To fully understand the origins and scope of the CryptXXX ransomware trojan family, one must begin with TeslaCrypt. In early 2015, the TeslaCrypt ransomware family emerged. A subset of the earliest TeslaCrypt campaigns specifically targeted the videogame-playing population by encrypting files related to 40+ top games, such as World of Warcraft, Diablo and Call of Duty. Hard-earned files such as those used by saved games, maps and mods were all encrypted upon infection.
TeslaCrypt’s payment processing, requested ransom amounts, and timer control remained largely static throughout the life of the family. Generally, victims would be required to pay $500.00 USD for the decryption of their game-related files, to be paid within 50 or 100 hours of receiving notice of encryption. Payment was required to be made in BTC (bitcoin).
However, multiple revisions of TeslaCrypt were observed in the wild, with improvements to the encryption scheme and mechanism or enhancements to evasion being the driving factors behind the updates.
Decrypting the CryptXXX Ransomware Family
It did not take long for the security industry to fully defang the TeslaCrypt family. Each revision to the ransomware by the malware authors was swiftly met with utilities created by security professionals to decrypt affected files, saving the victims from having to pay the ransom. Ultimately, the malware authors themselves brought the TeslaCrypt family to a dramatic end by publicly releasing a universal master decryption key.
Fast-forward to April 2016, and we have CryptXXX rising from the ashes of TeslaCrypt. Enterprising cybercriminals, wishing to remain consistently profitable, quickly adopted CryptXXX. Authored by the team behind Bedep and Reveton, CryptXXX caught our attention via its staging and distribution via the infamous Angler Exploit Kit (AEK), which is used to facilitate high-volume drive-by downloads of malware from infected websites.
However, the AEK and Bedep combination is not exclusive to the recent CryptXXX campaigns. In late 2014, Bedep was delivered in a ‘fileless’ manner by way of AEK via compromised websites and malicious advertisements.
CryptXXX has been particularly prolific and highly visible in recent months. Every day it is possible to observe the rotation of new decryption sites, each dedicated to specific infections:
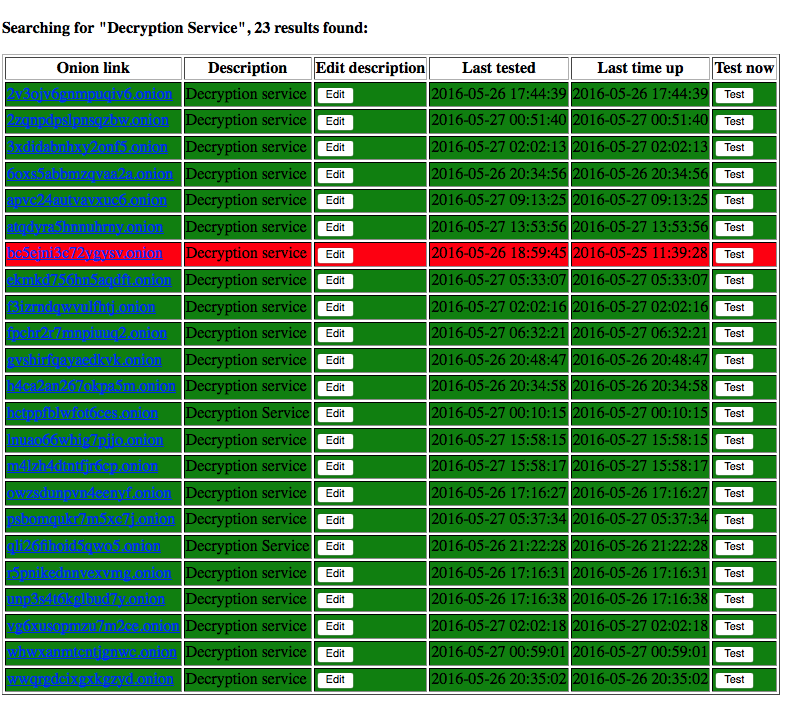
Figure 1: CryptXXX Decryption Sites/URLS 1
Similar to TeslaCrypt, the CryptXXX family was quick to update and evolve during its short lifespan. By late May 2016, CryptXXX 3.0 had arrived, the primary goal of which was to continue to circumvent ‘decrypt-for-free’ tools being distributed by security vendors and independent researchers. Multiple CryptXXX campaigns were covered in the media in recent months; including a compromise of the major French production company and cinema chain Pathé.
CryptXXX: Under the Hood
The CryptXXX family encrypts data files via RSA-4096. After encryption, files will be appended with the ‘.crypt’ extension. Some variants have been observed attempting to steal/exfiltrate data from the victim’s machine, in addition to standard encryption duties. Targeted data ranges from locally stored credentials to local bitcoin wallet information.
