Wouldn’t it be wonderful to receive an official-looking email from your company around April 15th about an unexpected tax refund? However, if you take the bait (as many people do) and open the attached ‘claims document’, a cybercriminal near you may be the one receiving the windfall. Tax-time is taken full advantage of by hackers each year in order to scam people into thinking they are being contacted by their own company about real financial matters, while in reality, the email contains a malicious attachment designed to covertly steal banking credentials and other financial information.
This particular threat is more effective than the usual run-of-the-mill phishing emails due to the campaign’s sophistication. Initial contact emails are typically written in perfect English, cleverly hint at a personal connection with the recipient, and may have a spoofed sender name – the attackers may even have the ability to make the email appear to come from the user’s own company. The hackers may use social engineering to grab attention, with subject lines containing words designed to elicit a knee-jerk emotional response from the victim, such as: Payment Details, Banking Notification, Sales Invoice, Court Appearance, Overdue Payment, Courier Notification, and so on.
However, if the user falls for the scam and tries to open the attached Microsoft® Word document to find out more details, the malware author wins. The attached document contains macros, which, if enabled by the user, unleashes a downloader onto their machine to deliver a malicious payload. In this threat summary, we’ll be taking a closer look at how a recent phishing campaign utilized the Donoff and Dridex families of malware and how to avoid becoming a victim.
Understanding Macro Malware
Macro-based malware is making a big comeback in recent years. A macro is basically a set of instructions that tell a piece of software (such as Microsoft Word or Excel) to perform a certain action. Macros can’t run without the user’s permission, so the end-goal of the cybercriminal is to entice the user to open the infected attachment via social engineering. A financing company chasing an unpaid invoice, a co-worker forwarding on a too-good-to-be-true resume for an open job position, or a promise of monetary gain such as an unclaimed tax refund are examples often seen in the wild.
When first introduced by Microsoft, macros would run automatically without first asking the user’s permission. This was a fantastic advantage for hackers, who could count on their malware executing immediately after the infected document was opened. Macro-based threats circulated by email enjoyed a brief spell of popularity in the late 90s. Microsoft soon disabled the automatic execution functionality of macros after this vulnerability came to light.
Cylance Research and Testing Summary
The Word document used in the cyberattack which sparked this investigation is a new variant not previously observed in the wild by the Cylance research team. The sample in question utilizes several advanced obfuscation techniques to accomplish its end goal, which is to steal credentials and personal information from the victim/host.
First Stage of Infection: Donoff
File name: Christina Luna.doc
MD5: 8b86bd2ee1d2e34b44a872272d3b0ebe
Donoff is a type of malware known as a downloader. It uses macros to exploit Microsoft Word to download a malicious payload. To begin this investigation, we looked at a sample named ‘Christina Luna.doc’, a fake subpoena Word document requesting that the user appear and testify in a hearing or trial at a civil action. The document contained the malicious Donoff macro.
During testing and analysis by our research team, Donoff behaved in a strikingly clever way. It used macros to execute a set of interrogatory commands and identify the fact that it was being run in a virtual machine. Normally, this would have been a very straightforward analysis of the commands contained within the macro. However, in this instance, the commands were obfuscated in such a way that reverse engineering and deobfuscating these functions became very challenging.
In addition to the macro obfuscation, the Donoff malware had the ability to check whether any security analysis tools such as Wireshark, ProcMon or Suricata were present in the environment. If the malware identified that any of these analysis tools were running, the Command and Control (C2) server was not contacted to download the malicious payload. If, however, the malware determined that it was on a bare metal machine and no analysis tools were running, it would reach out to hxxp://sellerie-western[dot]com for its malicious payload, which it named ‘word.exe’ or ‘KMWOW64.exe’. In this campaign, Donoff’s payload was a piece of malware called Dridex, a virulent banking trojan.
Second Stage of Infection: Dridex
Dridex is classified as information stealer malware and is designed to steal end user credentials and the personal information of all users on the machine it infects. This malware is well known and has been observed in many recent attack campaigns.
