In Greek mythology, Cerberus is the giant multi-headed dog who guards the gates to the underworld. In the modern world of malware, the equally devilish ransomware variant Cerber is an advanced APT threat. It encrypts victims’ files using strong AES encryption and asks for a payment of $500 to decrypt them.
Cerber was first seen back in 2015 and popped up again in March 2016 on the Dark Web. Dubbed “the talking ransomware” due to its capability to read its own ransom note out loud to the victim, Cerber shares many similarities with more widely known malware such as TeslaCrypt, Locky and CryptoWall. All of these ransomware variants will encrypt your personal files and programs and often lock you out of your computer completely, demanding a ransom to restore access to your machine and files.
Cerber is unique in that it uses a never-before-seen automated system to generate new file names and hashes, nicknamed Cerber Hash Factory, in order to thwart traditional antivirus detection systems that employ signatures to detect malware. This trick is carried out by the server, which delivers the payload from the server-side hash factory. Cerber is able to bypass legacy virus scans to infect a protected machine, even if the antivirus is up to date with all the latest signatures, by morphing its hashes every 15 seconds. This kind of automated morphing of hashes is not unknown, but the speed at which Cerber operates is new and concerning.
Cylance's Threat Guidance team took a closer look at a number of Cerber samples to find out exactly how this ransomware functions.
Mechanisms of Cerber
Infection: Cerber is primarily spread via weaponized Microsoft Word documents. These documents contain malicious macros that leverage Powershell. These are usually sent by email during phishing campaigns. Cerber can also spread by utilizing any one of dozens of different infection mediums, including peer-to-peer (P2P) networks such as Torrent, via fake apps and software or software updates.
Market Share: According to a recent report by Fortinet, Cerber is now the third most common form of ransomware for the first half of 2016, representing 24% of the market behind CryptoWall, which has 41%, and Locky, which has 34%.
Distribution: Cerber is offered on the side as ransomware-as-a-service (RaaS), allowing wannabe cybercriminals who may not be very tech savvy themselves to capitalize on the destructive capabilities of the ransomware. The RaaS option allows those seeking to utilize Cerber for monetary gain to connect with the original malware authors via a closed secure forum. For a low payment, the aspiring malware propagator can then log in to a basic user management portal, where they can set up and manage their own Cerber ransomware campaigns.
Exploit Kits: The Cerber payload can also be distributed by means of exploit kits, such as the Magnitude and Neutrino exploit kits. An exploit kit is a separate piece of software, often offered as a service, which can be attached to a hacked website. The exploit kit lies in wait until a vulnerable victim comes along, such as a user with on older operating system or software that has not been updated with the latest security patches. Exploit kits penetrate vulnerabilities in unpatched software such as vulnerability CVE-2016-1019 for Adobe Flash Player. The major exploit kits can cost thousands of dollars per month, so they are typically used by larger crime syndicates or particularly successful ransomware distributers.
Affiliate Program: According to publicly available reports, Cerber also runs as an affiliate program. Cerber distributers willing to promote and spread the program can earn up to sixty percent of profits, with a five percent bonus for each new Cerber distributer recruited. The rest of the profit goes directly to the original malware author.
Geolocation: Cerber currently restricts itself to target specific countries based on their geolocation. Up to 50% of Cerber infections were traced to the U.S., with victims also targeted in Taiwan, Japan, Australia, Brazil, Portugal, Spain, Malaysia, and Germany. Research investigators currently believe that Cerber originated in Russia, due to the fact that the ransomware will not infect users in Russia or in neighboring countries such as Uzbekistan, Moldova, Armenia and Kyrgyzstan. This is most likely to avoid being caught by local law enforcement agents. Cerber even checks to see what language the user’s keyboard is set to, and will not execute if the country of origin is the same as the malware author’s home country.
Cerber: Sequence of Infection
Our threat researchers took a look at a number of Cerber samples to determine exactly how the ransomware gains a hold on the victim’s system. We had an interesting time downloading these, as each hash delivered by the hash factory is different than the one before it, making duplicating our experiments difficult. Here’s what we found.