CryptXXX employs various methods of analysis evasion. Multiple ‘sleep’ routines, coupled with virtual machine (VM) detection and processor interrogation are used to delay and potentially inhibit standard analysis techniques.
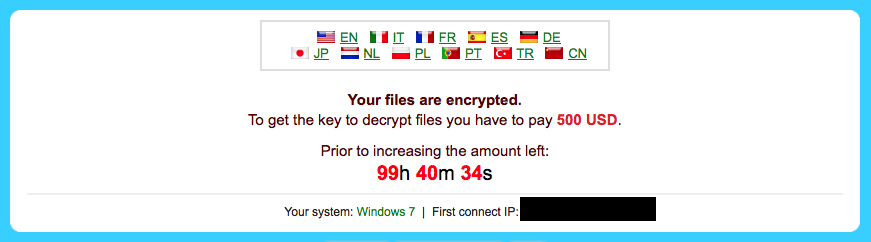
Post-infection, victims are instructed via desktop wallpaper modifications and dropped text documents on how to access the TOR-based payment service. Details on acquiring bitcoin and properly submitting payment are provided as well.
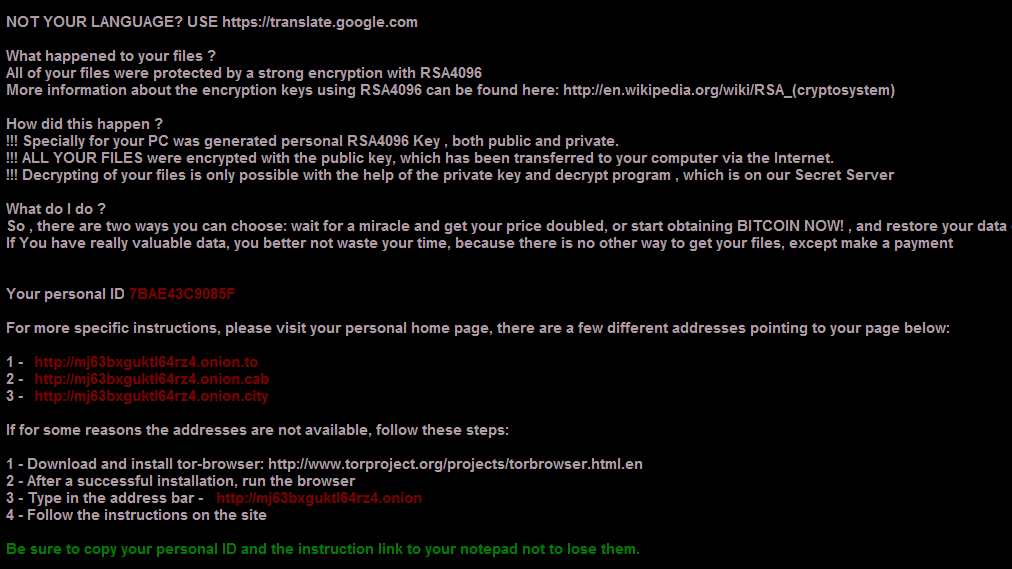
Figure 2: CryptXXX Post-Infection Screen 1
Figure 3: CryptXXX Post-Infection Screen 2
Figure 4: CryptXXX Post-Infection Screen 3
Figure 5: CryptXXX Post-Infection Screen 4
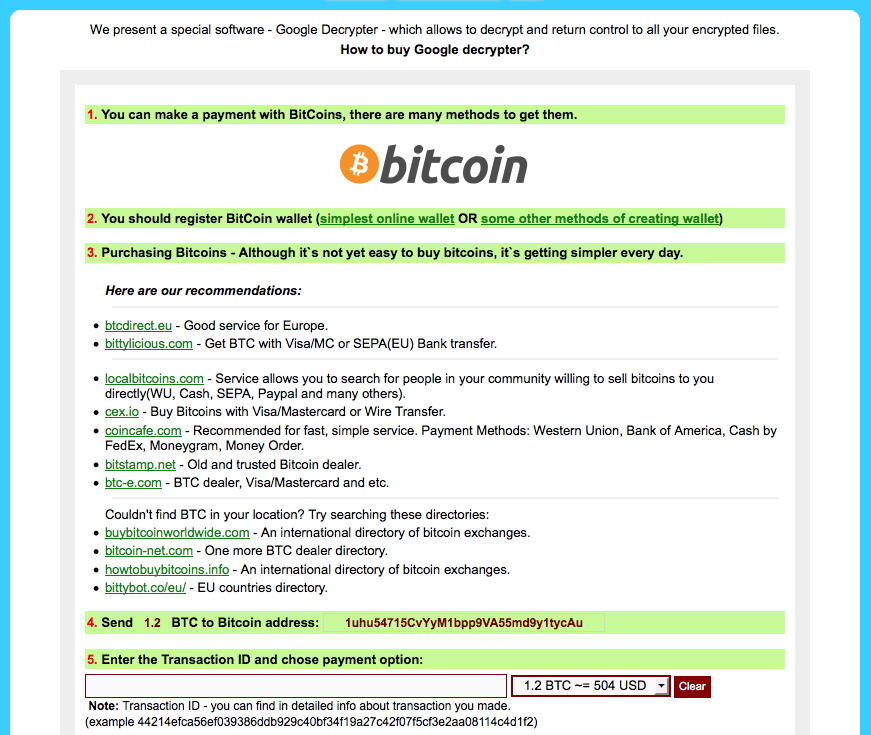
Figure 6: CryptXXX Post-Infection Screen 5
CylancePROTECT vs. CryptXXX
We pulled over 700 CryptXXX samples, along with a handful of Bedep and Reveton binaries, and verified CylancePROTECT’s ability to detect and prevent the execution of these samples.
