The time has come to follow up on our previous analysis of the Petya and Mischa ransomware family. When we last left off, private ransomware distributor Janus Cybercrime Solutions had started opening up the platform by offering private stubs and support, in line with most ransomware as a service (RaaS) offerings.
Now, the day security experts around the world have both expected and feared has finally come: the Petya and Mischa bundle is open and available to all!
The update was quietly announced on July 26, 2016, on a little-known Twitter account run by Janus Cybercrime Solutions. It is important to note here that this Twitter alias changed between updates as well. Prior to July, the account username was '@janussec,' whereas now, Janus is operating as '@janussecretary'.
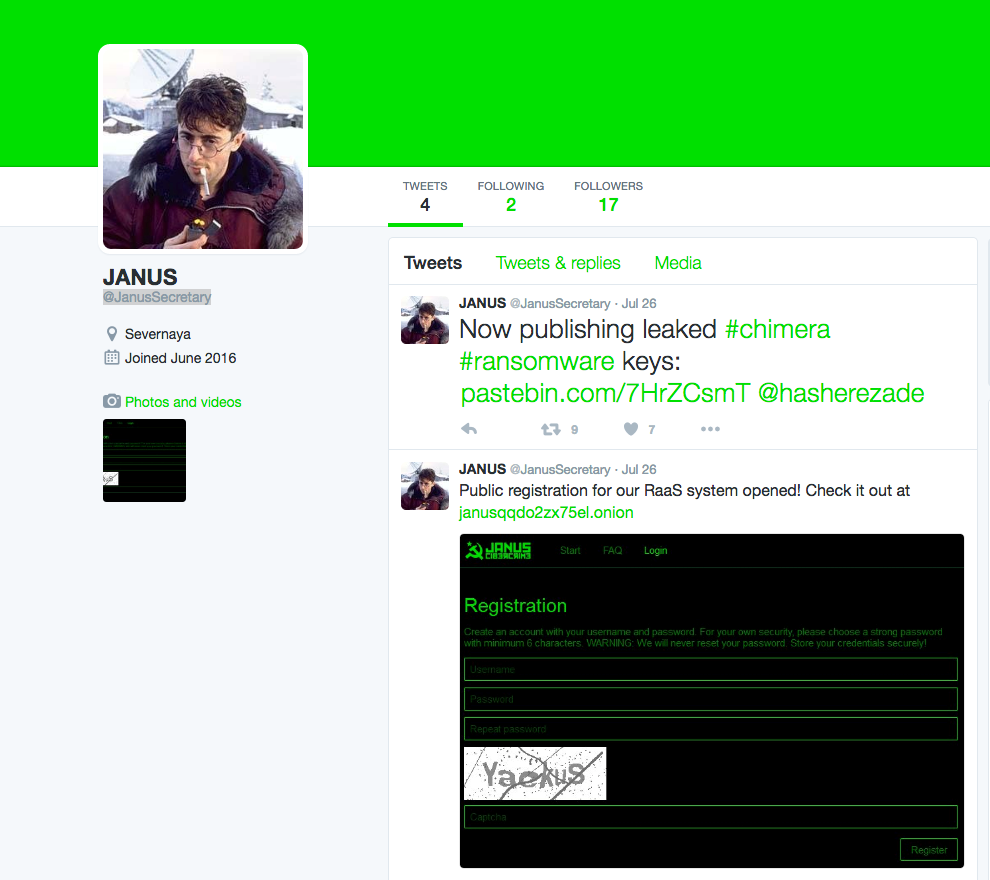
Figure 1: Janus Cybercrime Solutions Twitter Page - July 26th, 2016
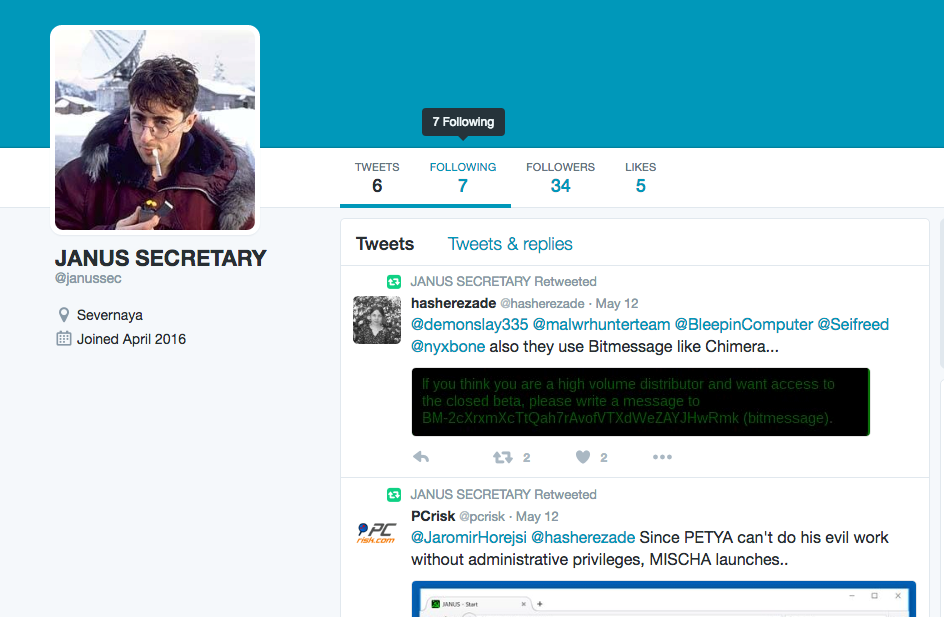
Figure 2: Previous Twitter Page for Janus Cybercrime Solutions - May 12th, 2016
Petya: Coming Soon to a Computer Near You
In short, the platform is now fully open to anyone who wants to create, spread, and manage their own Petya infections. The danger here of course is that the Petya ransomware generated by this service is every bit as destructive as previous generations.
This is how a typical Petya infection goes: upon execution of the malware, the infected host computer will shut down and reboot. Following