As a security researcher, it's always exciting to discover new vulnerabilities and techniques used by malicious actors to deliver malware to unsuspecting users. These moments are actually quite rare, and it's increasingly frustrating from a researcher’s perspective to watch the bad guys continue to use the same previously exposed methods to conduct their malicious operations.
Today's example is no different. We discovered a malvertising campaign on Google AdWords for the search term “Google Chrome”, where unsuspecting MacOS users were being tricked into downloading a malicious installer identified as 'OSX/InstallMiez' (or 'OSX/InstallCore').
Malvertizing’s Bait and Switch Tactics
In 2015, Malwarebytes identified a malvertising campaign via Google AdWords [1] that targeted searches for "youtube". Affected users were redirected to a fake blue screen of death (BSoD) and instructed to call a toll-free helpline to resolve their issues, at which point they were duped out of hundreds of dollars to purchase a phony support package.
The malvertising campaigners bid on popular keywords to get their ads displayed at the very top of Google's search engine results page (SERP), then tricked users into visiting a malicious page instead of the legitimate page. Advertising networks allow ad owners to set their own display URL to provide the user with an idea of what domain they will visit, but do not rigorously enforce the requirement that the display URL matches the actual landing URL.
The good folks over at Hunchly discovered the same unscrupulous technique used on Facebook, [2]where malicious actors bought advertisements with legitimate looking display URLs which led the user to a fake webpage.
The malvertising campaign targeting users searching for "Google Chrome" on google.com uses a display URL of 'www.google.com/chrome'. However, clicking on the ad takes a user to 'www(dot)entrack(dot)space' and then redirects them to 'googlechromelive(dot)com' – a page offering a free download of Google Chrome. Even the URL displayed in the lower right hand corner when moving the cursor over the link shows the same legitimate-looking display URL.
Searching for ‘Chrome’ on Google displays a similar advertisement with the same display URL of www.google.com/chrome, which does in fact redirect to the legitimate Chrome webpage hosted by Google:
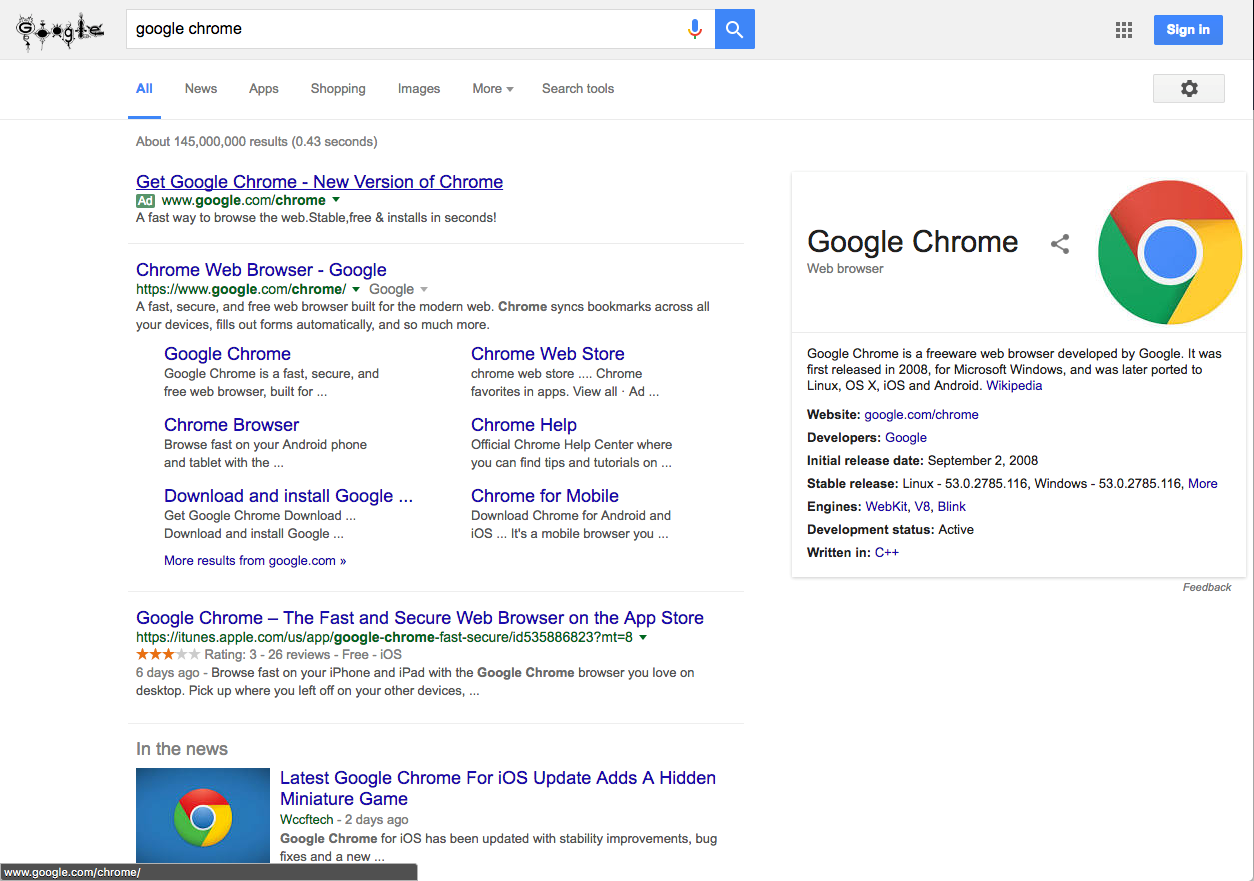
Figure 1: Google Search Results Page for "Google Chrome"