Cerber is downloaded to the victim’s computer when the user opens an infected Word document, usually recieved via a phishing campaign. The ransomware is dropped in the user’s application data folder:
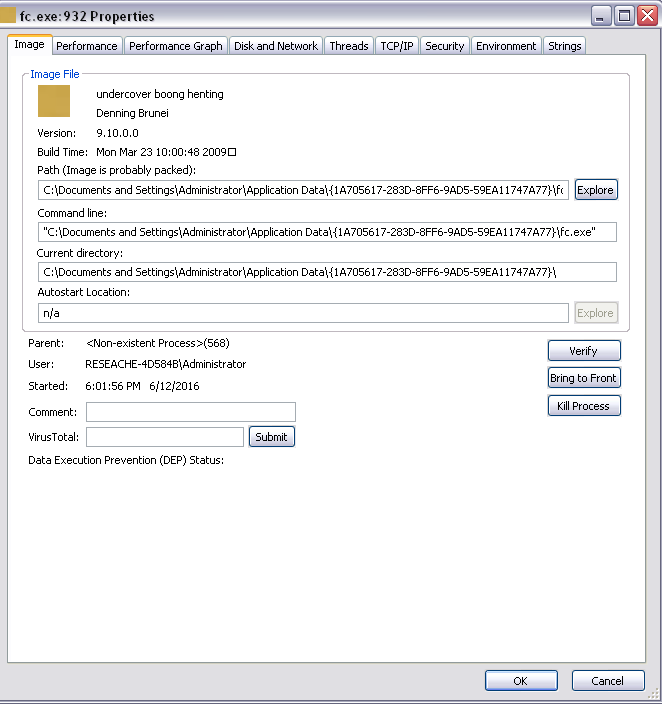
Figure 1: Cerber Gets Dropped into the User's Application Data Folder
This is where Cerber creates the following mutex:
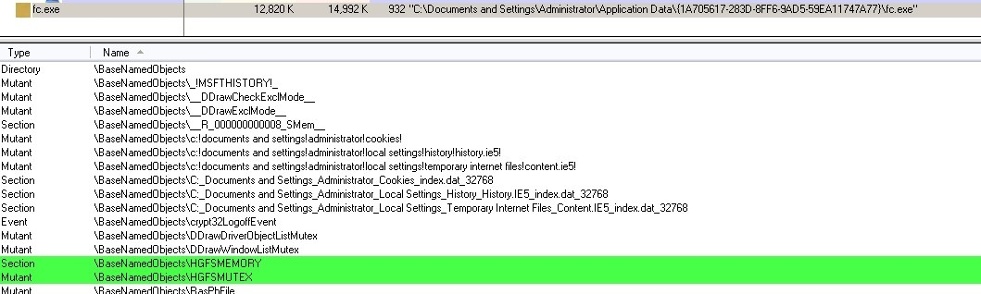
Figure 2: Cerber Creates This Mutex
The mutex can be considered as a placeholder; it simply prevents the payload from running more than once.
Cerber then queries ipinfo.io to fingerprint the exact location of the victim, as shown below:
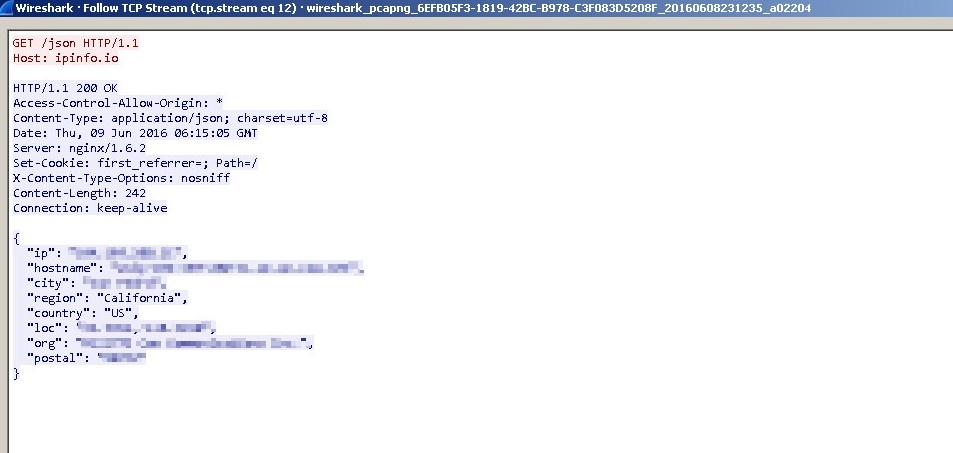
Figure 3: Cerber Queries ipinfo.io to Fingerprint the Location of the Victim - Part 1
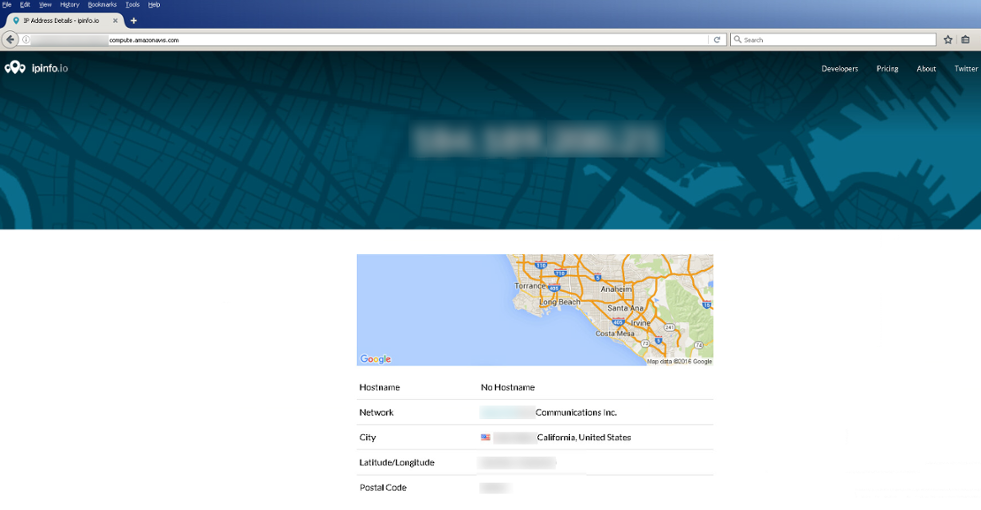
Figure 4: Cerber Queries ipinfo.io to Fingerprint the Location of the Victim - Part 2
Next, Cerber encrypts the victim’s files with advanced encryption (AES-256 and RSA). It then replaces all common file extensions with a .cerber extension:
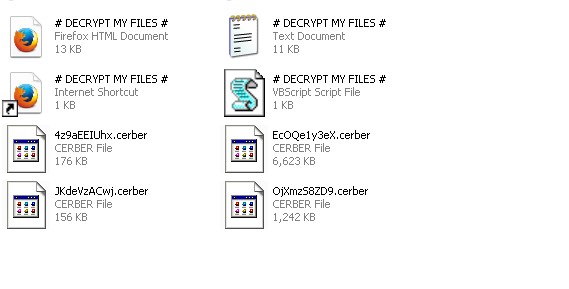
Figure 5: Changes the File Extensions to .cerber.
