Over the past few weeks, our research teams here at Cylance have witnessed the emergence of an update to the highly-prolific TeslaCrypt ransomware family. We were not alone in our observations, and many outlets have begun the requisite flurry of blogs, IOC updates, and any other means of distributing threat data in the hopes of assisting the security industry to curtail the threat.
The update, TeslaCrypt 4.0, includes stronger encryption using RSA-4096, bug fixes, formatting changes such as omitting easily recognizable extensions for encrypted files, and changes to the ransom note and instructions. Beyond this, the basic attack model remains the same.
TeslaCrypt: the Saga Continues
TeslaCrypt initially surfaced in March 2015 as an aggressive ransomware which specifically targeted gamers. Users of 40 popular games such as World of Warcraft, DayZ, Fallout, Diablo, Minecraft and Call of Duty found themselves locked out of their games with crucial and hard-earned files including saved games, maps, mods and configurations maddeningly encrypted.
TeslaCrypt also sought out and encrypted valuable finance-related files such as tax returns and Quicken software files, plus files with common extensions such as JPEG, PDF and DOC. Newer generations of TeslaCrypt now infect computers without any stored games, as the ransomware continues to evolve. Once the user is infected, TeslaCrypt demands payment of $500 in Bitcoin in order to decrypt the user’s locked files.
Although security researchers were initially able to release a number of free decryption tools that exploited a weakness in the ransomware, when version 3.0 was released in January 2016, it included a patch for the flaw, rendering the decryption tools ineffective.
Initial Deployment of Version 4.0
The initial campaigns for TeslaCrypt 4.0 were email based. These emails had a malicious .ZIP attachment containing a .JS file. The .JS file was responsible for retrieving an executable from a remote server. This second stage executable was responsible for the file encryption routines.
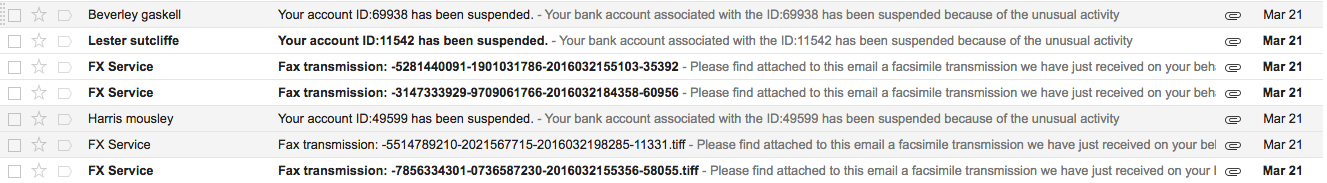
Figure 1: Malicious emails with TeslaCrypt .ZIP attachment
It is important to note that, as with other ransomware attacks, user interaction is a requirement to the successful deployment of TeslaCrypt. The victim must be lured into manually opening and launching the attachments in the email. As such, the actors behind this campaign have updated their social engineering tactics to make their email hooks more enticing and authentic in appearance, typically by preying upon the user’s fear of having their bank account compromised or of making a mistake in their taxes.
Example Subject Lines:
Your account ID:69938 has been suspended.
Your account ID:11542 has been suspended.
Example Body Text:
Your bank account associated with the ID:11542 has been suspended because of the unusual activity connected to this account and a failure of the account holder to pay the taxes on a due date.
Your debt: - 341,24 USD
For more details and the information on how to unlock your account please refer to the document attached.
Example Attachment Names:
- confirm_66988313.zip
- warning_letter_43923148.zip
- watch_it_89827269.zip
Execution of TeslaCrypt 4.0
Once executed, TelsaCrypt’s encryption routine and system modification begin. The stronger cryptography used in this version makes previously successful methods of recovery no longer possible. Third party decryption and recovery tools will not function with TeslaCrypt 4.0. Likewise, it is computationally infeasible to break the encryption.
To make matters worse, similar to other recent ransomware threats, TeslaCrypt will attempt to delete the VSS volume data (Volume Shadow Copies) from the user’s machine, thereby making the most obvious fix unavailable.
