Within the last month yet another new type of ransomware has appeared, and with the best name yet. Named after the email handle this malware supplies as its primary contact address, JuicyLemon asks the compromised user for 2.5 bitcoins, which is around $1100, in exchange for the safe return (in theory) of their files.
JuicyLemon typically infects a computer via a spearphishing attack, during which an unwitting user is enticed by the hacker to open an infected email attachment. The attacker may use social engineering to convince the user that the infected attachment is a time-sensitive personal document that needs to be opened right away, such as an unpaid invoice, a UPS delivery notification or an unclaimed tax refund. Other popular infection vectors may include fake job application forms, infected websites and unsafe freeware bundles or torrent feeds.
This ransomware targets all versions of Windows, but is limited to PCs only. It creates registry entries deep within the system that allow it to run on Windows startup.
What is ID Ransomware?
Much like ransomware families such as Locky, JuicyLemon is a family of malware known as ID ransomware - malware that scans host information and attaches a personal ID based on this info to each file it encrypts. This ID may contain a unique number, a bitcoin payment address and the letters ‘id.’
For example:
".id-[victim’s ID]_email1_support_@_juicylemon.biz_email2_provectus_@_protenmail.com_BitMessage_BM-NBRCUPTenKgYbLVCAfeVUHVsHFK6Ue2F"
Once a machine is infected, the ransomware then scans the victim’s hard drive for files with a large number of popular extensions, which it encrypts.
Extensions affected* include:
PNG .PSD .PSPIMAGE .TGA .THM .TIF .TIFF .YUV .AI .EPS .PS .SVG .INDD .PCT .PDF .XLR .XLS .XLSX .ACCDB .DB .DBF .MDB .PDB .SQL .APK .APP .BAT .CGI .COM .EXE .GADGET .JAR .PIF .WSF .DEM .GAM .NES .ROM .SAV CAD Files .DWG .DXF GIS Files .GPX .KML .KMZ .ASP .ASPX .CER .CFM .CSR .CSS .HTM .HTML .JS .JSP .PHP .RSS .XHTML. DOC .DOCX .LOG .MSG .ODT .PAGES .RTF .TEX .TXT .WPD .WPS .CSV .DAT .GED .KEY .KEYCHAIN .PPS .PPT .PPTX ..INI .PRF Encoded Files .HQX .MIM .UUE .7Z .CBR .DEB .GZ .PKG .RAR .RPM .SITX .TAR.GZ .ZIP .ZIPX .BIN .CUE .DMG .ISO .MDF .TOAST .VCD SDF .TAR .TAX2014 .TAX2015 .VCF .XML Audio Files .AIF .IFF .M3U .M4A .MID .MP3 .MPA .WAV .WMA Video Files .3G2 .3GP .ASF .AVI .FLV .M4V .MOV .MP4 .MPG .RM .SRT .SWF .VOB .WMV 3D .3DM .3DS .MAX .OBJ R.BMP .DDS .GIF .JPG ..CRX .PLUGIN .FNT .FON .OTF .TTF .CAB .CPL .CUR .DESKTHEMEPACK .DLL .DMP .DRV .ICNS .ICO .LNK .SYS .CFG
*Source: Fileinfo.com
Next, several text files named 'RESTORE FILES.txt' (or 'Read me now !.txt') and '[victims-ID].txt' are created and appear in the same folder as the user’s encrypted files. The victim is invited via ransom note to send one encrypted file to the malware authors to ‘prove’ they are capable of performing the decryption. JuicyLemon gives two email addresses as primary and secondary contact emails: support(at)juicylemon.biz and provectus(at)protonmail.com.
JuicyLemon may also display bogus messages claiming that any attempts to try to manually decrypt or restore the computer will result in the immediate destruction of the official decryption key. Scare tactics are very common with ransomware, so bear that in mind when considering your options.
