If you go strictly by the daily news headlines, you'd think that the majority of current cybercrime issues were limited to just a few ‘hot’ areas such as China, Russia and Iran. This is far from the truth, and in fact, there has always been a great deal of concerning activity that originates from outside these ‘hot’ areas. One such area is the nation of Nigeria.
When you think of Nigeria and cybercrime, the first thing that pops into your mind is probably the familiar Nigerian “419” scams. Those enticing emails that promise huge sums of money while scamming victims out of ‘advance fees’ and personal data have become something of a punchline these days. Despite being well known, they still persist and often succeed, but in reality, these are just a minor percentage of the total cybercrime activity coming out of Nigeria.
For years now there has been a more serious Nigeria-based cyberscam with a rotating cast of actors and groups. The goal of this cyberscam is primarily financial gain, with disruption of business as a welcome side benefit. The potential, however, exists for more severe actions, in terms of physical compromise or destruction of property, cargo and possibly even human life.
While this activity has received a decent amount of coverage in the past, Cylance’s Research Team decided to take a closer look.
Nigerian Scams Grow in Sophistication
Cylance’s investigation concentrated on an ongoing campaign out of Nigeria, primarily targeting high-impact industries in India. In particular: manufacturing, shipping, freight/cargo logistics, and transportation companies were targeted.
The immediate gain from these attacks for the cybercriminals is access to a wealth of financial data. By leveraging credential-stealing tools such as Pony and Hawkeye, the attackers are able to gain access to personal and corporate email accounts as well as breaching corporate intranets and VPNs.
But rather than simply stealing data wholesale and selling it online to the highest bidder, the attackers do something unusual: they manually read through the mail in the compromised email accounts, searching for further targets (both personal and corporate) which they can leverage to infiltrate other companies or siphon money from. The level of detail to which the attackers are privy after accessing corporate email accounts is alarming. Sensitive data including employee records, banking transactions, vehicle or ocean vessel tracking info, and standard intellectual property were all targeted and exfiltrated by this group.
There have been multiple ‘waves’ observed in these attacks, primarily spanning from October 2015 to June 2016. With the Pony Loader 2.2 infrastructure in place, the attackers were able to begin the initial stages of attack. This was typically carried out via a standard spear-phish email to individuals in targeted companies. The messages all have invoice, cargo or shipment inquiry themes, and are sent from registered domains that look very similar to the domains of legitimate companies with whom the target companies typically do business.
For example:
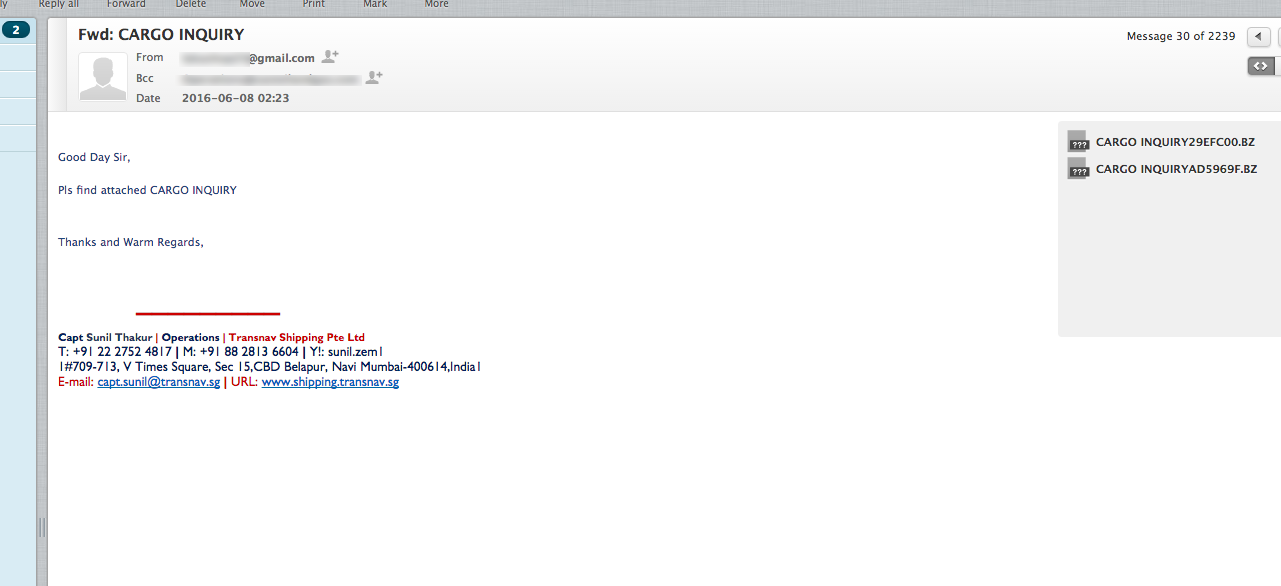 Figure 1: Phishing Email 1 - Bogus Cargo Inquiry (With Malicious Attachment)
Figure 1: Phishing Email 1 - Bogus Cargo Inquiry (With Malicious Attachment)
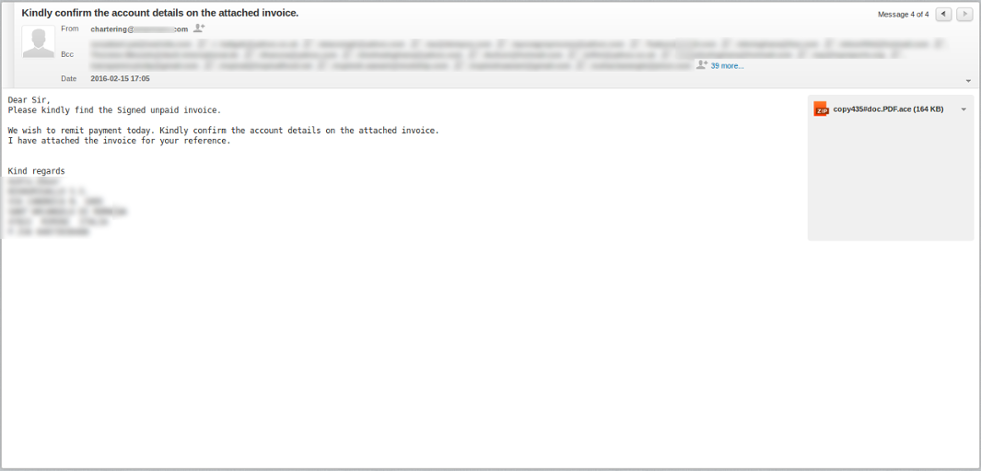 Figure 2: Phishing Email 2 - Bogus Account Details Confirmation (With Malicious Attachment)
Figure 2: Phishing Email 2 - Bogus Account Details Confirmation (With Malicious Attachment)
The spear-phish emails are weaponized with either .BZ or .ACE compressed executables (extracting to either .EXE or .SCR files).
Those attachments are Pony or Hawkeye trojans, which are then used to steal even more credentials and data from the targets. Once the cybercriminals have actual legitimate credentials to work with, they send further spear-phish emails to additional targets manually identified from the compromised accounts.
