A new variant of the notorious ransomware Petya is back - again - and with yet another James Bond reference for a name: Goldeneye. Presumably from the same author of Petya, which was first seen in December 2015, and the Petya-Mischa combo, which hit users back in July 2016, Janus Cybercrime Solution’s latest creation is another step in the evolution of their ransomware-as-a-service expansion.
Petya is a form of ransomware that overwrites the master boot record (MBR) in order to block access to both the user’s files and operating system. Safe Mode access is also disabled. Once Petya executes, the user’s machine will crash, restart, and show a skull-and-crossbones animation before displaying a ransom note asking for payment in bitcoin (BTC) in order to decrypt the system.
VIDEO: Watch CylancePROTECT® do battle with live Goldeneye ransomware and block it, pre-execution.
VIDEO: CylancePROTECT vs. Goldeneye Ransomware
In this past week, the new Goldeneye ransomware variant has been seen for the first time, almost exclusively attacking hosts in Germany. Numerous organizations and enterprises have already been hit. Starting with a highly common infection vector, Goldeneye infects hosts via malicious email attachments.
Here is one case that masquerades as a job application:
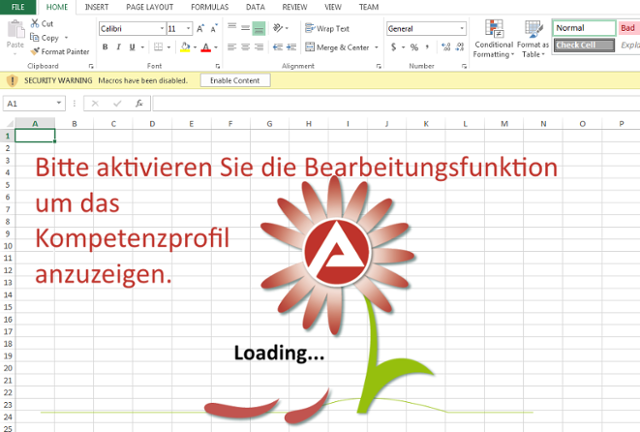
Figure 1: Image Text Above Translates to: “Please activate the editing function to display this profile correctly.”
(Translation Via Online Translation Engines).
Text displayed reads: “Bitte aktivieren Sie die Bearbeitungsfunktion um das Kompetenzprofil anzuzeigen.”
As with most malicious Microsoft Office documents, before the embedded macro can execute, user intervention is required. All MS Office documents since MS Office 2007 containing macros present a security warning to the user as default, so the malware author provides the text in the above image in an attempt to fool the user into clicking the “Enable Content” button.
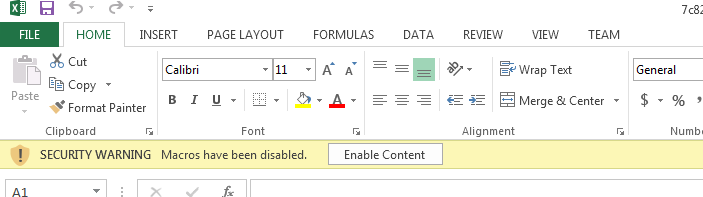
Figure 2: Microsoft Office Document Displaying a Macro Warning
Once enabled, the macro executes using the Workbook_Open function. The macro itself is also obfuscated, using a series of DIM declarations to store the malicious code and script. As you can see in the below image, the DIM statements are randomly ordered and assembled in the correct order only once run.
This macro contains several large portions of code obfuscated in the same way, each assembling a portion of code:
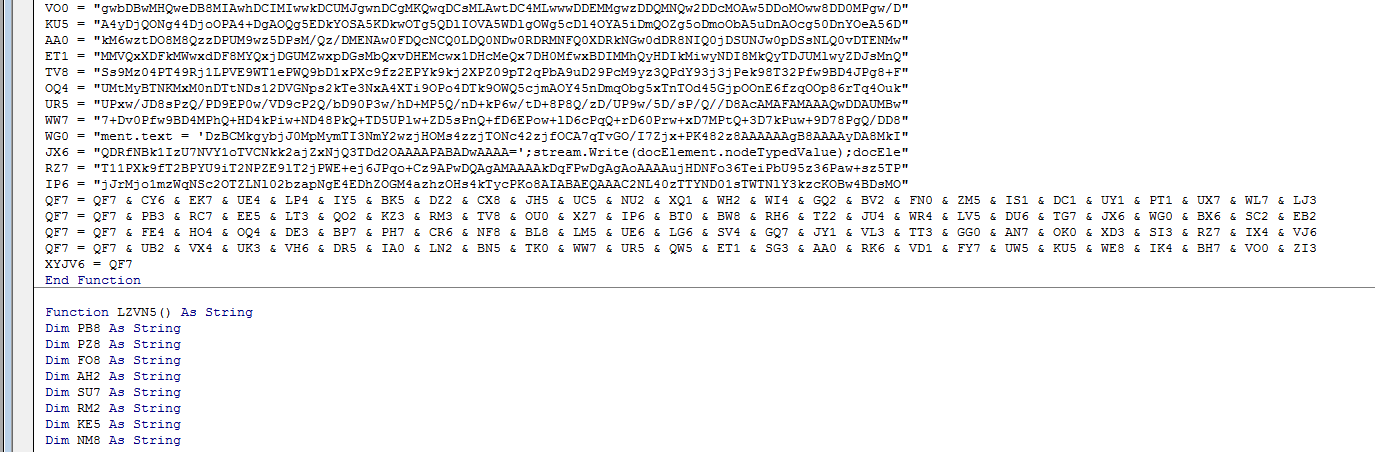
Figure 3: DIM Statement Displayed in Random Order Prior to Execution
Once this first stage of code assembly is completed, the main function of the macro assembles each of these large chunks into the malicious binary. Summing up to ~8,000 lines of code, this contains the Goldeneye PE payload.

