News recently broke of a merger between two prominent banking malware families. Earlier in the month, Cylance began tracking what appeared to be Trojan samples sharing feature sets from both Gozi and Nymaim. At this time, we are aware of over twenty organizations that appear to have been specifically targeted by this new hybrid threat. Most of the victims are based in the United States, with a few outliers. The continued morphing of the code behind the threat is not expected to slow down.
Introducing GozNym
The Gozi family is regarded as one of the most successful and prolific financial malware platforms in malware history, with the first reports of infection dating back to 2007. Nymaim is not nearly as well established, with the first reports of infection by the malware dating from 2013. Nymaim’s hallmarks closely resemble those of ransomeware. Initial delivery occurs via malicious office document (.doc file). The original variants of Nymaim were of the ‘fake police warning’ variety. The malware locks up the victim’s computer and displays fake legal warnings purporting to be from the FBI, the police, Interpol etc., claiming that the victim had violated certain laws while using the Internet and threatening years of jail time unless certain ‘fines’ are paid.
The latest union between the two Trojans merges their codebases to produce a much more robust banking malware package (like Gozi ISFB), with better fluid and stealth persistence capabilities (like Nymaim). Some aspects of the initial dropper are also pulled from the Nymaim side.
It is important to note that while the Gozi ISFB source code has been previously leaked a few times over the years, that does not appear to be the case with Nymaim. At this time, presumably only the original malware authors behind Nymaim have access to that particular codebase, and therefore they are the only ones with the capability to add on additional modules or functionality, as with GozNym. Also, as recently as late 2015, there were important legal proceedings regarding the use and spread of Gozi. [1]
Live Demonstration: CylancePROTECT vs. GozNym
When these ‘new’ threats arise, it gives us another opportunity to show the power of Cylance’s machine learning approach and the capabilities inherent to using the power of artificial intelligence within CylancePROTECT.
Without previous analysis, CylancePROTECT was able to detect 100% of the GozNym variants we threw at it – watch our live demo video below.
Believe the math!!!
CylancePROTECT Screenshots
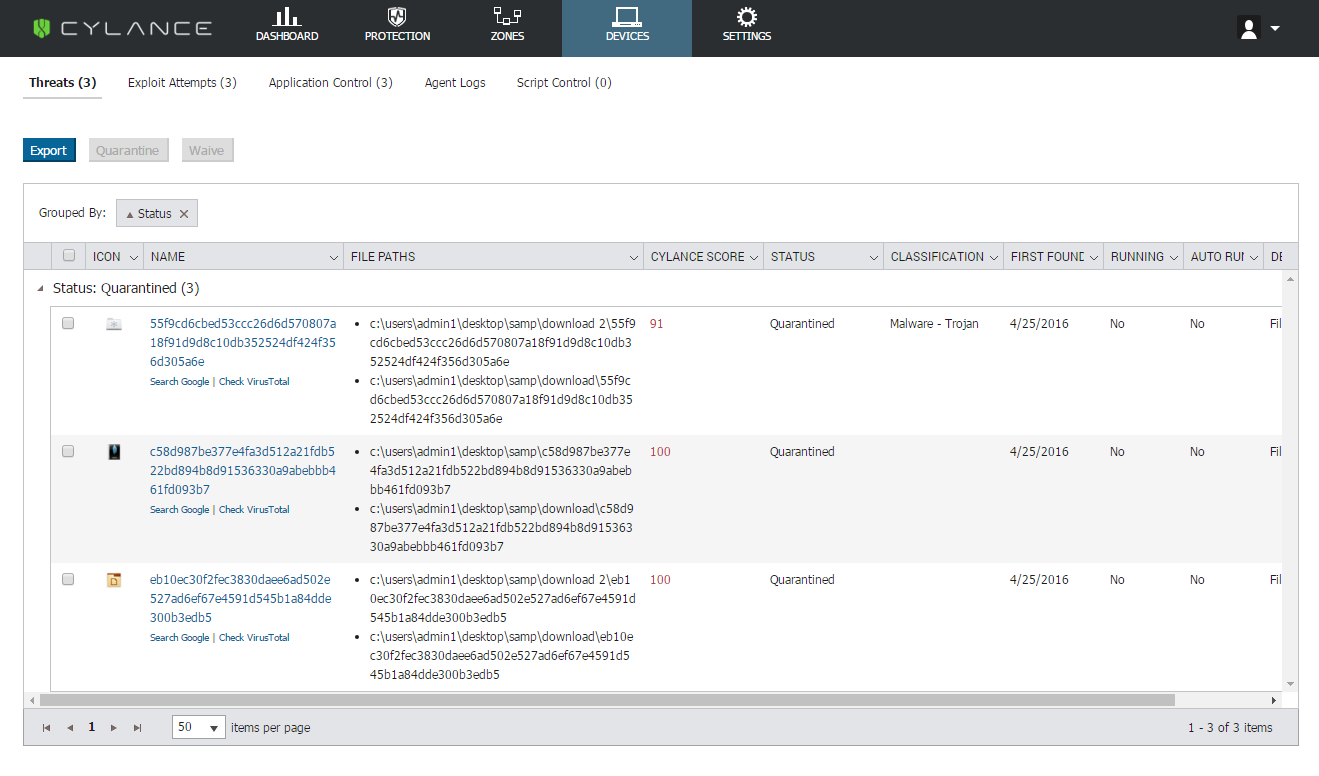
Figure 1: CylancePROTECT console view, showing detection and quarantine of GozNym
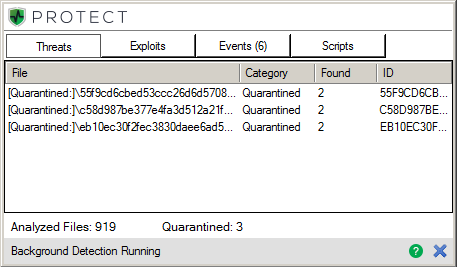
Figure 2: CylancePROTECT event window, showing pre-execution review and quarantine of three GozNym samples
Indicators of compromise
Samples (SHA256)
eb10ec30f2fec3830daee6ad502e527ad6ef67e4591d545b1a84dde300b3edb5
55f9cd6cbed53ccc26d6d570807a18f91d9d8c10db352524df424f356d305a6e
c58d987be377e4fa3d512a21fdb522bd894b8d91536330a9abebbb461fd093b7
Domains
carsi12(dot)com
mbcqjsuqsd(dot)com
kustitoop(dot)com
Debug Path Entries
F:\SinglePageViewer\warped\Honey\W.pdb
U:\Chown\version\passionate\NOP\Ad.pdb
[1] http://www.scmagazineuk.com/gozi-trojan-financial-web-injection-hacker-pleads-guilty/article/437201/