the restart, the victim (as was the case prior) will be presented with a false CHKDSK screen. Interrupting that screen, or forcing a reboot in an attempt to stop the fake process, leads to the familiar skull and crossbones animation. Pressing any key during the skull display leads the victim to instructions on how to pay the ransom, along with their personal decryption code.

Figure 3: Skull and Crossbones Display – the Hallmark of a Petya Ransomware Infection
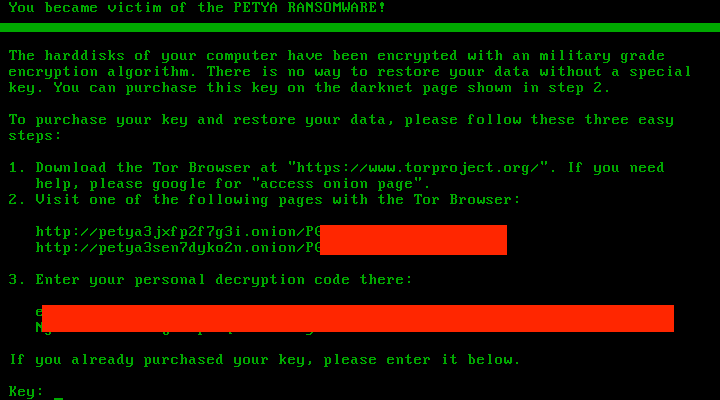
Figure 4: Petya Ransom Note
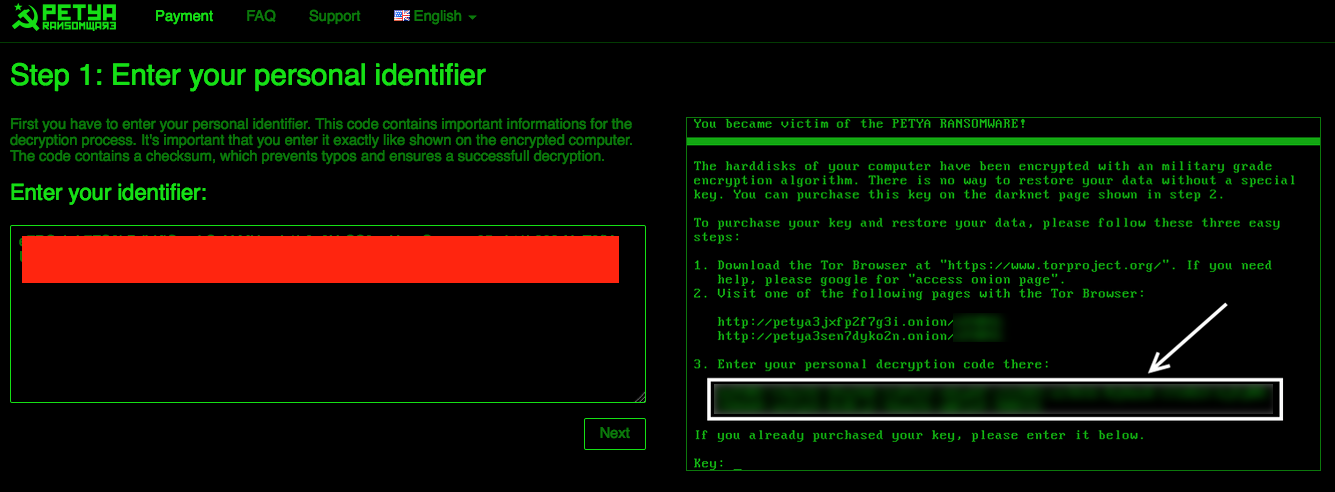
Figure 5: Petya Payment Screen
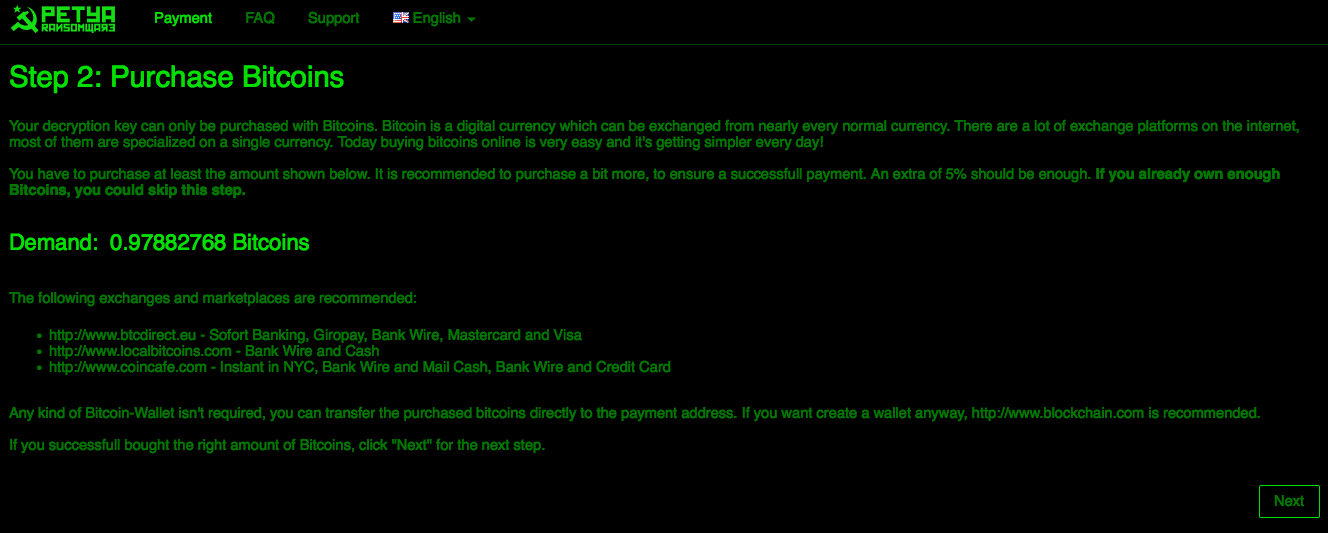
Figure 6: Purchasing Bitcoin to Pay the Petya Ransom