Main Function Assembling and Executing Binary
This main function also contains the obfuscated code for creation of the Jscript object that will execute the payload. In the middle of this function is the code handling of the variable “AH2”. The first of which is the variable assignment obfuscated by using the concatenated results of the “Chr()” function. This function takes in raw ascii codes and translates them back to ascii text. The second use of the “AH2” variable also uses the obfuscation technique, and they both translate to:
Set AH2 = CreateObject(MSScriptControl.ScriptControl)
AH2.Language = Jscript
Once the malicious binary is assembled from the macro, it is executed using the “eval()” statement. This starts the next stage of Goldeneye: local file encryption.
How Goldeneye Encrypts Files
Similar to the Petya-Mischa combo, Goldeneye has the ability to encrypt files locally as well as overwrite the MBR. In Petya-Mischa however, Mischa’s encryption of local files only takes place in case of failure of the Petya MBR ransomware. In Goldeneye, the local files are encrypted before the MBR is overwritten, typically resulting in the system being hit by two doses of ransomware.
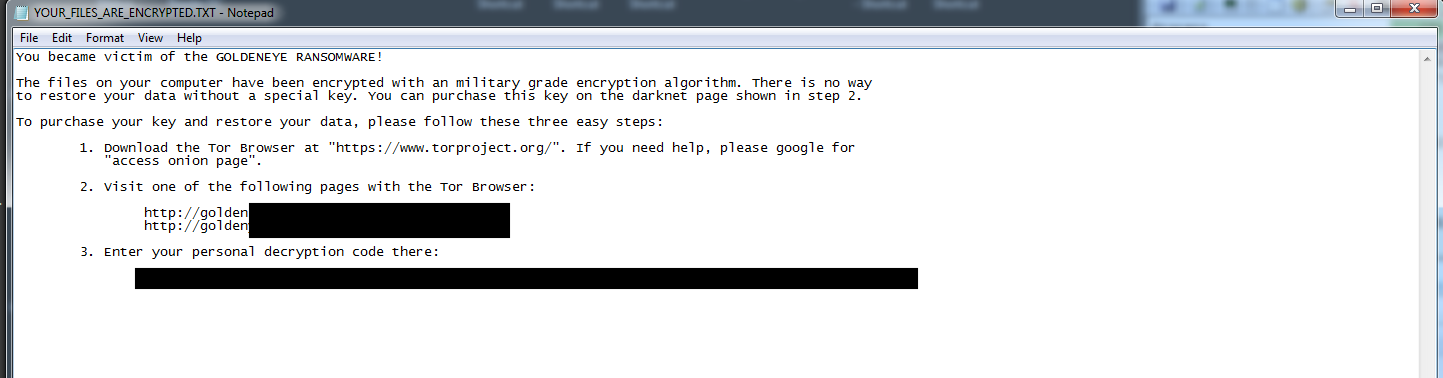
Figure 5: Goldeneye Ransom Note
Once the local files are encrypted, the Goldeneye ransom note appears for only moments before the MBR ransomware stage of Goldeneye overwrites the MBR, and restarts the machine to the usual fake “Check Disk” screen that is typical of Petya:
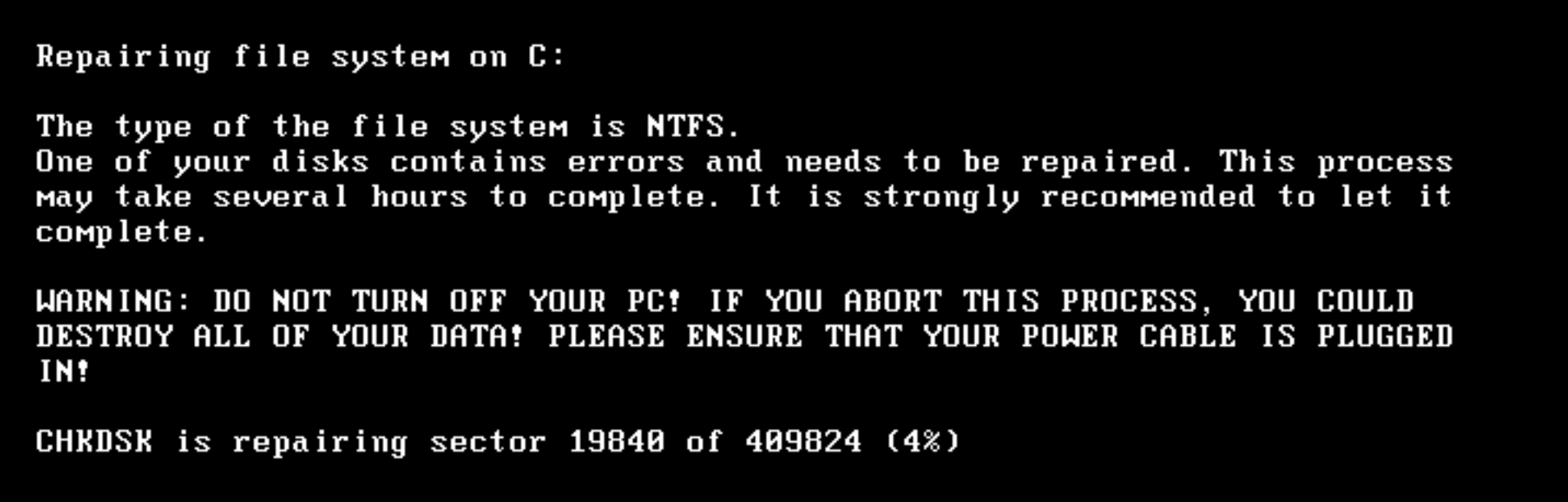
Figure 6: Petya’s Fake Checkdisk Screen
Once restarted or allowed to complete, the infected machine then goes to the iconic skull and crossbones ascii art of classic Petya, this time in ‘gold’ (yellow) text, and then displays the MBR ransom note.
