In June 2016, JTB Corp, a major Japanese travel agency, announced it had experienced a massive data leak after their servers were compromised. Initial reports indicate that 7.93 million people who used JTB Corp. to book travel may have had their personal booking data exposed, a revelation that sent shockwaves of alarm through Japan.
The leaked data contains sensitive personal information including customers' names, home addresses and email addresses. Passport details were also leaked in the attack, including over 4,300 valid passport numbers, revealed local media outlet Japan Times.
JTB Corp., headquartered in Tokyo, is one of the largest travel agencies in the world, employing over 26,000 people. The official announcement revealed that the source of the attack was a targeted email phishing campaign: a company employee opened a Microsoft® Word document email attachment infected with a particularly stealthy trojan known as PlugX, which spread to infiltrate the company’s data server. The document in question purported to be a travel booking request from All Nippon Airways Co.
JTB President Hiroyuki Takahashi has since apologized for the breach, which may also affect JTB customers who used the firm’s online booking portal. The case spotlights the urgent need for companies that store large quantities of sensitive customer information to review and strengthen their cybersecurity policies and practices. This should include cybersecurity awareness training for all employees, who are often the most overlooked link in the security chain.
PlugX Comes Out to Play
Here’s the shocking thing: PlugX, sometimes referred to as Korplug, is not a new threat. However, the recent attacks against JTB have put this family of malware back under the spotlight. PlugX and associated trojans such as Elirks (an information stealer) have undergone years of evolution, employing different and novel techniques over time, thereby ensuring high levels of stealth, persistence, and detective/preventative control evasion.
That much being said, we have observed that traditional signature-based antivirus (AV) technologies still have issues detecting these ‘older’ malware families. With years of easily accessible samples freely available for research and study, one has to wonder exactly what is stopping traditional AV vendors from taking steps to upgrade the functionality of their products in order to prevent the execution of these threats.
In this write-up, we will focus specifically on the PlugX family and some of the recent techniques used by the malware authors to establish a foothold on the targeted endpoints. We must be very clear to point out that the samples highlighted and analyzed in this blog post are not the exact PlugX samples directly associated with the JTB incident. However, current intelligence indicates that very similar PlugX files and techniques were used in the actual attack.
This is, therefore, a prime opportunity to revisit this threat family, and to take a closer look at some specific behaviors associated with the PlugX family, as well as highlight the power of Cylance’s artificial intelligence-based technology to prevent these threats from ever occurring.
Meet PlugX – a RAT in Sheep’s Clothing
PlugX is a multi-function remote access trojan (RAT) with a history going back to at least 2012. The use of PlugX is not exclusive to any one adversarial group, nor is it unique to any specific region. Over the years, it has been observed as a component of many notable attacks, including Operation Poisoned Handover, Operation Poisoned Hurricane, ClassicWind, Clandestine Fox and many, many more.
In the latest travel agency attacks, reports indicate that the PlugX malware came bundled with, or programmed to identify the presence of, many legitimate applications. Recent examples include Intel’s CPUMonitor, Dell’s Toad for Oracle packages, and Microsoft’s System Information utility. The malware also comes with a PlugX DLL and a high entropy binary that contains shellcode. It leverages the legitimate executables to side-load PlugX into the executable.
DLL side-loading takes advantage of vulnerable executables that do not specify imported DLL locations during runtime. When this happens, the threat actor can trick the OSLoader into loading a malicious DLL in place of the original DLL and storing the newly crafted DLL in the same root directory as the executable. When this happens, the DLL will then get imported into the executable.
In recent attacks, the PlugX trojan was reportedly embedded into weaponized Microsoft Word documents, which were then attached to spear-phish emails. The trojan will often generate a new, unique copy of the malicious document to further avoid detection. Spearphishing is a popular technique commonly used to gain access to high-value corporate and financial networks, such as in the case of the recent SWIFT banking attacks.
PlugX: Under the Hood
PlugX is typically configured through a builder. The builder contains different settings that the threat actor can use, including specifying a legitimate executable, backdoor connections, services and scheduled events. These options in the PlugX builder allow the threat actor to specify a legitimate application which it then uses to gain a foothold on the victim’s system.