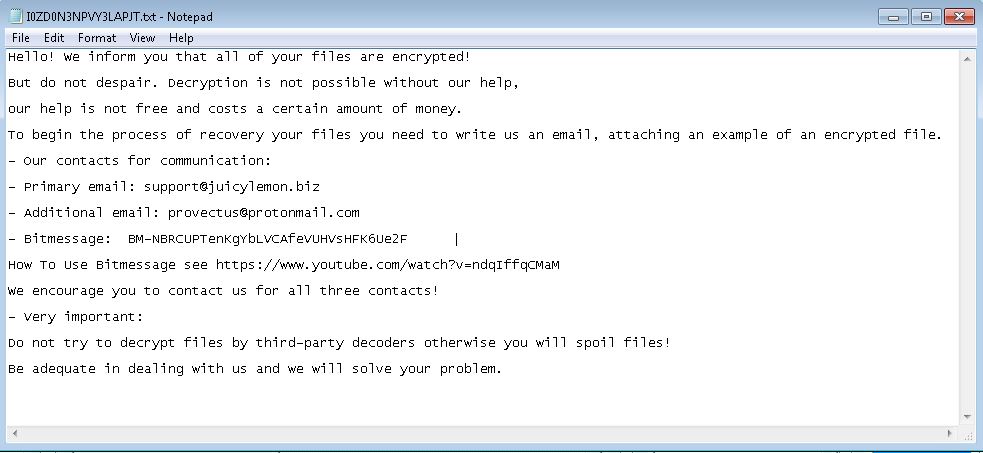
Figure 1: JuicyLemon Ransom Note
If the malware authors reply to your email, which is often a big “If,” the following message may be received:
“Hello! The cost of the decoder for you is 1000 (€) Euro in bitcoins, for a guarantee of existence the recovery program at us you can send the test file for decoding, after decoding of the test file we will send you requisites for payment of the decoder, and after payment the instruction on decoding and the decoder.”
Typical Infection Behaviors
Most ransomware encountered today shares very similar, if not identical, behavioral patterns: entry into the victim’s machine via a spearphishing attack, a ransom note, payment demanded in bitcoin and the encryption of the victim’s files using a strong AES encryption algorithm. However, with JuicyLemon, the size of the ransom requested is larger than most, at €1000 ($1131) in bitcoin.
JuicyLemon’s primary distribution methods are the infamous Angler Exploit Kit (AEK), network shares, and malicious email attachments. With no static indicators, this malware would be hard to catch using traditional signature-based endpoint protection solutions. As it operates typically on the same escalated privilege level as the user, it can slip past many real-time antivirus shields.
Once JuicyLemon gains entry to the system it will add the following values to the Windows registry:
Values Changed:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{75048700-EF1F-11D0-9888-006097DEACF9}\Count "HRZR_EHACNGU:P:\Qbphzragf naq Frggvatf\Nqzvavfgengbe\Qrfxgbc\VaPgey5.rkr"
Values Added:
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Explorer\UserAssist\{75048700-EF1F-11D0-9888-006097DEACF9}\Count "HRZR_EHACNGU:P:\Qbphzragf naq Frggvatf\Nqzvavfgengbe\Qrfxgbc\77ro59o2638936qo2p0pqs8s46q64856rn886s98p17s3pp16200109s16s7s5s3 .rkr"
HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run "98GdCJw9VXPVWeFL"
HKEY_LOCAL_MACHINE\SOFTWARE\98GdCJw9VXPVWeFL "98GdCJw9VXPVWeFLp"
Keys Added:
HKEY_LOCAL_MACHINE\SOFTWARE\98GdCJw9VXPVWeFL
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Enum\PCI\VEN_15AD&DEV_0740&SUBSYS_074015AD&REV_10\3&61aaa01&0&3F\ClassGUI
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Services\LanmanServer\Shares\\
HKEY_LOCAL_MACHINE\SYSTEM\ControlSet002\Services\LanmanServer\Shares\\\_
JuicyLemon deletes itself once encryption of the victim’s personal files is complete, in order to evade malware analysis. It does this by dropping a .bat file, which cleans up the original infection file.