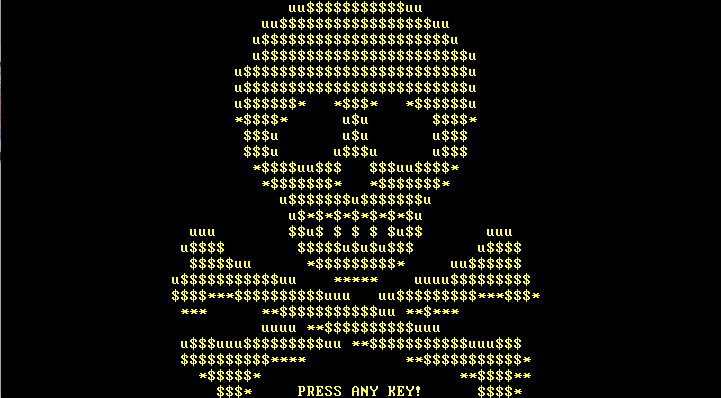
Figure 7: Updated Petya ‘Golden’ Skull and Crossbones Ascii Art
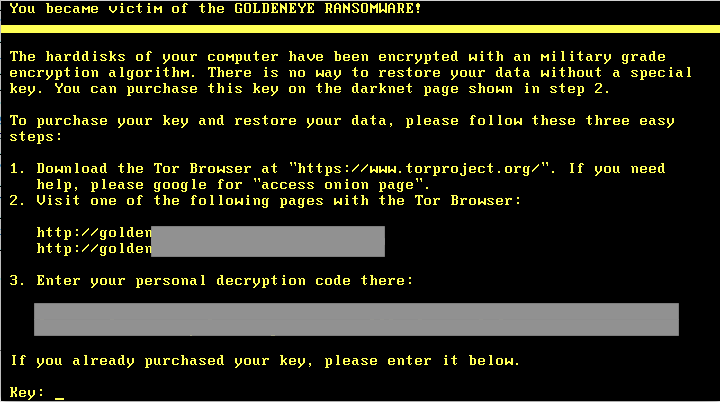
Figure 8: Goldeneye Ransom Note
Both the local file ransomware as well as the MBR ransomware come with a ransom of ~$1,000 USD. This is payable through the typical TOR address starting with “golden” and using bitcoin for anonymity.
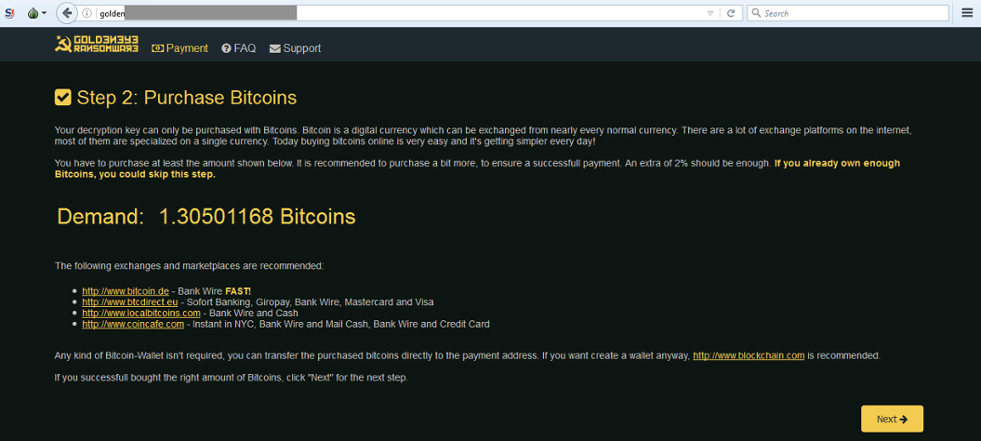
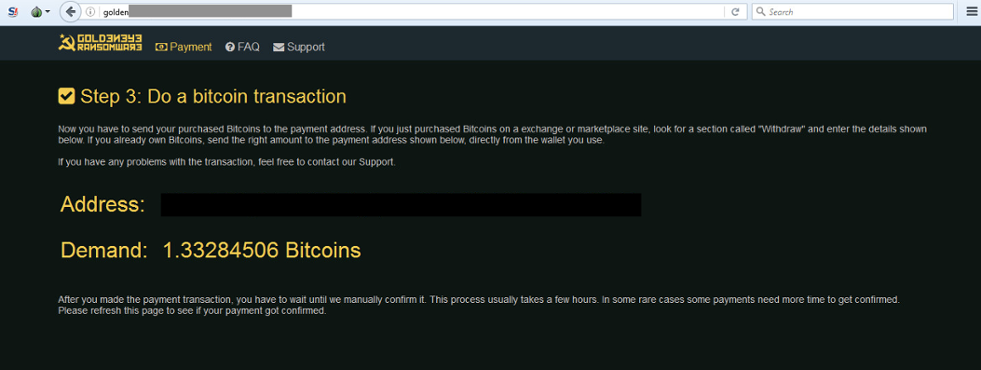
Figures 8 and 9: Goldeneye Ransom Payment Options Screens
CylancePROTECT vs. Goldeneye Ransomware
Cylance’s Research team tested over 300 samples of the Goldeneye ransomware against our flagship endpoint protection product, CylancePROTECT. Our artificial intelligence based mathematical model was able to prevent the execution of Goldeneye right out of the gate, stopping it dead pre-execution. The Goldeneye ransomware was no match for our math based technology.