Once Cerber verifies the target’s geolocation, it proceeds to delete shadow volume copies so that the computer cannot be restored from a backup:
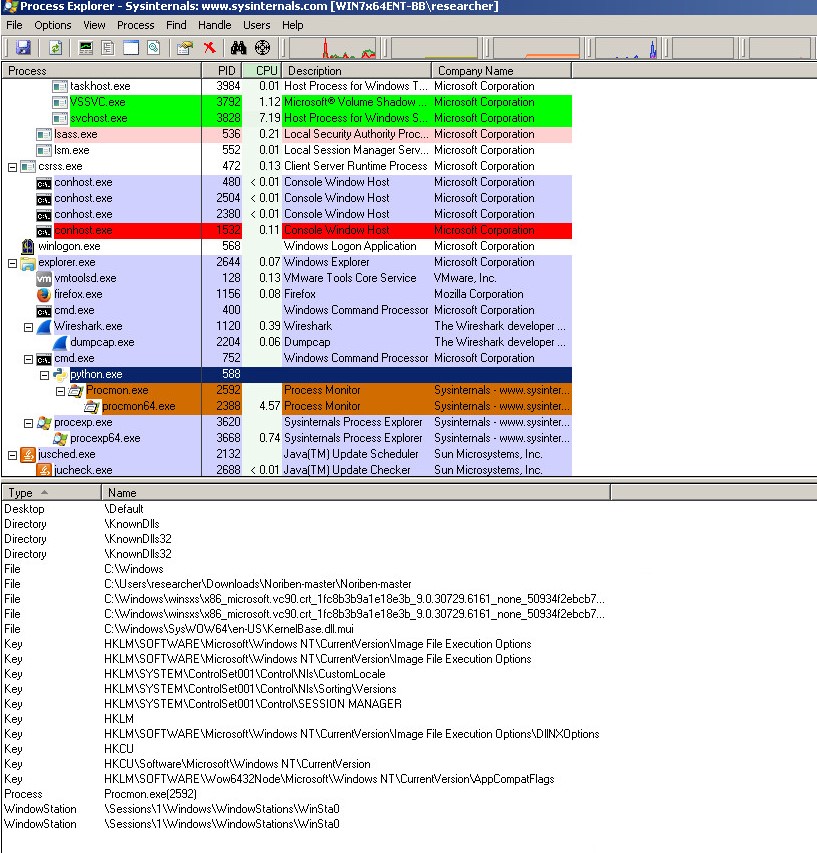
Figure 6: Cerber Deletes Volume Shadow Copies
Once the user’s personal files are encrypted, Cerber executes a Windows shell script that drops a Visual Basic script:
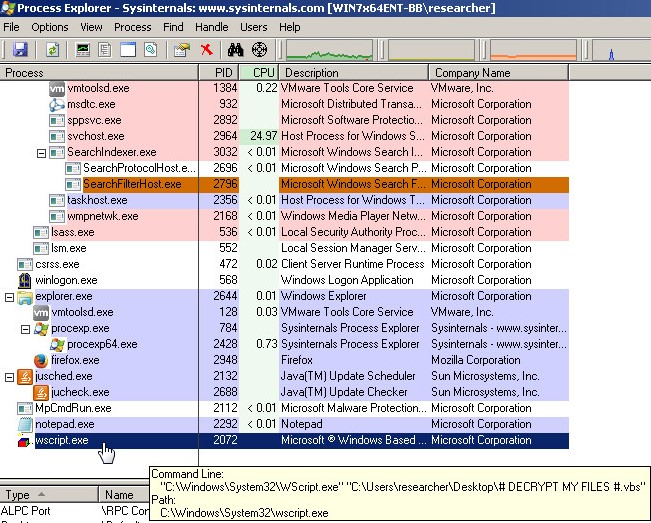
Figure 7: Cerber Drops a Visual Basic Script
The Visual Basic script is used as a scare tactic by connecting to the computer speakers and directly speaking to the victim, alerting them that their files are encrypted – which, as you can imagine, would cause a great deal of alarm.