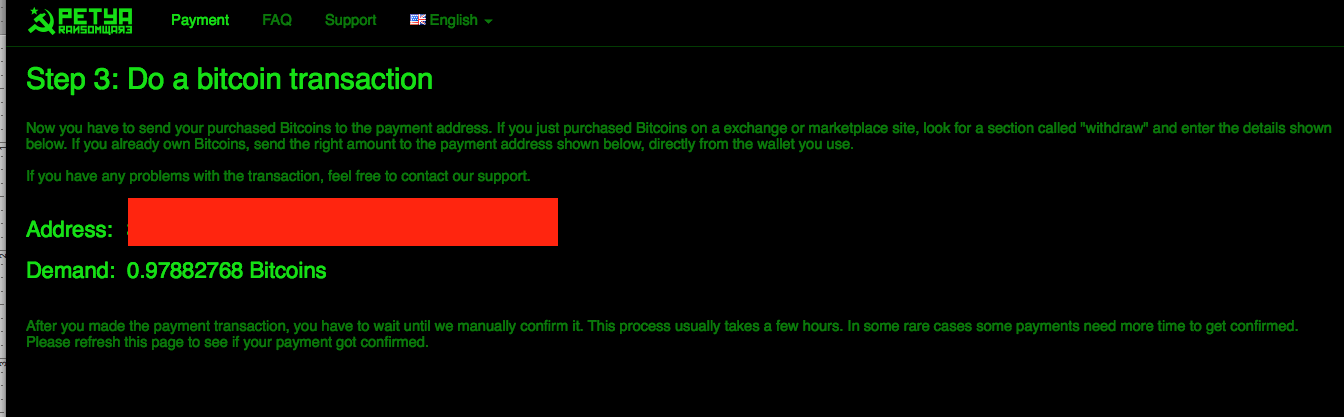
Figure 7: Ransom Demand for 0.97 Bitcoin - Worth Approximately $637.00 in July 2016
What’s in it For Them?
As is the case with other similar ransomware offerings (TOX, Ransom32, Encryptor RaaS[1]), the authors or facilitators get a ‘cut’ of the payment. Payment is dictated by a random range set by the user of the portal. The victims will be charged a random amount within this range.
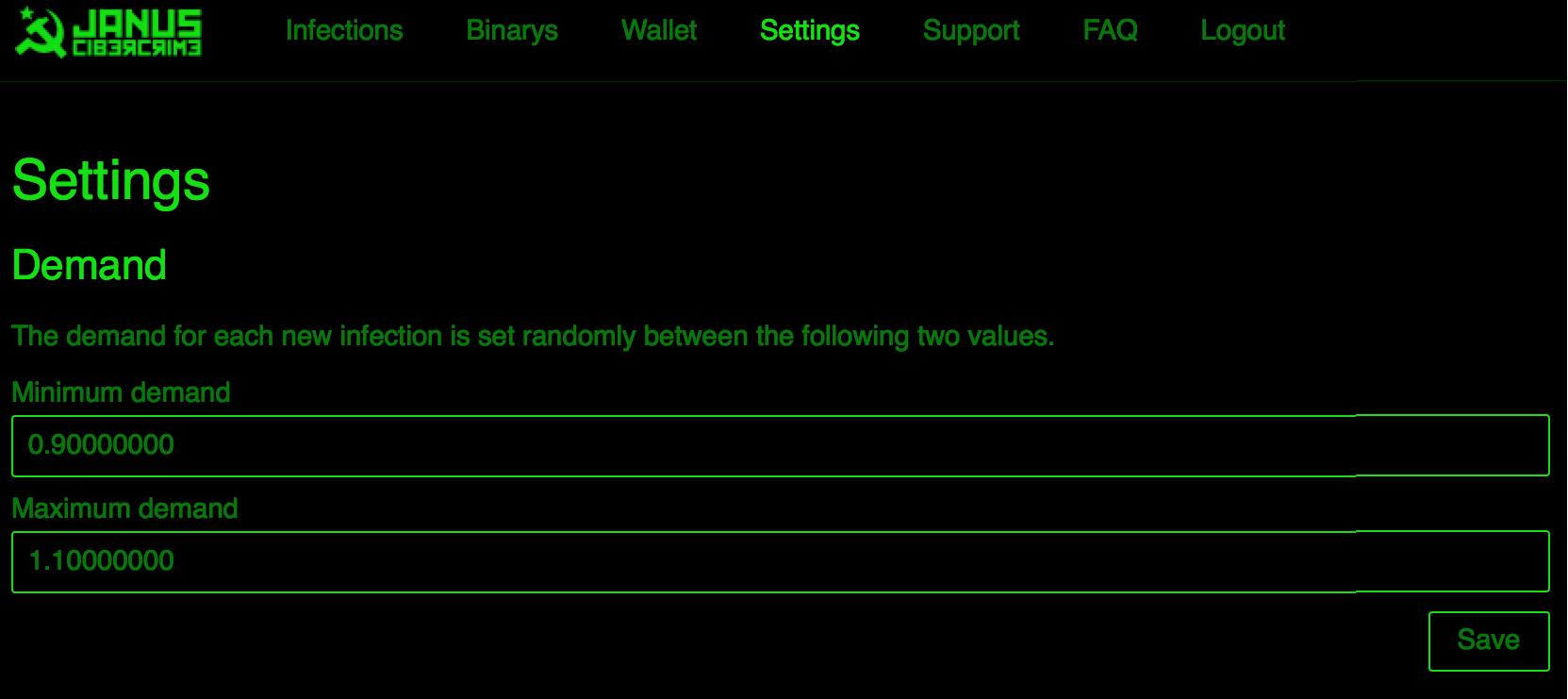
Figure 8: Janus Cybercrime Solutions Payment Settings Screen
The amount of the ‘cut’ is unclear at the time of writing this, as the FAQ for Petya RaaS is not yet live. In the absence of the FAQ, users are instructed to message support via a form on the Janus Cybercrime portal.