In the example below, we show versions of the PlugX builder using CPUMonitor and the Operating System Information Utility (msinfo32):
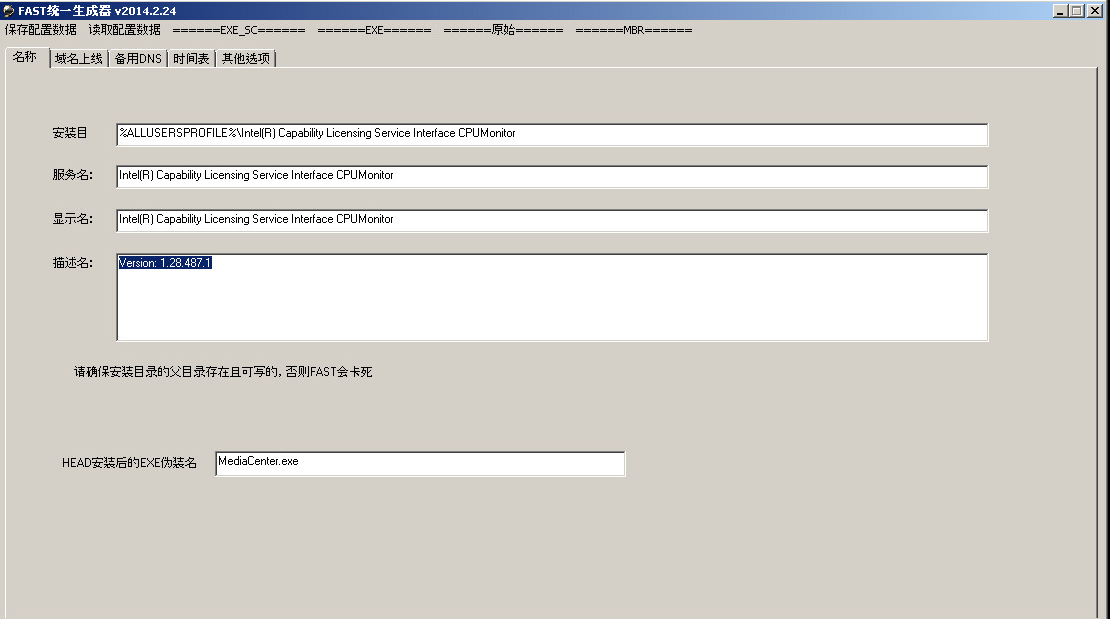
Figure 1: PlugX Builder Showing Intel's CPU Monitor Being Used as a Legitimate Executable
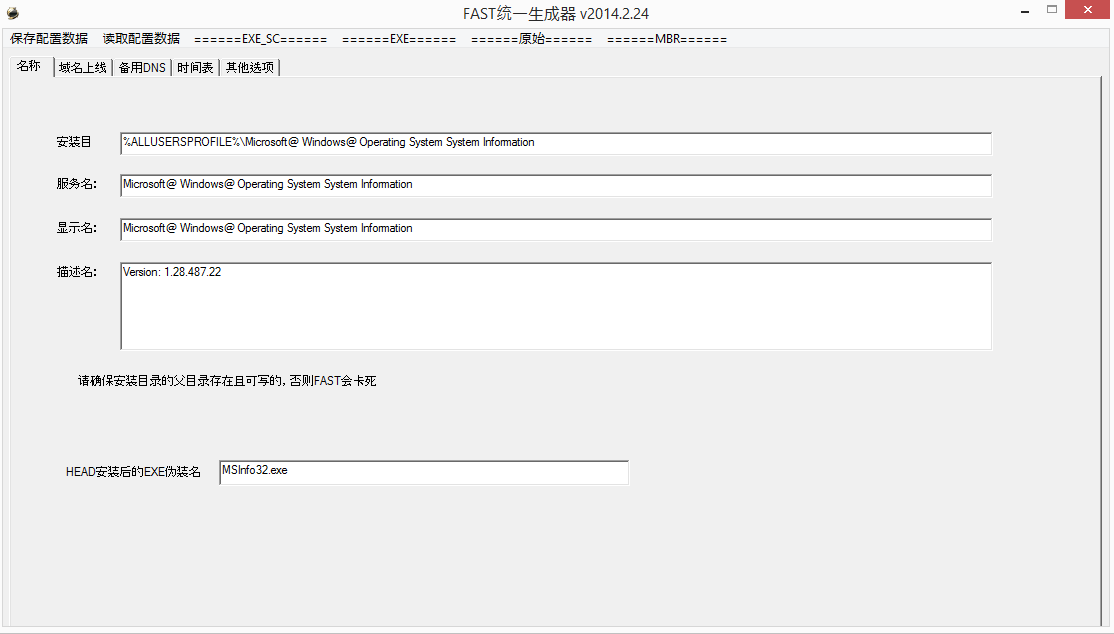
Figure 2: PlugX Builder Showing the Operating System Information Utility (msinfo32) Being Used as a Legitimate Executable
Additional configuration options in the PlugX builder application are shown below:
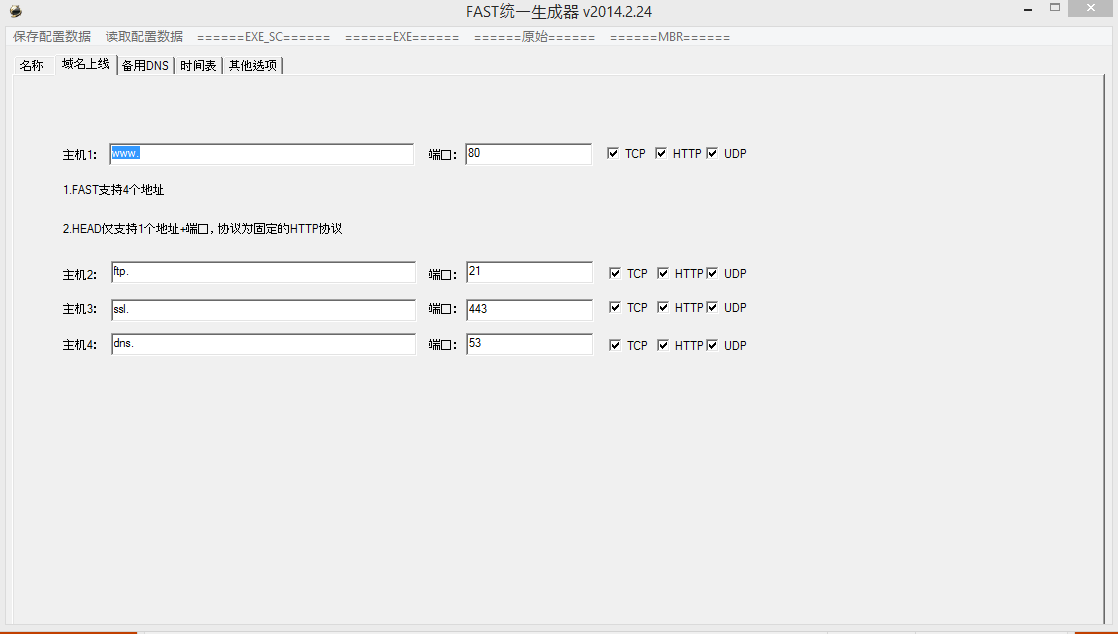
Figure 3: PlugX Rogue/ DNS Server Options
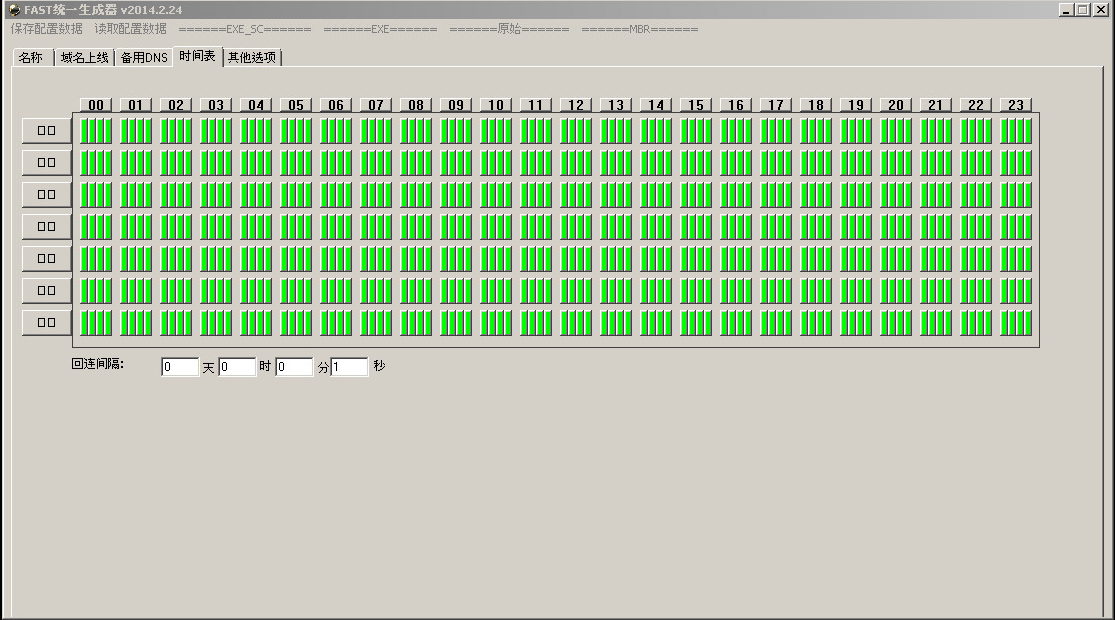
Figure 4: PlugX Event Scheduling Options
PlugX Sample Analysis
When specifically analyzing the sample (8abcbfe0f44726f898c1c288c4a5d3a84f1aa11a60156e28d125fffbf0b81ce6) we observed the following behavior: PlugX injects code into process "C:\Windows\SysWOW64\svchost.exe” and elevates its access by utilizing the following kernel mode functions:
SeShutdownPrivilege
SeIncreaseQuotaPrivilege
SeCreateTokenPrivilege
SeAssignPrimaryTokenPrivilege
SeLockMemoryPrivilege
SeMachineAccountPrivilege
PlugX then injects code into msiexec.exe, drops a malicious Microsoft Word document into the victim’s AppData\Local\Temp folder, and then attempts to launch/open the Word document.
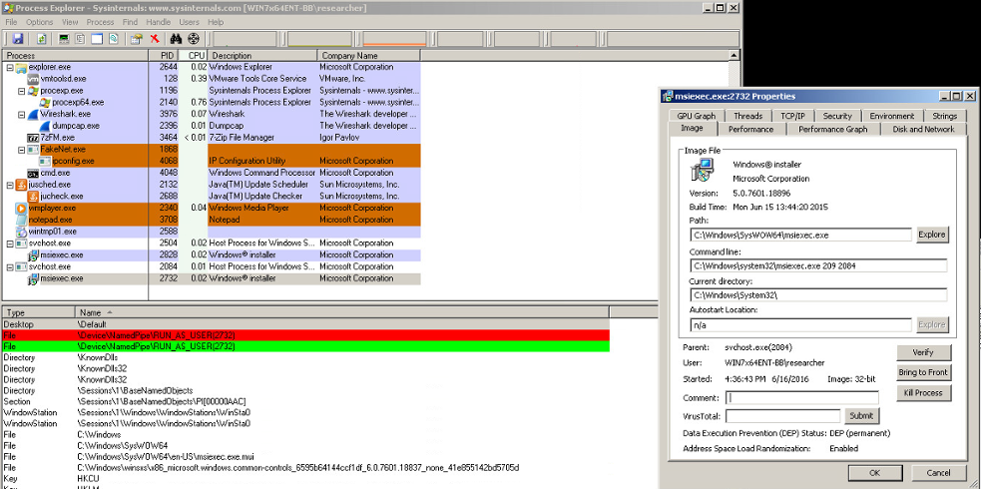
Figure 5: PlugX Malicious Code Injection Process Witnessed Via Process Explorer
Figure 6: Malicious Word Document Dropped Into Victim's Temp Folder by PlugX
PlugX profiles the victims and the infected computer system by collecting the user name and computer name. Then it uses a pipe for inter-process communication to pilfer intellectual property, credentials, etc.