Every single sample was intercepted with ease, pre-execution. CryptXXX, as well as the related families of Bedep and Reveton, are no match for the mathematical approach leveraged by CylancePROTECT.
The same, however, cannot be said for the more traditional, signature-based antivirus (AV) technologies. When reviewing submission to various multi-engine AV testing services, the first few submissions averaged an 11/57 detection ratio[1].
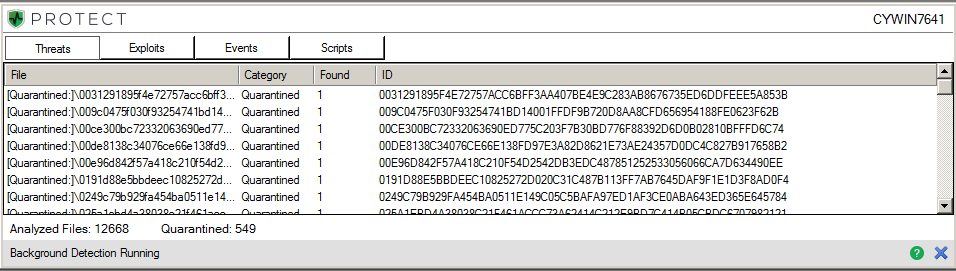
Figure 7: CylancePROTECT Agent Detecting and Quarantining the Malicious CryptXXX Samples, Pre-execution