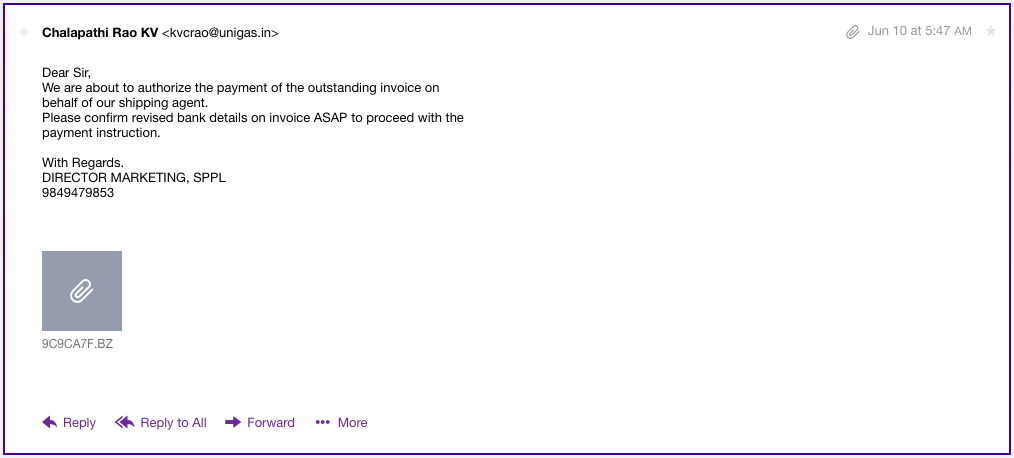 Figure 3: Phishing Email 3 - Bogus Outstanding Invoice Confirmation (With Malicious Attachment)
Figure 3: Phishing Email 3 - Bogus Outstanding Invoice Confirmation (With Malicious Attachment)
In some cases, Hawkeye and Pony are sent in the same email, as per the example in Figure 4, below:
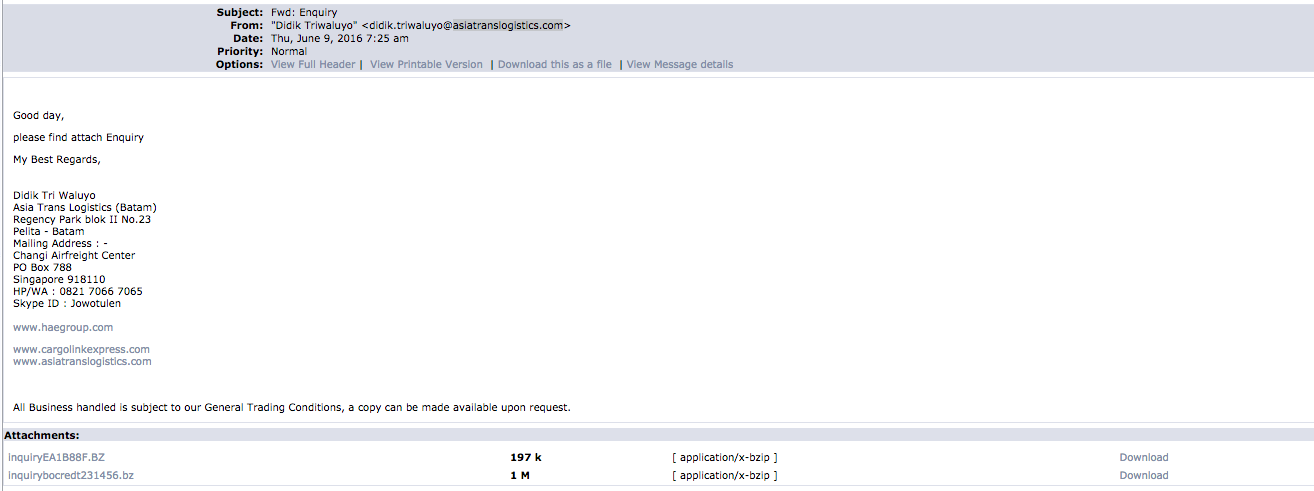 Figure 4: Phishing Email 4 - Changi Airfreight Center Enquiry (Note Spelling Errors) - With Malicious Pony & Hawkeye Trojan Attachments
Figure 4: Phishing Email 4 - Changi Airfreight Center Enquiry (Note Spelling Errors) - With Malicious Pony & Hawkeye Trojan Attachments
Panels and Infrastructure
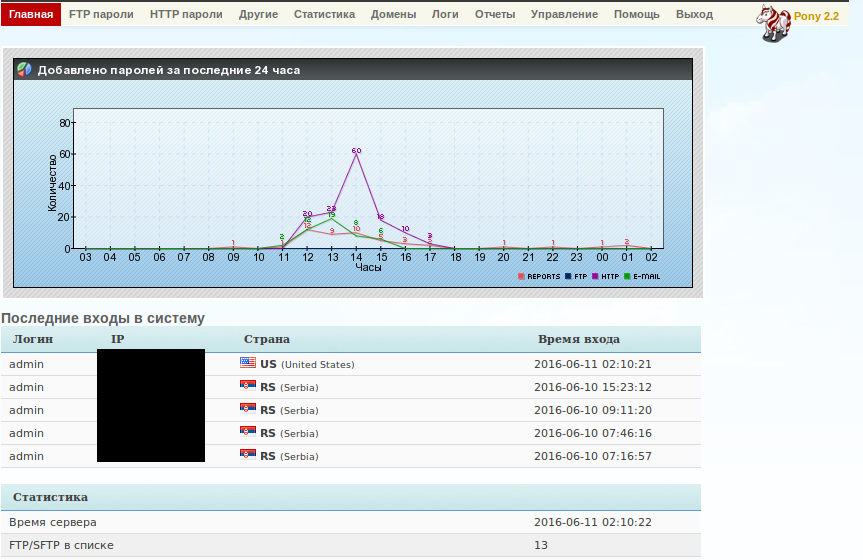
Figure 5: Pony 2.2 Control Panel - 1
Cylance's primary investigative focus with these campaigns has been the wave which started in early April 2016, and (as of this writing) is still ongoing in June 2016. In early April, the attackers set up their main infrastructure via Unlimited Web Hosting out of the UK. Multiple registered domains were immediately used to set up Pony Loader panels and host associated malware:
Initial Registered Domains:
cosmoships-gr(dot)com
equinoxdsitribution(dot)com
etaship-sg(dot)com
fortressict-nl(dot)com
friendshlp-chartering(dot)com
iwenconsultinggroup(dot)com
nevig8group(dot)com
nqvoil-sg(dot)com
octagonainternational(dot)com
pcchand(dot)com
pruship-tw(dot)com
seahorsegroup-in(dot)com
toships(dot)net
tosihps(dot)com
toslhips(dot)com
toslhps(dot)com
vietexcurisons(dot)com
alexbensonship(dot)com
