Introduction
DLL hijacking is not a new technique by any means, but that makes it no less effective. When a common Windows signed PE is set as a scheduled daily task, the average individual or IT staff member likely wouldn’t think anything of it. It would be just another Windows task necessary for the operating system (OS) to perform its normal operations. But that isn't always the case.
Cylance recently took note of malware leveraging SrcTool.exe, a utility signed by Microsoft. SrcTool is susceptible to DLL search order hijacking when a malicious DLL with the same name and exports is found before the legitimate DLL. In particular, SrcTool imports functions from DbgHelp.dll, which is present on all supported versions of Windows.
The malware acts as a trojan, implementing just the needed functions required by SrcTool to hijack the loading process and overwrite the initial instructions of SrcTool with its own malicious code. This maligned pairing is an attempt to hide the malicious DLL from both static and dynamic analysis.
Comparative Analysis of DbgHelp
In comparison to the original DbgHelp.dll, the first thing to notice is a drastic size differential. The legitimate DbgHelp.dll from a standard Windows 7 SP1 installation is larger than 800 KB, while the malicious DLLs range in size from 23 to 24 KB (Figure 1).
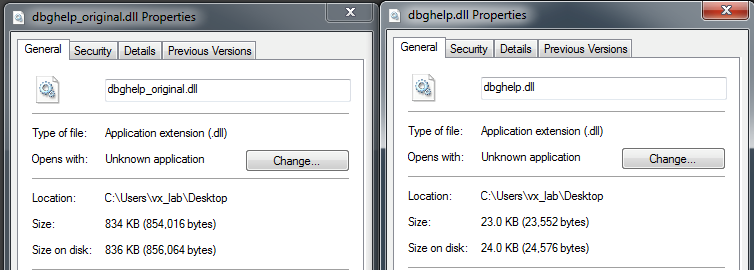
Figure 1: Size Differential Between Legitimate (Left) and Malicious (Right) Dbghelp.dll
The purpose of the typical DLL is to export functionality to be used in other programs; so the exported functions of a DLL can mean a great deal. When compared to the original, the malicious DLL mimics only a few of the functions. The original DLL contains 206 functions, while the malicious one only has 22, and even contains an export that isn’t shared with the original, ‘DLLMain(x,x,x)' (Figure 2, highlighted in red). This indicates that the malicious code is not made to duplicate the full functionality of the original.
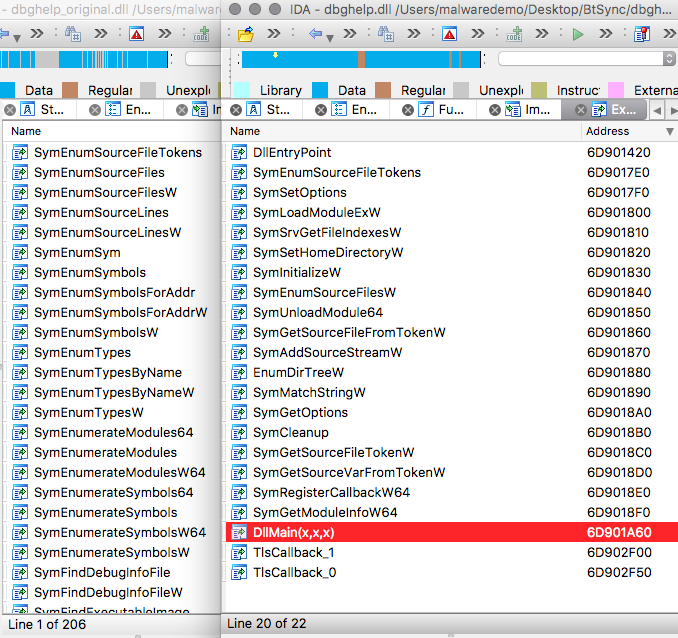
Figure 2: Comparison of Exports Between Original (Left) and Malicious (Right) dbghelp.dll
The functions exported by the malicious DLL can almost act as a fingerprint, leading us to SrcTool as the target of the DLL search order hijack. The exact imports used by SrcTool.exe are those exported by the malicious Dbghelp.dll (Figure 3). So the only functionality that this malicious DLL attempts to duplicate is the code necessary to cause the OS to select the malicious DLL during a search for SrcTool’s dependencies. As we’ll see, SrcTool merely acts as a carrier and is never meant to run its own code.