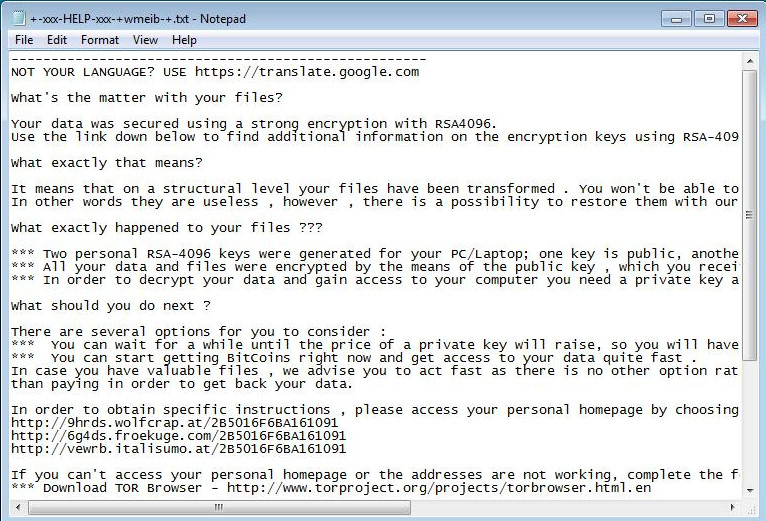
Figure 2: TeslaCrypt ransom note displayed as a Notepad file
C2 Communications resemble the following:
- URL: h x x p:// marvel-games[.]com/binstr[.]php
- Data: POST /binstr.php HTTP/1.1
- Accept: `\xff\xc1\x02X 1\x038\x01\xc1\x02n\x07\x01g\xf8t\xc1\x02, \, X 1\x03`\xff\xc1\x02DCED486F16D001F6CA18E3D207F6ADCF1225FD4C843950AC2230FF235664BA07067CFBC16C72F08627A91036EEC585A4509F34FC01D8BD6BAD2F099C9D40FA31EB2E513E8C2AD2812BD305D36148FEBBE866E5AD616E88027F40E42DED, `\xff\xc1\x02X 1\x038\x01\xc1\x02n\x07\x01g\xf8t\xc1\x02, \xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe4\xe4\xe4\x1b\xe2\xe2\xe2\x1d\xde\xde\xde#\xe3\xe3\xe3%\xfe\xfe\xfe\x13\xff\xff\xff\x02\xff\xff\xff
- Content-Type: application/x-www-form-urlencoded
- CUser-Agent: Mozilla/5.0 (Windows NT 6.3 rv:11.0) like Gecko
- CHost: marvel-games.com
- CContent-Length: 645
- CCache-Control: no-cache
Decryption Process
Payment to decrypt the user’s files is requested via Bitcoin (BTC) as per the instructions provided on the ransomware lock screen:
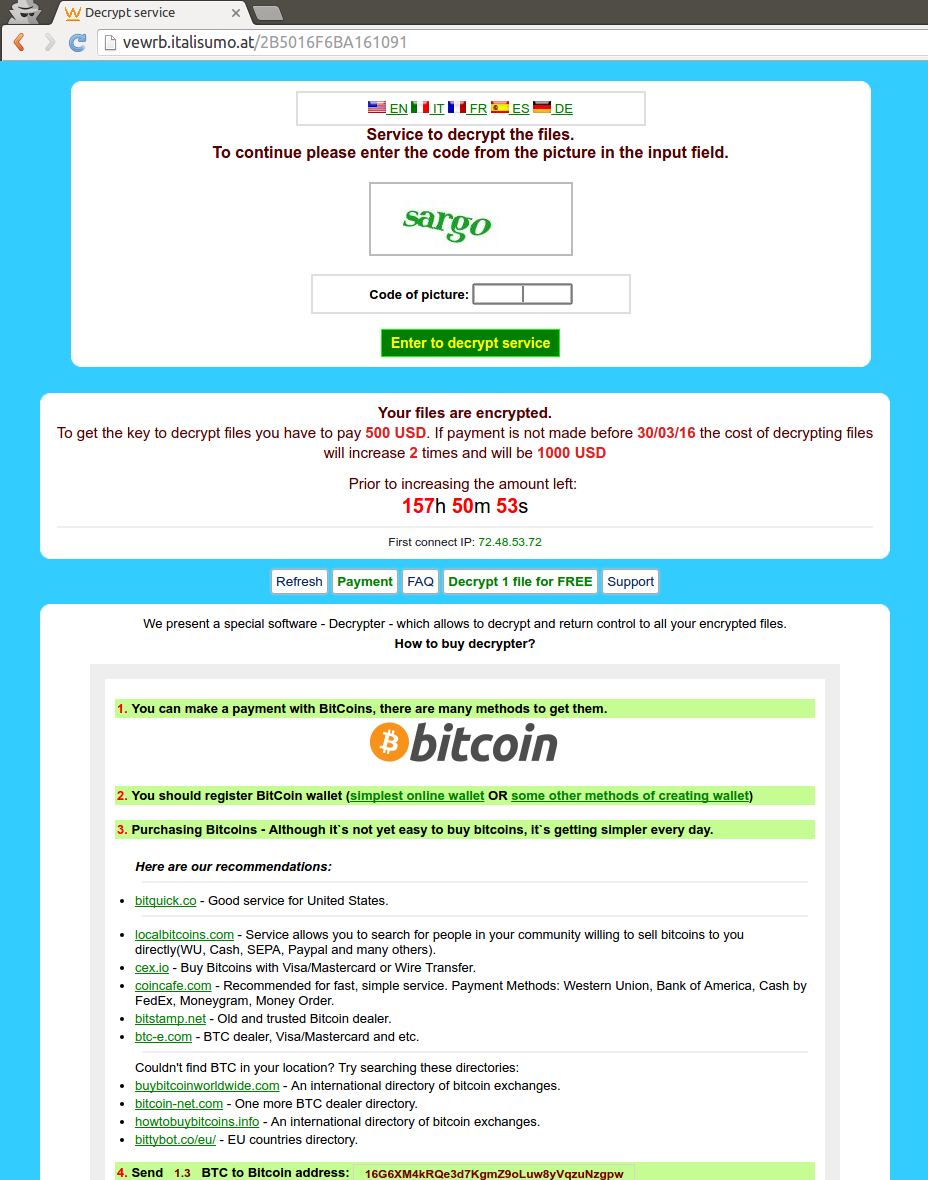
Figure 3: Ransom note generated by TeslaCrypt 4.0
As of March 2016, standard AV detection rates are still abysmally low for TelsaCrypt. Even with the ample media coverage and exhaustive sharing of file details within the industry, we are still seeing very low detection rates for both the .JS and .EXE files associated with this threat.
Example:
One leading multi-engine upload site shows this to have a 5/57 detection rate as of 3/24/2016:
SHA256 – 6964900cef84e768d69424e4950ac74992dbdf654e6865df59932dd4bd8f64bc
CylancePROTECT® vs. TeslaCrypt 4.0
Cylance pulled samples of the latest variation of TeslaCrypt based on C2 domains and other relationship markers, and deployed them on a machine loaded with CylancePROTECT. In this round, we looked at 60 unique binaries. Out of the 60, CylancePROTECT both detected and blocked 100% of those unique binaries, using a mathematical detection model that PRE-DATES the current TeslaCrypt campaigns.
Once again, the math prevails and prevents a potentially catastrophic ransomware attack:
Figure 4: CylancePROTECT console showing detection of TelsaCrypt 4.0
Hashes (SHA256):
- 6cb9ef0cb238752db082c482a35053d0dddff28becf1cfbb4a632d72aced1e2c
- 50f84771d333540c969ec2183f7712e53ab0a387191c7b58678eae82fd548456
- a7fd86ee2179598a7830d16f1b3c3b3bd7c89d5c03c993c9a0819665977dfe69
- 5aa6a88868308064e1f9f8df3477addd3baf5e864523717d2b654705f4630588
- 593543fffae9c12cb2d527c405309b46575aa111d64689d593785643e1294b30
- f5a5102bae7fbf31ab2318c8d0feb9c691d1d7345d3f3885edeb2cf41edda596
- b29b77d35c65b2543f1d7a8fe7feb64cefe2204a3fb2225cb4c7c4a4734b0cdc
- 475022ad1c94da21d90cc48523f92a91533781c9c3101c7f64cbf8d2e6e05819
- 6bdab9543a8ac059bb2b333755da5d534f8430aa09f9e4a359e78151d2aeb1b5
- b568d4b836139baa0123fd5eabdde20bfabe05324ba7d68bfc2b02efa0bb6b0b
- 1d8e0998e760a690070d1101b72c10ce129378e8a212221b04c5b866f6634d2c
- e1ea9a411a2bea988c2b921871849b9b9039193104c885bedb99f8c8d3bb1214
- 062dbdad33b58903a14bb49d2888714deb45ff7439bd28ebe8660d2ef4fcc1a0
- 6964900cef84e768d69424e4950ac74992dbdf654e6865df59932dd4bd8f64bc
- 72c11bc4998ba5b2c5717af04187259f6ddc9297ebd092f2aa1c32d165fd2648
- 4b60a413c2c3c7608b8473eb2d6941b5ef7c4663a07fabb58e1985bd5a29ba38
- 16e2d300a5133c6a0ff21e7cb6575507405df4c096828424eb370fdec4e2f89f
- 2433f6e17cf7381cec531acb490fc13399392bc5dfe340f2549555923293a983
- f581ea4ba7a3c58ef8dd5923401cd720a3fc7c58e13c1101471d8ca090d9f3c2
- 8dbcc4795a8f9f6fc02aac62a0498ddbc6592ba34d1cc8eeea8a2cf18511da78
- ef0df94ca52c835a74d047de808e9c24f31c9468953a11c0cc76cc97432d1647
- 48b6f4c6a99547fdd9bdff0b815f1c6582664d6c366c7dd5962c730c2656f750
- ad89f8066a368c14418d1c3b8144454f22d784f10785958142a934dc36e616a9
- b253da1456b47de73f146ef395ae8e4b105751acaddf8b2fcb9e50398b79b27c
- 943b2d3ac10936ef65244c894d831dddd22cd865d8e6b6fe9fbf50876f6781ce
- 3189ad72d4c817ad4dcc4320eed86157d1c5232393a186a47efba5c6149198a6
- ad0a52c915f4eb78c59e54db0f441edddaf56a9d6a812bedb1b52a910248072f
- b2f857e052924061c219b6462a06f2b6221409e706204c4e247611bfbfa71cf2
- 95f49139ff0f98af8ac0f26b15f4add0c56c45afb2261eb257c6cc44f4f76d34
- 673d694e9debc2832baab93b633a815dc478453bf429551364902297493dd7ba
- 644c54329771fa735a34390e72532e0262ce9f0ca6e18ccefd4d141aa4d5995b