The longest running panels (now down as of 6/14/2016) were hosted on nqvoil-sg(dot)com, and pcchand(dot)com. Pony C2s were briefly active on friendship-chartering(dot)com, toships(dot)net, and tosihps(dot)com. Both the Pony-hosting domains, and those not hosting Pony were observed sending out weaponized email messages, directing victims to one of the active Pony C2s:
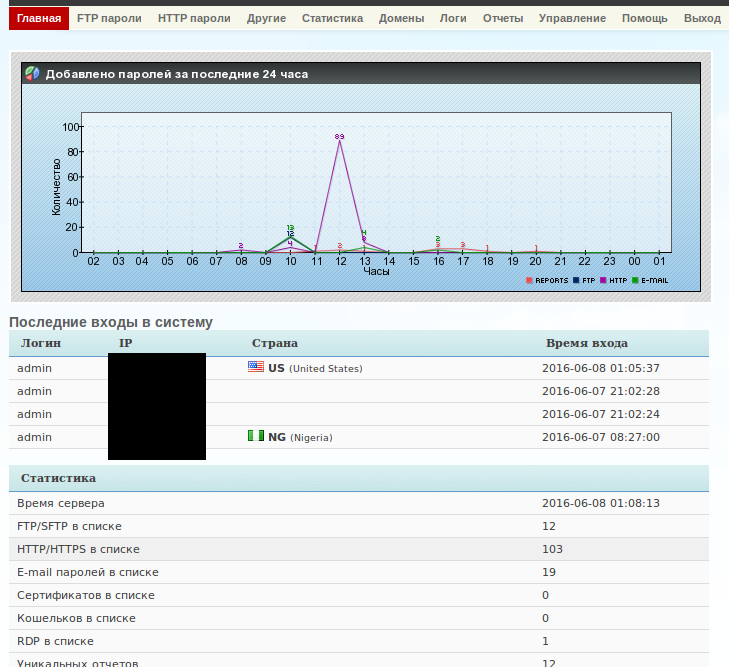 Figure 6: Pony 2.2 Control Panel - 2
Figure 6: Pony 2.2 Control Panel - 2
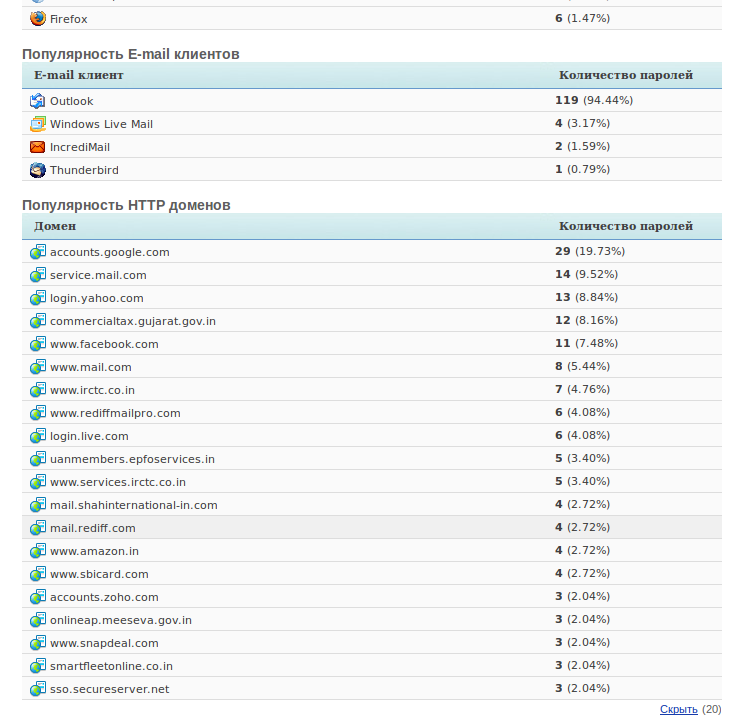
Figure 7: Pony 2.2 Control Panel - 3
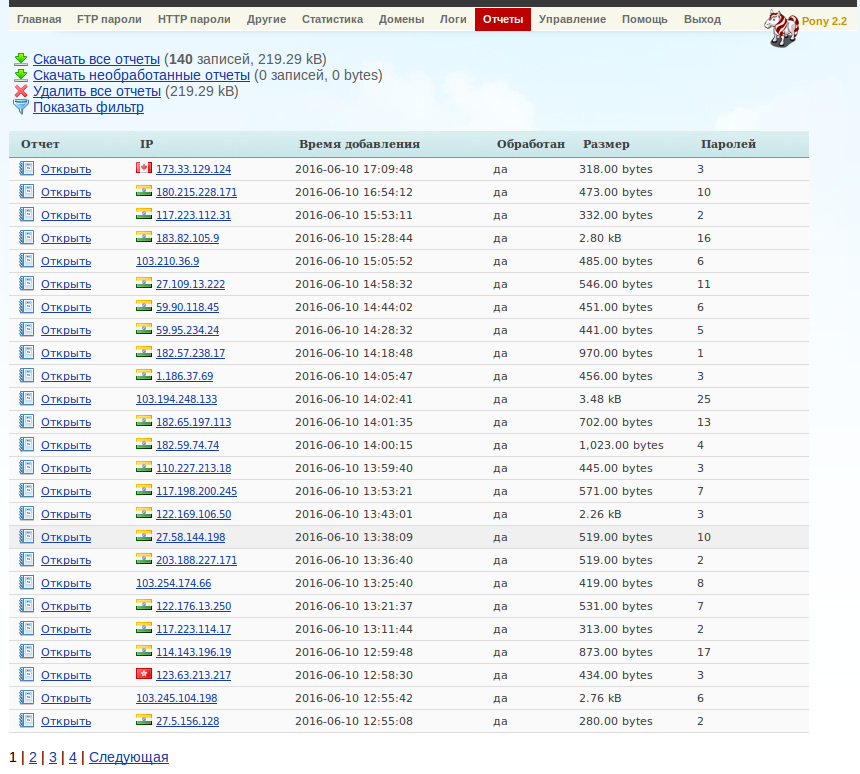
Figure 8: Pony 2.2 Control Panel - 4
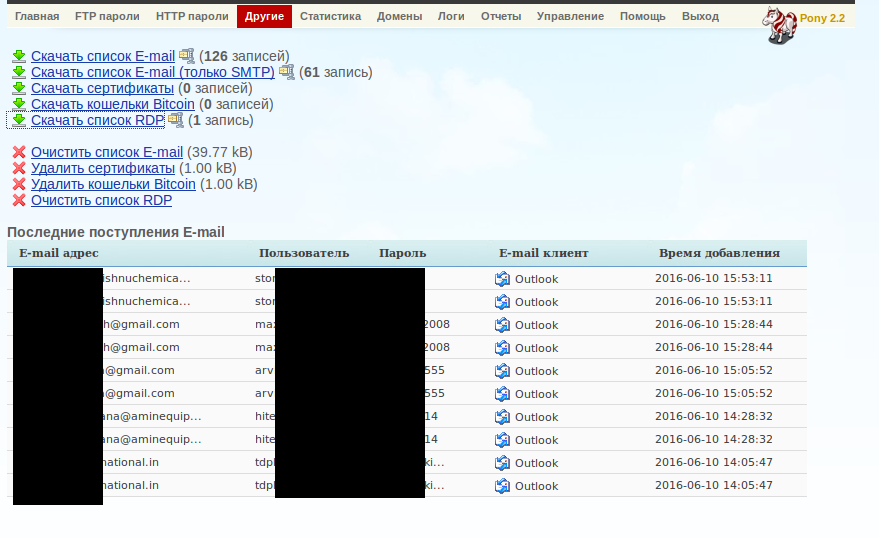
Figure 9: Pony 2.2 Control Panel - 5
Armed with ample sets of credentials, the attackers now have access to an enormous amount of sensitive information. This is perhaps the biggest takeaway of this post. Even if the attackers were only interested in the financial data, of which there is plenty, the potential for financial and physical damage via leveraging other segments of acquired data is alarming.
Not only do the cybercriminals have access to critical financial data such as account numbers, transaction IDs, bank routing numbers, SWIFT codes, IBAN codes, and so on, but in this case the attackers also have direct access to vehicle, shipping, and cargo logistics data. This data ranges from the routes and locations of delivery truck fleets, all the way to routing and cargo of commercial and government marine vessels. Examples of financial and transportation data, gathered/ monitored by the attacker, are given below:
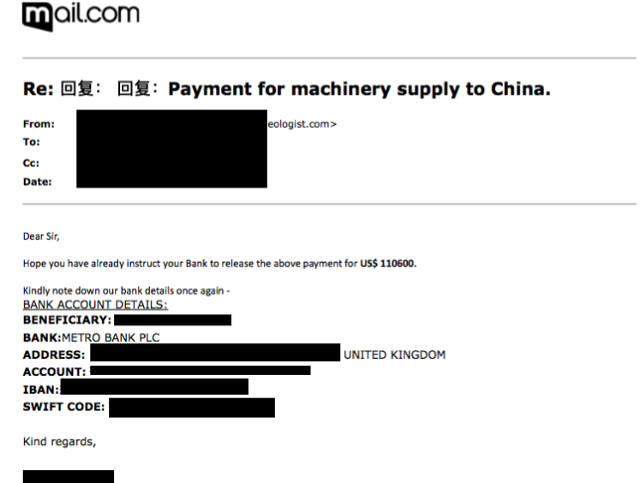
Figure 10: Confidential Banking Data Monitored by the Attackers - 1
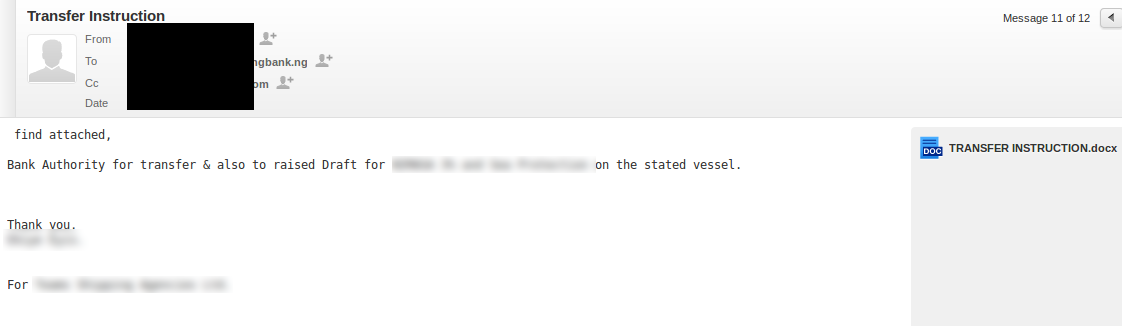 Figure 11: Confidential Data Monitored by the Attackers - 2
Figure 11: Confidential Data Monitored by the Attackers - 2
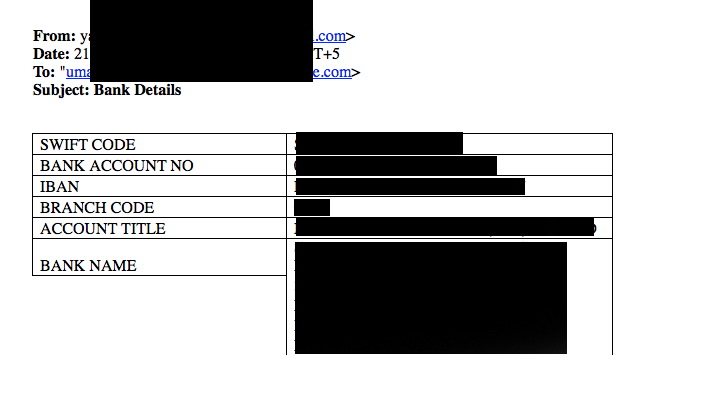 Figure 12: Confidential Data Monitored by the Attackers - 3
Figure 12: Confidential Data Monitored by the Attackers - 3
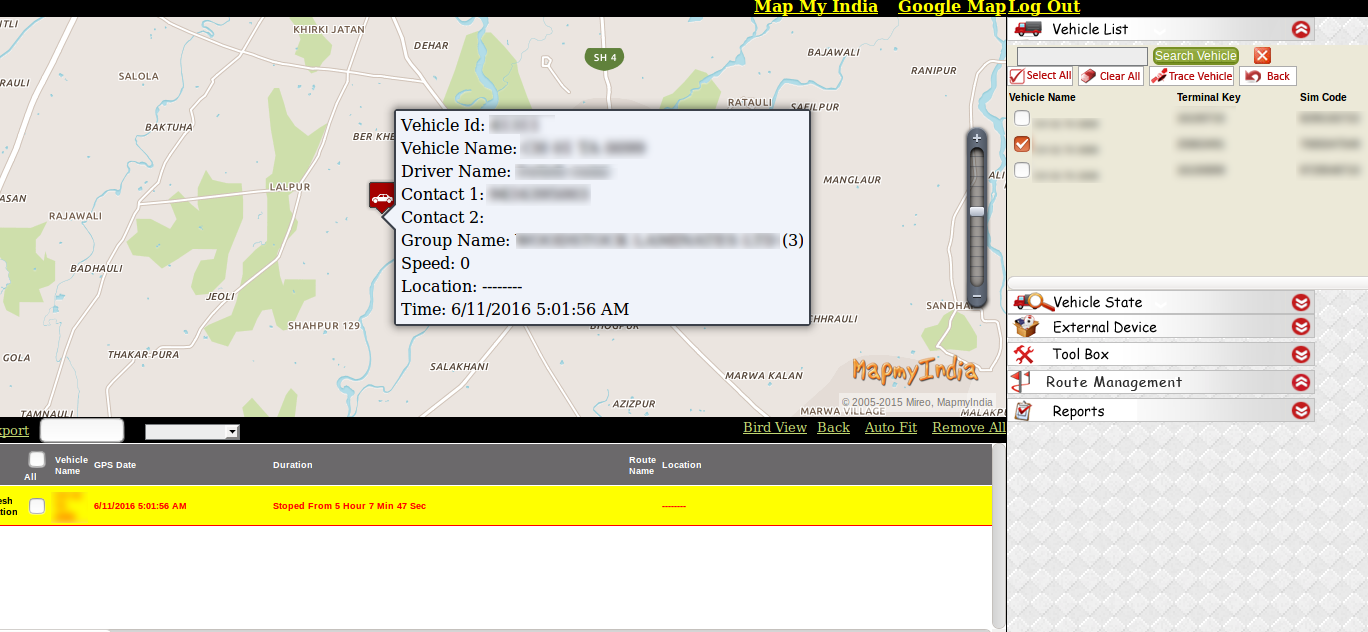 Figure 13: Vehicle/ Tracking Cargo Info Monitored by the Attackers -1
Figure 13: Vehicle/ Tracking Cargo Info Monitored by the Attackers -1
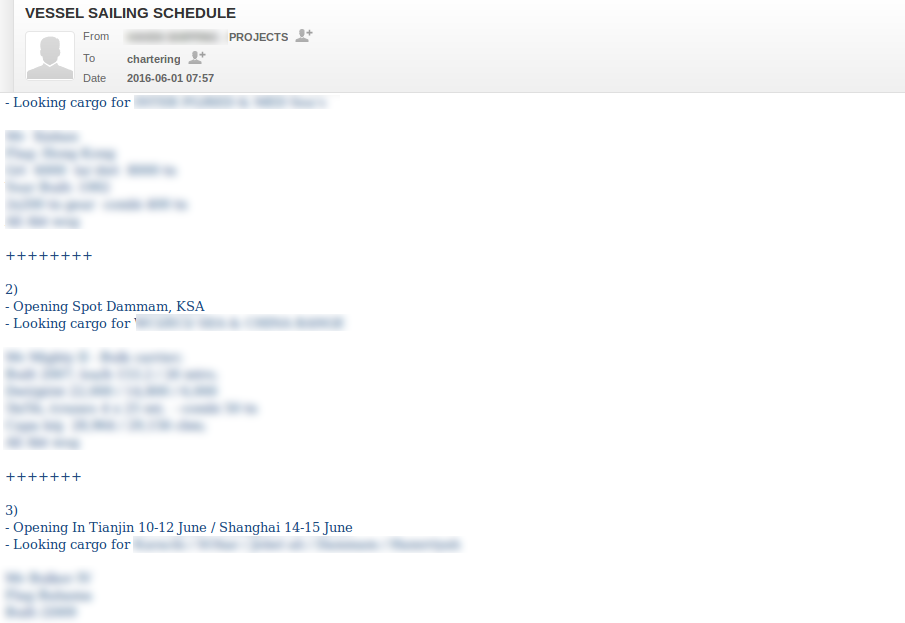
Figure 14: Vehicle / Cargo Tracking Info Monitored by the Attackers - 2
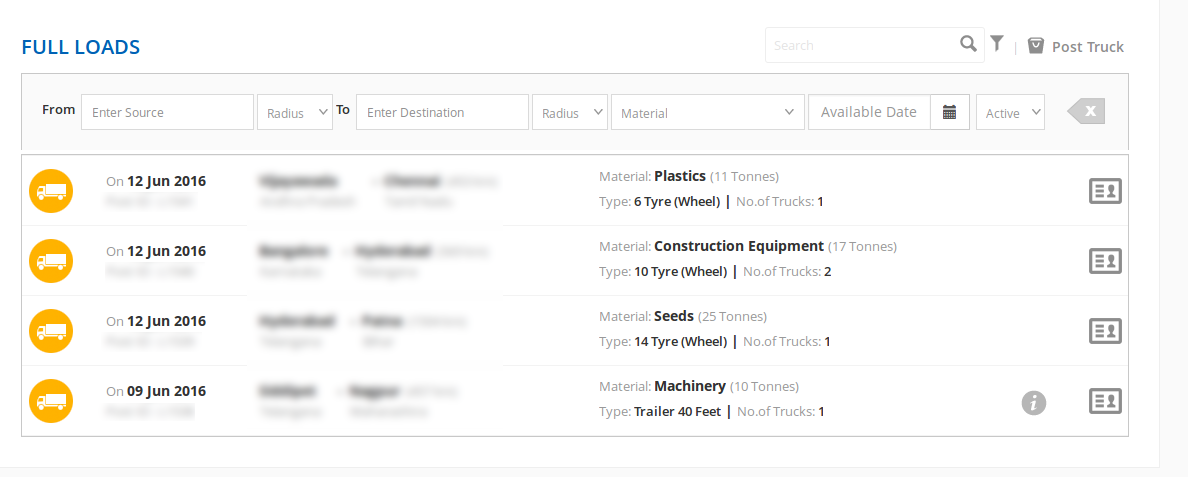 Figure 15: Vehicle/ Cargo Tracking Info Monitored by the Attackers - 3
Figure 15: Vehicle/ Cargo Tracking Info Monitored by the Attackers - 3
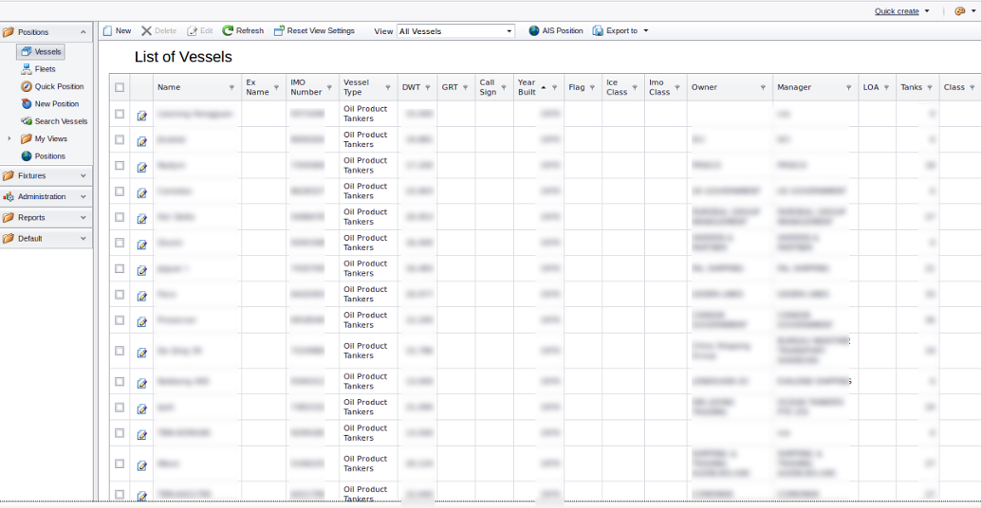 Figure 16: Monitored Vehicle/ Cargo Tracking Info - 4
Figure 16: Monitored Vehicle/ Cargo Tracking Info - 4
Malware Used in the Attacks
The attackers are utilizing Pony Loader 2.2 almost exclusively for these attacks. There are a few specific targets where Hawkeye and/or Zeus came into play, but most of the focus and benefit comes from Pony. The Pony malware is purpose-built to harvest a prescribed set of credentials and data from the victim’s machine. Pony 2.2 is capable of harvesting RDP, HTTP/HTTP, FTP, SFTP, SMTP, POP3, IMAP as well as bitcoin (including Electrum and Multibit modules).