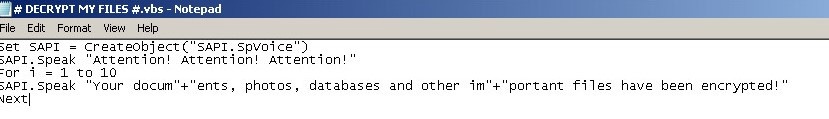
Figure 8: Cerber Alerts the Victim That Their Files Are Encrypted
Next, Cerber displays a ransom page in both .txt and .HTML format, demanding that the victim pay a ransom in the cryptocurrency bitcoin. The ransom note is also delivered as an audio message. A special discount is offered if the user agrees to pay within a certain timeframe, after which the price of the ransom doubles:
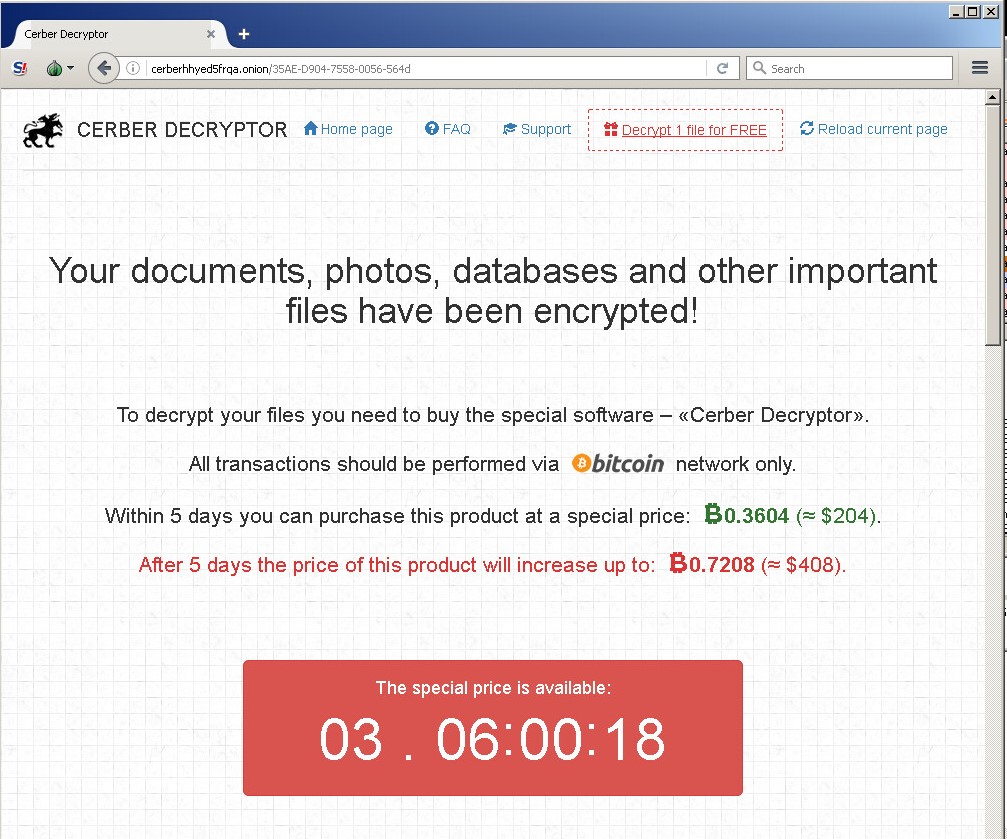
Figure 9: Cerber Ransom Note: Victim Must Pay Up in Bitcoin
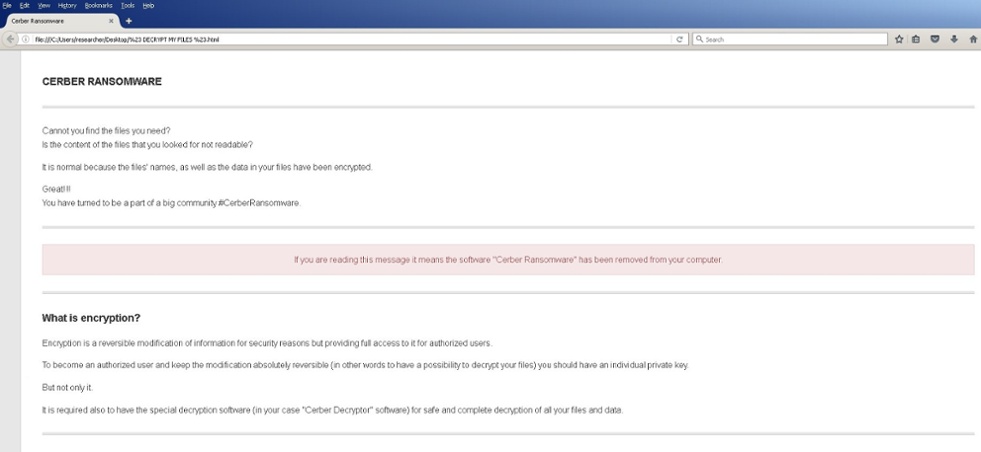
Figure 10: Cerber .HTML Ransom Page
Cerber authenticates a channel to 85.93.63.229 using CS-Auth-Svr. Below are network details that are associated with Cerber activity:
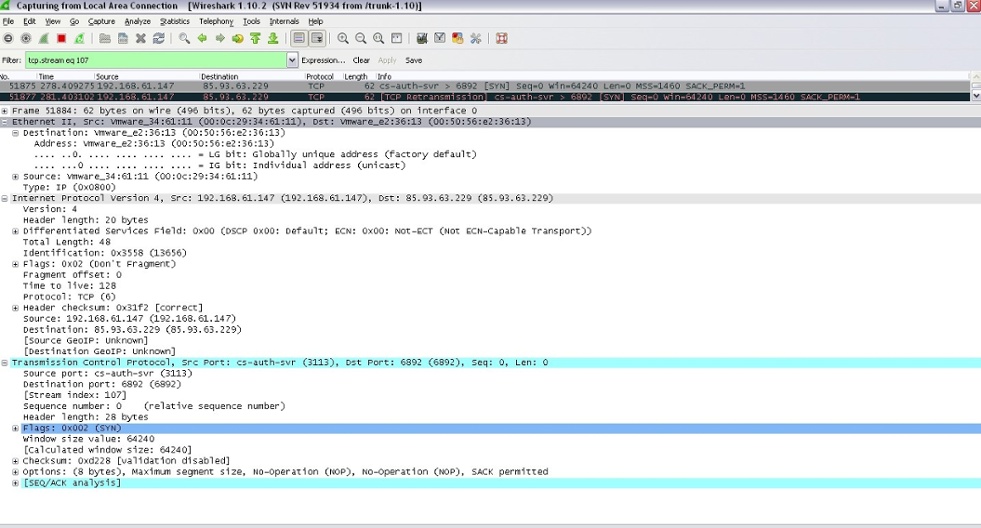
Figure 11: Cerber Connects to 85.93.63.229 Using CS-Auth-Svr
Cerber then builds and establishes a listener service called d2000webserver on port 3120:
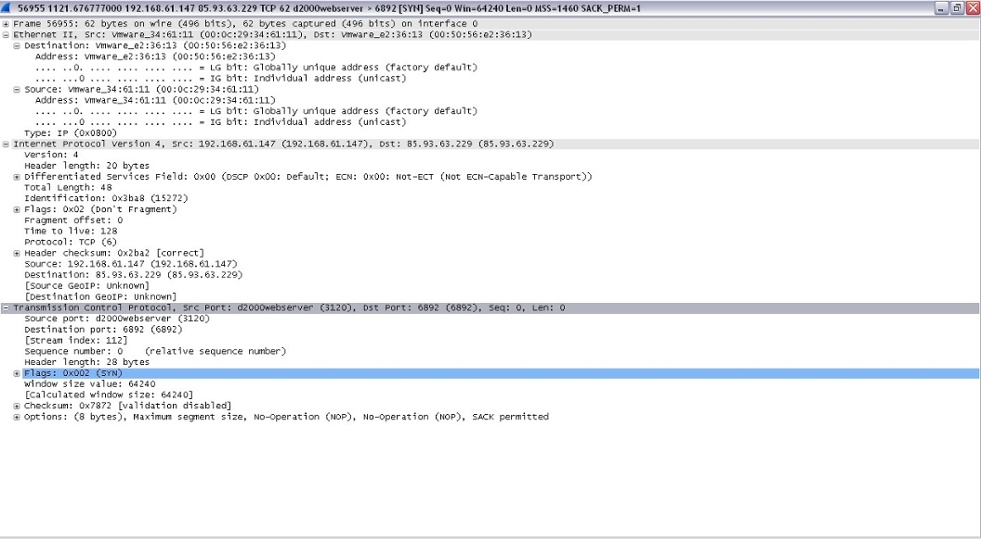
Figure 12: d2000webserver Associated With Cerber Activity
The IP range that was discovered was: 85.93.0.0 - 85.93.63.255. The Port that the payload communicated on was port: 6892. The services that were established were: autocuesmi, autocuetime, and sim-control. These services allow the criminal to send remote commands to the victim’s system, including sending a distributed denial of service (DOS) attack.