Upon execution, the Dridex malware will monitor the user’s machine for any logins to a specific set of sites, which are usually social media and banking related. When one of these sites is visited, Dridex will perform HTML injection actions such as form-grabbing, screen shots and site injections, to harvest credentials.
Third Stage: Command and Control (C2) Communications
File name: KMWOW64.exe
Md5: 44b067f36efbc17e9b64dfebd2cb9530
Upon successful compromise, Dridex will ‘phone home’ to its C2 servers. The goal of this communication is to exfiltrate stolen credentials and other system information gathered. Additional capabilities such as downloading remote administration and other malicious tools have been identified as well.
After the exploit and execution phases completed successfully, the sample we looked at communicated outbound to sellerie‐western[dot]com. An additional domain was detected (stats.point-web[dot]fr) in the code, but no communication attempts were observed during our analysis. Both of these domains were previously seen resolving to the IP address: 178.32.162.187.
Protecting Your Enterprise Against Macro-Based Threats
As cybercriminals become increasingly more sophisticated, a healthy dose of common sense is a good start in keeping yourself and your organization protected against infection by malware such as Donoff and Dridex. So take the time to educate yourself, your employees and IT administrators on a consistent basis about new and emerging threats.
As a starting point, always exercise caution when opening email attachments from unfamiliar senders. If you receive any unexpected financial or legal news via email, such as notice of tax refunds, court appearances or unexpected payments, take a few minutes to verify with the source whether the email is authentic - even those from known senders, as email aliases can be easily spoofed. Don’t be afraid to call the company in question directly or email a trusted department contact to check that the email is real. Never hit ‘Reply To’ in the suspect email.
To protect your enterprise endpoints against macro-based threats, a strong company email security policy is essential to block each link in a potential malware attack chain.
Here are some first good steps to take:
• Ensure that macros are not enabled when viewing documents on your machines.
• Switch the default setting for macro security on all Microsoft Office products to High. Contrary to popular belief, you don’t need to enable macros at all in order to view the contents of a document.
• Monitor for unusual pings from internal company computers to IP addresses such as 1.1.2.2. or 2.2.1.1. This can indicate an infection.
• Make sure your organization’s email programs do not auto-load graphics or open and display attached pictures.
• Set the company email system to automatically block email attachments from unknown senders.
• Instruct your employees to take great care to verify the authenticity of the sender when opening unexpected attachments with the .doc or .xls extensions, particularly those seemingly from HR or Finance.
CylancePROTECT® vs. Donoff and Dridex
If you utilize CylancePROTECT, your organization will automatically be protected from phishing campaigns like those utilized by Donoff and Dridex. CylancePROTECT blocks both Donoff and Dridex pre-execution, even when no Internet connection is available. Cylance customers can sleep well at night knowing they are protected both on and offline from emerging threats.