The bitcoin theft modules are relatively new to Pony Loader. That is to say, the functionality related to theft of cryptocurrencies was introduced first in version 2.0 of Pony Loader. The password stealing modules are (in standard Pony fashion) also specific to certain products.
Global Password Module List:
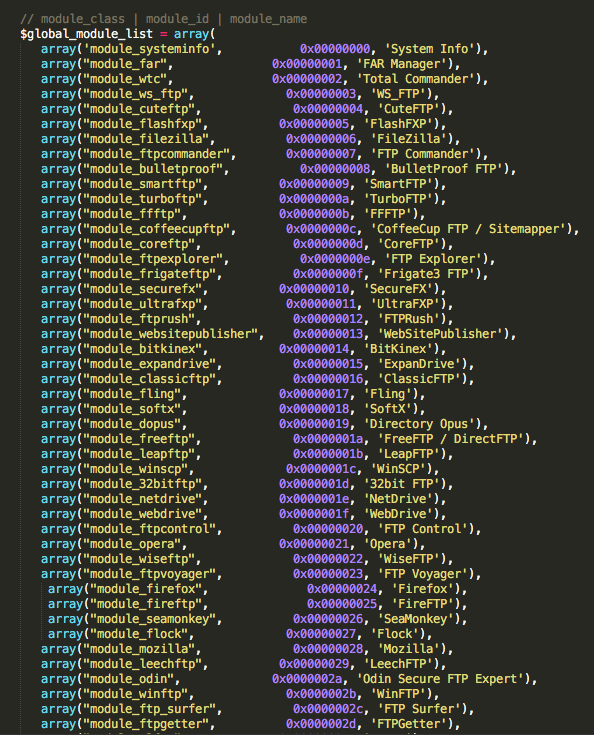
Figure 17: Global Password Module List -1
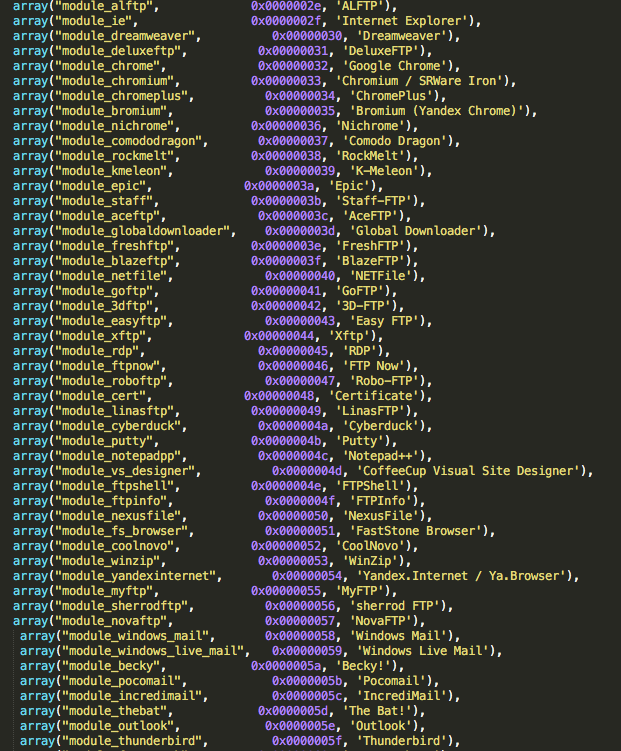
Figure 18: Global Password Module List - 2
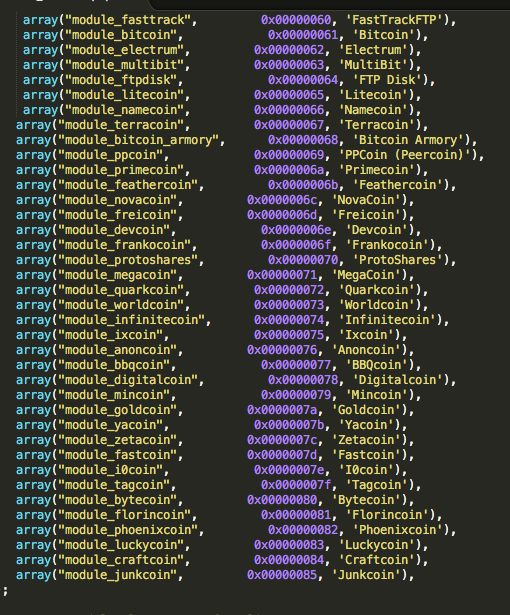
Figure 19: Global Password Module List - 3
The RDP Capture module can be seen below, along with portions of the bitcoin processing modules:
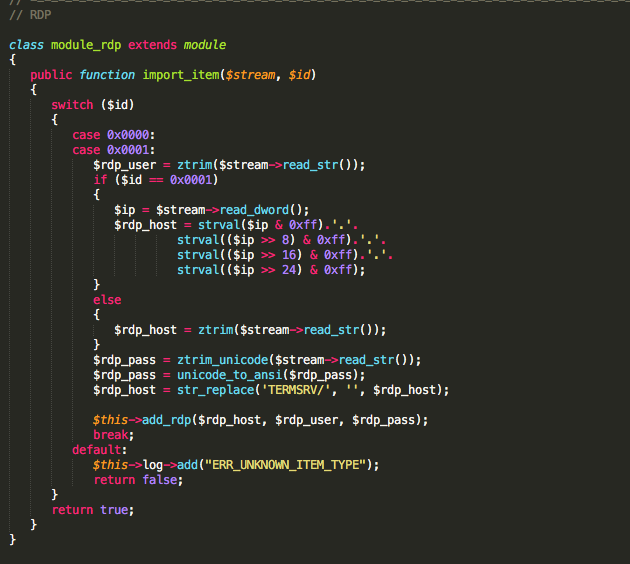
Figure 20: RDP Capture Module -1
Below, we see how credentials are constructed from the data submitted from infected clients:
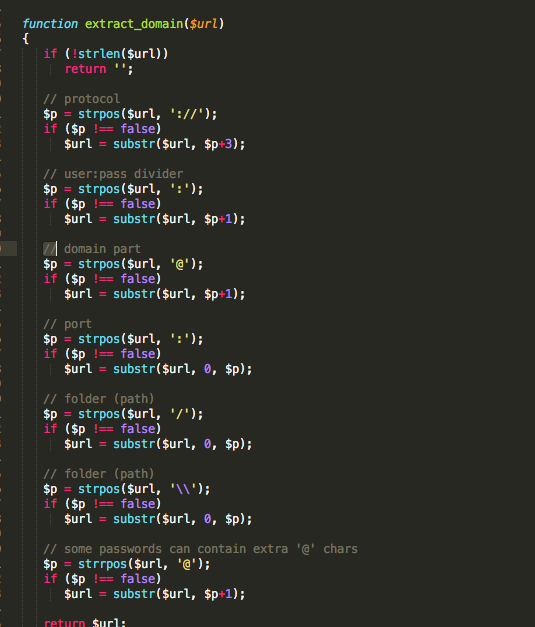
Figure 21: RDP Capture Module - 2
Pony Loader stores data in a local MySQL database. This functionality is outlined in database.php on the server hosting the Pony DB:
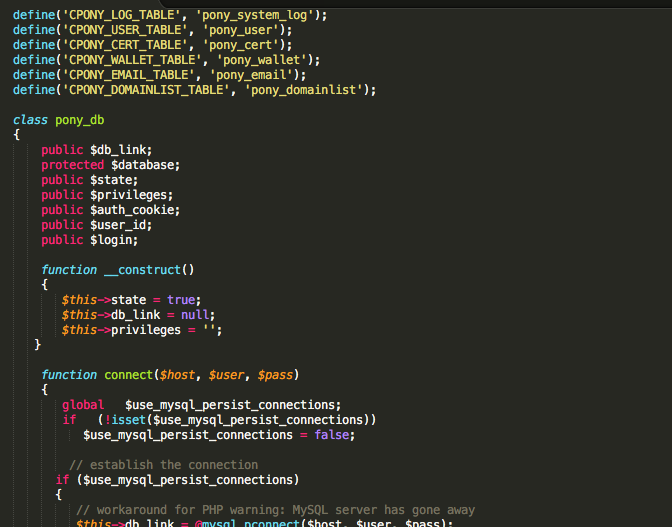
Figure 22: Pony Loader SQL Database
Here we actually see an example of the attacker leaving the MySQL credentials exposed (in the clear) in the server’s config.php:
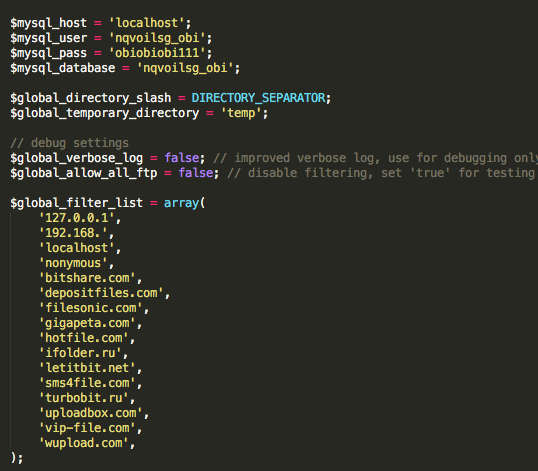
Figure 23: MySQL Credentials - Exposed
Upon execution, Pony Loader will attempt to identify specific AV products running on the victim's machine, for evasion purposes. In the analyzed examples, the binaries are looking to identify running instances of antivirus products from the following companies:
* Bitdefender
* Kaspersky
* AVG
Pony binaries (associated with these campaigns) do not stray from the natively built binaries generated by the Pony Builder, with one exception. Some of the binaries are encrypted with an off-the-shelf Crypter tool called DarkEyE Protector:

Figure 24: DarkEyE Protector Logo
In one example we looked at, the license for DarkEyE Protector is bound to / associated with the email address lakashop25(at)gmail.com. (Visible as artifact embedded in the malware binary). That same email address is associated with the hosting of the Pony C2 domains.