On the other hand, the malicious download link redirects macOS users through 'ttb(dot)mysofteir(dot)com', 'servextrx(dot)com', and 'www(dot)bundlesconceptssend(dot)com', then ultimately downloads a malicious file named 'FLVPlayer.dmg'. The malware hash changes on each download, making it difficult to detect and track.
Windows users are ultimately redirected to 'admin(dot)myfilessoft(dot)com', which returns an error due to a DNS failure.

Figure 2: Landing Page for googlechromelive(dot)com
OSX/InstallMiez
The OSX malware follows the same process that was initially documented by Intego [3] with some minor tweaks. An installer application launches purporting to install 'FLV Player.'
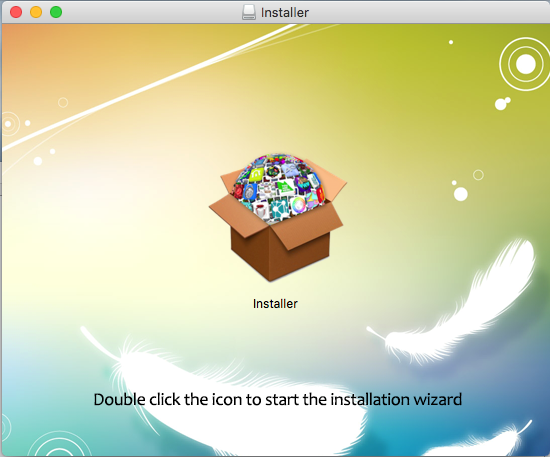
Figure 3: Downloaded Installer Wizard
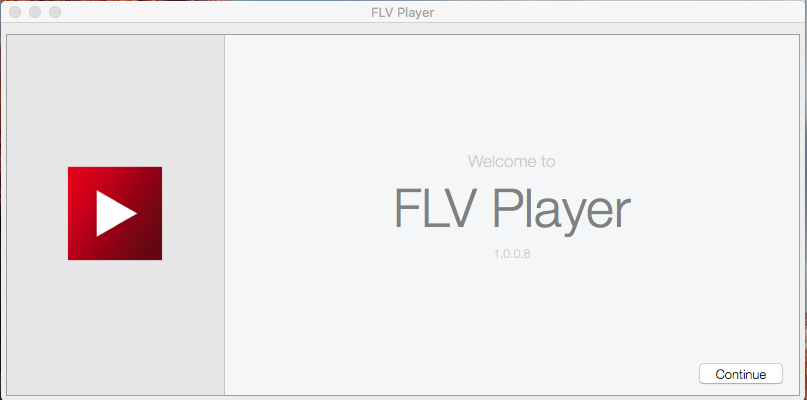
Figure 4: Fake FLV Player Installer
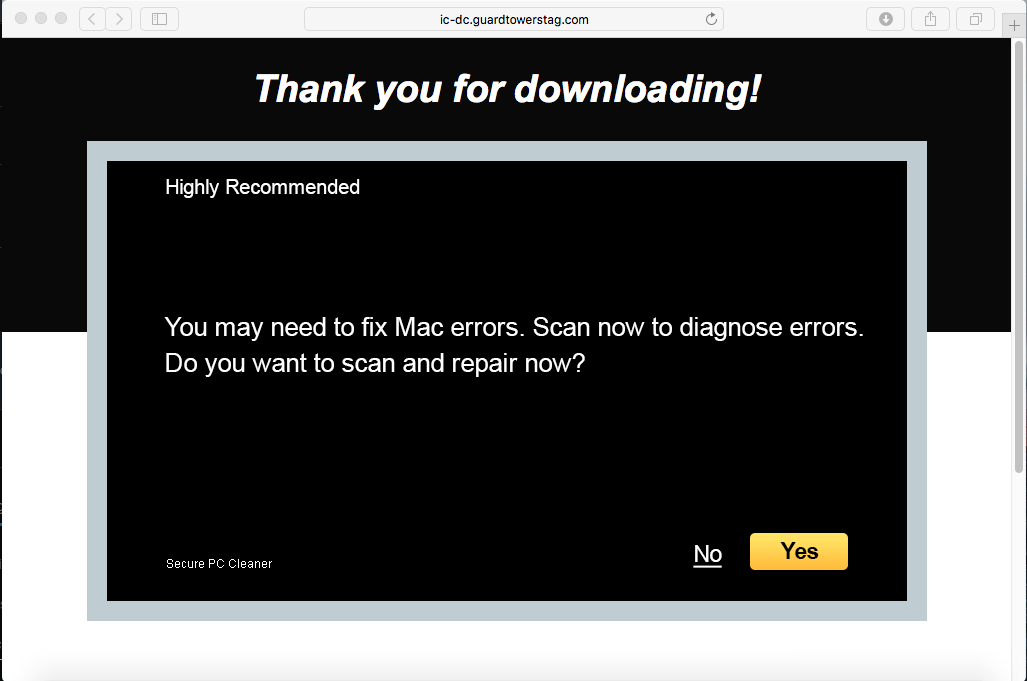
Figure 5: Scareware Page Opened After Installation
Once the installation is completed, the browser is redirected to a scareware page at 'ic-dc(dot)guardtowerstag(dot)com'. Clicking on the link takes the user to 'macpurifier(dot)com' – a potentially unwanted program (PUP) claiming to cleanup OS X computers:

Figure 6: Macpurifier Advertisement
Simultaneously, a download for 'fastplayer.dmg' is started and immediately opened, prompting the user to copy the "Fast Player" application into the Applications folder.