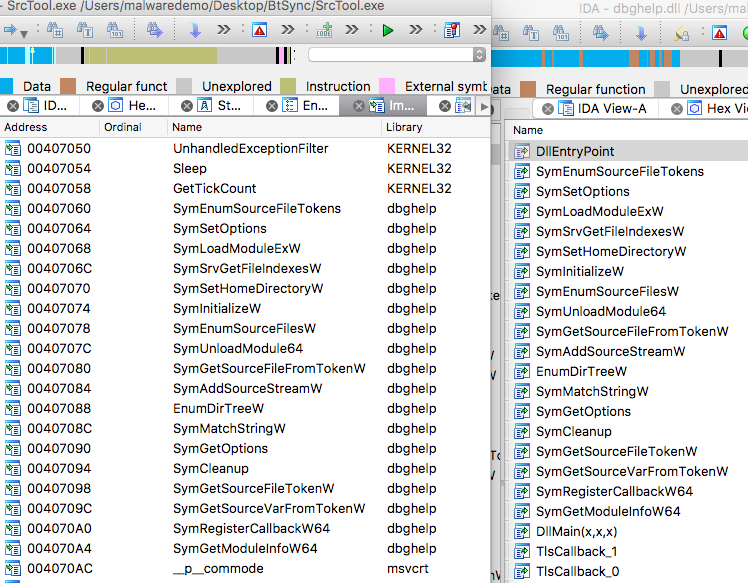
Figure 3: The Imports of SrcTool.exe from Dbghelp.dll (Left) Compared to Those Exported by Malicious Dbghelp.dll
Malicious Code Invocation
As with all DLL search order hijacks, the goal is to gain code execution. There are a number of ways to achieve this goal and the malware in this analysis chooses a fairly direct path by overwriting the entry point of the loading process. A comparison of the DLL entry-point functions of the two files shows a simple code flow for both libraries with one important difference. The malicious DLL calls another function before returning execution to the caller. This function (Figure 4) is quite complex, but ultimately will invoke the DllMain function previously highlighted as an additional export.
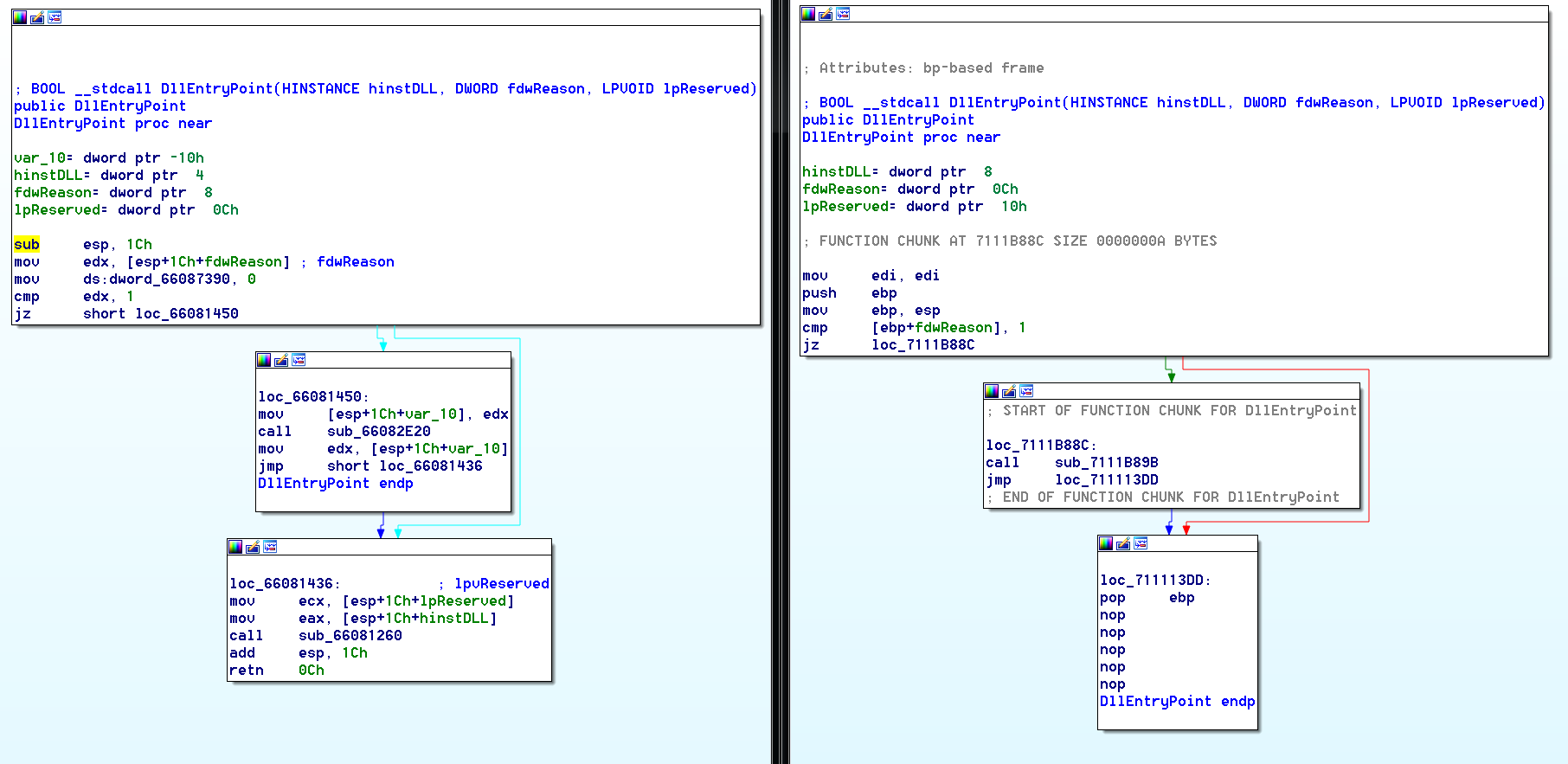