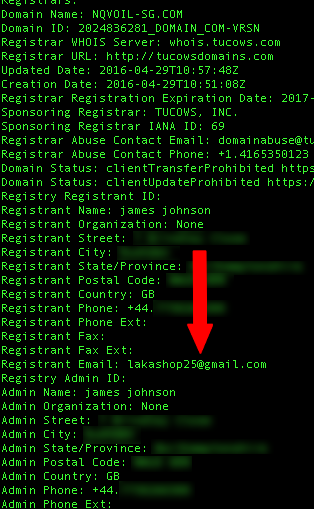
Figure 25: Domain Hosting Purchase Showing Use of Email Address: lakashop(at)gmail.com
If we go back to some of the initial spear-phish campaigns, we can actually find one where that same email account was used to send the infected message:
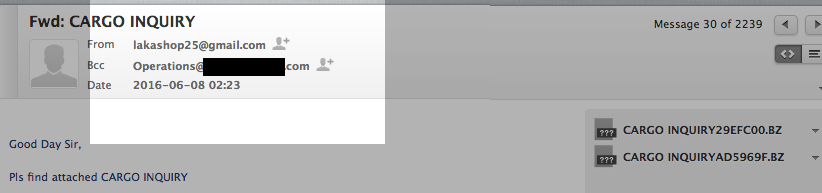
Figure 26: Spear Phish Email Showing Same Email Address Used as Domain Purchaser
Attribution
There are many aspects that point to Nigeria above and beyond the by-the-book modus operandi outlined in both this write-up and some of the past efforts previously referenced.
We also observed that most of the logins to the various Pony admin panels were tagged as being in Nigeria:
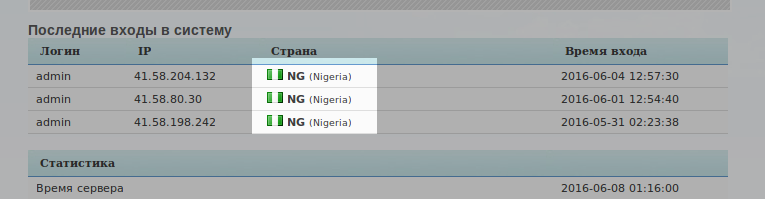
Figure 27: Pony Admin Panel Showing Logins From Nigeria
We also see consistent reuse of user names and passwords that reference Nigerian culture. These accounts appear consistently among the compromised accounts as well within the actual administrative credentials to Pony admin panels.
For example, one particular actor uses several variations of “waxxy” which is a reference to the popular Nigerian DJ known as DJ Waxxy.
EX: waxxy3:waxxysomuch
EX: waxxy3:vgwbnpcnra
EX: waxxy3:louiss33
We also see several recurring uses of “chukwuka123” and “chukwuka”. “chukwuka” is a reference to the popular Nigerian actress Chioma Chukwuka:

Figure 28: Chioma Chukwuka, Whose Name is Often Used as a Password
The term “chukwuka” is more frequently used as the password to some of the Pony admin panels, but appears as a modified password for compromised accounts as well.
Going back to the specific attribution side, we can do a little more digging around these terms to find OSINT pointing to specific individuals acting as part of this cybercrime group.
One particular username and associated email account pops up far more frequently than others. The “onyeb4real” user name is frequently observed setting up dummy/burner email accounts and using them to send out either weaponized messages, or text-only social engineering lures in attempts to lure victims into either running malicious code, or visiting sites hosting malicious code.
Examples are listed below (exact URLs obfuscated):
h x x p s / / - onyeb4real@gmail.com:hope@www.maxxxxxxxxxxxxxxxxxxxxxxookmark
h x x p s / / - onyeb4real@yahoo.com:louiss33@www.xxxxxxxxxxxxxom/cart
h x x p s / / - onyeb4real@gmail.com:louiss33@dolxxxxxxxxxxxxxxxxxxom/join/shipping
h x x p / / - onyeb4real@gmail.com:louiss33@traclxxxxxx.xxxx/signup/
h x x p / / - onyeb4real@gmail.com:louiss33@my.fxxxxxxxxxxxxxomgnup.seam
h x x p s / / - onyeb4real@gmail.com:louiss33@wwwxxxxxxxxxxxxxomm.ng
h x x p s / / - onyeb4real@gmail.com:Louiss33@wwxxxxxxxxxxxxxomount/login.jsp
h x x p / / - onyeb4real@gmail.com:louiss33@www.juxxxxxxxxxxxxxom959.html
h x x p s / / - onyeb4real@gmail.com:louiss33@wwxxxxxxxxxxxxxomm
h x x p / / - onyeb4real@yahoo.com:louiss@wwxxxxxxxxxxxxxomos_.html
h x x p / / - onyeb4real@yahoo.com:louiss@baxxxxxxxxxxxxxomgnin/
h x x p s / / - onyeb4real@gmail.com:louiss33@m.exxxxxxxxxxxxxomnin
h x x p s / / - onyeb4real@gmail.com:louiss33@signin.exxxxxxxxxxxxxomSAPI.dll
h x x p s / / - onyeb4real@yahoo.com:louiss@xxxxxxxxxxxxxomgin.php
Oftentimes, the “onyeb4real” string is coupled with “louis33”. If we refer to the "waxxy" references outlined above, we see that there are also couplings of “louiss” (and variations of it) and both “onyeb4real” and "waxxy".
A little OSINT digging reveals numerous profiles of a specific Nigerian individual names “Louis” with a frequent handle of Waxxy or Waxxy3. The email address tied to this individual’s social media accounts is: onyeb4real(at)gmail.com.