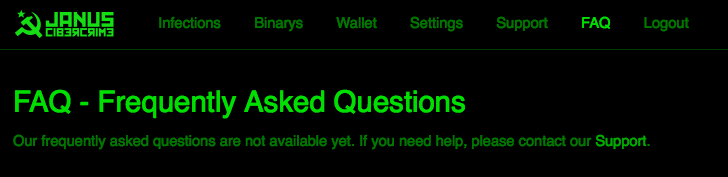
Figure 9: Missing ‘FAQ’ Section for the Petya RaaS Offering
Petya RaaS Administrative Portal
The administrative portal for Petya is very straightforward and ‘Tox-like’. The same site page used for registration serves as the management portal and panel for subsequent infections.
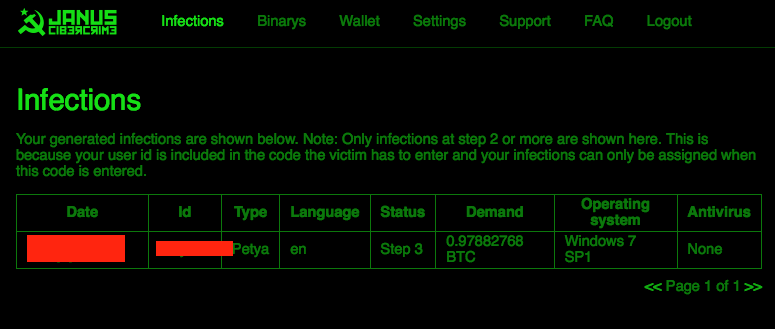 Figure 10: Behind the Scenes at Petya RaaS
Figure 10: Behind the Scenes at Petya RaaS
Registration, however, is not as immediate as the past offerings from Janus. For starters, it is not 100% free. The authors require a small fee which is paid upfront. On their registration page, they position this as a way to weed out the “timewasters and kiddies”.