Watch CylancePROTECT go head-to-head with Goldeneye in this video created by our Research team.
To make things more challenging, we are not actually using the latest version of CylancePROTECT in our demo. Here, we demonstrate the predictive nature of Cylance by using a version of CylancePROTECT created a full year before Goldeneye was even released. You will see in the demo that the version of CylancePROTECT we are using was built in October 2015 - version 1.2.1320.56.
Ask yourself this: would you trust your existing security solution to keep you fully protected after not updating it for a year? What about a week?
Watch the video, and decide for yourself.
Video Transcript
Demo System: Windows 7
CylancePROTECT Version: 1.2.1320.56 (1 year old build)
Demo 1: Goldeneye Executing on an Unprotected System
In this first demo, we used a ‘vanilla’ Windows 7 system without any sort of protection on it. As Goldeneye has typically been delivered via an extensive email campaign, we used an email delivery system to show the typical sequence of infection.
As you’ll see in the video, the attack begins with a seemingly innocent email being sent to the intended victim. Attached are several files, one of which is a spreadsheet. Before the user opens the spreadsheet to view the contents, they must first enable macros. When macros are enabled, a VBScript runs in the background to run the malicious Goldeneye executable.
Within a few seconds of the user enabling macros, the system will automatically reboot and Goldeneye will begin encrypting the MBR and the rest of the file system. The user is then given information on how to purchase the decryptor key. Goldeneye claims another victim.
Demo 2: Goldeneye Attempting to Execute on a System Protected by CylancePROTECT
Now that we’ve demonstrated what happen when Goldeneye executes on an unprotected system, let’s run through the same steps on a system protected by CylancePROTECT.
CylancePROTECT is configured with Script Control disabled. This is because we actually want to show you how CylancePROTECT fares against the Goldeneye dropper – not just the VBScript. Cylance’s Script Control would have prevented the VBScript from running in the first place.
In the video, we run through exactly the same steps as before on the unprotected system. However, this time, after enabling macros in EXCEL and allowing the VBScript to run, we see that instead of the user’s hard drive winding up encrypted, CylancePROTECT automatically quarantines the downloaded Goldeneye dropper file before it can execute.
With most legacy AV solutions, it may take days to weeks to provide signature protection against this specific attack. In the meantime, many users will become victims of the Goldeneye ransomware.
Even though the version of CylancePROTECT we’re using is one year old, it has completely prevented the VBScript from executing the Goldeneye dropper and has protected the system from this ransomware.
But don’t just take our word for it. If you’d like to try out CylancePROTECT in your environment, test it for yourself and let us know what you think. Contact a Cylance expert to get started.