Before auto-deletion, JuicyLemon contacts the remote server and makes an HTTP post, presumably to send the unique encryption key to the c2. Here is an example of a (dead) c2 channel:
How to Decrypt Files Infected by JuicyLemon
Although decryption without paying the ransom is currently impossible due to the strength of the encryption algorithm JuicyLemon uses, users are strongly advised by the F.B.I. and other cybercrime defense agencies not to pay the ransom, as each ransom paid simply encourages the malware author or propagator. Even if the ransom is paid promptly, there is absolutely no guarantee that the files will be decrypted following payment. Ransomware proliferates for one reason alone: the cybercriminals who create, trade and purchase it do so in order to profit from their victims. Every victim who gives in to their demands is sending the message to cybercriminals that crime does pay.
There are currently many resources online detailing step-by-step removal of the JuicyLemon ransomware. Victims are urged to approach these with a healthy dose of caution. Most of these manual removal instructions require the user to edit or manually change essential system files and registries via Regedit. Doing so without a certain level of knowledge of computers and recovery methods may cause software damage that may be irrecoverable without the aid of a professional computer restoration company.
CAUTION:
If you do decide to go this route and follow advice provided by a third party in an attempt to restore your computer, be aware that following these steps perfectly will only restore your operating system to its pre-infection state – it will not decrypt your personal files. In the event that a full system restoration is achieved, this action may wipe all of your personal data from the computer. In addition, you have no way of knowing what other malware JuicyLemon may have installed while resident on your system. Even a clean-looking, restored OS may have a number of invisible or silent pieces of malware lurking in the depths of your hard drive, such as keyloggers, password stealers or worse.
If you are able to back up your encrypted files and get your computer back to a point where it functions reliably, a reputable security solutions vendor may be able to help you restore your files and scan the PC for remaining infections. If you don’t have the time or the money to do this, best advice at present is simply to grit your teeth, unplug your system and wait. An official decryptor may be made available in the future by independent security researchers.
Protecting Your Computer Against JuicyLemon
There’s a lot of truth in the old adage that the best defense is a good offense. Following these ‘best practice’ cybersecurity measures before infection strikes will go a long way in protecting your devices from most typical ransomware, including JuicyLemon:
• Install reliable anti-malware software on all your endpoints and keep it updated
• Set up anti-spam filters to block unsolicited email
• Block macros from running automatically (you don’t need macros to run in order to read most documents)
• Never open email attachments that come from unrecognized senders
• Be wary of email attachments from known senders that promise ‘too good to be true’ offers such as an unexpected tax refund
• Don’t click on any links in emails
• Disable automatic picture loading in emails
• Keep your Windows OS and all installed software and apps fully updated
• Avoid file-sharing sites, which are often heavily infected with ransomware, viruses and other malware
• Carefully check the URL of ‘official’ software download sites to make sure you are on the real site and not an infected copy-cat site
• Repeat after me: back up your data. If your data is particularly important or valuable, backup the backup
• Keep all external hard drives and USB drives unplugged when not in active use; ransomware will quickly spread to encrypt an external backup if it is plugged in
• Consider going ‘Old School’ and burning irreplaceable data such as wedding and baby photos to CD or DVD
CylancePROTECT vs. JuicyLemon
If you have CylancePROTECT installed on your computer, you can be confident that you are protected against ransomware such as JuicyLemon.
In tests by Cylance’s research team, CylancePROTECT immediately detected and quarantined malware files associated with JuicyLemon, pre-execution, without requiring an Internet connection or needing to download any extra updates.
