every day the detection rates of traditional antivirus (AV) vendors are updated (via tests against NoDistribute). Detection rates for Encryptor RaaS are currently fluctuating between a 0/35 and 1/35 rate amongst the scanners that are included in NoDistribute’s test:
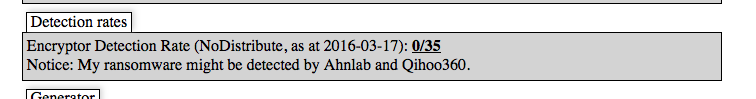
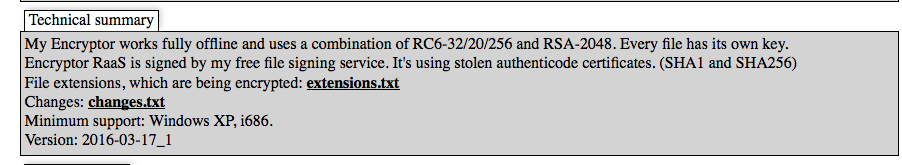
Figure 2: NoDistributes’s test results for Encryptor RaaS
The current FAQ and Changes.txt boast some interesting updates as well. Most notably:
2016-02-17: It came to my attention that developers of other ransomware families are using my free file signing service. It's not kind to make financial profit and not even donate to me!
2016-03-09: Code signing is disabled until further notice due to a lack of certificates. I would be glad if I would receive some donations and/or certificates.
2016-03-18: I've got two stolen authenticode certificates for sale. The highest bid wins. It's OK to bid just for one and the end of the auction is not determined yet. (Details: SHA1 and SHA256, both are valid until late 2018, they aren't issued to the same name and I would use them for my service instead if they wouldn't be valid for that long).
And this from Changes.txt:
- 016-03-04: Evaded the Bitdefender engine, Avast, AVG and ESET.
- 2016-03-05: Evaded ESET.
- 2016-03-06: Evaded ESET and the Bitdefender engine.
- 2016-03-09: Evaded Avast and ESET. Code signing is disabled until further notice.
- 2016-03-10: Evaded AVG, Dr. Web, ESET, the Bitdefender engine and MSE.
- 2016-03-11: Evaded Avast and ESET. Just screw you, ESET. Can you imagine, how much you're annoying the hell out of me?
- 2016-03-13: Evaded Avast, Dr. Web and ESET.
- 2016-03-17: Evaded AVG, ESET and the Bitdefender engine.
When you study the available information, it just tells us that this lab experiment/malware is still being actively developed, albeit with a very low adoption or success rate. Attempts to evade traditional AV products and technologies are adjusted almost daily.
Technical Details:
Encryptor RaaS utilizes a combination of RSA-2018 and RC6 (varies), with each file being encrypted with a unique key. A list of encrypted file extensions is as follows:
0 -0 000 001 002 003 004 005 006 007 008 009 1 -1 10 -10 11 -11 12 -12 13 -13 14 -14 15 -15 16 -16 17 -17 18 -18 19 -19 2 -2 2fs 3 -3 3dm 3ds 3g2 3gp 4 -4 5 -5 6 -6 7 -7 7z 8 -8 9 -9 aac abbu abw accdb adr ahk ai aif alt ape apk arc arv as asc asf ashdisc asm asmx asp aspx asx aup avi ba0 backup bak bas bbb bc bc! bcmx bdb bde bdf bdg bdi bdk bdl bdm bdmv bdsproj bdw bdx bee ben bes bex bexpk bf bf2 bfa bfb bfe bff bgz bhx bib bibtex bik bkf bkp bks bkup bmp bpl bpn bson btd bz2 c c++ cad cadp caf cbu cc cda cdf cdi cdr cdx cer cert cfc cfg cfm cgi chk chr class cnt cod conf cpio cpp crd crt crypt7 cs csproj csr csv cue d64 data db3 dbf dbt dbx dcp dds ddz del dem deviceids df dfd dfproj dia dir diz dlc dmg doc docm docx dot dqy dsb dsn dta dtr dtv dwg dxf ebk eddx edoc elfo eml emlx enc eps epub es es~ ex4 exp fdb fdf ff1 ffa ffl ffo ffs_db fft ffu ffx fh10 fh11 fi2 fig fil flac flg flp flv fmd fpt ftp gam gar gbc gcode gho ghs gid gif gla gpg gpx gz h h++ hbk hdd hds hex hpp hst htc hwp hwp ico ics idml idx if iff imb img imh iml imm in0 indd ini2 int ipd iso isz iwa j2k jad jar java jdb jks jmf jp2 jpeg jpf jpg jpm jpx json jsp jspa jspx jst k1f kb1 kcf kch kcl kdb kdbx key keynote kml kmz knt kpr lbl ld ldif lib lic lis lpd ls ltx lwp lyc lyt lzma m3u m4a m4v mab mar max mb mbox mcs md2 mdb mdbackup mddata mde mdf mdi mdinfo mds mdw mdx mid mke mkv mmf mnu mobileprovision mod mon mov mozeml mp3 mp4 mpa mpb mpeg mpg mpj mpp mq4 mqh ms msf msg mso mta mts mus myd myf myi nam nap nba nbf nbi nbu nbz nco nes net new nfo nick nng note nr nrg nri nru ns nzb oa4 oac odb odc ods odt ogg old ops opt or4 org otm ott ova ovf ovpn oxps p p12 p2i p65 p7 pages pbi pct pdf pdfx pehape pem pfq pfx pgp php php3 php4 php5 phps phpx phpxx phtm phtml pid pins pip pk pl plist pmd pmk pmx pnf png ppdf pps ppsm ppsx ppt pptm pptx pref prn prt ps ps1 psd pspimage pst ptn ptn2 pub pvm pwd pwi px py pym qbquery qcn qcow qcow2 qt qxp r0 ra rar raw rdp recipients recipientsbackup0 recipientsbackup1 recipientsbackup2 recipientsbackup3 recipientsbackup4 recipientsbackup5 recipientsbackup6 recipientsbackup7 recipientsbackup8 recipientsbackup9 rm rpb rtf s sam sav sb sbf scv sdc sdi sds sdx sdy secure seed sel seq set sfs sfv shlb shs skb skd skp slf sln slt sme smk smm smp smr sms spb spi spro sql sqlite sqlitedb srp srt srv ssc ssi sss stf stg stl stw sub suo svg swf sxw symbolmap syncdb tag tar tav tb3 tc tdl tex tga thm tib tif tiff tlx toast torrent tpl ts tv tvc txt ucd ufo user val vbk vcard vcd vcf vcs vdi vfs4 vhd vhdx vir vmc vmdk vmx vob vsd vsv wab wallet war wav wbk wbverify wc wdseml webarchive webm whtt wim win wlt wma wmb wmv workflow wpb wps wsb xdw xed xg0 xg1 xg2 xlg xlk xlr xls xlsb xlsm xlsx xlt xlw xoml xsn xz yg0 yg1 yg2 yuv z zip zipx