This particular sample calls out to and interacts with the following IP address:
202.181.24.147
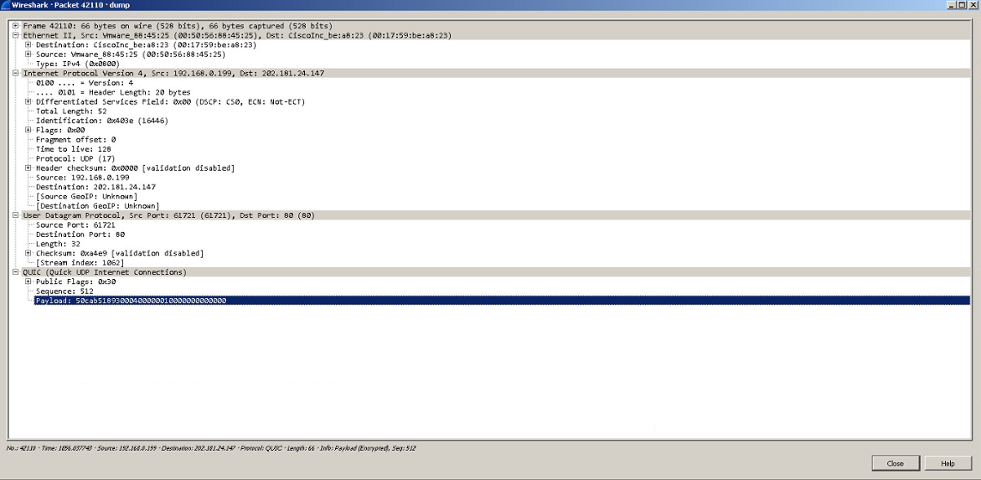
Figure 7: PlugX on the Rampage... Viewed Via Wireshark (Network Protocol Analyzer)
CylancePROTECT vs. PlugX
Cylance’s research team tested an assortment of PlugX binaries - collected over the last year - against CylancePROTECT and our current mathematical models. Our artificially intelligent, math-based technology was able to stop and prevent execution on 100% of all tested samples of PlugX.
This is definitely not the case when reviewing the detection history of these same binaries across traditional, signature-based AV technologies. Given the financial and business impacts of a PlugX-related attack, no business or corporation can afford to let these threats go undetected.
Results as seen in the CylancePROTECT console (and local agent) are shown below.
-Believe the math!!!
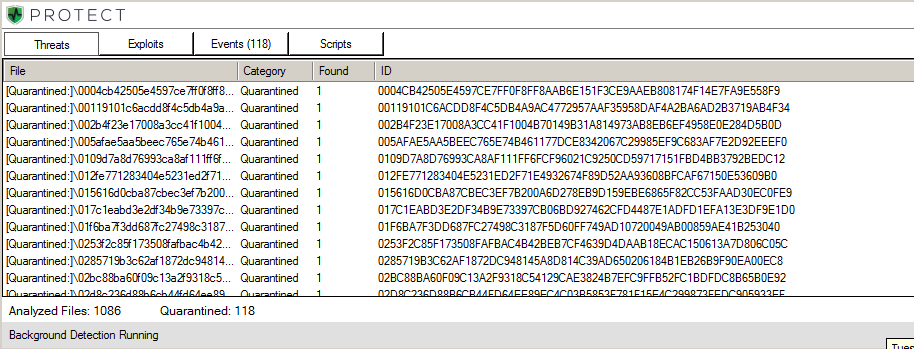
Figure 8: CylancePROTECT Console Showing the Detection of 118 Out of 118 Malicious PlugX Samples
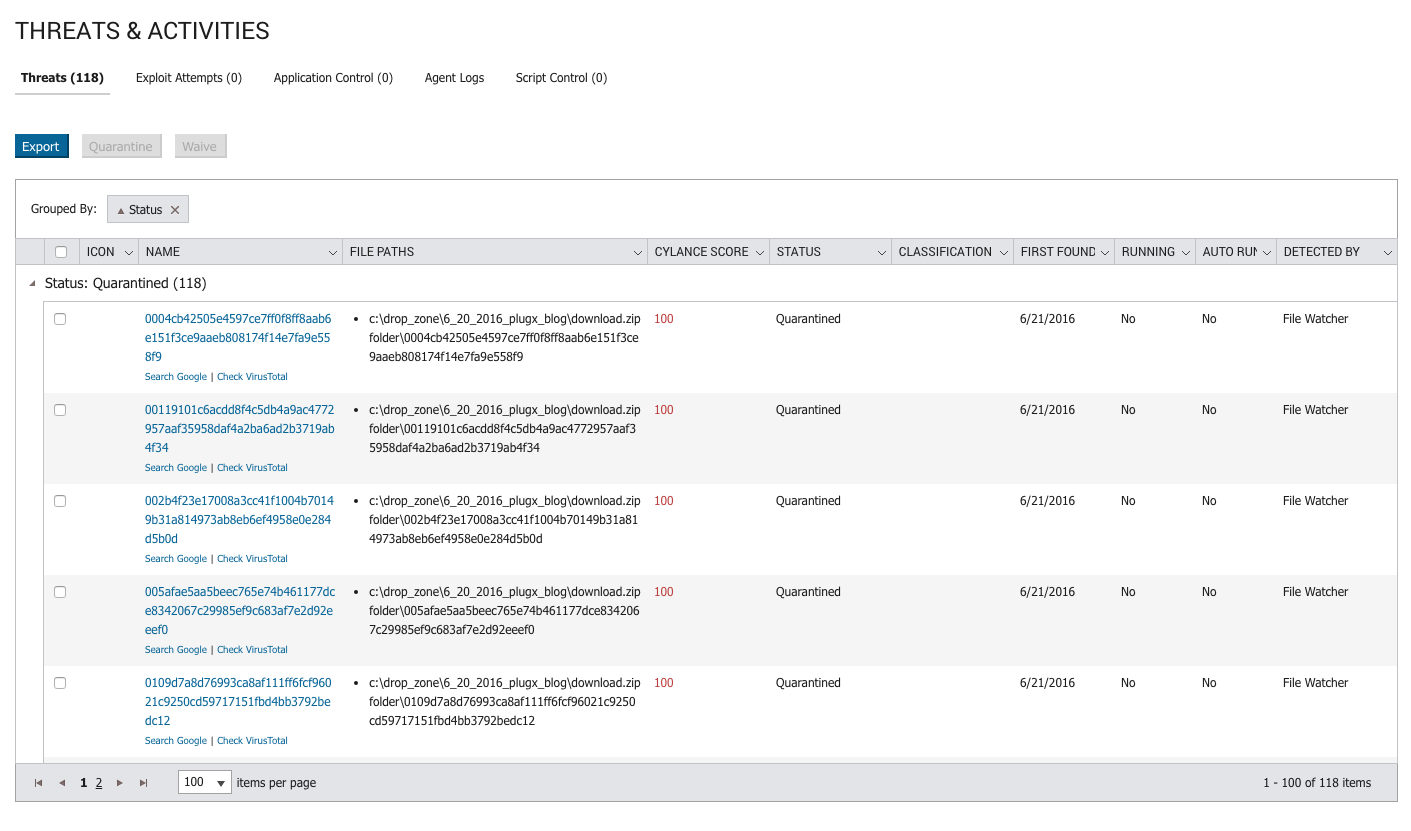
Figure 9: CylancePROTECT Threats Tab Showing 118 out of 118 PlugX samples Quarintined, Pre-Execution
Our threat research team recently posted a video showing our technology in action against PlugX:
VIDEO: CylancePROTECT vs. PlugX
Indicators of Compromise (IOCs)
SHA256 Hashes
f776bcf605ade06f0f99dab8ea846ca8789971e58695cb6f448ea65f6eaa586e
b69215b1cb5452a514d6d34fb93d27b2ac0c6f001ad7982b3470aedc55b56a3c
169ea7ebfd960207c97dc5000dde13a6657019ec3ef327f9b5861181b20aa1c0
067bbb48870273f6ce48e85c0ee4cd9b745a7ea13875fb1f2c31faf2219cda88
065cc420648591b5b93306cc94e510a30dfd79b1a5be975df0fcf803d3246bdb
063e5dcdeeb45a81e3c93e37e72f2c68c58d08462ce101a61ba635498343bdee
05dfd15282401cbc557167fc9bc268cf766a766ba42f188ae82f9742eb91d446
05d72a63588cbf2d376f6a86a0b87ad7f4c8812e6db8009ef3bf03706b186713
899281c665ba9bb467a01cf0d25db9406a06e5e13c2cdd122d784a4a06bdfff8
318bc1028af7ce0cf01317a5171080e2d2f1171e22137b23c0cfa6365d16ba2b
044718d2b607bdef073b893086a2c50d36fbe8d1607b3d5409cdddabb543a896
3d512aa68ed6a0708bb091f136806011127c7c8cf3bb4e64087336034e636eb8
040bfc9cf212a9a6ff48fccbc409290ef27f3bf875fefaeb9e7142a20905e4f4
038a0a4684248631bf27fadb4603216c338216ce2331f69bb1fe46cd0039ab0a
40011d18865225a9350785dd3ae8bc9795c840c592806692eb1bcf3fea88e181
0314e12462813723e4b6ce806ba41d16e5d4b6bbf5eeb3830e196ad0e979be26
02d8c236d88b6cb44fd64ee89ec4c03b5853f781f15e4c299873fedc905933ef
0253f2c85f173508fafbac4b42beb7cf4639d4daab18ecac150613a7d806c05c