Introducing the Cerber Hash Factory
Cerber uses a feature called Malware Hash Factory which sends automated assembly code to generate unique file names and hashes every 15 seconds, like this:
The first picture represents how the infected computer checks in with other zombified computer systems:
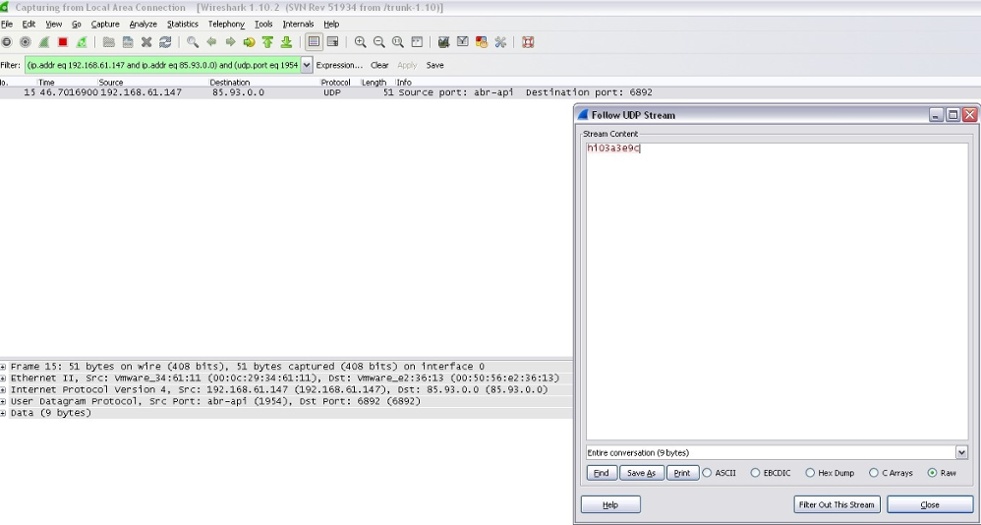
Figure 13: Infected Computer Checking in With Other Infected Computer Systems
The second picture represents how the infected computer transfers data between the C2 server and the computer:
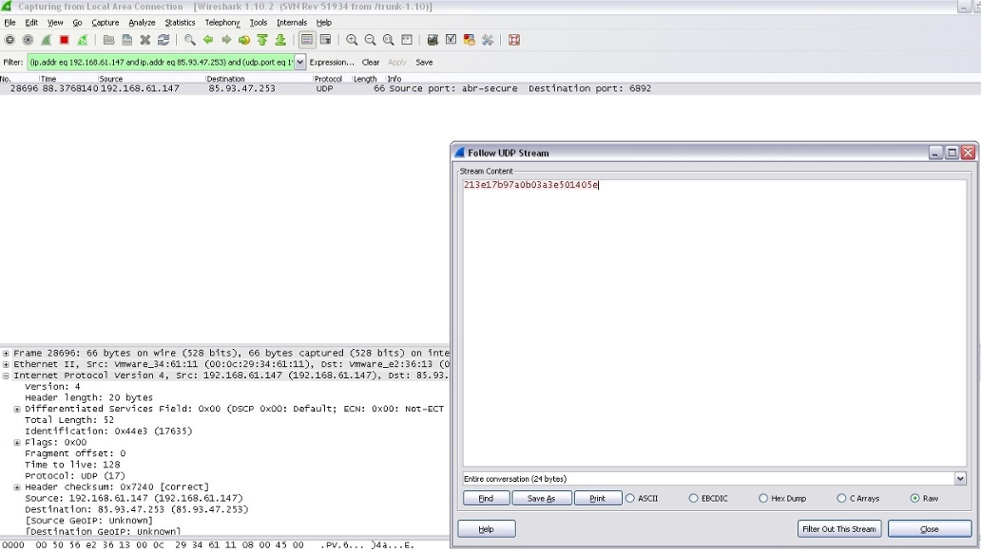
Figure 14: The Infected Computer Transfers Data Between the C2 Server and the Computer
Preventative Steps
With the average cost of a ransomware infection averaging from $1 million to $10 million for large corporations, security training needs to be looked upon as an investment into every company’s financial and branding health. The rise of near-untraceable cryptocurrencies such as bitcoin, which is regularly used in ransomware payments, has made ransomware one of the fastest-growing threats today, with losses of up to $1 billion predicted in the U.S. alone in 2016.
Government agencies such as the F.B.I. have publicly stated that ransoms demanded by the Cerber malware authors and other similar ransomwares should not be paid, but faced with the loss of irreplaceable files such as medical records, important client projects, or a lifetime’s worth of digital photos, both home and business users face the near impossible task of placing a monetary value on their digital ‘life.’
In order for business leaders to protect themselves and their companies against Cerber ransomware, leaders should implement a company-wide security-awareness training program. This should include staff training on the basic mechanisms used by cybercriminals to spread malware, such as spam, phishing, spear phishing and social engineering so that employees can be properly armed with information on how to safeguard themselves (and their companies) from these types of attacks.
The Role of Malicious Macros in Cerber Infections
Cerber relies on you as a user making a mistake that allows the ransomware entry to your system. In order to prevent a Cerber infection in the first place, treat all attachments sent by email with suspicion, especially those from unknown sources.
That much being said, remember that cybercriminals often study corporate targets for many months before striking. They may intercept corporate communications, learn the internal workings of the company, then take the time to fashion a fake email or announcement that looks identical to a real piece of corporate communication sent by top management. They may even study company social media to learn small nuggets of information such as the fact that the sales team is currently travelling – anything they can use to make the email appear more authentic.
The takeaway is if anything seems “off” to you about an email, always trust your intuition and check with your company HelpDesk or IT team before opening any attachments. Disabling support for macros in documents downloaded from the Internet is also advised, as Cerber utilizes weaponized Word documents in many cases of transmission.
In addition, exercise great care when running software that isn’t digitally signed by a trusted source. If you’re downloading a new app, make sure you source it from the official Apple App Store or on Google Play. As an additional precaution, check out reviews for the app before downloading. Malicious apps can (and do) make it into the official app stores, and may remain undetected for a length of time. A fake app for a popular brand such as Pokemon Go will have a suspiciously low number of reviews which may be written in bad English, often a telltale sign that they are fake reviews left by the scammer.