Figure 4: Comparison of DLL Entry-Point (Malicious DLL on the Left, Real DLL on the Right)
DllMain simply checks that fwdReason equals 1 and if so, sets a stack variable to the offset of MaliciousFunction and then calls OverwriteEntryPoint.
OverwriteEntryPoint was so named because it does exactly that. The function calls a subroutine that finds the entry-point of the loading process and overwrites it with a JMP (0xE9) instruction to the address passed in on the stack, i.e. the address of the malicious function (Figure 6). This essentially hijacks the execution of Srctool to execute the malicious function when the system finishes loading dependencies and passes control to the fully initialized process.
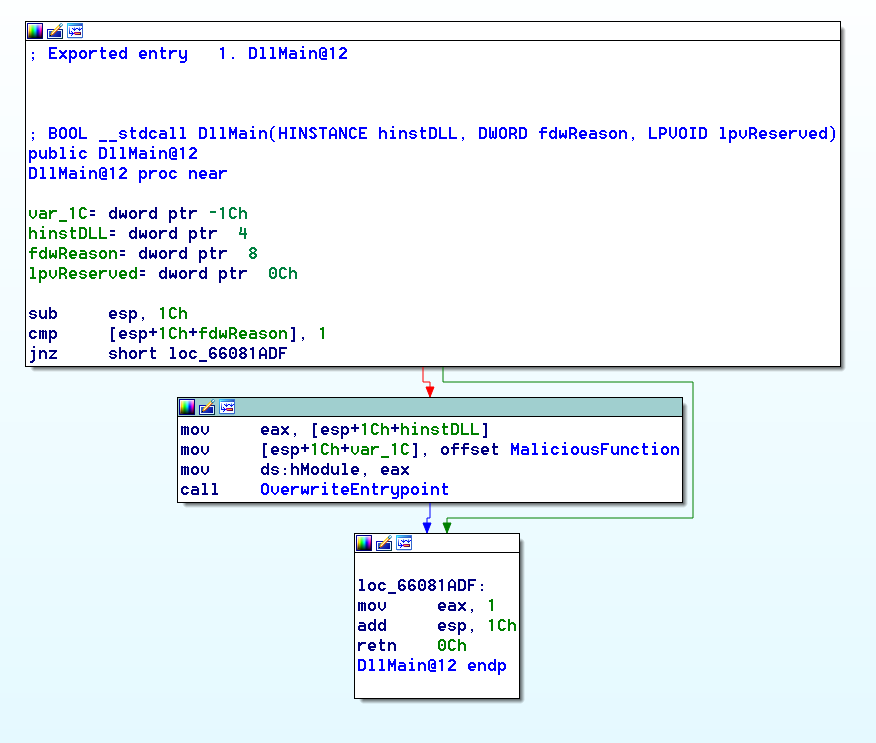
Figure 5: DllMain in the Malicious DLL
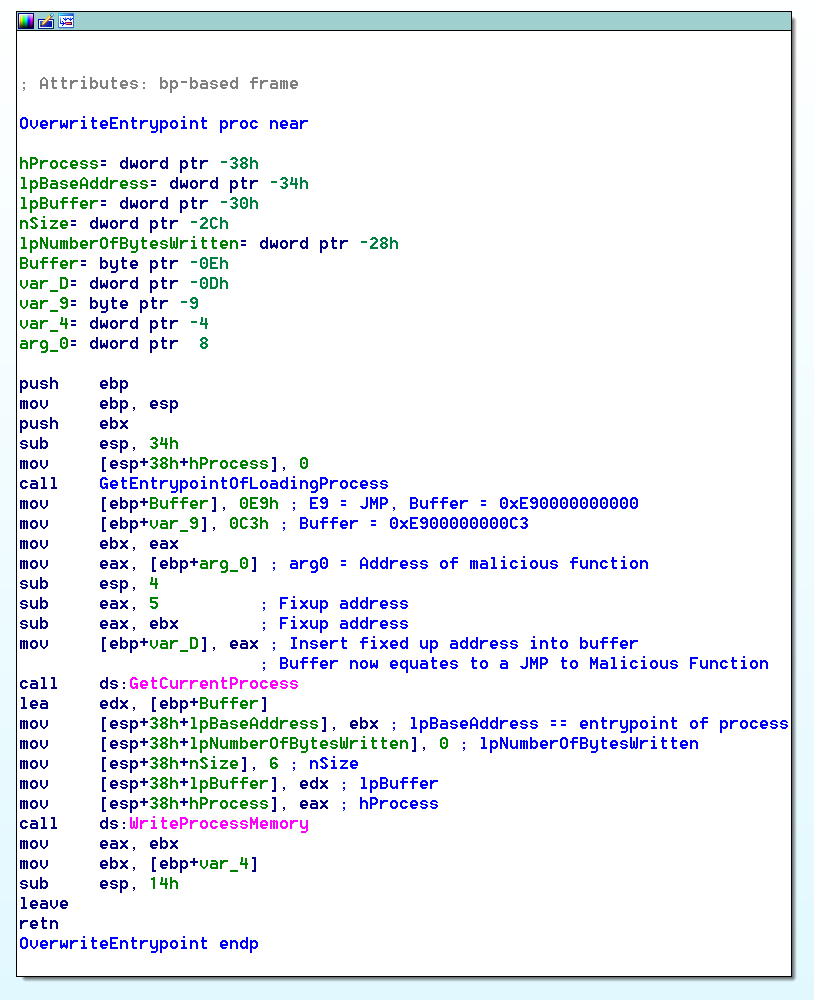
Figure 6: Function OverwriteEntryPoint in the Malicious DLL
MaliciousFunction Code