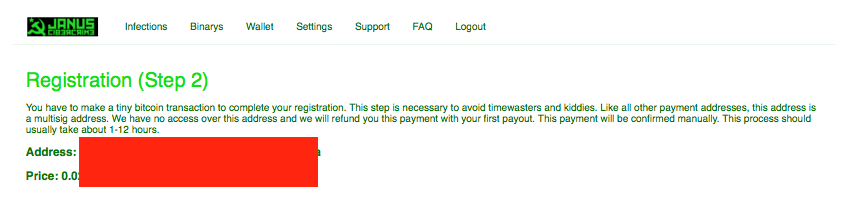
Figure 11: Fine Print on Janus Registration Page
The price of the upfront fee fluctuates, as it is based on bitcoin (BTC). That being said, it appears to hover around the $8.00 to $18.00 USD range – a low price which is (in my opinion) certainly well within the reach of the aforementioned “kiddies and timewasters.”
In order to register and make payment, you must provide the authors with a valid bitcoin address for payment collection, along with the public key for that address. The system then runs a script to generate your private key for the ransomware.
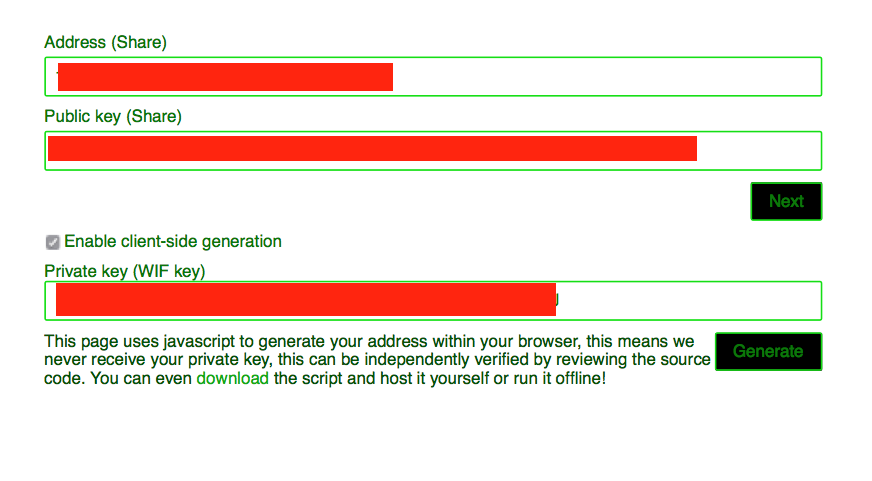
Figure 12: Entering Registration Information Into the System
Once you are ‘in’ - a process that takes between one and twelve hours due to manual verification of the bitcoin transfers - you are then able to download binaries, update wallet settings, track infections, contact support and more.
An important note on the binaries themselves: most registrants will be offered the ‘public’ stub. The private stubs, which are more rare, are reserved for their most active distributors.
The stubs (binaries) are updated daily, possibly multiple times per day, to ensure detection evasion. Even the ‘public’ stubs vary per user, and as stated, over time.
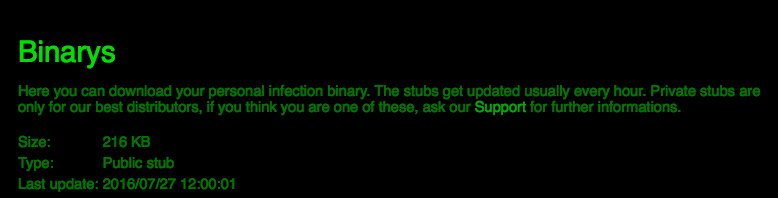
Figure 13: Download Screen for Binaries
Petya vs. Mischa: Stages of Infection
Mischa and Petya infections are handled via the same binary and portal as per previous generations. When Petya is denied administrative privileges by way of UAC controls or otherwise, the Mischa-specific payload is executed. Rather than overwrite the master boot record (MBR), Mischa behaves more like ‘traditional’ ransomware. It will encrypt the local files and then inform the victim how to recover them, in a style mimicking the Petya instructions.