Indicators of Compromise (IOCs):
Goldeneye SHA256 Hashes:
520c507b7f0343c612ed30844d470542a04560625651019db22dc7e516096255
71080f7b6ebb130affaebda2bc5c32d99779f019970405301385ffae896ad2e6
ea677e756966f221b622ca3a5a7e6c810e2491d1ead05b6712d6f90417f104e4
196c05948482a55d9b9f44c96b2390f1378acdfc214f46f3f8e0a7c1726362a7
7968f249fe3472931cc0795bcd951e88de6d0611395c7f2a436a30a563007ed8
7c8201efb2861bedffcc19eb91caef89c426bb4cb10dace6f13863a7a55f3396
48cad7d3696ea2c37d9f5b2744cc518d49209d5eb38744020c047c3179fae942
a07463f4165e41efc224d16498843533d293ff73f54eee1eddb26fca2b2433de
b5cf3676e56370d859f2d1f4a38978e7d55605efdcb6b992c9e95fc8e3e0ae87
929d8ebd6c1bd49e2103e9866b98a49c92f8fff7a456704977cf12196c7d7778
8b78d4122c571b391f7cce03d6e7de8c5cab4b2a1aec6adc2b72350a9051b2c1
b3b03935bc755e6444f907effa69d30b05ba994d67b7fe43bd12d5f2c1f8ed9b
5be3851cf4b63fcfbace4c967558f56350005c5b9413640bbacc9821acafc335
f0bb60343c08151e1cc2589a63ce2cb573dcf93181ae8228ffbcd4aaf06dd277
6b45d829035d916cc3c05f8150e1380832de243e5c2336fc6b50668dedc05b31
42a7b7e9e3943e5dc3c9139698bf0b455d37521094c5968b2eadb127c46afaf2
2a00ddfb883b40c9acff6dc35e52063b38663a17cd1f971c12ca675b2e11c774
bd49984c005a1d37bae0c4f600f29eff12841bec297b34458e228c5357ee6abf
0e0f72408d58405f9b09cc4f9dd828bd57e285bd3d099de7e36178a95114f070
1db193aeb389ad578cc0c3e6934b8f0d5e8683d1352437f78bfaaae53156ae5a
68eae10474f79966f74accb7487da30d673d6c5c1040a0ed5f58ae7860814981
e44adbd70a7f82a37e63d4cb1b18f1e0df3da2720062d914d1be695c555e5b7f
fc69b5f0a2bc6a83b226c5a1520eee973a46ece3479f14c61c1733e84d8bc369
e40ed47ace9afea91702ba6f70ba1bae0f3d0a6c3942c8dd218a59c2a09726f0
db847340786c8a949c80a78de4fb757dcdaace78717c3b1e59416948d5b508a0
cafa6fa8eb56c5a3cc34c2215618d30696493f191885021f35ae683265632751
10bf8972bc8de948aa7918461dd6bd1ab44349e563aa821cac4d1f32d633bb2e
2320d4232ee80cc90bacd768ba52374a21d0773c39895b88cdcaa7782e16c441
51db7151ea3e53376234d696ab3c17eaf532a839bb586eac5e58eaa4c89ec4f0
2bb64ef0c20168207d2133fd538d96e70b235dca640cccab512251c21eaf0889
c7ea3ed20a6934d13765b461ffa0bd493fa81c4b5f6ed26f8a4ec4152982731f
11fb0a42a14042fefce9b2879d93609faef5294507e93671f4056e939b91874f
d2dce1614d5d8e2b6d3aa5aba102ee5d360ff855848686385e8e7d133220937d
2f8579354b4ed65d292b15e64f91c9722d939587abf8d0cf4f695a4e370d5182
b1bf065e03d5faf74322d9ddda083a2f4c5d12f4d6080a791ec69ed0b709b3c8
cb4ba70ff52f16586033e5dc923754d493c8c897bd14848e9cb2417298790667
115be7d5d31c5494128cf7dd2ddb4eb1196f83cc95b1a118c97fbce89fd4b4a0
10ab73d8ecdc7d7d3ec01059347ce5e7aab5e3a8b64f0eea268fde044e806155
9c20d24705b3186ee6dd68d4291964b259b55c1b990a0e02099927580b4f3141
60d5b0c8a0815414badbb38a90abecd412105321cac0a6b71e5fc949d0e5d926
dc816988967417b79182c7691d6c882c38c9bc97ceee647ddf7075a811da52e6
0aa1bdad5b13decd65bed0514f0778d6ff9ba2337a5b5d4cdef1e84dd0b20b0c
0db3c3a5720792720d548c3b47f9eaac5d2d483a361a6ea40b26aac40e64ae66
051fa691b68b468e5a8862f05ebddcc83bcff6ddffeab143113ecd6625c96dd4
61c73c1610ff2c82e2d800ff2b0bbafa0d7d2460fb8fbf7358711eb5f559c26f
caa7ccdabc5738a149e14dc280008f736a2f8e67c80f501be2b49cb70e61b66c
45349981e919db14460cac23b290204903d4d6a7e13630f5069463d37fc0f2b7
75f5243ef823d8fcb924b16832e279bc89985bfb60ed439837548f68994619d2
5af79ce1172b27241374e0205453e56c5ddff1524337a8274f6ad3c756961ae3
9083aca9cc63f096e9580742a326424476f6757f668e1dc2beda8c7bc81e5dd3
5f3a07471409327d4dbc348d34601a8fbd5a0193a01750241af1021503d8bda9
e40a1a0ccb3bc30954416fddf4c5421cbd0d4ccc2f34a58fa4e648311a4068e8
6e59301b48103d96a9df61b033077fabb3fecb03a82a26995d1609681174afb7