01f6ba7f3dd687fc27498c3187f5d60ff749ad10720049ab00859ae41b253040
017c1eabd3e2df34b9e73397cb06bd927462cfd4487e1adfd1efa13e3df9e1d0
015616d0cba87cbec3ef7b200a6d278eb9d159ebe6865f82cc53faad30ec0fe9
012fe771283404e5231ed2f71e4932674f89d52aa93608bfcaf67150e53609b0
0109d7a8d76993ca8af111ff6fcf96021c9250cd59717151fbd4bb3792bedc12
2b034b457d0e2a321199ffc5e40acdb2ddb011e2add88fc0f4e7133792ea25a5
a37f04b726a376fa812a3d04f5ec31c5eb163c16ba04c63580bf52992592a748
005afae5aa5beec765e74b461177dce8342067c29985ef9c683af7e2d92eeef0
002b4f23e17008a3cc41f1004b70149b31a814973ab8eb6ef4958e0e284d5b0d
0004cb42505e4597ce7ff0f8ff8aab6e151f3ce9aaeb808174f14e7fa9e558f9
5dff1e086c5191a0bd7ac13466b7a81a87e99e51968df2f32570eb031c537ab4
0bca46c6cc32ec675785d24621902f983b3328aa762144533a484cfe8f299b05
87eda6d855d462f17daf23e5afc80bc1fdaa9a9fb36c8efdedce3eb83072a3d9
fe27376d24d367e649b5177acb6f099cafbd11917aa31fe5eb1e677a93ee9b15
1818ee0712108b86dbfd08b18dfa3e0d8e64cc6fc1f1cdd79990271cb3e4e8ba
7a1f17f316096b954fe275997cdc6cf682601f57bf26d8e11fb872f721e9207d
bf9a7f7b91d3ebe0eed2b2ddd661922784505e623be3e2cc142ffa639cd48c76
710326804b78ccd2782abc16354e389f0e36ba9474ebdced17337a13082ac12f
00119101c6acdd8f4c5db4a9ac4772957aaf35958daf4a2ba6ad2b3719ab4f34
8c0047d5f89170fe2e8993ba71e6e7fcd15fe3c2b8ab37213b79bfba07ed1c69
a920bac566a50b5f95dc0128fde9637962515edf7fb1dad54c7142671e44627e
3d36e9abbfe2c3784cf08621b9246b82f1127f988f42424320df5b244258fef3
8abcbfe0f44726f898c1c288c4a5d3a84f1aa11a60156e28d125fffbf0b81ce6
79186a6a00be05a4f0f6fa484a19b4e4a6df4e5445ff3f88638e32f1420432d0
ec6b2a727600ffd9e9d790eaea1a51a42a683a8ecb7bb0efdbd04a815f5d5af6
c437465db42268332543fbf6fd6a560ca010f19e0fd56562fb83fb704824b371
2e3a2cea18bb9cd7a65df2a9c972ee1d4553acd67925b5d42aff24d5a61adae3
3526690a6f799bf033c05b0d21bc176228b986bd42a5836e376d6731e18ab6d1
da5917981f599b33db6640684d332893157792e904ebeb7b429b914c77f8198a
61231cc9d0ec4726633a4af762e7ef30f2466e4d32d9ce9a151481602d05b5e6
96c172465bc040b1f892953783f3eadd83d4e0002647c38967fa67de615ff405
f7d81d22a2ae5eaa59dc9ada3952ef4db43e8a6d2110f83bfd72faacf8f4e203
d261d6daa8f4b187b64a3a099b637803a181bb9cb7c0ddf006d4f6d91d348975
3a9ab623c8a0a9f6c65e108e83c90da7620d2d6b22192c857556117587d0d038
987384231546ae5bf4c6b40be4d7f79c7f95c4cb53f6f6dbce239826975bee6c
6ce13ca6e981c6a5d5ba8a69d9c8ccddfcae236aba9b8c875be9cf67682e5284
c214dd926f5cc7536df6f195bb0770354414991c09e7921f07c87ad66865b161
9a6db53bccd607f8bd6bf2f60cc468ccadda81260d39d3bc07dc7522c20f8fea
7cdea920b598191ad0ad7d79429f6c14d646b00b1b8fb3fac48a1197aa2e5475
884beb161843b7642b066805c603ed24f7e983837aa1bfccb22878999b115917