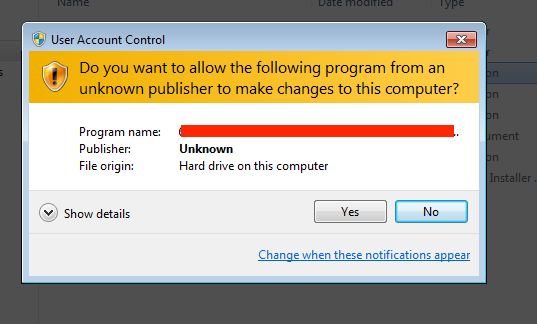
Figure 14: User Account Control Notification – Clicking "No" May Earn You a Mischa Infection
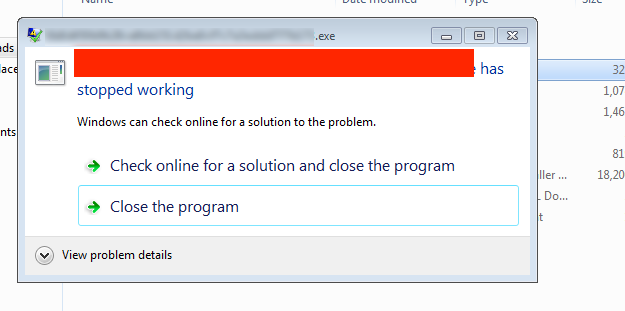
Figure 15: Mischa Malware Detonation In Progress
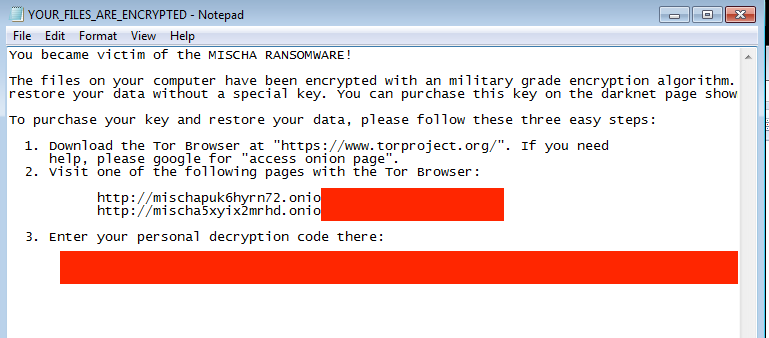
Figure 16: Stage 2 of the Mischa Infection
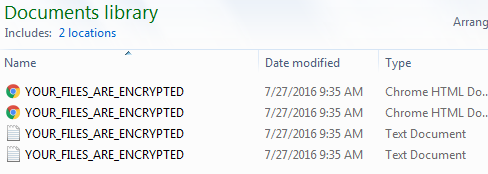
Figure 17: Victim Document Library, Showing Mischa Ransom Notes
In our analysis, Mischa-encrypted files are given a 'MspqYy' extension.
The Test: CylancePROTECT® vs. Petya and Mischa RaaS Bundle
Even the public stubs are very effective at evading legacy signature-based endpoint products, as you can see in the image below. The fact that the binaries are updated daily, if not more often, further compounds this problem. Casual testing with a popular multi-engine scanning site shows that only one vendor picked up the Petya/ Mischa sample!

Figure 18: Multi-Engine Scanning Site Encountering a Malicious Petya/ Mischa Binary
It’s a different story with CylancePROTECT. Our artificial intelligence-based mathematical model was able to prevent the execution of Petya and Mischa right out of the gate, stopping it dead pre-execution. We tested multiple binaries over the course of 48 hours and the Petya/ Mischa bundle was no match for our math-based technology.