936a1b72132d16b12e659c6c2a3371019486bfc579696c5612cc7555e40c1589
7f082e5c680716e934201461cbac987f169a64da1dd6108f506cdf4d4a87f833
871a331b9f92c7aeb97862d01f2c8cc92449ea06b1a62b0bed6e7add04046d53
c5dfdb1a2d55ad1f9218c3636448de9c899750a073e2e12206d33863b17d864c
fb58221d8d3c9b3ce61f47dea76c7ef70c9a68eaf685736f038638f5367c21ec
46461f829a51036bf143d5de6ce033a8be7000d6174e8a8f413ff38a08ba6628
5e90ec9900d87e36554eacb0ab45a797f5656edb0a010787ac7eac5b056e4e77
d31b1ada7c2a573624f10c542a69ed4b69d8ba63b933533213f1f1a9281b6b2f
82c74b02177b0f53ea5d16208d1f7ce5c90a945bc57396ac51c4a4baaded5a00
187bf89130622b170a51342405af0b911073da58434cbac0c0d86570f1002f67
9eb90ea2f55af7bc7cbb67290ec6d98272b63a597124637b3abedd24c5fd7e32
957dfa81b455c1a5e3584f88977e9a063d13fa4e85d7dedc1294529367677a3f
bcd8e3da91724796369a813fac4074674ac6cd37bf9306f536d745529a631803
7703805115f3614131961b1c709c6ba1ab6a2e2010c677fa822e16b134b02df6
aa777449e1deb36df600d8e16001d96bb82e756f125db2677c3f8469b4b61164
296f1738fbf1b1d27c56cacd2534cc61d056cd6fc61f2f3df609f6e001ebc2fa
cbc32680b9dc22714fd3cab27bf1069ee80e9f58deecd5cf04ae4c273b54fea8
4ad17b072dd6fbcbe6a3b10abf52a5ea26080dd3d96fbe4397488c46c8cee357
3e5e6f5b04757e7ca70b5103ec04b4c7914773357d5d728919f624d988c0321a
48caf5a32c2c8422c1abbc3c7f80d432b59db5c494cc21837189e1df361c7a10
2f211001f89cc71cbf29203999267c56aa68abb4208e604dabf7770c0070a7b5
9c081281e605d32fd2343efbecd08481d38e51aed8451baef3d866919d502a07
956fda741b03de19fb23afb24aee683b9ff441282f3f7b79d3e2d466d054aa8c
2dd153bc47f32a2c5b5e116fd146f986a4311d1da785c5fce7b5400fcba014a3
55ca2ce46d2a246cbc9dc504eb61e0a7a6767cbad958e0959762c3038d923ee5
138ef01b5df30d36770abde53a86f43593647ffabda13a2f95865380397b61f1
cd14894cb57a600606823fa9b6b8ed44cafabad805b4752f78790b888cdf0954
f079663117066b46d3f53d077d594e063d98bc4852d73f2279c4d9cfb25eff22
4e717ff0db9425b144d6be5e7152854652207b6b3dfcd914f1e8288830dde65c
c66e9d536e2b0a56bad088b92f44cdabb16ae6017e4eeae4eb0d194cbbb4eec0
6afa248e8392c28814eb26790fe5b338c6c980096e7619a3b2fa8d2799fb1097
30e8e179d8cdf77312322b3d9521c1ed664ae3ecd830a91538f3e09c92d8e108
deeecaa3a7866c3618ce4f21d0b98b6d7a174f741a8fb955b8161bde62f39da0
3daf8a25136eab32c126a73d2790afb0fe8d67d19cff30b0c1a6fc52afc0b0ad
421329327183608b7a2bf1bce83a839a1673e083ac9c86cb34d310cd9b1d4160
93935a4e927449ff728e963ad7d121956914b323658392207251e77b55b5e624
a0238dd66435c44cdb3e5ac361fa3ab59242b53fa26ebb917a9a9a7fd4a5987c
3ff2047460dd5261ce48c183151be33ee739fcf5bb2044a385560c2660c58304
239d93c3b7325666a0fc072791ad7b3d10d5862c57bee9d485d4e7b9a6feaea8
947768b85774ae11bd6487be74347b57069371c4c8e5a282410f201105b08ef4
6a876d1c0c9c67baeb6fbe4358bcfb58d95bffbdb5324496f14d39e2f9aa03a9
6d40cbac0065c7958d776bf27f6058c13dad43be7b381c035622acc8f15d7245
3feb336e6e4cab92765b8a4c79c039fd6b21c14642010210080fe9a0fdc3f1d0
21ebbe73b6ea5abaa6ef670dae7dc49618458522e856071a3455e5e80dbbe682
1bbef0d8934b6bd2190ada7e8d12cbfd1e3369edef129ffe619813915a93504b
e496359fb2d493daac6b9d7e6f0db670b7828e4a064a449f9c619c0440380ce5
a29819cc703e34cf89cc4f10b47296ff3d4164caec2ec6e053f4eff0ea14c16f
Goldeneye MD5 Hashes:
991a9fe9a76616699e29f909c7c5c3dc
d1efba25f4737556ccbff817c4684e81
22bd74b23c681a16e2390bcf69bba89c
7425d582473246b78d431b2709ce6734
e34600ef7ba677be5f805706a8d07bd8
ad79cb5828fba093134c35531f7c9215
e7dce8ecd38d550c231083c748ed9732
b32bf69955a36ac292e704b06ab044d9
234e5a2e704460060c0b7151b9530e76
b58d40537c54da4570c84571445c50bd
4da8dc9ca76bbbb81354b57aa165aac0
7236e770aeac15f237c9febc17ae64e4
6b160857daa1c515a12eff83513b7b9d