The best, and cheapest, defense against ransomware is to regularly back up your files and keep your software up to date, including your operating system. Servers should not be overlooked in any preventative updating that takes place. Many types of ransomware can spread and propagate themselves through an entire network in a matter of seconds, so if you choose to backup to an external hard drive, always keep these backups disconnected from your main machine once the sync is complete. Do not leave backups such as USB drives physically plugged in or the infection may spread to the backup.
Reporting Ransomware
The F.B.I. has recently released an alert which encourages victims of ransomware to report infections. This request is intended to “help the government gain a more comprehensive view of the current threat and its impact on U.S. victims”.
Victims are encouraged to report the following information:
- Date of infection
- Type of ransomware (if named in the ransom note)
- Method of infection – such as an infected email, etc.
- The malware author’s bitcoin wallet address
- Ransom amount asked for
- Ransom amount paid (if any)
* Any further comments or observations about the infection
You can report a Cerber or other ransomware infection to the F.B.I. by visiting the Internet Crime Complaint Center at www.IC3.gov.
Help! I’m Infected With Cerber Ransomware. What Should I Do?
At the time of this research, there are no available public decrypters for Cerber. A number have been made available along the timeline of the ransomware, but unfortunately each vulnerability has been patched in turn by the malware authors.
Should you pay the ransom? That is up to you to ultimately decide for yourself. Doing so is not recommended by security professionals, and the F.B.I. has strongly advised against it. Why? Because you are handing over your wallet to the mugger. On top of encouraging cybercrime by paying up, you have absolutely no guarantee that you’ll get your files back, even if you pay whatever ransom is demanded. Often, the malware authors may then raise the price or demand a second payment, should you clue them into the fact that you have the ability to pay.
If you don’t want to pay the ransom demanded by Cerber to restore access to your files, the only no-cost option you have is to unplug your machine to prevent further damage being done, and wait. Further decryptors may be made available in the future, so remain vigilant and check the Internet regularly for updates. Setting up a Google Alert using the keywords ‘Cerber decryptor’ may assist with this process.
If you are currently infected by Cerber and need your machine up and running again ASAP, you do have the option of enlisting the help of a professional computer recovery firm. But if you don’t have the cash to splash out on a recovery firm, your last option would be to try to restore your machine completely from a backup. Be aware that launching System Restore will irrecoverably wipe ALL of your personal files, documents and settings, even if they are encrypted. Also be aware that even though restoring the computer to its factory settings may restore the full operation of your computer, it won’t decrypt your personal files – instead, it will wipe them for good.
