News recently spread within the cybersecurity community about a curious new variant of Qakbot (aka Qbot). Qbot is a multifaceted family of threats, which first emerged in 2009. Most strains observed in the wild are highly robust and adaptable, and contain various trojan-esque components as well as the capability to evolve, mutate and self-propagate. Early variants were utilized primarily to steal data and establish a persistent foothold within the target environment. Several further Qbot campaigns between 2009 and 2012 were set up to steal online banking credentials, making it an attractive choice for cybercriminals.
While some of the most recent variants contain new features such as improved polymorphism, updated inline hooks, bandwidth testing and more, much of the core functionality remains the same. The use of server-side polymorphism and multiple anti-VM (Virtual Machine) monitors all serve to evade detection by traditional antivirus (AV) technology and similar ‘established’ controls.
These tricks also add complexity to standard analysis and automation practices in place within the security industry. With encrypted, in-memory strings as well as the ability to alter behavior when running in VMware, VirtualBox, QEMU and others, a few more steps are required for analysis. These tricks are not exclusive to Qbot, and most seasoned security researchers are well aware of these methods and can react accordingly during their analysis. Nevertheless, it adds extra pieces to the puzzle.
That much being said, regardless of any new functionality, the basic observables are still present and predictable for Qbot. In recent highly publicized campaigns targeting multiple verticals, including healthcare, government, commercial and academic, the spreading and initial infection duties were handled via the Rig Exploit Kit. The Rig Kit has been around for many years now and was especially popular between 2012 and 2015, utilizing exploits in Internet Explorer and Flash Player.
The Test