2c2f29cb501acf30db4d923904b6ac62
cbbb650fdf8bc1ceaa9407244f00f28b
dba35a3b30082d3f675b4082a168ecc8
cdb5f27da4cee39fc516beece0ca20ec
1554ada6364b9611e608575af9c46ba3
5c0382ec155f6a4dcf7777897e9e48c2
c65fab983e5f47e0d2eb74047b560b83
a20371dc3e0dd5fcdf9076ff591ceff5
bc5c7f3b583e2df16302825af4c235cc
4e80bbba8f88d751849c2ad231e7e3dc
af813168402e60cfdf7c78a0d70d86e9
7385a72641ca3e5c6bcb1e371f3c8b1f
da50fbc0552834869f467d5d3263b35c
8855dee52ba475c5287af576853a08f3
698c92594fc689c2b161daa5cbb5f445
e2ad29c71f3ce97601425cb538ebd041
97960518fac0ccfa080c668b1e1d6f7e
14dfbfca0a1f92263d0783739aa7532a
feb442aec8dc21abcdb49cd4d660cfa6
ae32d15a0f725a063831fa16bb4bab25
5364ebc5610fa7f87e218648cd832ccc
c2c9cd43ce5a6ef920778e5f66099edf
0aefc4d0b999557adb154af5f385d40b
83c7102a5067ecc9106b0ab6435feeec
17f4816ed0aa80b9cc559f26bdd5c09c
fde0ec504b4171218fdc25074d913887
8be9e8618a61c9052a916c1ec8095475
b231884cf0e4f33d84912e7a452d3a10
db18f4d58ea1406078a0ce3097455311
a4a98d88b8788020cc59e49753a04c7a
f1a858d35d42d5a57ef402121aced606
7b53ce64d575f0967130ca6f6dcd6b87
9207db63add726bf47f39f542187ed2d
51691037c4a521181494710ade1c7ff8
630a5e90257b3762f304e02368ab68ef
e6be88fd1942fca6de0c3adf7266e41f
0486775b5852fa55de45d080088dc189
5c123b6936b4bf0b29375fbf7411f5fd
a130d1b7ea18cf5be76e8fc76babfa08
911a54e80d925f88065a4c1aa205753f
baabdf9f58f8cbc482a47f10d95ae4be
3587e8f6c25c1f623951427dbbe57335
0c0ded5a76094db5fb47a5bf6b5168a7
4759d42b58a31d8563d5c3dcc0790467
66f54129ab00e04fe4ec1de65119df86
9e364db35a1cde6140d287143cef2c4f
9f35f48fb190be4257eb67ee5b12dadc
75649ec76079a925fffbeed3f31b40eb
10b438456d1085e776620a484379f5b9
a66a68cca92bcc8d8341fa42376d79ac
619d869e9503bb35ecc8515e69f01cb5
bc46dc609e94785c526b396236d6ca48
e1641c297d8c5d60f0f699f10f7a3b49
acc279b46d2e2dcb53bf7506a121b271
76c6659f71aedfdf8db573810160709d
a33399fd1a6586946658679e9b56888f
83322160d48b16602ae93c3cf161521a
0db960b5be45e5bd7ce143cef9e3ef06
fb81e7444838052a45c28d5af88a9dd2
26230a627d11766656e522007032e1b8
571502e5e49229bedc7159d7aaa9a29d
0119f6b5573f502c6259c2d9a90cae3f
42b581bc4e0c20202d44f7476e0899d0
b68d8bb4d7d119a717aea69320c1a597
07e8c721b6169741bf37b26f009e87e4
d8126f7fdfefb144b194230290670efe
f4e7d52e7ec7b3702fbaa00c2426f58f
8badc9fdc551e84c1a610cb8e8ce02a6
d7b7c0263b9827660536d56f0031dc06
19b06f1cb3da5182e6223a7c701ef879
2c219e996afb64954ccd792d38ae809e
2cf8960b838c4971b9f8cd939c2d90a1
7f05e7b9ef465ffacef3be8a070be489
56bca96efa93f11bc31e650b08ef3f30
0a79350220c915e79d161718a208343d
3b3697d6e087c26d02534158c55bd2b2
ea24f966619555245c821ab60e420595
abf084a4016e6cff2e56a1bc4f1873bb
8ae6f29cc144d8d17c330995c5441ebb
97fda4418069cc1a51b1d9ffc20b11ae
25625a587afb3a6518f384ffb8a4d058
7985c87a6dd3e791ca13fb7cf764249a
55da8ad4fa4cecc5e40ed19a2d3deb30
6cf778f34a104669ec4f640576588388
d3f7b820183dadb9731405216970b745
6a002eea2075ffa0bdca872ffa544a21
dd3fd44dae57b93d2f15b3a23c4b6604
Goldeneye SHA1 Hashes:
54197008baf7e50d9e3e3776bc53e59ca75c43a1
d7b43c71e8e126c46d57c2f5de5c5ffb0ef1481b
6098b3a242fe0ef6e9d99449245b75371ce936b7
958764cb5a5748711a6dbecf227a2cd307a7255d
7554438af2f6a323b41755e6ff487510592e6603
494cb85fea9f0f42d53cc9e5517acae81455cb9f
ed23c13bc41faf717bee8827d0d7000effaad42d
68571ea4dff73336f6c0329ee3f98df16274e0f1
b47630f887c06e059a8f2f34dcf142fb254f34b4
79130e360270449dd3da69f02424e1b34a941f11
e9b1ca9c548a790c2146c88fcb4b478ba4f89644
d05aafe3d18056d04740880d4100ce736117a19c
1531d7038ab9f4941730732d15ab617d574c30e2
9abcb88cf3b77923678b5e5d2b9661d7337e8e12
8b3747ac57b556117dccda4856d524985d7f3de9