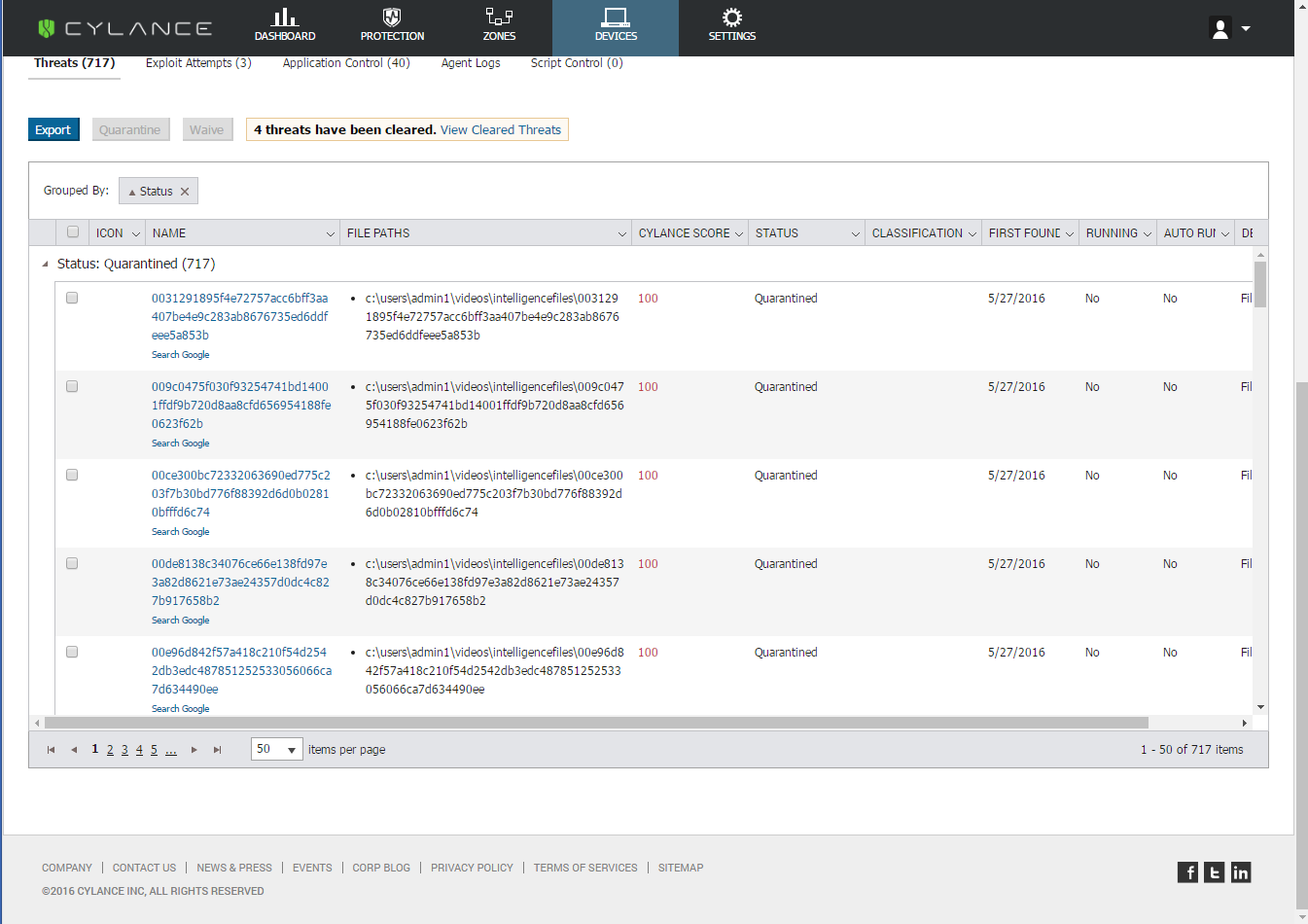
Figure 8: CylancePROTECT Console Verifying That All 714 of the 714 CryptXXX, Bedep and Reveton Samples Were Detected and Quarantined
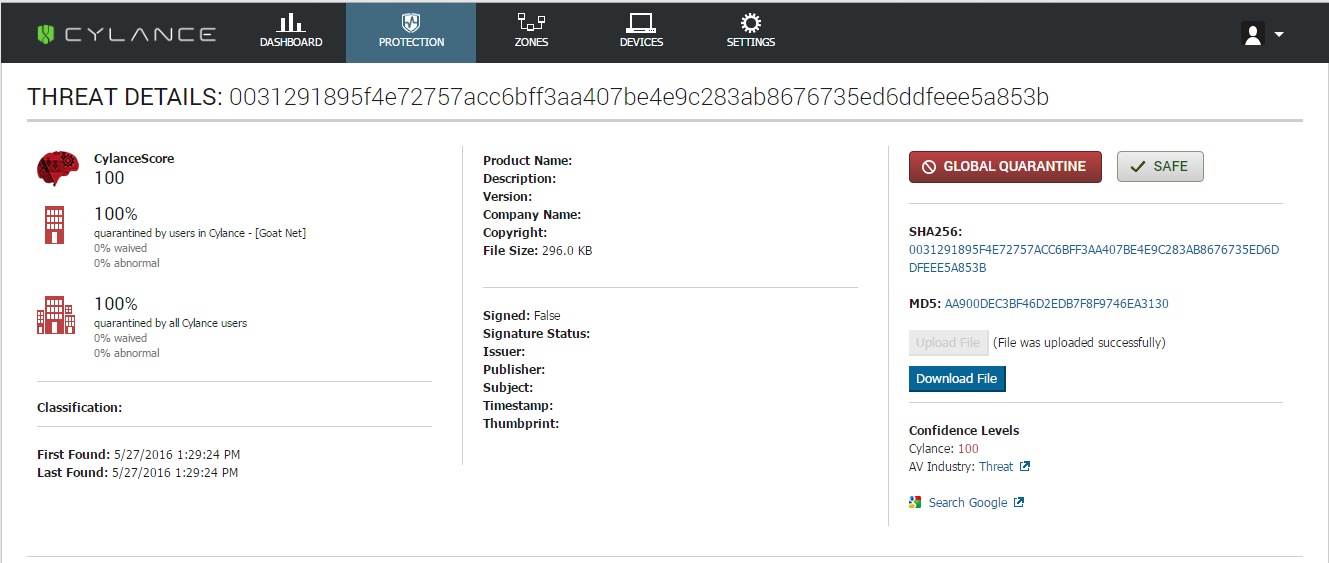
Figure 9: CylancePROTECT Protection Dashboard, Showing a Cylance Score of 100% (Global Quarantine) For a CryptXXX Sample
Believe the math!
Indicators Of Compromise (IOCs)
SHA256 Hashes:
Convinced that the next generation of endpoint security is right for your organization? Contact a Cylance expert to get started!
[1] 11 vendors detecting out of 57