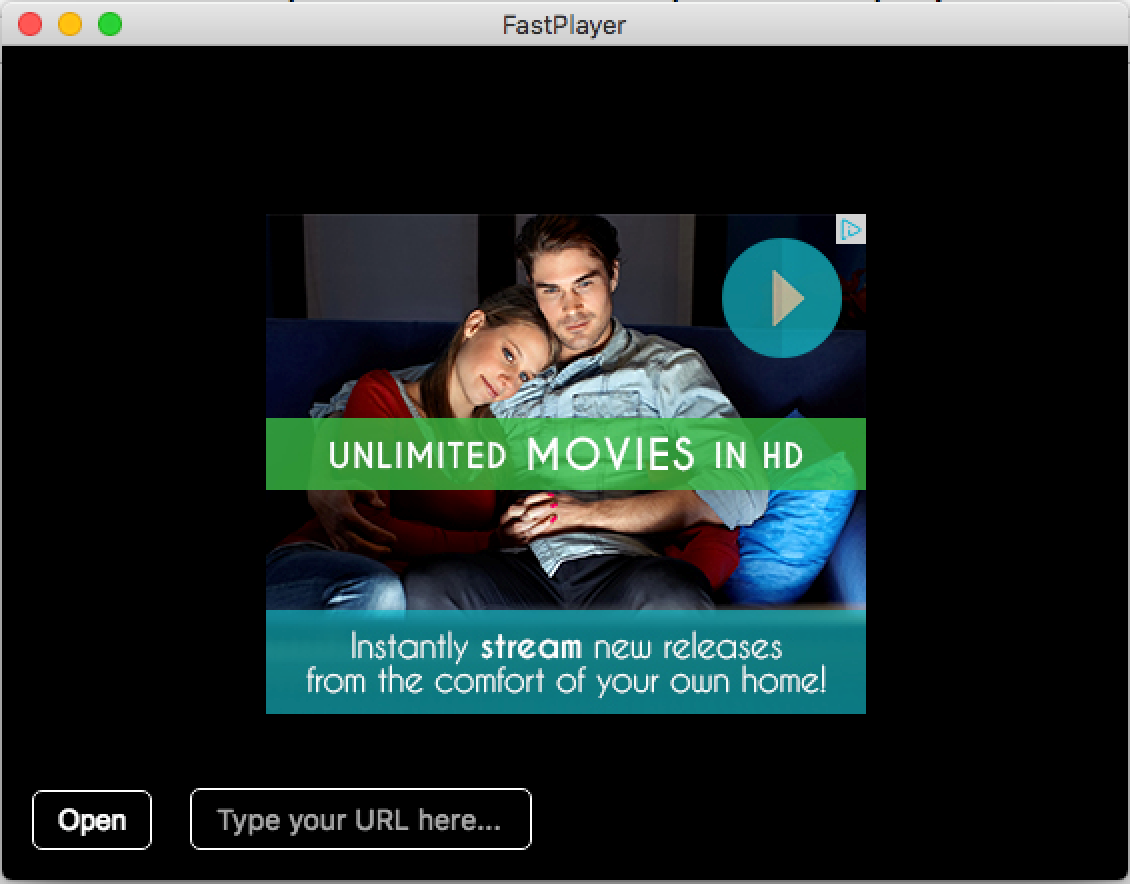
Figure 7: FastPlayer Application
Reporting
The malvertising campaign was reported to the Google AdWords team on October 25, 2016 and the malicious advertisement was removed immediately.
CylancePROTECT® vs. OSX/InstallMiez
We tested Cylance’s endpoint protection product CylancePROTECT against live samples of OSX/InstallMiez. CylancePROTECT immediately detects the OSX/InstallMiez installer and blocks it pre-execution, all without requiring an Internet connection or additional virus definition updates.