dab84f20bc67294db31b2f32cb379f51e38a59b23c19e6135ef97abe92d86803
23d5c4ba6494a03d6a3f030cae4dc4222333078480581eb85af148dc64904654
c5483a8c886ba468dc9233f8fb719e3a5566874d41178bc4e9528083fe944b48
becec7a1a009a9e1b5dacb21447f2cdd50d0cbcd5252604d3b70a5ce1cf16dec
34ed12229b08d17c0ceb35f8a682ce116a94f62b5e4c9a2d813262524144b284
b361582f6d0213d3513fb085d0d978fefc28824b435403463e0dbf110399a807
2d1dfe79097134dac74704caf1632b9ab11089b78144d53fc7820ce7fa97824b
7487669a06a6f65f1794c4a2c4c40875889fde14d4aa53a728f859702501f3f8
550174889eff16b9339e3d4108a92d40fca688cb0210f0cc09ebd755ce868ae8
973e966acf727c4b720de01a5bf7bfbe4cdcedb49e2ad936ec3078c8f3fb0312
b9f1acf143ebf86eb41ee963c7a3e6d37ae8ec014b413ada90d58c86acace413
f28f06340ffdde58981d604ee9677525bb82f92f7f3c95d642693d823a461323
62368f02634b78826a98ce0810c956f8c35b7e8708868580cc6ffe948b00e734
9780bfd41046cb938c262dfea45f949ac7c6d146037f3dc7025314ba89737ef2
32f0d2becec6a8a4c2dd5b0b95d02cca534735316ec46d5dc9736c9a74e988fa
2e984371f32ba6b04c65fe9a2c311e7e494b652f08d330796d4aa619a968b382
a8a212f095505422f0b9de8b96a10669ed7aa9dad92281c191636fd71f01f9ae
2b338f50b3a26c63e78f63db4d1666764c4cb36cee1643667655298901d04805
db6e3f38e48db688d9d2a3d3e162805ab69195ac428cc5cd73335b48e2c573f5
b4884094dc75bdd0e41ad43a56ed49a585823d9df47c57a03eacea3f7b2a2ddb
aed8cdb9300b1fd693a57ed68cb18776f222cc132a4833aa8d61a92742728b0e
63bbd0931baaef4b6b1062ad8983be064166be428cbb9c6bbc87783ce0821c88
ecb8846d41c5ae4461db2b9858a825aa3321ade8970a6944fffe96a3afc90f6e
3aa59457eff992663da0d4b677d64d66dff392db7a259fa2d29e78d3917c5672
e9d23c70cecdabee69d57616a63ea65a8c2bce1fe4cc31cda27310b63cf71e5d
183a377e446bca57e450c5516687f6f3444cc344b09df03f3f697c401a061dee
ee9307dfa325337644f23973fe25c20acc5d683221b370c24bc1dee0ad7351ac
f98344eeee04cea47b8f405c466063b379a5c8f66b1e950e2c4f0fec645d3fd4
0f6516c51902a9ef5b259e27704ff625fff1a8fb91697387c0511f12d7373aca
66cf3da2904fe2510d54f35ac906d6e8812c98d290f7e21236bff54c640ce901
f708839763369794311a6a95a790a1ac1d7eaf180935283e83d2b315f373d12d
404a3a48e0b18afb0e2c70b4baf22831cd57b501e4ea0bc7d4ff8d2dbd43ad42
1f883c1d14cfb16dfe652cdb11ccf87f107cc1ed0540b4bb7bb4d14b4947ebf5
0fd134c72b21ea8264c2ba07d3cd6e72af3d835777ee7894774688e4026fad52
73b1a85a8dbb72475c710afa7e3da444a88b214f029dd4d0dd7cf54c47d0a92e
75568a088d93ec2b2a22329920b607c08b70da04b3bafc9a82db1fd26b293d56
e1f5420c2e9604e4ec0b925a70af859c013fcfd18b318a851cd5d23303f6e10f
4f90212c399d0a11c19f389c368628185c2f6baa8618d2167153df555cccba3e
1d77e7612299967555af423ce5886ca3ecbcfac374b43feac87c6eb63c3b8835
4a75ac1ef6b9264fb902a996dd97d992819e76cab9f61a3601d2bc0ee73e37d9