098044e650cdb17f9a569edcc7d923cbeb092f79
ad949ffb61abb2162644a6921ef25f947a15d4b8
f6f3be1d9c20cf049f36f8ce01dd7c995bc6dfab
e85a2c96c38cc46b5f9220d18a3e874e7c7039d4
ea1d80bbd81904a22b2385c96ac16f85fee65c0a
f2cedff7f366254e8ee022f5bef19b33138f4916
ea142b9682e81fe520f9938e21656ea9e195b5ab
724266993c04e31a9e1cb0e760eff547b968e1ab
0b2c0dc4aacaced8a98b7771602755855e639f7b
b66876c67bc2169699a55030a17923f840f2f4cc
2928053abc53f3e6d5beb9ecd695e65b489cec96
83da0314e2cb89fd21d084c1462dee9e4659a079
2e2382c4fd60eae176abdedd7507d793b53263ff
c240043b4c2c6967df3666ddb53d0c759e3dc57c
09889894087323b4f9ac9512ec0e184095fc7cb8
1a0f22cc230c0231dd9167997792cffcfbeda7e4
45d7feed50c239e6f44c79984dfd19784a2d10f4
b2ec3b42a84ac09442f4c78c437282489e24c706
b3eaca92aac693904e295010526d4481151ec830
1f2cccee6e70b4fc279bf9a159bbdd2953898c22
2d667b894afada90310e932670418f34ca155037
4051420e93cda31e107d897b457bb82efe8ef256
5d1417841961c0414cd3624bc840d960c4fa6b54
cf81f00acded351e2f3531f915ec8c5890cd7c9e
5cfc87b40c79848a3e3ad07d30e5880270acf2f1
46790d76765ce1a5e01de1d619068670bd145a3b
daedcf065156b912c11aca5a668849ade94bc5ef
9d54614b9bca23b5e8a7f7e15e3e9450338e324f
357327e076d7261847ea55acc40754d18fe523fc
de06b07dc4215c440825e02fd69dd852b585f8fc
c9288e51c292e93f3b2d4705d99a5128bafc1ec3
75bc75ae58ec4984d86476eee9f520542d7c256b
2d7120ef4423b5b39df8a45ae6e0ed461c440b8f
355e3686e4dbe3238d5b221934ff5caea7af6987
2e2f0559d77e4daad69268ba58ae2cf12c47cb99
de257bcdd4ac079f44abae2e6e776ca6a08716d3
87441837d278f5586110abbbb21fc045ec92181a
03467c5e831d317bfc38d92208629f926861ea7a
ad290a75d9c9a38f4ac416ca2abcbee182ceed6e
a91b2e1fdc418edc43f16f70d9d9282b9443f24c
225a8c43041b889350d8a8cba5bafee91431a036
7982e7a445f16213e19393e845ac75f5947c194c
61a8f476e586c2238492f9cb0c726d91edb05c90
3ecd71c38a447137574ff94979b0ebd43aab7de6
9c4dd6f4313b62fb163326824579a9ffad17fde0
fdab60ae7211e7100114f06afdaa5df5ad45decb
4971ccd0daf81932f62c29264d7fd7861671c035
5f2e1a8b827bae72221f9f9c7f1339480dab20db
e1013592825622747bec40ab4dae5709e40d8eac
914c3d1aef910531619d57d18acce416787fb535
04bd86128ebc48dcdc36fa101e3b71fa854efc4c
bd0b612301ee843631f9a350917a7b690dbfd061
f83d3710d9c78fc792e2d588df7f25c5a64ed9ad
119f54487c1b71ff0eab9feacd71b0ddc9da730b
360783a252c1f004b7b82f815fcdb75daf68f777
17c12489129f016aee605e8813a8436b0482279b
db9384e6c8b4be285cbd083ff8750d7f122666a6
01866ca38b896abb1ed476258f01627b0e842a44
e5ce733ac5f0c784829a04292b3103428615bdba
3923b560b9fc00b36bed4d4cbb308b53b9b40eaf
d09574a6ee9a75faba460e5c1080730b800e102a
b7809637b12f34dd5b500f97cd4950bf34544ba0
534c52337006cb1c341d9468210828277a794798
5977e9c188f921ef1b0ddf0dc5402fb7a45df63a
a27873c3fb5d292109ab44e9d534276bd784f75c
176b2a9b4159b1c38554532564abe2292b0a9c0a
93fc5f95e8e96d73daed4b57e5912224759f9629
5a55ff57b608b544beb7783b27d19f140d5a1926
acf1e71a37c45018c3729a4410f5c0e685196cc6
6546e9171b61d1bc51a5a1a161b8c69f28cb6fb7
a4927799876b3e8189c44405b9b4bfe9346c934d
e617755a2504a912f13c077c6567f83f4ebe1199
917df70b9d3bbcbadb5fbff13e9bdcd0a7dfbfb4
62dfc954dc78975dc057df6460254b04e135ffa4
7df34fea6ef65c7f8b3346e948c69c6131b709eb
39b1370f8bb4ad2cf0c221a80a1b88af519cf564
ecf9c24902421ed00e53dd7537da7bb56f4a6d0a
836b07f203dc0f1466fd382116f4548ac9c241bd
b002b797966f9247d46b6a7888e39ee5b073b8f5
a587270226db34be191ce733ab50667a4d80e97f
7354ff3d47e6c041ecd6c6687fdb8c346b6481d5
9d3045f8cd145dae5fe0857b19a22ed479824193
62463db3b9064039463a188998ee54c635f4b2d2
4bbc55d60eb3a7103a3f6e57e91e8eab91a5cf31
efa92b80ed431e876fad859be713bd65072bf053