An inspection of the MaliciousFunction reveals a clear effort to hide malicious activity by getting a handle to the console window (assumed present when running Srctool), minimizing the console and then hiding it. The function then sets a local variable used as a filename to a hardcoded value (Figure 7). The way the malware author sets this value one byte at a time is a further attempt at obfuscation.
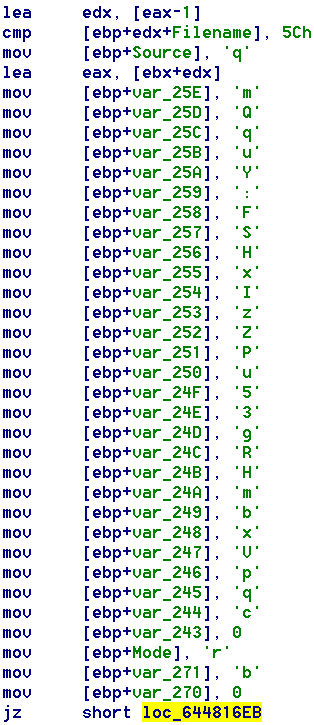
Figure 7: Deobfuscation and Execution of Data in the ADS
The hardcoded filename uses an alternate data stream (ADS) nomenclature, which the OS natively handles with the core file I/O routines. This is an excellent hiding technique. Files with alternate data streams are not differentiated in any way from normal files. A user or administrator would never notice the ADS file unless they knew to look for it.