ec1daecac0c0c28873262b126f1c6c56fdeec16e41cf0688d4d7bbcaf83eab1d
e27160d6fc96f0034f9dd309bb6b9c719f71ef6325a49659ee8d8c01a9420e83
5ecd3f9ce1b7f798e753e9c82549cf3566f76335335bc2c20ff4abea4dbf44bb
0e7dde1fe8f05cdee965403dd3d07f4dbc25659be569391487f22b95081efc81
4d8ab7c2d1ef941a1bdccf746091c1487018334288441bdbfd36703ff734edf1
a2589b7ae2187468afbefbc847639f7086f389f55ee74539f874a30aeb3f799a
1915d46ca544ec373197cd6e4e5d5ca99bd4f40c8fb737c1de3970213e0a1070
5127ead0702c78f1efa3ece08a1d910001dd0bd302f0a2fda96276db5947976e
0433063c69f972ecb7564091858c614b92631ab31ba472af51f55aa18523eb23
b50506e1004bd6fd33ba2d88d37e9d7cc4d7d9e4173db7ef9c75bb31a1bb306a
2e41a74c212e108374fabfcd847f8ba6571b60981598c29a84ea1356ae1e9a80
7c6d6b660b5af41cdff9547b5a7d26a960dfbfba8cefc5353a4bc749f8b0e379
cb6aa6e7cb3a28d708ddb87589e0a6be52c273d9c975492f4de1b9dce51744e7
9a5651289f8a73ca08be416bef004ff88fa4e5d929e046bb87e5ad7767608f1c
c2d4b61d0956de4ac5a83d70721a5f41e9719a5c2f27cb5e31335415d4f85aa0
39781a1db27774d5654d7320d36f1ab6f969d5ae3678ea046b7f5da2e098c513
0fbdebe4e39e1c27b133b0162c02821fadb397818a6a2a2f2d19b86a7d970a61
1e60adccdb3ac338390c893d2e4bc1a6d18d9f19d1c7c69a2feaa0510c8dd912
1f15a573df30f472b495be69344cf86174215a92740a86924d69eeaa9b4025ad
02bc88ba60f09c13a2f9318c54129cae3824b7efc9ffb52fc1bdfdc8b65b0e92
b9befc40804612f623df10992cba6b81a8c28e9eef0e056dbc100dac7877173b
5a0327dd1e295d296211764dce545cddbbf25edaf615f443563bf9d67002bebb
eab5273858bdbe6bb2cd3dba5e1abe8aaf36ec9d0974474f0a46b9a6b9634395
a1446d3983724c71546285250d4a70a12fc3bc0994b9ae907bb545e4e9b9dec9
d15133aa5d82bf2324f1745ea5f60a062e228f7fd2f9cb92040843d4ad1cde33
58eeabb3e1b4d2ab6b33ea7d4dfb0bf2fdff128ec42d20d61a50a8439f7995a4
f7aef8232265db0d7be76c906deb9b621bbb7cfe0298fccf76da21016174a8e5
711bad21a19e10d4bcfc4aa247cc95aa13882c8996f9c27626c3b4956f640e40
8e0f0e9ca5d6a1a245f8351c7cdcc9d6bcc3e932e00b4b6ba78b3eb2c12653f1
9ace87fdb9ed74e2ad53ca05157917cf8571b844595fbcbe8e6cdb8905efe22d
0f6f3832b9b6f54c58f00effe7ce35713c9d959ea5d586b5620415a10951af59
c3572be5d204c60c4083950a57e915ef2b0704dd884a296a27bf6df88153c3a8
a67c980d0dfeffccfc1708b52f48c9731d91b362b4ff0191e8ffe617952d949e
b41df46bd4150714c72b4fa072950ec3b8c06acd40d32980313b3f2b5b96cb17
40835f44b8ff7d5085d804b5164a376ac95090f46146e36eb2129ca2c5e60169
3348e241ba1f7867f24b4cc26723eb6c25ff4a74708a21d372743d3ea03184b0
0a107b41d937f0085e2a830cdae2adb9b67fe21d6c2e1ac19f876e0aea7529ee
e72ea242cd5b0d4b1c03a19529fc26c694718e0dc12a183e3301b894eab28700
ab8ac49e0273c9fb9ba6449db626891b7c6e9741a328049893537ef97279a1ee