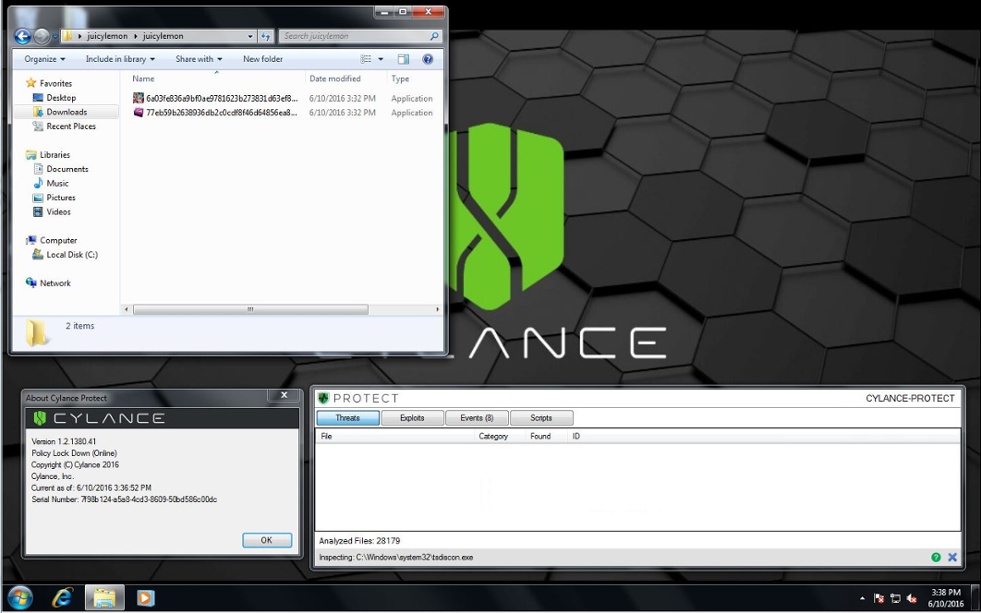
Figure 2: JuicyLemon Malware Sample Application Files
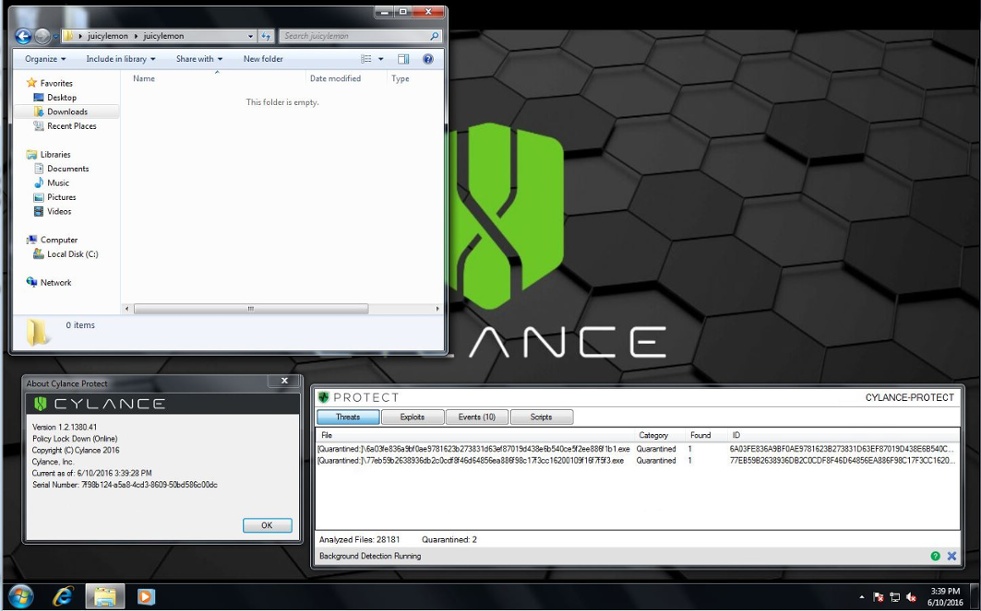
Figure 3: CylancePROTECT Instantly ‘Sees’ and Quarantines JuicyLemon, Pre-execution
Our research team documented this process. Here’s a short video we made showing CylancePROTECT in action against samples of JuicyLemon:
VIDEO: CylancePROTECT vs. JuicyLemon Ransomware
Indicators of Compromise (IOCs):
SHA256 77eb59b2638936db2c0cdf8f46d64856ea886f98c17f3cc16200109f16f7f5f3 6a03fe836a9bf0ae9781623b273831d63ef87019d438e6b540ce5f2ee886f1b1
Network IOCs:
Domains:
Beginbegone(dot)com
IP Addresses:
174.128.251.22
174.128.251.23
Believe the Math!!
Convinced that the next generation of endpoint security is right for your organization? Contact a Cylance expert to get started!