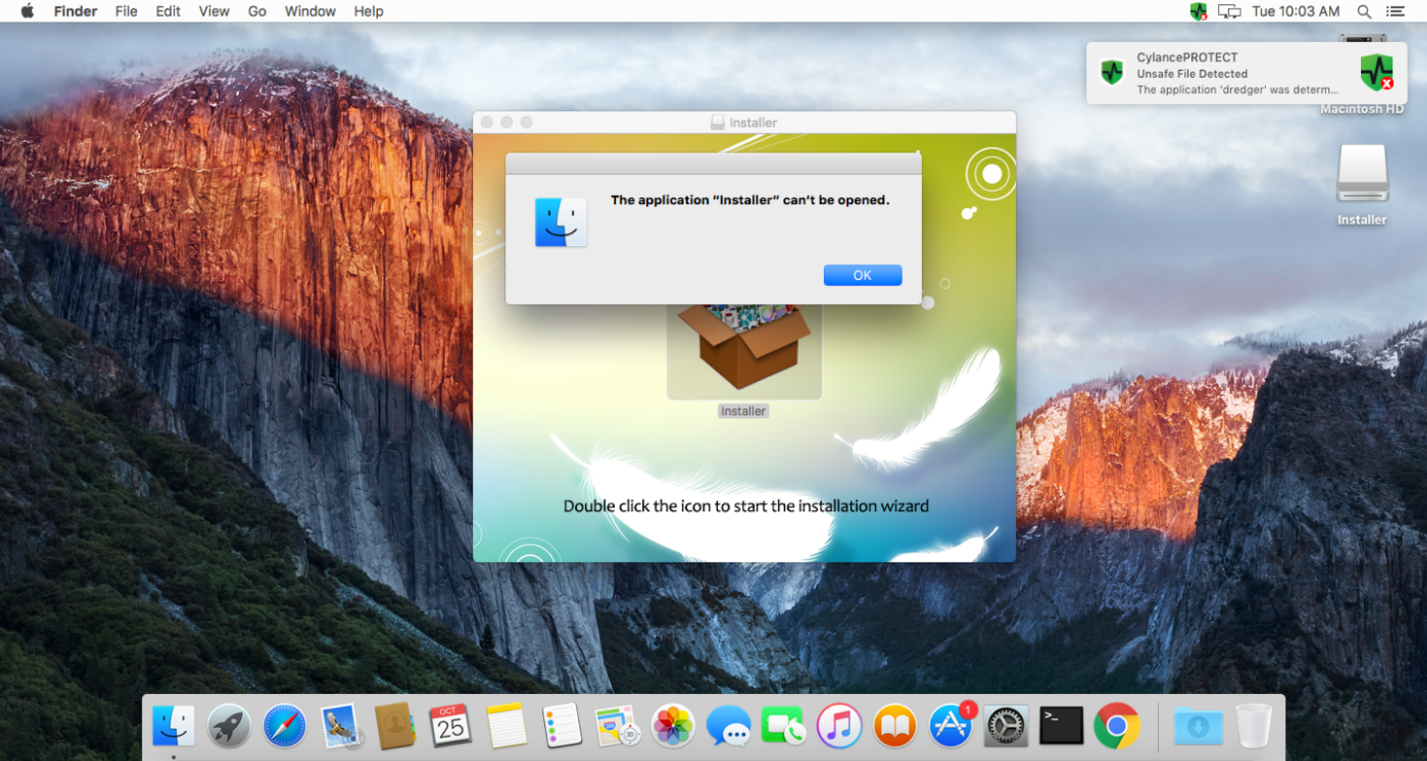
Figure 8: CylancePROTECT Detecting and Preventing Execution of OSX/InstallMiez
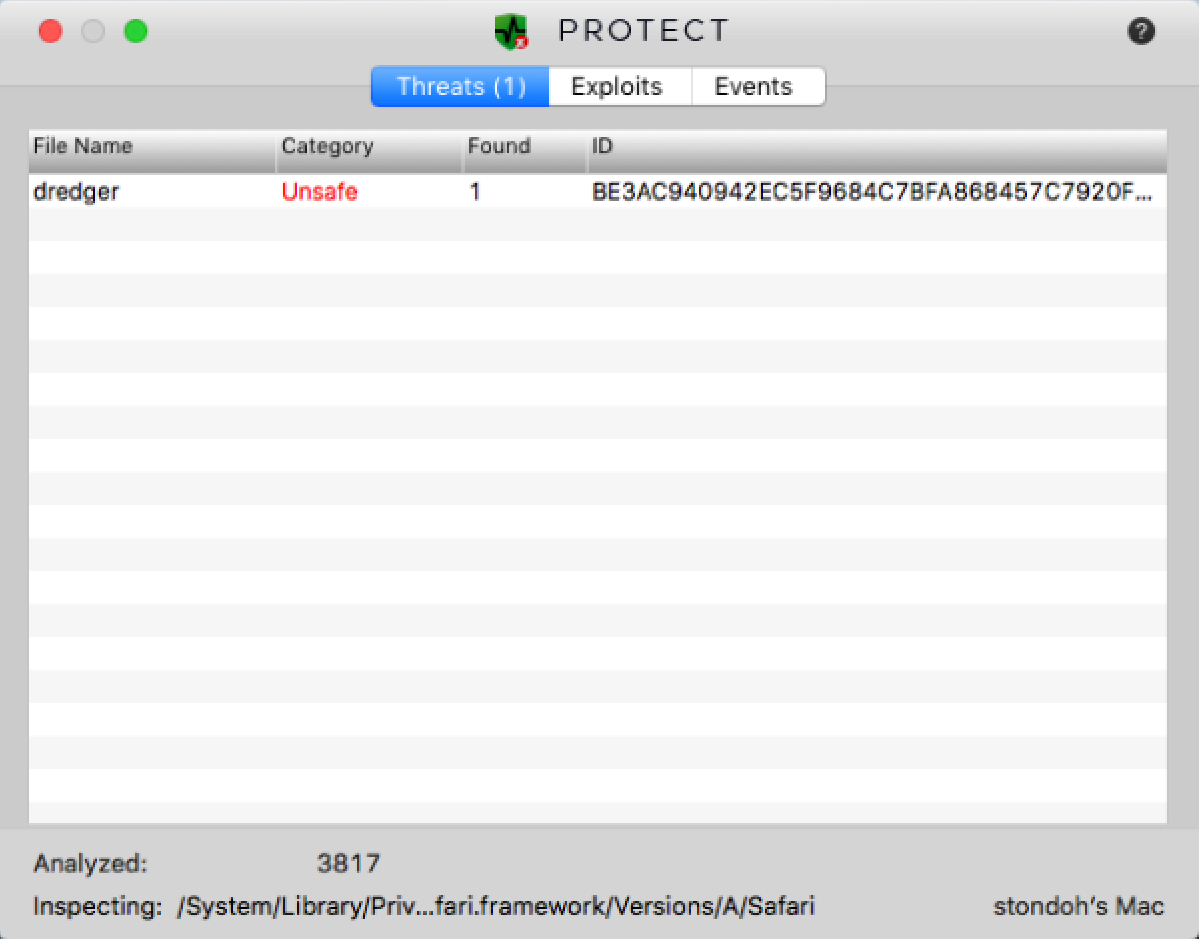
Figure 9: CylancePROTECT Detecting Dredger Malware, Pre-execution
Indicators of Compromise (IOCs) – Files
8a412dc97f953b7a061e90dd6ed8fb476eeadce6e8ab0175300a9f8ce146f846 - AssetsChanger
be3ac940942ec5f9684c7bfa868457c7920f863c438658aa7be50898da46fb19 - dredger
Indicators of Compromise (IOCs) – Network
www(dot)entrack(dot)space
www(dot)googlechromelive(dot)com
ttb(dot)mysofteir(dot)com
servextrx(dot)com
www(dot)bundlesconceptssend(dot)com
rp(dot)gugutug(dot)com
img(dot)gugutug(dot)com
ic-dc(dot)guardtowerstag(dot)com
104.238.250.96
Related Indicators Identified Through Passive Intelligence:
www(dot)googlechromedl(dot)com
downloadec(dot)com
myfilessoft(dot)com
mtrack(dot)space
ttrack(dot)space
abtrack(dot)space
webtrack(dot)space
ddtrack(dot)space
References:
[1] https://blog.malwarebytes.com/threat-analysis/2015/09/malvertising-via-google-adwords-leads-to-fake-bsod/
[2] https://medium.com/@hunchly/bait-and-switch-the-failure-of-facebook-advertising-an-osint-investigation-37d693b2a858
[3] https://www.intego.com/mac-security-blog/fake-flash-player-update-infects-mac-with-scareware/