- 42e562c5902cbd0a531a41925956c632e1e957f7f79cb58b1310eedd1cf77921
- c830dc7f823c71e50b0302849d4e546f4dae75dea8694fef903991c6759f9feb
- 7da88e7719267a69d75bd8a44455a7d4e9cabf0c1639c7d200243517b354dd17
- f8b4ca84f342d351ce94342dd77fe8c420fca157c6de31ced78d278e8d514b7c
- e823b0bf0935559e2913b3adb6d650d85f2fe8345aa3d5321f235a7261ec12ef
- b1064d0229bee77960dda91ad91b1fc77a0e13e4139a9e04539dc1107e1163fc
- 839067b46b94eaa4d471d39229bf8b77fc4e333e3ba2c8358ef4e0f85ff5aa20
- e052f248f9a4e667b9c4658e8340811c6fff2db35f79e88756af680d3f12e2af
- ebafe18803975341b9a6f4cee298a5e8a2adb7df539dff722f1689b4ca6999cb
- 8331e625dc343d59c007f4814d88ba4ca59090db37102b41b7acac97a2044356
- 9d27684ad3cfe7036b0f8b76146485c4808088767fd7de70381e7dd42b866b1f
- 0f79116e2d6a2259724f48f79c89421f50d2dee82b279f24c50d364337cfe8de
- 3906731fd5c73b193b03251a6922d7a3c8ac0b248e9cc52f3a0997e9c6b2a24b
- 0f50bdaa0c6576ac49ab48582ea5108083f1cd8fc439bc3737967729985818f3
- 86ee7197f19434ca385204b94acda7af8671c0db3103cbcfe9e21651c3df60b3
- 4c749298a32f1913282dd7cffeb23bacfbe9164b85673e54a78e5b708a87ecaa
- 584d2cc682be4cd81117f4aec2bcf8600a209482609ab2b4a3a7f02bf314436a
- d62ad20b0b0f314d32a45688d8b47f85e0b0eae9a18e5533ac2d37c2fa530f63
- 6e151355866e68cb527c593a543604e80c2e14b9c12d733c90fdf1e7a213e1cf
- bf403e9f57535c440870ca92aedb324a10c998d0c3aac158e5108150e89a0fb4
- 9731588e5bd63200f01d21707293beeadca9da38d791d65486bd805ef914a252
- 7db62797f09e8b4c91b54ad84c3f904643ff7e6a2cb9162a59f05a88ad84719a
- 1ab761f6c5659b57f8dc82d59aa756ae4ff68d5e31010d448f13110bf9d04efb
- 3ae6099b7cd27530c11d74c25becf5b73910bf63d8e2b430b49e12177126e7ef
- e15e39032dac05b65e78b044d44215742aee475cebf5ddcc1199fc0c8ac43f22
- d3b16261b5b5ee7c4ced37f58bd307f5a6bc7771e7ba5ffcd9dd07cc84225479
- 086691503751c00b0a28323507543e01478a26a1ca8d3af5b0e36b0f63dfab04
- 16097d181bfd788211e2efb5d259b125ad196454fee49e763c0327d58e0fd0e1
- 93ad40cd3fd7d5934e37b3ed09f44dc70cc616326b41578f549c6477bbf6cfe1
Additional Indicators of Compromise (IOCs)
Domains:
Email Senders:
- gaskellBeverley76675 (at) vocationalalternatives.com
- sutcliffeLester87269 (at) thiagoamaroarquitetura.com
- mousleyHarris145 (at) questcomputersolutions.com