Encryptor RaaS is also currently capable of signing your generated code via “stolen” Authenticode certificates. The latest update on this can be seen on the site as well:

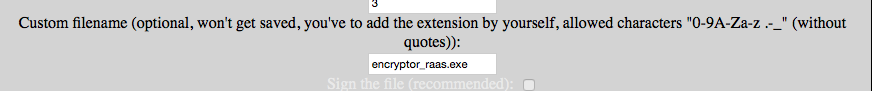
Figure 3: Stolen Authenticode certificates for sale via a third-party website
Setup Steps:
The basic model for setting up Encryptor RaaS has not changed since its inception:
- 1. Enter a BTC address (for payment, and this serves as a unique ID in the Encryptor RaaS system)
- 12. Enter price for decryption prior to timeout
- 13. Enter price post-timeout
- 14. Enter timeout
- 15. Enter number of files that can be decrypted for free
- 16. Enter custom filename
- 17. Toggle code signing (currently unavailable)
- 18. Toggle UAC behavior/level
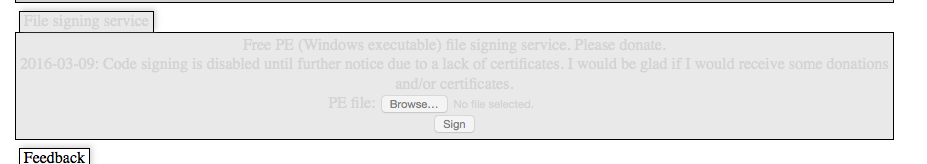
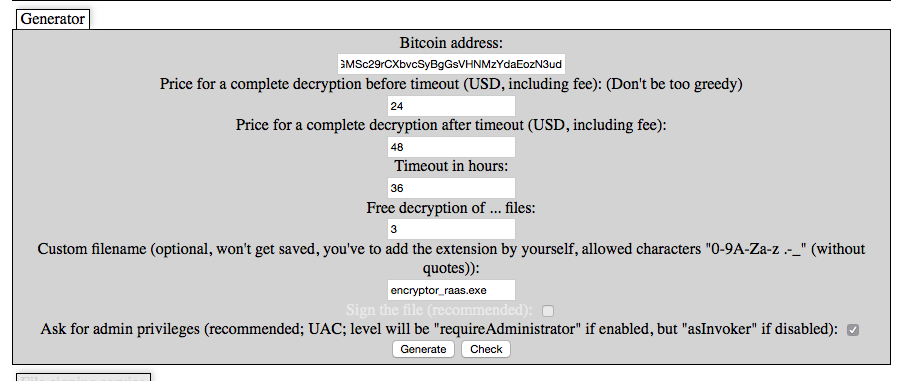
Figure 4: Input fields for Encryptor RaaS setup
Output:
Upon generation, you are provided with a W32 EXE file with the name of your choice:
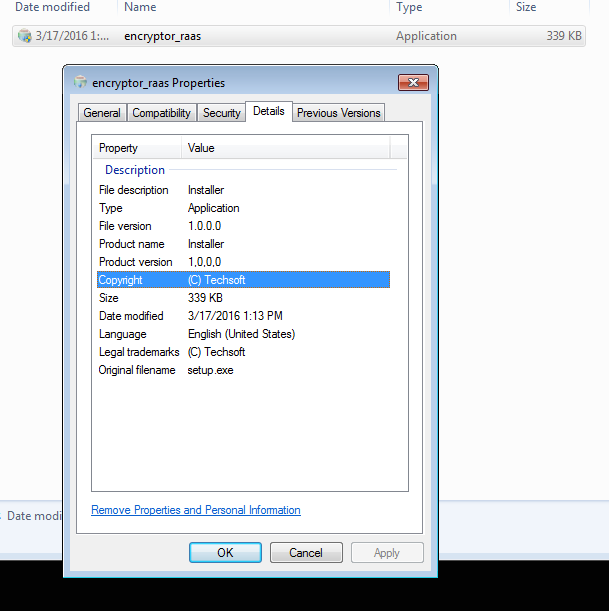
Figure 5: Final output of the Encryptor RaaS application.
Upon execution, decryption instructions are written to the user’s %TEMP% directory as 'readme_liesmich_encryptor_raas.txt' ('liesmich' is German for ‘read me’). The victim is then presented with a webpage, with the default browser window open to the corresponding decryptor/message site via onion.link URL:
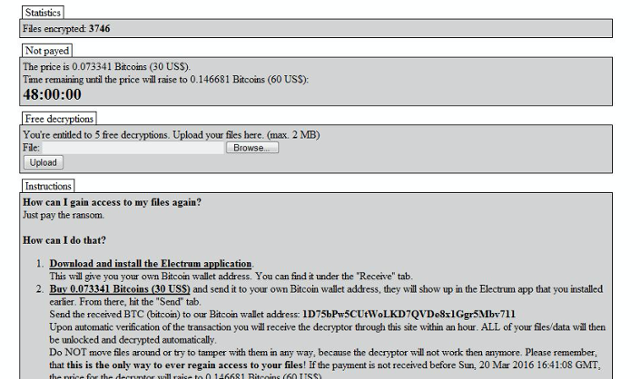
Figure 6: Screenshot of ransom message displayed to Encryptpor RaaS victims.
It is also important to note that like many other recent ransomware families (including Locky), Encryptor RaaS will directly target and delete VSS (Volume Shadow Copies) on the victim's machine via the following command:
cmd.exe /c vssadmin Delete Shadows /Quiet /All
Encryptor RaaS also attempts to modify local proxy settings and appears to detect various virtual environments to evade analysis.
The decryption site(s) are readily visible as well:
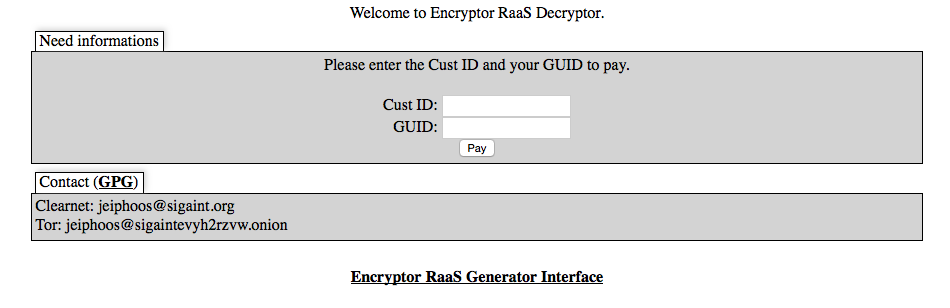
Figure 7: Demo Decryptor site.
