In April 2016, a hyper-aware, obsessively picky, and intelligently stealthy trojan started making its way into the ether. ‘Furtim’ translates to ‘stealth’ in Latin, and aims to steal victims’ credentials. Furtim thoroughly evades not only traditional AV controls and security products, but sandbox and Virtual Machine (VM) environments as well.
Furtim’s targeted paranoia seems calculated to defy the research and security industries. It first scans the potential host machine for any sign that it is being watched or monitored. If it discovers it is being run in a test environment, or if it detects the presence of any one of over 400 security products, it immediately aborts its own installation.
By preventing or inhibiting its own execution in these simulated environments, Furtim makes typical research tasks like reverse-engineering, static and dynamic analysis, and isolated detonation exceedingly difficult. This then increases the time-to-solution; hosts are delayed in receiving signature or rule updates from their security vendors, and the malware authors triumph.
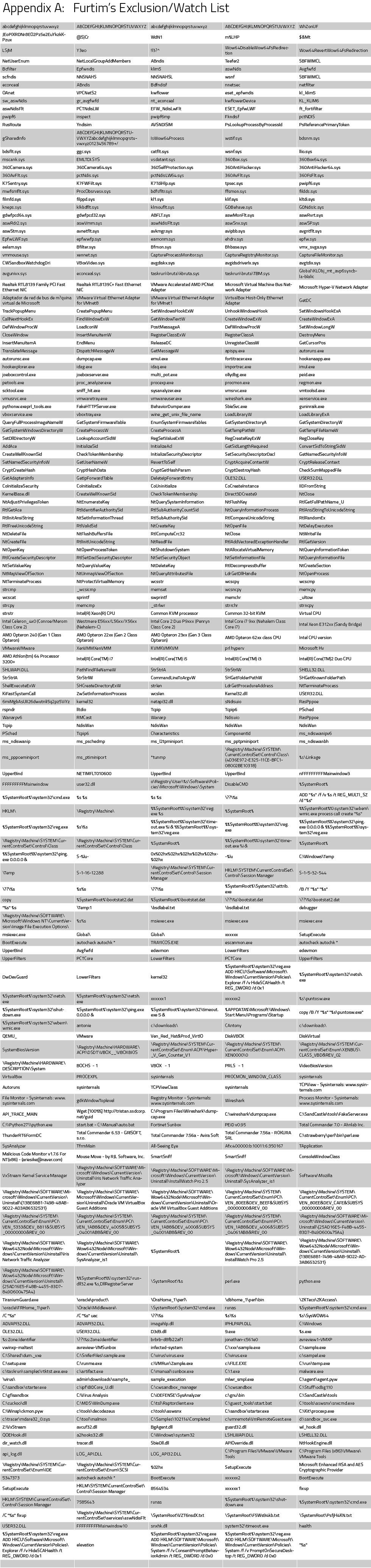
The meticulously long blacklist Furtim adheres to covers the prohibition of specific processes, DNS and other network requests aimed at security vendors, and file and script read/write operations.
Furtim’s extracted blacklist is included as an appendix table at the end of this post.
The Three Stages of Furtim
Cylance’s research team analyzed a sample of Furtim. It seems that the malware has three distinct payloads. The malware first deposits a dropper, which serves to open a backdoor on the victim’s machine in order to acquire and assist execution of future payloads or secondary binaries.
The initial payload is a low power config module which disables Hibernation or Sleep modes. This ensures that the user’s machine stays on in order to maintain the connection with Furtim’s server. Next comes a well-known credential stealer (Pony Loader) which targets sensitive personal information such as stored passwords, browser history and the credentials involved in accessing FTP file servers, which may then be used to help it move and spread within an organization. Lastly, comes a third binary, which we are still analyzing.
The victim machine must be rebooted for the infection to run to completion. At that point, it configures itself for startup persistence via the Windows registry. Additional system configuration controls are also implemented. The task manager and the command-line are made unavailable to the victim to prevent them from killing malicious processes. It also blocks users from manually rebooting or accessing a list of 250+ cybersecurity websites in search of technical help. Various logging and notification mechanisms are disabled as well such as pop-up notifications, further adding to Furtim’s cloak of secrecy.