Regardless of the delivery methods, polymorphic capabilities, self-protection, etc., our endpoints must bear the burden of prevention. If down the chain, the threat executes and you are compromised, this is the end of the story. This is where CylancePROTECT’s approach truly excels and shines. There are still all too many ‘established’ AV products that do not detect the latest (and prior) artifacts associated with Qbot, which should be a big red flag to anyone still running one of these traditional AV products.
CylancePROTECT’s machine learning models can prevent execution and subsequent environmental compromise of both past and present variants of Qbot, regardless of what shape the binaries take, or how they are ultimately delivered onto the system.
We put Cylance’s technology to task with the following samples of Qbot:
(SHA256)
020356457e95f7607c1941e03294b4c16e23daa402d7e79cfd2ba91b23969480
1154cb9fb9cf44a54aca9d3d689759ad6e89614a60c643ee3a5f496b52715b14
1826dba769dad9898acd95d6bd026a0b55d0a093a267b481695494f3ab547088
19bc15f4ff791d0ea11e9820781fe3375d09f79f7e8db504cf367bc9abd7e0dc
1b2ad766759b5d1418ec0f00457d1420386773a4b9e1d89ecfac12ba9bcc333e
428f253c68a3458e3ed46106303ec1330439da46eccac895b5973f829e39c5a7
4f9c55162e7daa23aa79013bcd89876fd3b20148e1599397bfae18b974b73202
5553e5808ebe40e4c5fc54bdd3fba7f2a6c7cbead7f3008e9e0d0a3a45055164
6fbb43ed7040856c48256fb3336bb347ca030c47e20e86885632d0ab7e88e4d5
9417c5f596e7b05596e45b0935c157cb16b57c4f20ee58058f4b1ab581d718f7
9490f5d06d46231ffd57d8244f1b63267b6da532ead148915782fa9662833b1a
9ea5655df078af9fd5f0a8288d7ca563ff9325ec71deceb6a2433693d86cd5e2
bd4efb0d92ebb563c9128f70f282dfaa33b217c15c4a9b37b590c535e25186d9
c8b311ac38d74ad410f6795d055b08f3f91f78a6b3fc3c0a2f69484d19ba6699
d599e92d3a9e1e22e5b7243e6b54b39b241f3b2fab5be879924e605c1291a84f
d8e26423aa8375190089f65f7013ea8d21217ffb25bcbf49fdd988ce8267575a
dded086d7cff8546c395df9c794ef1efa342428fd6d011e1f59641d3ba0f0aeb
eecdfa2fbfcd1b34c9461224f8cd46ed0b874409805f87a547a481a9d4909ec1
fb5fcf8a9b688fdbb8a982d1bf2adf2fb1d8cdd5b470bd0b22cbe8a7b09a132d
The Qbot samples were quarantined by CylancePROTECT immediately, preventing execution:
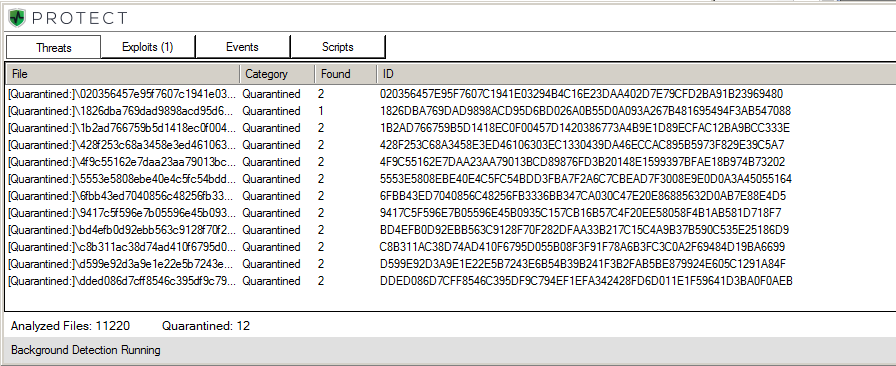
Figure 1: CylancePROTECT vs. Qbot. No contest.
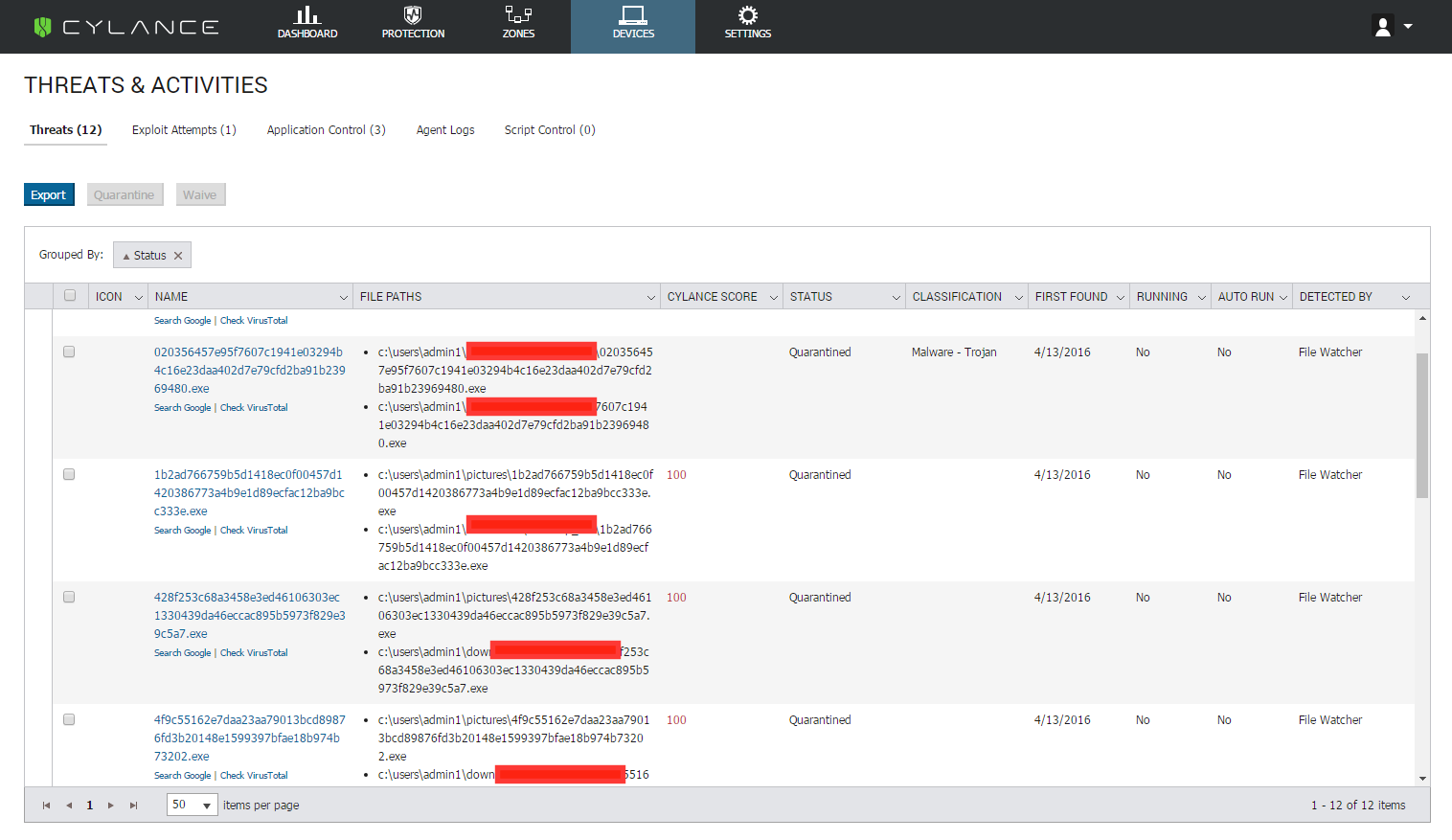
Figure 2: CylancePROTECT console view, showing the detection and quarantine of Qbot.