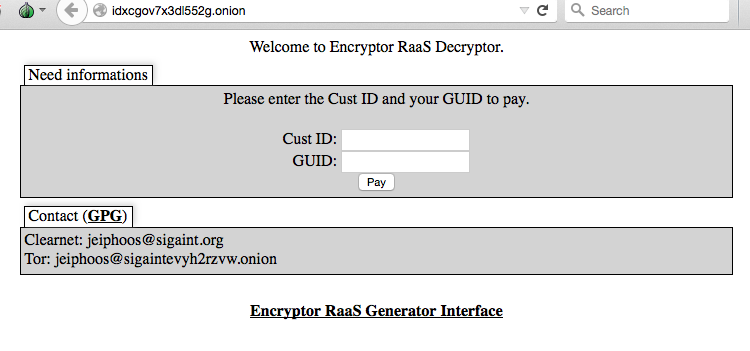
Figure 8: Live Decryptor site.
CylancePROTECT® vs. Encryptor RaaS
In-the-wild samples of Encryptor RaaS will be unique based on the nature of the service. This would be a handicap with traditional endpoint AV technologies. Because each piece of Encryptor RaaS software is unique depending on the parameters set by the service user, AV vendors can’t build exact detection. Generic detection is also a challenge, when considering the potential risk of false positives that must be weighed.
Let’s take a look at the current detection rates provided by the Encryptor RaaS author via NoDistribute:
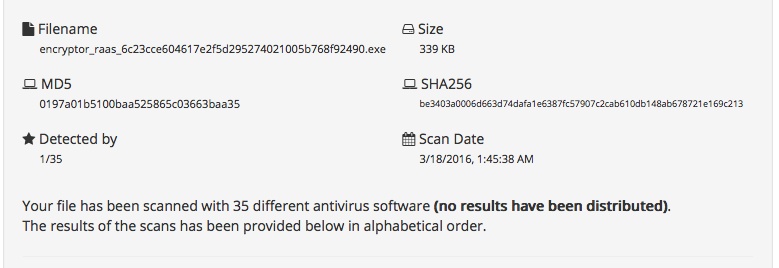
Figure 9: Results of NoDistribute vs. Encryptor RaaS
35 different AV products were run on the Encryptor RaaS .exe file, but only one product detected it (the single detection was a heuristic hit). Think about that: one single detection on a very ‘obvious’ piece of malicious malware that has been available free for nearly a year, for any and all to analyze and mitigate against. (This is not the first blog on this threat either.)
The bottom line is that there is no reason whatsoever why current AV/endpoint technologies are missing this. To compare, I uploaded my own copy of Encryptor RaaS to NoDistribute to see how the results compared with the daily test by the malware author.
Sure enough, I have the exact same [2] results!!!!
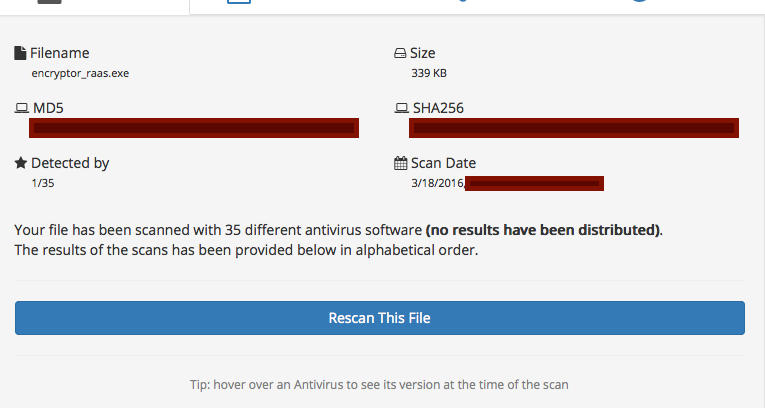
Figure 10: Encryptor RaaS detection results on NoDistribute.
In contrast, CylancePROTECT detects all the code generated as Encryptor RaaS, even though it uses models developed prior to the creation of the malware.
Here are the results of a single detection scan by CylancePROTECT. As you can see, CylancePROTECT both detected and blocked Encryptor RaaS, despite never having ‘seen’ this particular iteration of Encryptor before:
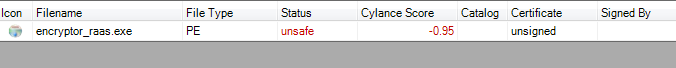
Figure 11: Encryptor RaaS detection results in CylancePROTECT.
Believe the Math!
[1] https://blogs.mcafee.com/mcafee-labs/meet-tox-ransomware-for-the-rest-of-us/
[2] Scanning with a different, more ‘mainstream’ service still resulted in a 5/54 detection ratio