Once the function reads the data from the stream, it deobfuscates the bytes (Figure 8) and eventually allocates memory on the heap and executes code from this data. Obfuscation is necessary because many security tools will automatically check for ADS files and scan their contents if found. The obfuscation employed would throw off any file type and string checks. The malicious code ultimately ends with a call to ExitProcess, supporting the theory that SrcTool merely acts as a carrier to mask the malicious code.
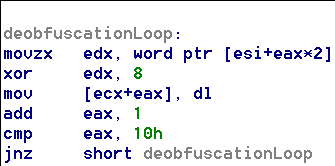
Figure 8: Deobfuscation and Execution of Data in the ADS
Conclusions
While Dbghelp.dll is clearly malicious, it is useless without several key environmental constraints in place. Without SrcTool and the payload in the ADS file, this DLL isn’t capable of malicious activity. The use of SrcTool seems to be purely for camouflage and may be set to run as a scheduled task or at startup. As a signed executable, this would not raise many red flags among most users or IT staff.
While we can’t determine the ultimate goal of this malware without the payload in the ADS file, we can conclude that this is an excellent persistence mechanism able to hide in plain sight.
Mitigation and Prevention
Unfortunately, DLL hijacking is more of an implementation and logic flaw in the executable itself, so user side mitigation and prevention options are not very effective. The only real configuration method to help prevention is to ensure that SafeDLLSearchMode is enabled. By default, this is enabled on all support versions of Windows. In addition, software developers could help mitigate these attacks by making all their DLL searches a direct path, rather than relying on the DLL search order to find the DLL for them.
Seeming random data in ADS files may also be an indicator that some malicious activity is present. The presence of ADS files themselves is not a strong indicator of malicious activity, since they are used in various ways by the OS as a core feature of the NT file system.
If you use our endpoint protection product CylancePROTECT®,
Indicators of Compromise (IOCs)
SHA-256 Hashes:
02FBC1019C1C5BB7A424D473F6507D69201B15DF50FB99599EFD7FE3C54B5DA8
14ADEBC453CB40142DA98CD562A08ED66ECE45DD1D77F4340972C391FBEE6C59
2AF9C1CD31091E04D56AB64A1E08B84C6964B675D76FC0A591C28470A63469F4
2B42203DE5E328D6064401F3E1D6546BA05925D76D8EAB4FC4B2B1CD2A69562B
2D6B2D1A1FF61DC6127F5BC1A2CE284CC48F6B3768B307A237F91014CA0AF327
31547B1FD319F9EA29029AD5AD832B3C5FBDF32B8C85AA326F3DF02F993F2F2D
31FF6C377CEDF8E2F284B93E05BF747E68DA19EE8784D0AB99B28E1CA7B9B12F