Detection: CylancePROTECT vs. Furtim
Most AV solutions rely on frequent signature updates and thus require an online connection in order to stay effective against malware. CylancePROTECT does not rely on updates and it does not require an Internet connection in order to run, making it very effective against threats such as these. By utilizing the power of AI and machine learning to protect the user against cyberthreats, it is able to defend the user against stealth malware like Furtim - which operates by cutting off its host’s access to infosec websites, including AV vendors.
We tested our artificial intelligence based technology CylancePROTECT against a collection of Furtim samples:
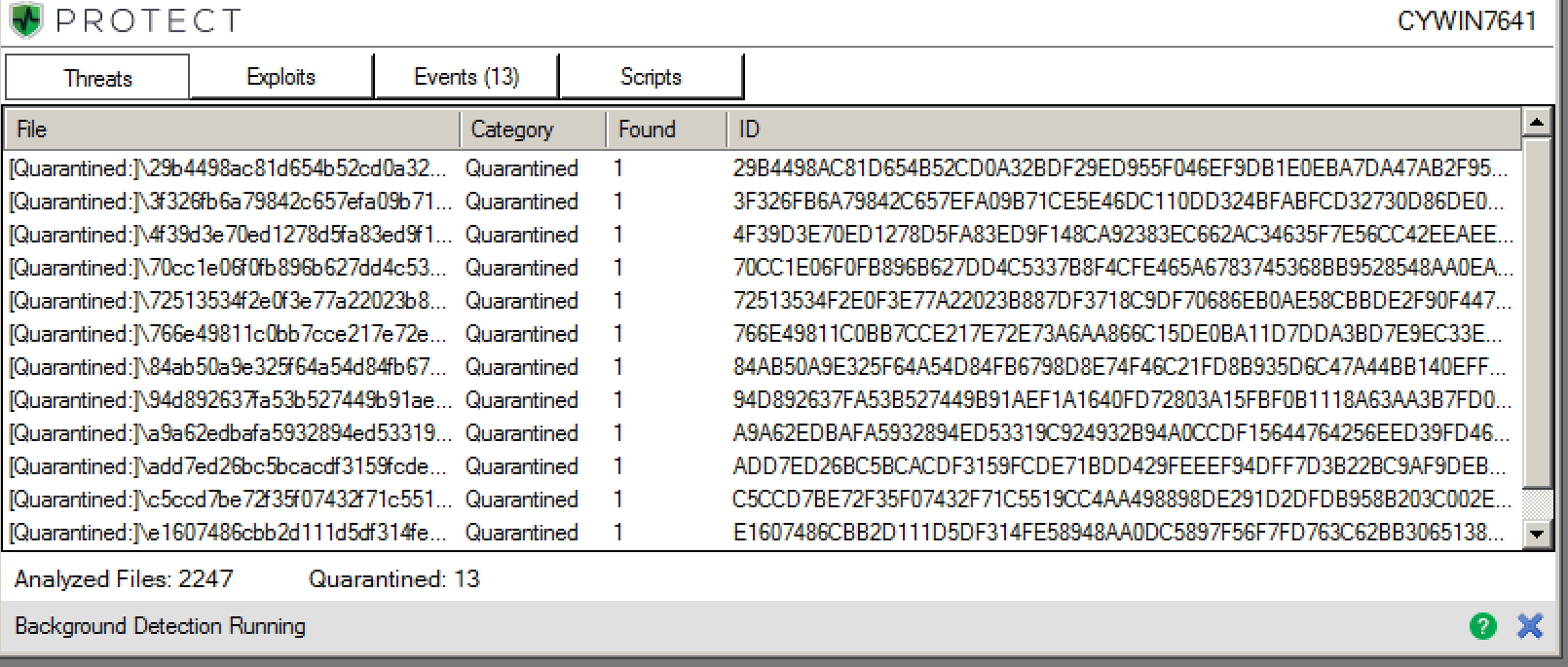