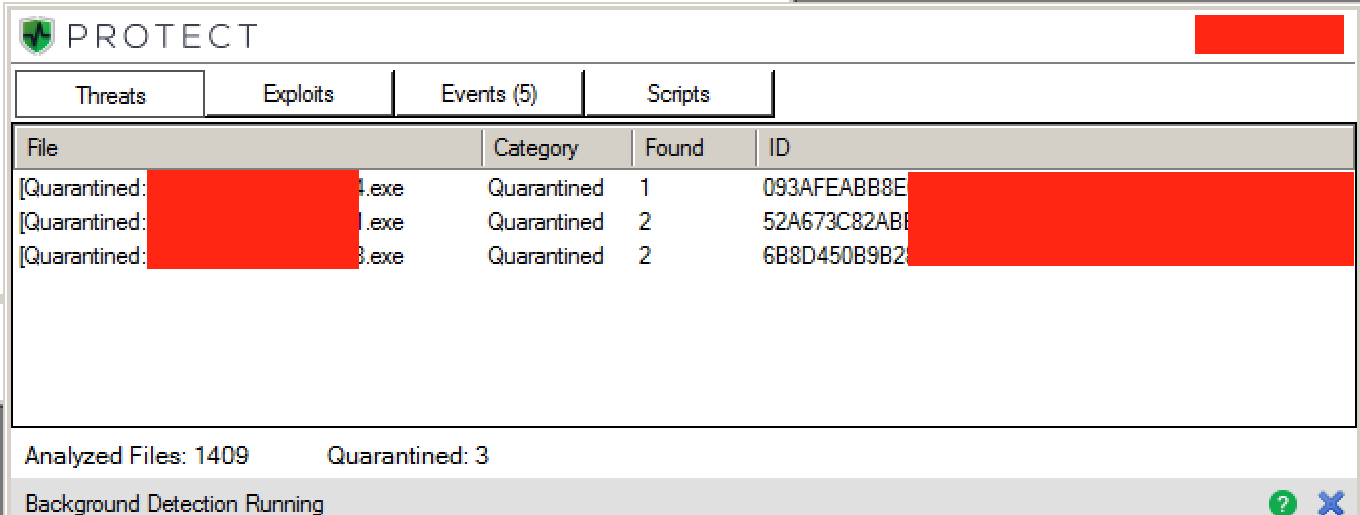
Figure 19: CylancePROTECT Console View, Showing the Detection and Quarantine of Petya/ Mischa Binaries
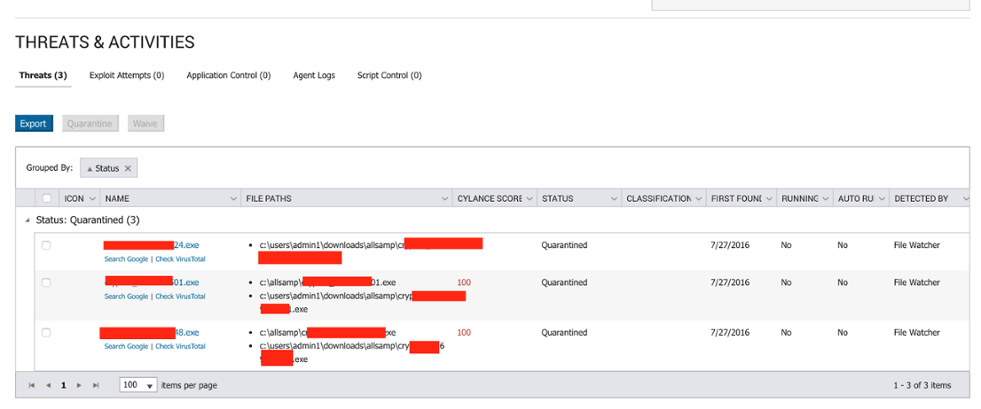
Figure 20: CylancePROTECT Threats and Activities Tab, Showing the Pre-Execution Quarantine of Petya/ Mischa Binaries
Believe the Math!
(NOTE: Sample hashes withheld intentionally.)