Once you are sure that all trace of the malware has been cleaned from your machine, you can guard against future attacks by clienting your environment with an endpoint protection product such as CylancePROTECT,which will detect and quarantine Cerber pre-execution, should it be downloaded again or if it is lurking on one of your backup drives. See below for a demonstration of how CylancePROTECT stops Cerber from taking hold of your network in the first place.
CylancePROTECT vs. Cerber Ransomware
We tested CylancePROTECT against files associated with the Cerber ransomware hash factory. The server associated with this particular attack morphs the payload it provides to victims every 15 seconds in order to avoid detection. This is a case where any endpoint protection software powered by signatures will have a tough time keeping up.
It is worth noting that the latest version of CylancePROTECT features Macro Script Control, which blocks malicious macros before they can run. This is of benefit when a ransomware which relies on macros is accidentally downloaded by the user.
We started the test by extracting the malicious Cerber samples to our desktop in order to be analyzed. We kept the CylancePROTECT events window open during the test, so that we could watch the progress of the files.
As you can see from the screenshots and video below, CylancePROTECT’s file watcher detected and quarantined all Cerber samples, pre-execution, and the endpoint was protected: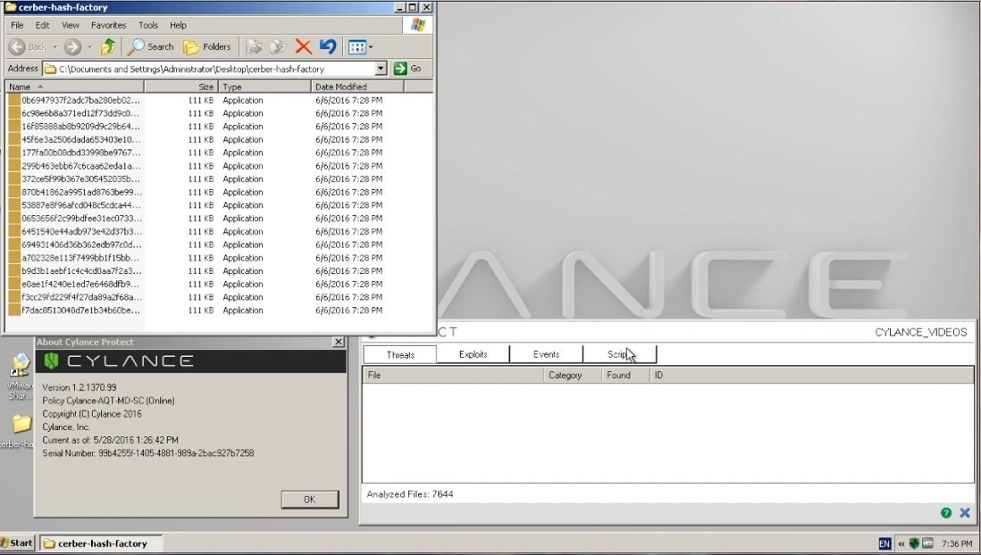
Figure 15: Live Samples of Cerber Ransomware Are Dropped Onto the Desktop
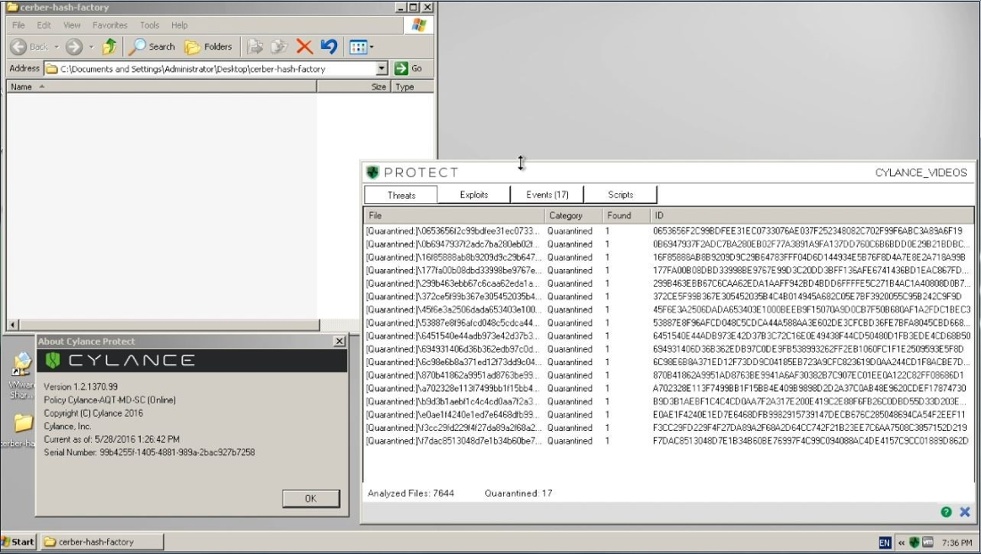
Figure 16: CylancePROTECT Instantly Moves All Malicious Cerber Files to Quarantine
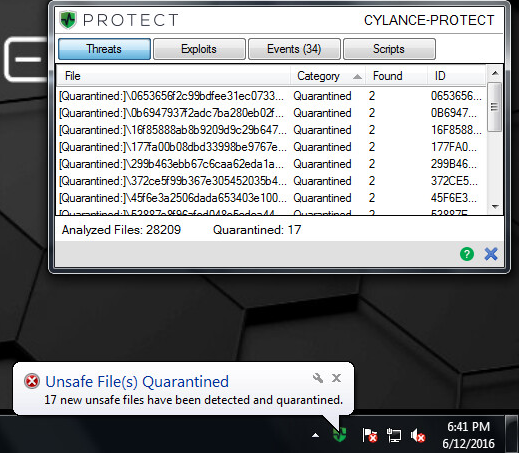
Figure 17: CylancePROTECT's File Watcher, Showing the Quarantine of Cerber
Our malware researchers made this short video to demonstrate the 'silent' power of CylancePROTECT vs. live samples of Cerber ransomware. Enjoy!
Indicators of Compromise (IOCs):
0653656f2c99bdfee31ec0733076ae037f252348082c702f99f6abc3a89a6f19
0b6947937f2adc7ba280eb02f77a3891a9fa137dd760c6b6bdd0e29b21bdbc51
16f85888ab8b9209d9c29b64783fff04d6d144934e5b76f8d4a7e8e2a718a99b
177fa00b08dbd33998be9767e99d3c20dd3bff136afe6741436bd1eac867fd5a
299b463ebb67c6caa62eda1aaff942bd4bdd6ffffe5c271b4ac1a40808d0b722
372ce5f99b367e305452035b4c4b014945a682c05e7bf3920055c95b242c9f9d
45f6e3a2506dada653403e1000beeb9f15070a9d0cb7f50b680af1a2fdc1bec3
53887e8f96afcd048c5cdca44a588aa3e602de3cfcbd36fe7bfa8045cbd66833
6451540e44adb973e42d37b3c72c16e0e49438f44cd50480d1fb3ede4cd68b50
694931406d36b362edb97c0de9fb538993262ff2eb1060fc1f1e2509593e5f8d
6c98e6b8a371ed12f73dd9c04185eb723a9cfc823619d0aa244cd1f8acbe7dc0
870b41862a9951ad8763be9941a6af30382b7c907ec01ee0a122c82ff08686d1
a702328e113f7499bb1f15bb4e409b9898d2d2a37c0ab48e9620cdef17874730
b9d3b1aebf1c4c4cd0aa7f2a317e200e419c2e88f6fb26c0dbd55d33d203ec47
e0ae1f4240e1ed7e6468dfb9982915739147decb676c285048694ca54f2eef11
f3cc29fd229f4f27da89a2f68a2d64cc742f21b23ee7c6aa7508c3857152d219
f7dac8513048d7e1b34b60be76997f4c99c094088ac4de4157c9cc01889d862d
Convinced that the next generation of endpoint security is right for your organization? Contact a Cylance expert to get started!