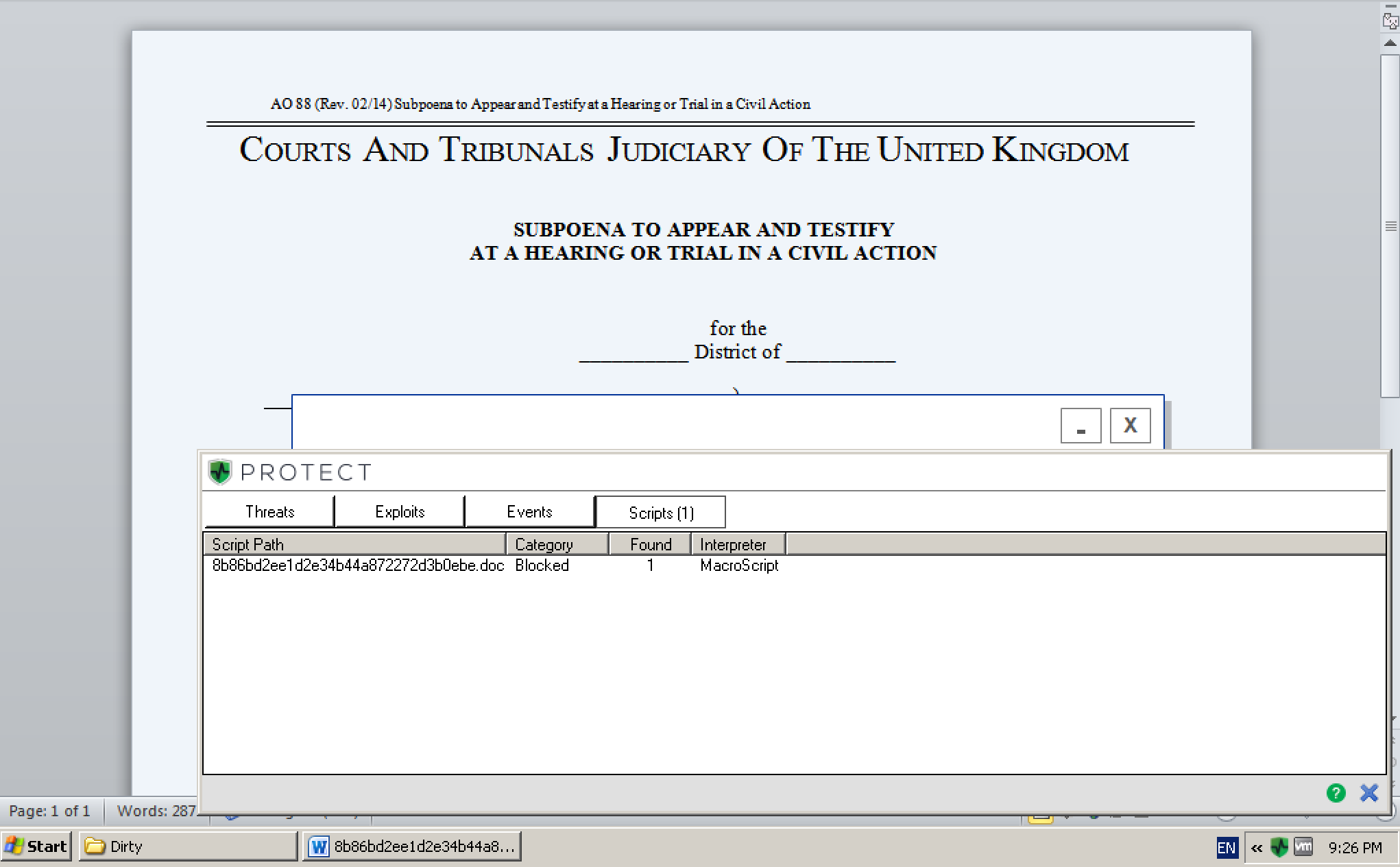
Figure 1: Malicious ‘Christian Luna.doc’ sample MacroScript detected and blocked by CylancePROTECT
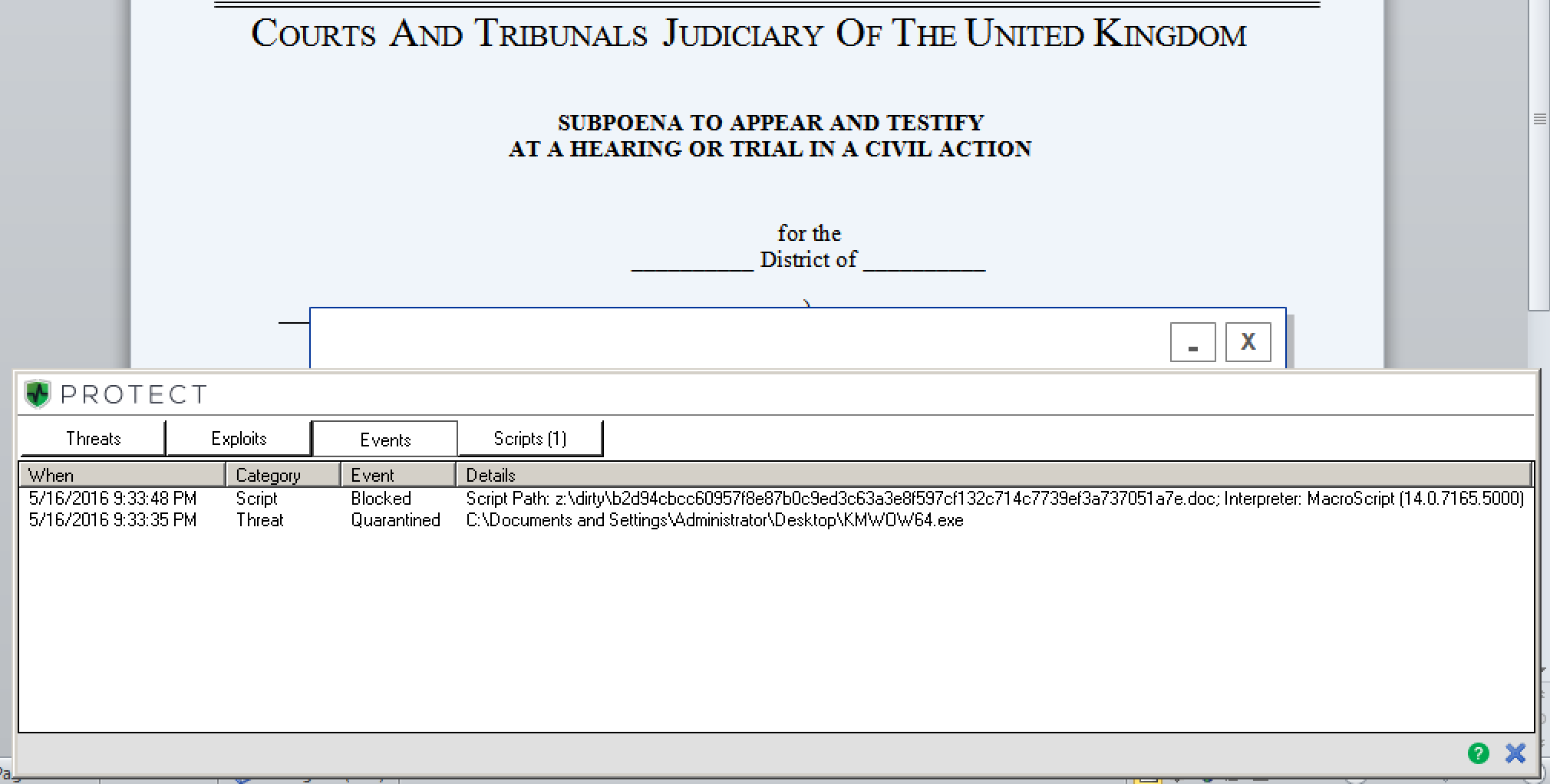
Figure 2: Donoff’s macro-based script blocked and the .exe file quarantined pre-execution by CylancePROTECT
Additional IOC’s*
Initial:
103.245.153.151:4033
103.245.153.65:4033
217.64.100.34:4033
45.127.92.175:40443
C2 nodes:
149.241.234.103:8443
165.120.141.131:8443
186.202.116.206:443
196.210.53.59:8443
203.151.94.214:443
210.65.11.155:443
27.131.149.102:443
68.169.148.133:8443
68.178.61.18:8443
70.57.247.38:8443
71.177.37.250:8443
72.79.199.65:8443
72.9.14.159:8443
74.92.81.105:8443
79.67.174.241:8443
81.136.142.29:8443
81.155.179.166:8443
86.164.57.192:8443
86.172.87.135:8443
86.19.148.86:8443
87.232.39.203:8443
88.98.84.148:8443
90.215.192.242:8443
90.217.24.12:8443
96.11.166.102:8443
Believe the math!
Convinced that the next generation of endpoint security is right for your organization? Contact a Cylance expert to get started!
* IOCs pulled from Open Source Intelligence.