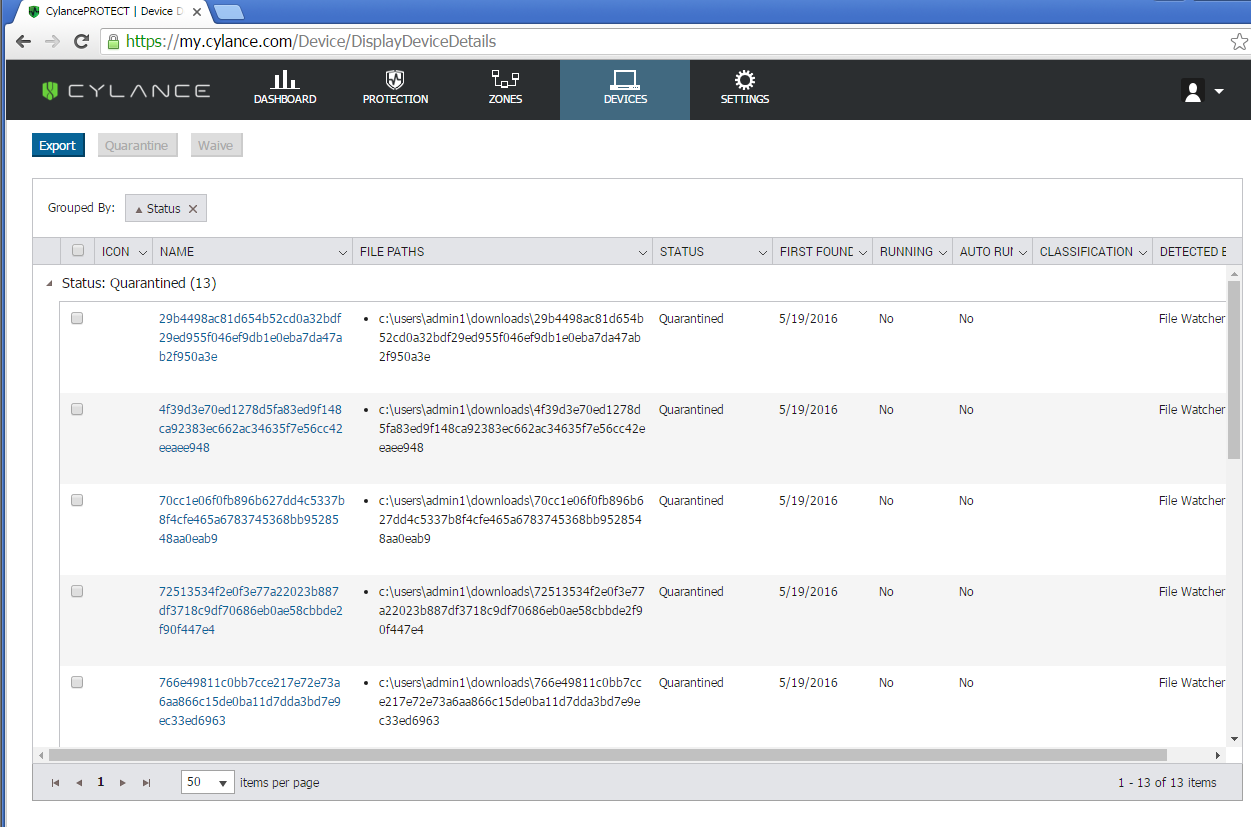
Figure 1: CylancePROTECT detected and quarantined the sample Furtim binaries
Figure 2: CylancePROTECT Threats & Activities tab open to show more detail on the quarantined threat
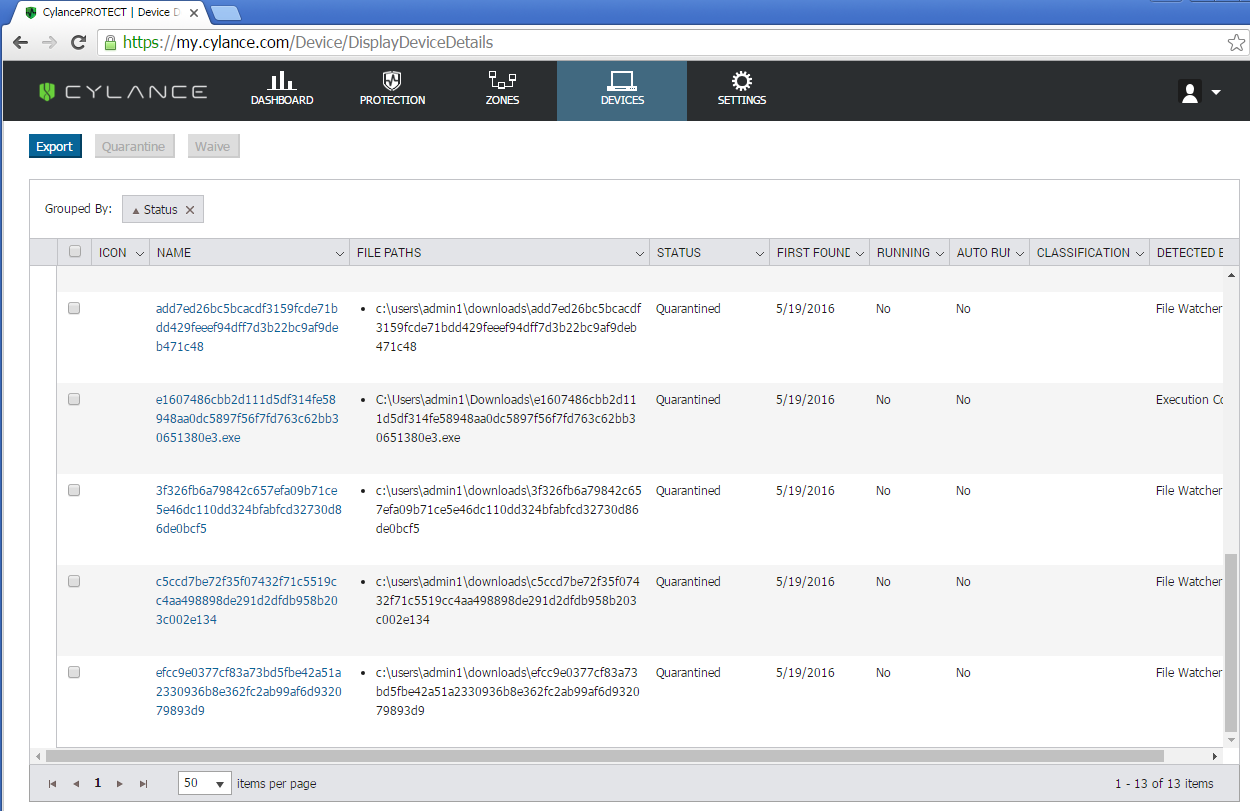
Figure 3: CylancePROTECT dashboard showing the quarantined Furtim binaries
Our Research team has created a short video showing the effectiveness of CylancePROTECT vs. Furtim:
Indicators of Compromise (IOCs) – SHA256 Hashes
3F326FB6A79842C657EFA09B71CE5E46DC110DD324BFABFCD32730D86DE0BCF5
4F39D3E70ED1278D5FA83ED9F148CA92383EC662AC34635F7E56CC42EEAEE948
29B4498AC81D654B52CD0A32BDF29ED955F046EF9DB1E0EBA7DA47AB2F950A3E
84AB50A9E325F64A54D84FB6798D8E74F46C21FD8B935D6C47A44BB140EFFAD9
72513534F2E0F3E77A22023B887DF3718C9DF70686EB0AE58CBBDE2F90F447E4
A9A62EDBAFA5932894ED53319C924932B94A0CCDF15644764256EED39FD46D86
D1DC9B2905264DA34DC97D6C005810FBCC99BE1A6B4B41F883BB179DBCACBA6E
E1607486CBB2D111D5DF314FE58948AA0DC5897F56F7FD763C62BB30651380E3
EFCC9E0377CF83A73BD5FBE42A51A2330936B8E362FC2AB99AF6D932079893D9
ADD7ED26BC5BCACDF3159FCDE71BDD429FEEEF94DFF7D3B22BC9AF9DEB471C48
70CC1E06F0FB896B627DD4C5337B8F4CFE465A6783745368BB9528548AA0EAB9
94D892637FA53B527449B91AEF1A1640FD72803A15FBF0B1118A63AA3B7FD049
766E49811C0BB7CCE217E72E73A6AA866C15DE0BA11D7DDA3BD7E9EC33ED6963
C5CCD7BE72F35F07432F71C5519CC4AA498898DE291D2DFDB958B203C002E134
DA5471323B95F1FF79E9ABF0BF842453C317E6ED37C55361466C6D358660B5E5
Believe the Math!