In summary, even the latest updates from the Qbot threat family are no match for CylancePROTECT.
Our research team has posted a video showing our preventative controls and mitigation in action. See us in action and believe the math!!!
Indicators of Compromise
The following are a subset of Qbot-related IOCs related to the samples analyzed for this specific post:
SHA256 Hashes:
020356457e95f7607c1941e03294b4c16e23daa402d7e79cfd2ba91b23969480
1154cb9fb9cf44a54aca9d3d689759ad6e89614a60c643ee3a5f496b52715b14
1826dba769dad9898acd95d6bd026a0b55d0a093a267b481695494f3ab547088
19bc15f4ff791d0ea11e9820781fe3375d09f79f7e8db504cf367bc9abd7e0dc
1b2ad766759b5d1418ec0f00457d1420386773a4b9e1d89ecfac12ba9bcc333e
428f253c68a3458e3ed46106303ec1330439da46eccac895b5973f829e39c5a7
4f9c55162e7daa23aa79013bcd89876fd3b20148e1599397bfae18b974b73202
5553e5808ebe40e4c5fc54bdd3fba7f2a6c7cbead7f3008e9e0d0a3a45055164
6fbb43ed7040856c48256fb3336bb347ca030c47e20e86885632d0ab7e88e4d5
9417c5f596e7b05596e45b0935c157cb16b57c4f20ee58058f4b1ab581d718f7
9490f5d06d46231ffd57d8244f1b63267b6da532ead148915782fa9662833b1a
9ea5655df078af9fd5f0a8288d7ca563ff9325ec71deceb6a2433693d86cd5e2
bd4efb0d92ebb563c9128f70f282dfaa33b217c15c4a9b37b590c535e25186d9
c8b311ac38d74ad410f6795d055b08f3f91f78a6b3fc3c0a2f69484d19ba6699
d599e92d3a9e1e22e5b7243e6b54b39b241f3b2fab5be879924e605c1291a84f
d8e26423aa8375190089f65f7013ea8d21217ffb25bcbf49fdd988ce8267575a
dded086d7cff8546c395df9c794ef1efa342428fd6d011e1f59641d3ba0f0aeb
eecdfa2fbfcd1b34c9461224f8cd46ed0b874409805f87a547a481a9d4909ec1
fb5fcf8a9b688fdbb8a982d1bf2adf2fb1d8cdd5b470bd0b22cbe8a7b09a132d
Digital Signatures:
Verified: Signed
Signing date: 3:33 AM 3/19/2015
Publisher: SWIFT Weather
Company: Irfan Skiljan
Description: IrfanView
Product: IrfanView
Prod version: 4.37
File version: 4.37
MachineType: 32-bit
Binary version: 4.3.7.0
Original name: i_view32.exe
Internal name: IrfanView
Copyright: Copyright © 2013 by Irfan Skiljan, Austria
Comments: IrfanView for Win9x, WinNT, Win2000, WinXP, Win2003, Vista, Win7, Win8
Entropy: 7.051
MD5: F878C04065C75592D9731C8F166A1236
SHA1: B775AEB6FDFB7D749A240EA389C2E37E0C6B85DA
PESHA1: 208B5E2BEAE8FE0B58BC31B6DE2CEEAE7752F45F
PE256: CDB3E1A4E430F82D4FB952A415418CE9276765088DB3036CFCBFF71C355C6727
SHA256: 9490F5D06D46231FFD57D8244F1B63267B6DA532EAD148915782FA9662833B1A
IMP: 3ED9D3768BDAF8028C489AFB67C5E0AC
Verified: Signed
Signing date: 1:53 PM 3/30/2015
Publisher: SWIFT Weather
Company: Sun Microsystems, Inc.