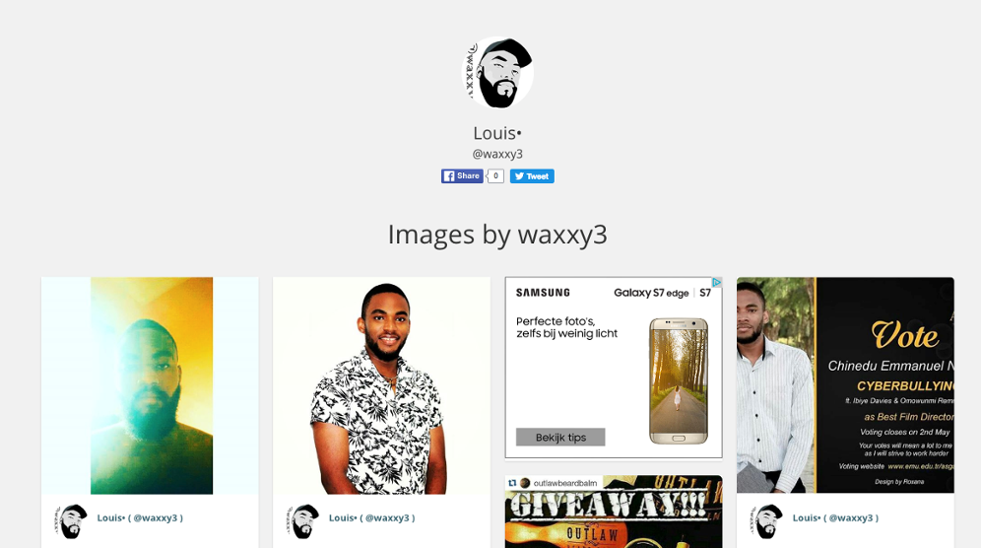
Figure 29: Instagram Account of Louis - AKA “Waxxy” 1
When cross-referencing publicly available information on this individual, we are able to collect numerous fragments of data that solidify the location of this particular actor. In the example below, we see a classified advert selling a used Blackberry:
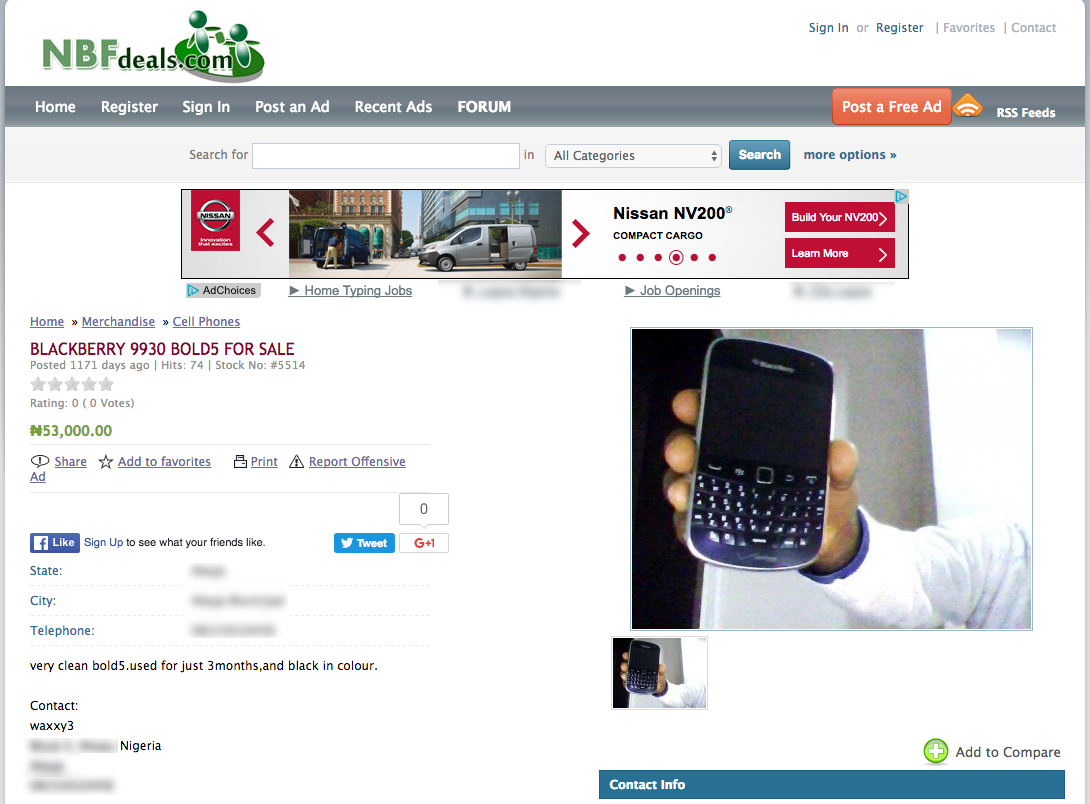
Figure 30: Blackberry Phone sold online by “Waxxy”
Meet Louis Onyeka - AKA Waxxy3 - AKA Onyeb4Real:

Figure 31: Louis Onyeka - AKA Waxxy3 - AKA Onyeb4Real
The Test – CylancePROTECT® vs. Pony Loader & Hawkeye
All of these compromises require that a Pony or Hawkeye binary be executed on the target host. It is therefore critical that any protective or preventative controls on the hosts completely prevent that binary from being executed. Now that we see how much sensitive information a small group of cybercriminals can get access to using simple stolen email credentials, we can understand how vital it is to prevent this simple theft from happening. Unfortunately, that is not always possible with traditional, signature-based, technologies running on the endpoint.
It is important to point out that some of the samples we analyzed were not ‘publically available’ at the time of analysis. That is to say, there were not available on any of the popular, multi-engine, scanning and analysis services which many legacy antivirus technologies and vendors rely on. Having to rely on third party services or quickly outdated signatures is not an option if you wish to prevent these kinds of attacks from occurring.
Cylance tested over 30 samples associated with these attacks using our AI based endpoint protection solution CylancePROTECT. CylancePROTECT stopped all of them cold, pre-execution. End of story.
The following samples were tested against CylancePROTECT:
9ece0cad4cbfe0cf2524880461d62419ed2dcc5f6531c4f4d0b88b16a8a29890
0f8995f8ece4ec14d6ad1745ec11987a02585c0e83ffa8f5c752331a16e0a02f
7009bde544c8cae66301899cd15963698fe78abf31d11b32a0e38028f3472fb9
6d53538d71e655b22a64e41dd986789fb0f81a0cec528fcfb9c7eff770f64363
1b7f600c8dbe9683e2e092e12ce6fc9a296e341c4106acfdb9fbf48c018b1fbe
d6093f98bb65a669487eb1e41f550a4cd7b0a8c30fa2a9f050eb3bb43d69e1be
35194eb171953f2df033a8941053c1f96b74a9d926ba8f991299956cf5243fe9
924fadc931ce2dd5f0b2a83e470ff7ef4ab30ccd17f99dad67103fca2dd5f2b4
7de63c48f9b5caba8855012875937a515b2a6821f230bc291884bc37bc92a62f
d49251a4909f51bac8981fde55696746572f38d463d2fb3fdfe8d7dfff973ff6
de64c7ff454cbb648091f6779eaf2351ddcb25e68087eb8853ac83848598315e
97f25bb70111fe56d3a6b788fc5a0160923fe82ec875305c10541bcff455d5d7
eb3808f586de4cadf98a9a08f303d07de63cdfd8e709181139627c15ff5bab5f
e613e0390fdbfd04d475747d84f966440f9a52a4d49170e5d35ed141bd849fb1
d70aab7549551161df985fe4bea9c00081816c529682f8e01673ca37cff73468
276286c21c93060701b4fd844be7af10b85671e90622e777ebeeeca6e44265b0
d35faedfa36e5ce25f5918e0fe4b536109d9ee49c95da7403c976189c3bcf950
b3062e772925653a6a1c52b7690854f8f26216e78ee836db295aa4c007144bea
befceb428a4f678731b368e00431d5c15e3522c03748e1980db559988c074837
f26a26ccdb91b4bd26406146858477556a5c734a0f276360d2b07fbd697f693d
495b2d3102de768ca3a8c428788777b254ff01023058bca1a1b3f19c9958564b
a7d9cd02734a49e30dfdff4d37e878831717afd9aaa0bbf04814980aea7bb65b
4c10dd2c7477ffa1921a3c646fd728a8f96210c8a984d6d4d4016ca9cf13db20
97c78d5ec6ca8b0b9af2038cb42d6d5c8c560ee11bbf7ba939f916f62b0d0f38
812284a88b8fe2b9af802aeb43d928e18443335fa4a83a62565224ff5e7bcccd
a4f362f3282a1988824fb4fcdf1faa40bb86e7c41ae813ad383753d33c6c5fc2
dd68390cba23f0a740e9cb2c44963c03ea38eb44067447a757fffd4c7a0d214d
3b8f1e963da628ebe6308fbdbbed378593242c5c9eaff9ee68e5c42f8277e608
c73fea308a2cd4c5f201c011b3ebba3466e3af0a0388b25e49680a01c3c8c61e
fb18cbe7482eccc37cca30f354a8fad710494477dd47bc0a8fb6744aeb6c3283
b9caa67341fe2c191a2fc7bc4b932c9f4c96bc4a7d4906d28871db609623e55f
72b8b03e9a0835529c4324e7d0f2c0d13e8d14e8ac1d77072407542c79705bb0
c374a14d2f95a6544acc084e78b70382b6d1294cfb47b486f757f0575d6d2fea
857f1201bd89c906cad2c4a0b9f280e0412392e82a09f5c3f5c3f032304fa34e