2781ab8459aba09708f2ce08a18b741569f53679405435379016ee22f6846b00
ececba605a43af501046023a465ae3085296b98293b383f78d4066b799347b3e
2a509fe5bb9c8045c5f272f194d41438d14e2994bce0674dff1739c5f2cc5aba
faba805b040e69d1995e85e43150bf53bd33bd03a2007f18a0faaf3007edb259
401ce2e28c47c488105e1eec96d7ea9356e7f9c622ff53946795913f58d21299
9d8c4b9a5f5d3704b3069702af8ac3680458b99723640b839d3342f254f0c29d
d4bdc922947482c9d2a64c0fd3ca100a428ed7954e7783310ff2ac9b6c542fe3
0285719b3c62af1872dc948145a8d814c39ad650206184b1eb26b9f90ea00ec8
ba3307e4f43a08b1f991658e8b266af07b3a3d0f748c358b730767bedd7efcd0
c5a0fe5f29c72b87ec6d38289e7e53b95bf67e2653bb0eed65a426045aec9925
32beb210062bc4688c482eb3af573ddefac47a7a2f5e9946296ab76e0bd12efc
f4ef7210014eaf293f5ca50e3888c7221f6de7da6e747f4be6fb8afd508e9a9f
84cd32c0771046aa8f6bd9bc82661025e85f4f6f8b9510dde7be39ebf03de11b
28f3951b2387482d93b6ebc8c423bee471433ad6c123fdd5e03fdc7f0bfcec17
fd3abb0bd4b081d8defc41d203ce77c510d4a86540c0849c260160344faf6b39
46e308d1302de8ab055c6d3e3193333ac269b949732128ed7ffd6b26049a9dbf
5c4e2d31d00273b45555991c7cf1a81c89d10e59b63596799201514b91ec8ddf
aa74d4d1094390c1dd13aaeae1208e891ea5734c3187467dba9ba0febcddbfa7
787b0459de83615814271bdf41cd74731fca75e2656c4fa5d0b9bc72fce50cbd
dfebc4ff0f255a737a8bb6a691e2dfa63a3c9585d08bbb6772c3d03b9aa2ee83
449f6b1de146a0c1d036593545fc259840f7fc1bbeb92d5a27d450232387c7d9
a16ce80cde9ee6f2d65f8405dd4061c501b07e28b7d666e8fc20873f328f02a8
10c5bfa9404eb686c72efdd9b279f24beedc75767201d72f19f3c4d9bcd262e4
12469af637299739157d2857db3c4e3f2f4473e6c1dde4df1194c7a4262af985
e10879b6f32941695f9ba6ac4e1b0e91b278b1913d7be58bfe3f9cc8693a9a63
7da69fc1e9422b51239681db222bdd426d3913a6046925f592ea3de28c88f579
1f8ea0461f2870db16831775c9da52bfcd01e3fde2e50da6235f836a271c66b0
105b1f2358f024222ae4cecf1ef4eccbec65baebab58b3d009ccff00820d6444
0add89dfdfef15ed0fd6550a8553a58316f70d1f9bf79bed51c3d78f540dda24
be0e25a9cc726372bcc7e48d6b716c58e42e5e0498e0823652a7b2de39a8916b
c4112127a4d1deb703757fa236d05caab9eb31ed96e5feb7b5b7335b588b9a24
83e48f0cd84cae46c41e66c4f759a9fe466b85689b426fa585dae9f0da4ebae7
1606a35009ec9252a7ba14d850db60f50e00d6f261f3f3f79ab55f79950afcfb
ae9e1dd78cd442cfd52235e66bce029e8746d45e0ca38b61330998be08a63cda
c2ef9dbb2710304ffbd95f3b8e065547efbad83cdcd5012449f54d71bb114397
9010f1150fef5839ea5a98f4db44797f0527c84edd0e6ab799ab908acbc4344d
4c41e8299883f43ae9eef4f276c4b6bcad2ac720d46174225b5966986dfb2cc6
3cc507c4b712294f9334191abf4beb7864f69e3899c367af46b7abd751619841
Convinced that the next generation of endpoint security is right for your organization? Contact a Cylance expert to get started!