3ADEA819A24300DF8DAB9D416F1717D21B1AD7608EF54FE497E7303CE79EF11F
3CE90A26BE7509EB69BEFDD3F24DA2821914151506392FEB2C7600B33CF0C1C7
3FA6EB80D93F05FEE54646B0BD6EB96920A82D66B687079697A0589C304AE2B6
450A8BFC15F4535AD088538B1A6A0EB0918A6C414DBE2957E982BDC67C45F2EA
471C78BD59AA9C1F0B972587C42F96E36F8C324BB758C68398ACAE40295AEB58
4E05CBD540D875DC4355FF535750DEF9992F1A346FB4617BD210E9BD88EB4A51
509C12031C15AD53B6D940060B286E9BFDA9B2FAEE4CC2B2B3D0E17E619AD76D
53E5CF1D96F9775696F3B00D5ACBDB46FA9304B437DF07A5FA6A0BAD85A61E86
55E653BF7EB4B0A6D746D0E4ADC71A798AA45241D08E9658C2A870FE6CF955B1
5AF409489C14A8D5CE83CD7EA0C9D5B24E1CA4F2122E16A1225A7E69211E9FB4
5D2BBE85FC476488E5D5CD5FF969A9670E0A8114817C35075D5C4098CB80C376
60FBDAE2F9DC8294D5628B656A5999AEB9EE6198781CB3F2450B9D50294400AB
66DAD7C7831C79040D04A4E5F8749D5763B994F9A3FAA085583E84E613BB4FFC
69BFD92E888EEDA8912ABB573424A50AB4E964F9C0630B618A247CCC75F20A35
6AE915C365579FAAA5695DB6050BA8D40B10D86A6BE86964CE87EDAF6EA03154
73ADD65DB1F824EC696C7756F1BF0014F52A00361876487070189BD4994729F0
747EE7DD649C07693AF284741BD1AB7870C433BCBF13C6B3EB2CE88A6E1DFD93
7F1C6B4E4D15B67DD8CA8F68EC14E00613656F9BB428B7F85CB328CC32B1A4DC
820FB00A650E13F6765645D7DCFACF13BA73853ACF260F5A20220CA780C48D39
876D83C3B1A5A2BCA55176A6BC739213AD0B6039A0ECB03613A05ECDA0CE5914
8772C2BC70174A81E9DA222B7D3ADDC1124B1589495EF67CF2727F2B518CAACF
92FE8C00F8BD98A858B4AC6DAE69FC4D0AEDBF7F0DE703DF02EC95461175C463
947E673CBF5157FC17CD81B650A8BCCD3F598589F3D55F416616CF58F4F9087E
955D09A47A5EF81024BAF4FF1F456FCF5C2F7AE73335D9EDE4E5294AF25F403D
99D3ACAE2779EE5C42B68DBF35A851529F00C191E8694D6910E050722E4E0318
9D83C8625E81F5454396184ACFC536AF29B33838D0327A0BE8E6805631911CE0
A2B62168B6365592FAEB56171A3DFE08691AF5BEBC7585F2D67B997591DD2422
A55C036CDF0D35B54A0E921B9BAC3FF2B34BF0BAC21B1CB6E44C9A63C6C32F91
A5EB757AAABDB4FE2F9C65014F4901AE5C14893B8D39B43FD4D37610C120ACE8
A61FA48DE7682C975FFD46E4A2DC16BC244DBF286049D9C082966373740EE395
A7D50571B7764C66CF7FF7E2D039E82A2C1C5B1D78400AEC1037820956A915DF
A876198B78E9662F6AE69206BD36DD2C78031D976BBF2BB88FF9D307B76DE068
A90C1F2245D5631D5804B87D4C5F36C085B90137E1263F4BA22D6D0D67C5EAD4
B58924EC4A76B807CEE08AFE7948C812163038ADC6C5D4221AFAEDBE9BAB096A
B7A294E3BEE5BCF4730F31F0ECB8639255BFFE0A1474F4334E155C2BD35BC27F
BAA7895FFEE85B15B96DFFCD2B7CB99CD4A75EEC3A6DF4A355B80EE38893F5FD
BD756F9A0631C1770A3B1CCC6A75848E6C3A4849AA7F379ECDC019AD8F3BD1CC
BDE84338A10B9CD160E0ADA5660552F925F4C07B1DFC53A59FAC0CB60EFD26BF
BFE2C9344E81A422CC9FB592475E942CD4DF673B33D0538566D914982008FD88
C4FD83B9C7818F5C2F620701A7E460C16A9C09A424B133A9B42477F127A095A3