Description: Java(TM) Platform SE binary
Product: Java(TM) Platform SE 6 U31
Prod version: 6.0.310.5
File version: 6.0.310.5
MachineType: 32-bit
Binary version: 6.0.310.5
Original name: tnameserv.exe
Internal name: tnameserv
Copyright: Copyright © 2012
Comments: n/a
Entropy: 6.617
MD5: 504248EED4316B3A92B6F4AA25AF4097
SHA1: 4D656DF558363EA61DBF124BB7B9CE919FD17959
PESHA1: 4A3E85B0EB3BC8A67D56505BD4FADA092368062E
PE256: AA7F01173465F9FBD4B929338B9CB546955C4D62681DF9E85164CCDA844DC292
SHA256: 9EA5655DF078AF9FD5F0A8288D7CA563FF9325EC71DECEB6A2433693D86CD5E2
IMP: EE5B0AFB1D7C7EA8A045C60F0D3DB1DE
Verified: The digital signature of the object did not verify.
Link date: 4:52 AM 3/13/2015
Publisher: n/a
Company: Irfan Skiljan
Description: IrfanView
Product: IrfanView
Prod version: 4.37
File version: 4.37
MachineType: 32-bit
Binary version: 4.3.7.0
Original name: i_view32.exe
Internal name: IrfanView
Copyright: Copyright © 2013 by Irfan Skiljan, Austria
Comments: IrfanView for Win9x, WinNT, Win2000, WinXP, Win2003, Vista, Win7, Win8
Entropy: 6.898
MD5: 956832EAA429FFBCF5D72927813BB800
SHA1: 180A9C5390B2C5A0CFB02CBE25ACD4A77FC69698
PESHA1: A93C673F264458E3BDD2BF25FAD273E9D2C3CF7C
PE256: C1759628B77B64EA9EA4039039E8325D97E319AB1E70D6042968836B1B5D9DDC
SHA256: D8E26423AA8375190089F65F7013EA8D21217FFB25BCBF49FDD988CE8267575A
IMP: 34B9339402735B3015FF2D2D049D729E
Verified: Signed
Signing date: 4:48 AM 3/25/2015
Publisher: SWIFT Weather
Company: CHENGDU WEISHU TECHNOLOGY CO., LTD.
Description: Picture To Video Converter Application
Product: Picture To Video Converter Application
Prod version: 1, 1, 0, 0
File version: 1, 1, 0, 0
MachineType: 32-bit
Binary version: 1.1.0.0
Original name: pic2video.exe
Internal name: pic2video
Copyright: Copyright (C) 2007-2008 CHENGDU WEISHU TECHNOLOGY CO., LTD.