a5f9fb3fb839f484359e89e7043ef3739da4ebcd01fd8bc010e26905f725cc72
be882ecbe903b4b9e74d6f592053231c4ce5e653212fadf05cb5261d69bad4f4
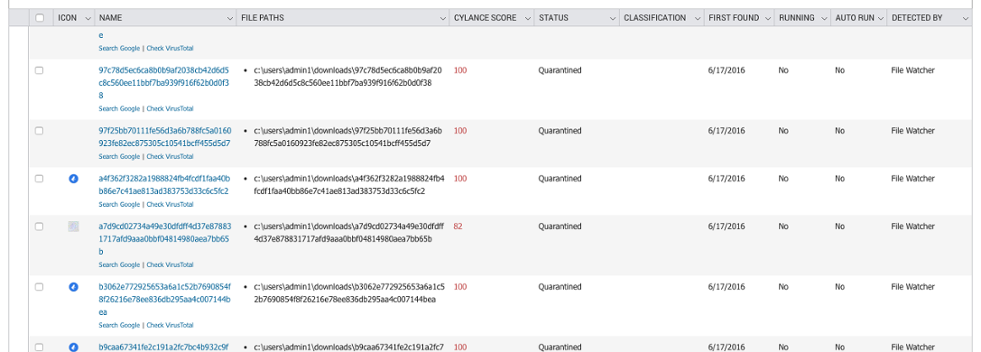
Figure 32: CylancePROTECT Dashboard, Showing Detected and Quarantined Samples Associated With the Nigerian Phishing Attacks - 1
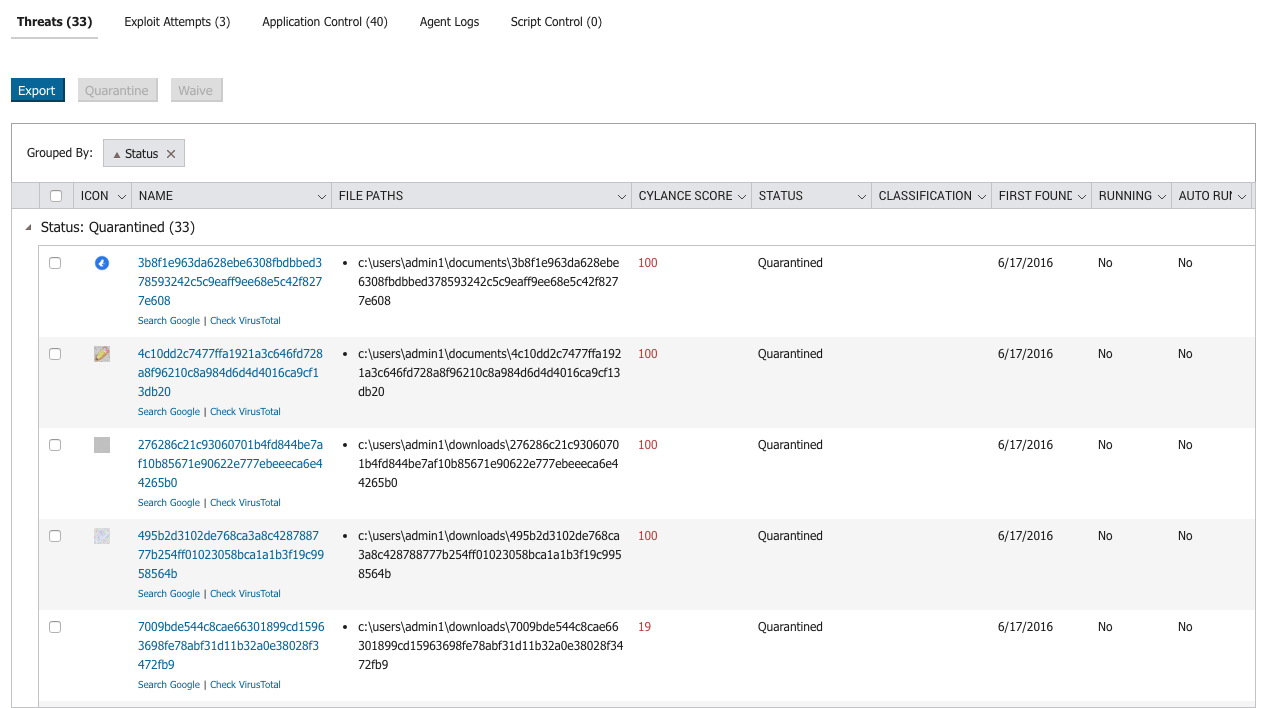
Figure 33: CylancePROTECT Dashboard, Showing Detected and Quarantined Samples Associated With the Nigerian Phishing Attacks - 2
Appendix – IOCs
SHA256 Hashes
9ece0cad4cbfe0cf2524880461d62419ed2dcc5f6531c4f4d0b88b16a8a29890 pcchand
0f8995f8ece4ec14d6ad1745ec11987a02585c0e83ffa8f5c752331a16e0a02f pcchand
7009bde544c8cae66301899cd15963698fe78abf31d11b32a0e38028f3472fb9 pcchand
6d53538d71e655b22a64e41dd986789fb0f81a0cec528fcfb9c7eff770f64363 pcchand
1b7f600c8dbe9683e2e092e12ce6fc9a296e341c4106acfdb9fbf48c018b1fbe pcchand
d6093f98bb65a669487eb1e41f550a4cd7b0a8c30fa2a9f050eb3bb43d69e1be pcchand
35194eb171953f2df033a8941053c1f96b74a9d926ba8f991299956cf5243fe9 pcchand
924fadc931ce2dd5f0b2a83e470ff7ef4ab30ccd17f99dad67103fca2dd5f2b4 pcchand
7de63c48f9b5caba8855012875937a515b2a6821f230bc291884bc37bc92a62f pcchand
d49251a4909f51bac8981fde55696746572f38d463d2fb3fdfe8d7dfff973ff6 pcchand
de64c7ff454cbb648091f6779eaf2351ddcb25e68087eb8853ac83848598315e pcchand
97f25bb70111fe56d3a6b788fc5a0160923fe82ec875305c10541bcff455d5d7 nqvoil-sg
eb3808f586de4cadf98a9a08f303d07de63cdfd8e709181139627c15ff5bab5f nqvoil-sg
e613e0390fdbfd04d475747d84f966440f9a52a4d49170e5d35ed141bd849fb1 nqvoil-sg
d70aab7549551161df985fe4bea9c00081816c529682f8e01673ca37cff73468 nqvoil-sg
276286c21c93060701b4fd844be7af10b85671e90622e777ebeeeca6e44265b0 friendship-chartering
d35faedfa36e5ce25f5918e0fe4b536109d9ee49c95da7403c976189c3bcf950 friendship-chartering
b3062e772925653a6a1c52b7690854f8f26216e78ee836db295aa4c007144bea friendship-chartering
befceb428a4f678731b368e00431d5c15e3522c03748e1980db559988c074837 friendship-chartering
f26a26ccdb91b4bd26406146858477556a5c734a0f276360d2b07fbd697f693d toships(dot)net
495b2d3102de768ca3a8c428788777b254ff01023058bca1a1b3f19c9958564b toships(dot)net
a7d9cd02734a49e30dfdff4d37e878831717afd9aaa0bbf04814980aea7bb65b toships(dot)net
4c10dd2c7477ffa1921a3c646fd728a8f96210c8a984d6d4d4016ca9cf13db20 toships(dot)net
97c78d5ec6ca8b0b9af2038cb42d6d5c8c560ee11bbf7ba939f916f62b0d0f38 toships(dot)net
812284a88b8fe2b9af802aeb43d928e18443335fa4a83a62565224ff5e7bcccd toships(dot)net
a4f362f3282a1988824fb4fcdf1faa40bb86e7c41ae813ad383753d33c6c5fc2 tosihps(dot)com
dd68390cba23f0a740e9cb2c44963c03ea38eb44067447a757fffd4c7a0d214d tosihps(dot)com
3b8f1e963da628ebe6308fbdbbed378593242c5c9eaff9ee68e5c42f8277e608 tosihps(dot)com
c73fea308a2cd4c5f201c011b3ebba3466e3af0a0388b25e49680a01c3c8c61e tosihps(dot)com
fb18cbe7482eccc37cca30f354a8fad710494477dd47bc0a8fb6744aeb6c3283 tosihps(dot)com
b9caa67341fe2c191a2fc7bc4b932c9f4c96bc4a7d4906d28871db609623e55f tosihps(dot)com
72b8b03e9a0835529c4324e7d0f2c0d13e8d14e8ac1d77072407542c79705bb0 tosihps(dot)com
c374a14d2f95a6544acc084e78b70382b6d1294cfb47b486f757f0575d6d2fea tosihps(dot)com
857f1201bd89c906cad2c4a0b9f280e0412392e82a09f5c3f5c3f032304fa34e tosihps(dot)com
a5f9fb3fb839f484359e89e7043ef3739da4ebcd01fd8bc010e26905f725cc72 nqvoil-sg
be882ecbe903b4b9e74d6f592053231c4ce5e653212fadf05cb5261d69bad4f4 shit(dot)exe, various hosts
Domains
cosmoships-gr(dot)com
etaship-sg(dot)com
prisheimpex(dot)com
toships(dot)net
seahorsegroup-in(dot)com
viatexcursions(dot)com
iwenconsultinggroup(dot)com
nevig8group(dot)com
vsuil(dot)com
rightltd-gr(dot)com
vrmeritime(dot)com
transegrldmcc(dot)com
vietexcurisons(dot)com
vietaxcursions(dot)com
toslhps(dot)com
pcchand(dot)com
arcadieshipping(dot)com
tosihps(dot)com
pruship-tw(dot)com
friendshlp-chartering(dot)com
toslhips(dot)com
alexbensonship(dot)com
IP Addresses
149.255.58.2
149.255.58.4
149.255.62.53
149.255.62.54
Believe the Math!!!
Convinced that the next generation of endpoint security is right for your organization? Contact a Cylance expert to get started!