C7E7D5925DDA7BE16CC1491192BA408F783DFED86F1A2CE67F74863C39EE4853
CB3794EC3B53993C505C371E7DC1C4468FECC9C5D67F60355C1B0E408AE35F6E
CC14C1B87E8F064AE5535E0A3D43650EB0DA04D67D9B948B143E67D673BB51D9
D3B4EBD893F6288BDB85F6EAF0FAF2C547C9A055BE5D684D91F621BC4DB50380
DD3C9C034324816B1A481EDF412FC8F80C4972503226CC4B60A1B105D2529F21
DFD4918D8E8ECC00E43D1A4FA962ADB8C0FA8D8EA0D984AB842EEC52647508ED
E22FE9DF7CDF9DFFDDA7F771B4C3C6F979BC1407D84C1D55FC765C3807FCB14A
E350698FD4074C40D696AA6FCFBCFD71423445802BA56A922DC2972E6F21173B
E4667D623BBC441927A6AEFD195A95D91DC95E08B5484703E9E47CDCC73A9219
E8CE5E24DBD934AA04490033C9FA8E25B7941766C0CFD51ABB79ECC013811251
ED4C64AAEB1328870677395C0B8C315CEB931B5C18BD7871ADE8AE1249F8B77F
F27E7C2AEFB5D193CCC5B89CE5CA3B7B9BDC4C9ED25EEAAEB1191712F069F0F4
F90362494020D12A2B3173DA6EBB86773F9318C712C15DCA9602465AE27B9371
FE5B96AA6E96C73BB785982BE3CA845177809BE0FE0180B567ABBD677E7BA711
Filenames:
qmQquY:FSHxIzZPu53gRHmbxVpqc
QJYtZO:wCVUH5xFhQ7L8r
iTcbnj:Gibb9Y9KKuwvlV8AYjvCPjCvC23A
t0LDyy:Om4q3n0Y2UPQJS
CfXehY:yHhV6Umvim2oVV6GvW7dBcVwV8Yz
g9pznO:q6rtdx7KvtfYQ8jnGbbgsReje6WN
duqVdl:1T0KdhsgPyoJ0YmDTf
Ett4fk:fRKTiowtfthpTOma23i5jGls1
DsbIAy:j72z5bk0xeAKApATOZCxUvYbb
yPk3bD:SUfDRlI5AT1ZhMaRhB82ZrjC
SbwPZI:bgJqayyiGS8CMZU5wNiGP53u8tLh
hzYZqE:3stZ6hwUYYfsQU
GATazM:mVR8LbxqZK8
46If2c:SHo5ujOfk
1UxBZ0:6qg2CrT1mysZQYaxIe
cPAyKU:o2CSWOTnStUNfXcew52cAidTcP
evLAEp:UxrqTeoxS7NXVvjIaUO5
6auL84:3R9m6zdnOGmn2gwCRymnpqCRiqGArWq
it0H8N:bErumpDkfy
YijER1:oXeGwCme0s
2O7AnX:TgVdArb
CKHPX1:fPfSGwLWDpfGXAaSakFY2CnAxe3S
RqGh8V:sJDjNmh5mqjVWPwttn9EZ5xs3M
znsZzb:nSOcEwhS3
AVOxiq:xYO6YxlnGXRCFKCN4KXW9FDOhUuhY1
4eAdXu:cNbIS649mjGUJ
MXXua7:NPZhR9q9fJ
54jrcv:nhUYkKdtx5f1fbtEvK4SbDvxjzH0j2
x0fgzd:TreEvLuss7RaKon
tQnYEz:nESdg4T1ytZj5fVVvygmjn
5U8HPW:lIUEf9wuYIgnQwtyeQh
SHa4OE:ZlUAkVEmKO
q4OBw9:6uUat37t
W8VkwP:xZ0OGjLGBYD7rsbNAxrSBp5lXPM
frVV4j:aDV5BEnlnZ16YPvEjH8H4vPwNb956MC
3brH7X:J9hGIYnGul8Mayj
48g10c:zDbLju6OTP5Uh9fEqN3vkg
Wkg8i8:gnUCkJhXLXnO765jlpFu0yiem
0SIDDy:ZzlBgOAm08Z5UT2uz5kRbt9VGhwgtoNe
4hdVCq:OuR75ogoDV
DQmiZP:H4t1rfGSWPbRJo
EyvB7C:lUJUeODp5F4ThaA6NWt
AAaWxW:PF2xTyyCZJKZQw74kZgUn
hH18UT:e2ChiKKBfT4A
nPXhf3:wmOt8ItIlmjNI6fmGbgzKw
0H7cgO:b90CHGl6L0FLe6EcqNTt1sYdC
pQrfsY:qo77f8ZdGjof9G0mnvYn
Lpf2Bw:dX5C5zmZ7lHvAasq1adk6lJsf
5I6rwI:zVXuAhKz1Hb
InA4KS:10v05t9TVG8AXGWss
u8Pu1Q:52SGgJDVF2H
AUndFX:Z5oNzEHJedrOuFj7jbFh
nEn6fk:u5FELEogUb0fqnHYLQZOITlFsM
SU5jzH:gZoErLYyp6SPboG0RCx942QeZX
TFJmBo:WkaTSvo0C
ifZmRA:4qA5KBVhTohQNMmer1m
RDG2Xs:3OxZHUcWlooLLbVKv
YpZWy7:qP04TQLIgdAbGGt
Tj0t2b:C5vTIuAaA5oNHj9kv2zwMn
p8EK7F:Rl69
5XMaVZ:7bhV