Comments: n/a
Entropy: 6.404
MD5: 71156A2A6076DB554436892B9E540E06
SHA1: E4EC005FF5A45C79E5E2FA7FC1D3B8A4B97C207F
PESHA1: CF7770B090EED414F68331EECBF16866DE9530C9
PE256: 579E222B183615127D83E712F6481A9FEE639193B1B12748CD4B42239921BE53
SHA256: FB5FCF8A9B688FDBB8A982D1BF2ADF2FB1D8CDD5B470BD0B22CBE8A7B09A132D
IMP: 9B0BB92D9B43400C0B7120C62F9156EB
Domains (C2 and call-out/function testing):
apxlrfuxlfhbcyfdxoce.org
tags.bkrtx.com
undrlryedwfkes.net
ksviuiqgpu.org
agjnydlrkluyxdueswm.org
huuebybyzitnjfih.org
kvjxyvzkygqnmvixjclp.info
evnffssblnzifztbj.org
sanjose.speedtest.comcast.net
stc-sjos-01.sys.comcast.net
boston.speedtest.comcast.net
hkeqznqsyetang.org
jacksonville.speedtest.comcast.net
fobeabcal.info
opuoybextdpdjviihpfhejg.org
houston.speedtest.comcast.net
wjqagrtill.org
vfcgvxdbnrqfqchitrcgj.com
ycuhdilyntwbawnjaujfinak.org
gkgiqjutaqvlmpminqeysycli.biz
bqcgcxcxbtb.info
lvjlezjytphkniwspzbllowsa.com
lkbyrknwtpuhduwqntfzd.org
qxlnrsxrsaodzyvdmd.com
dracwwfuopmziqvtnhuy.info
zezdehhemuzez.biz
yprazdskffxwtiuesq.biz
cdycvcrapugttcarliymg.org
mwncgezmtm.net
kfrqgwndfrnkccm.biz
dcwpvouketmuq.biz
cklpdidrvjoujyqxcclp.info
wzkvvnwvd.org
pdafxdsf.info
ghnorrrhhw.org
jnyqomkxtczlihdpzrocysquq.org
tcbqxkgaegznjdqlxllaj.com
dshuugdivpuacwiwlhzlkj.com
auqmgvweuatstbl.org
dwxkztbpntbyzyjae.org
xibitqqqpjdcgydy.com
udfloskikxswgmn.info
eyaugvfhugwwocg.org
rxosyypzgvwl.org
oxfklxxmyqpqxk.org
vmzdmuyopdjpdaiitelkgrgrn.org
xkvlvmjqihtokanbamcfwzk.org
wfrimetmb.net
uccebdzmkhe.net
jwxmeecbzpcm.org
rtdmxoqrvnpclzjxepci.biz
cdqykfgxpkjwvezxedeq.com
mddwapiwifsakevwgbkxg.net
ugatzjzpiqsqp.net
aguilfgq.com
nayusvehpyyaremifaw.net
mmqxjufvmofwaxgqboywtcc.org
qtnxelisxhob.org
mmjpdcipuacjczduhmzpvzi.net
ivntfgciayjqaydaestxjhusj.net
jastizqwovlyt.biz
tiryjusnfsdkwnv.com
rjcxwkcavrtwzrhjwvyxxqcvf.info
sirifgbgoxgk.org
kgtzmcocivzksolkfpipyjkcf.org
zjzxmgdxbbfxedolrryjq.biz
vtanqhti.com
kilnutoxcnbquwvhmblml.biz
naslaboauocjtkfdjuxrnemzh.info
bwwmtgrlwuyw.org
wcramuopsgfqhm.net
vfqabgyjufjk.info
ydaoxcmkmvbwjakpwczgqm.com
hmrfvmvrbmcvfqqkkwnekry.biz
ynepxhpgaddmgymnumoz.info
wpzuhabecasatijogwkr.net
txumdptwlqjya.net
fqsohcypjgtdjdszxymqij.org
ictocinuwasurvgnnyzor.biz
ertrofdoj.biz
gisktkcafrdkoeuowxw.org
rggerjwijhrmcgdn.org
cnrztabszkohzgcmlglx.com
axggducnhnzmcdmlqyubxrgf.com
fejkprosurgfugunv.info
mgygmgyw.info
gagyxqrc.info
jktzussyestjwx.net
dpqretyqqyfwwlevnafxif.info
yazhfhvkkehijilopgjea.com
rcmtxqrgutuaevj.net
odxsfaod.org
nrfndfqsidtfhbbgbwy.net
dvcuipjffmoxbbmdt.org
yoqtgpvfapv.biz
aeklgvuyvhwqrqvznlwclw.org
cdlqumiioqrvwlppunxovwrms.info
xldknontemtsxtvr.org
opoqicvdmwzedznvvtlzwu.net
zhphqifemoqyjnoiblh.org
nqrardktkh.net
ycfeepriklnncoqwrjed.biz
ilrqjskkcdofovm.net
anfoprwpaqawehwqimeqhjb.biz
cpjjubooafqic.biz
lcjrivfkwbfgsdcwi.net
jkjkbooycetcytzxva.org
ebknxkerfy.info
knryhuykxcagw.org
jmhsofzfa.biz
fyobetecrbcuyttbl.biz
bfegsuakfhegoxyadzcqf.info
ssufabqiprreoc.net
puphltsjvleajr.com
yjmmokwuavhgsbkogxwpissi.com
ugglgyorhlxvpgkluenua.net
zfxaetiwiqyanyohu.info
bfrvxptqgpnvg.com
cvzlmbun.org
afpnglbtnzrzupr.info
ytjmdcovsknlvdyvrjunop.biz
jxvfixnlumsr.org
thefzxkgfkkhlewlp.org
wsmymwdycdpkfsplvogt.net
jltjcvlfovgypkpfawjvt.com
tvqnwngagthdavbbw.com
opdegdorbxafizpoqxhlfr.biz
mkppkhjal.net
trewtqwpsiaebigdpodvnu.org
siqpwhwxrxru.org
azlxwbjnjiraqjhzpbkrifvl.info
njabuxdulgebcwtwzjylcn.net
aahuojhrcdaisdipvilbh.net
oydasssexhazrocfgtovlv.net
ednfjetgokmykx.net
pmqlhxiicbgwxz.org
tveysumigzbunqcejssmutjv.org
wpkoliguqggnuevvnzlrdl.org
vsazwrcssctsbzhvqcejnj.com
awauaqjgvlqotu.info
ralkrgzmu.info
mlkksnctehsioajwtgoylzrym.com
jgohpoaoykjl.com
slqhobocapvhdnm.info
dmppdbesnshrfzenbvpwkqk.info
whxmnlxppnksnrvnkav.net
ncpsgqwnwwcvcxmxiglaq.org
ipdliojsvqy.com
rnitriesathtm.biz
xacosayenxkmsiawbhl.org
exvkspiurcevthvjrfmdi.net
itnaosbgdstmfl.org
qcmcruymwfinbmc.com
haymvpcv.biz
flvgveznfiixazfkn.net
blgrlztjixgnjmdvcmhrbc.net
ikuubcteifoftsgpqzjyx.com
frfwzsvenmtwcmfxm.com
fibjbtyrlfkeqj.com
vylfytseutyzppemmcxzhzvk.biz
hfbktedica.biz
jksqcmdlnsozubtxotexszafj.org
uhsfyxmrbijhstba.biz
mddcyqapxbyjpsolxekihkub.org
cdqkfytvxbtkltrnjdbx.org
hqiuvvdajgspnifpuburyce.biz
yjvyeftosmpyzmsedjwahdgrs.info
rffzvfljvtsthkbdu.org
xilqzczljwufhvqgnp.info
idfvxaiedx.org
pvakkcbj.info
dhvkeuxmelktnxkiswnimug.net
embmcwfmolxcjibdndwmm.com
plzlpbperkax.biz
sgfubqqqbjqkawvdecezjaxm.org
evcfcicwqlnpojnwqum.org
qffmjgsoamfzwj.org
vucghraykaqrctaux.biz
gqfqavopztpv.org
fmfenmqowqgqltikso.com
fwqyshvisaze.org
ueqxwzcnjtsc.info
wzamzowmzcmbbxuz.net
skdprsroavxpupptm.com
zmckgjqmjomfucuu.org
seqwlfmo.info
xrvqtfzipthlpcllimxh.com
cymwgyfdfaebrsgoljnpdxzp.info
zsanwuwkv.net
ktzjhmxxwljttsiiestdox.net
rcubslryklaaneeyajsevfgen.com
cbvpcdhpnf.org
nyeyvudsnsyqzod.org
dbryotbxozqoiqanialgcjpid.info
ncahpftsrgsrckkqhio.biz
phbnbbctehcoxse.net
paelkvmv.info
xgebmgzpbjghxeruquaeqvcox.org
bndpdakfbedyqgtsuunsmu.biz
srbqbrgvxsavifpwl.com
veajrmvsbkto.info
szfqporhz.biz
gpnvivsjedteq.info
liwahrnohwurpdladmn.com
piniwokpxa.org

