Introduction
Recent news reports reveal that various high profile personalities in Italy were among those targeted by phishing attacks involving the malware dubbed as ‘EyePyramid’. The report was based on court documents declassified by Italian police. The documents show that 18,327 unique usernames along with 1,793 passwords were stolen, totaling roughly 87 GB of data.
The EyePyramid malware has keylogging capabilities and is able to exfiltrate stolen information to various command and control (C&C) servers. Technical information and indicators mentioned in the court documents led to the arrest of the Occhionero siblings, implicated as masterminds of the cyber espionage operation.
The malware has been in circulation since 2010 and has been observed as recently as 2016. Our colleagues over at TrendMicro have published an in-depth blog with a high level of detail about the inner workings of EyePyramid. We’ll discuss additional findings here, focusing on how this malware affects the security posture of its targets. After the malware removes and modifies different security settings, users are left unprotected from a slew of potential attacks and vulnerabilities.
Analysis
This malware usually arrives as an attachment of a spear phishing email. The sender of this email typically uses compromised email accounts to make it appear that the email comes from a trusted source. The malware itself contains a list of targeted domains (Figure 1):
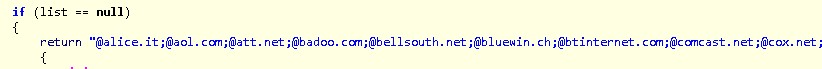
Figure 1: List of Domains Targeted
To date, published analysis has uncovered over 100 domains associated with EyePyramid. The complete list of these domains can be found near the end of this writeup, in Appendix A.
Another hallmark of this malware is the persistence mechanism. Once the user opens and runs the malware attachment, it drops a copy of itself into the Temp folder and creates registry entries to allow it to run on every system startup. The malware contains a list of pre-defined filenames used when creating a copy of itself to “%UserProfile%\Local Settings\Temp\” (Figure 2):

Figure 2: List of Malware Filenames
The following are the registry startup entries created:
- HKCU\Software\Microsoft\Windows\CurrentVersion\RunOnce\{malware filename}
- HKLM\Software\Microsoft\Windows\CurrentVersion\Run\{malware filename}
It also adds itself to the Firewall exception list, allowing it to communicate with its C&C servers:
- HKLM\SYSTEM\CurrentControlSet\Services\SharedAccess\Parameters\FirewallPolicy\StandardProfile\AuthorizedApplications\List
In addition to persistence, the malware takes account of every infected host system by obtaining the following unique information:
- ProcessorID
- Diskdrive Signature
- Lastbootuptime
- Computer System Product Name
- MAC Address
- MotherBoard Serial Number
- Operating System Name
- OS Serial Number
Lowering of Security Settings
User Account Control (UAC)
Once the malware has compromised the host system, it checks to see whether the Admin Approval Mode for User Account Control is enabled by checking the registry entry below:
HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System", "EnableLUA", 1
When enabled, Admin Approval Mode ensures all users from the local administrator group require specific approval (or elevation) to perform administrative tasks. This is added security to limit malware from making system-wide changes without the administrator’s knowledge.
This malware, however, will disable UAC and UAC remote restriction by setting the registry entries as below:
[HKEY_LOCAL_MACHINE\Software\Microsoft\Windows\CurrentVersion\Policies\System]
"EnableLUA"=dword:00000000
"LocalAccountTokenFilterPolicy"=dword:00000001
In addition to disabling UAC for local logons, the LocalAccountTokenFilterPolicy setting allows remote users belonging to the machine’s local administrator group to have full administrator access. This sets the malware up for lateral movement within the network environment.
New User Account Creation
The malware will also try to create a local admin user and add the user to domain administrator group in Active Directory. This will allow the malware to perform system changes and other functions with administrative privileges. It will also allow itself to connect to remote systems, possibly with full administrator access token:
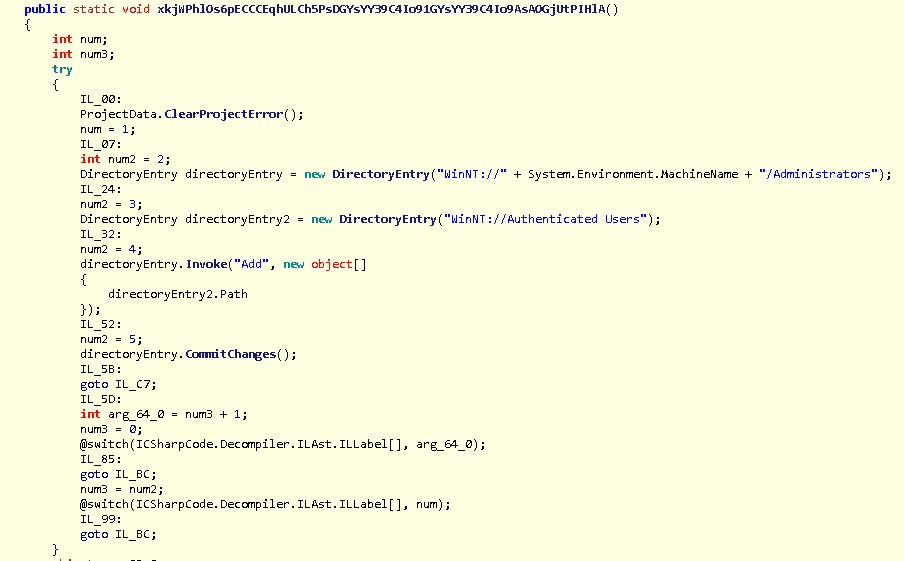
Figure 3: Code Snippet Showing Adding Local Admin User
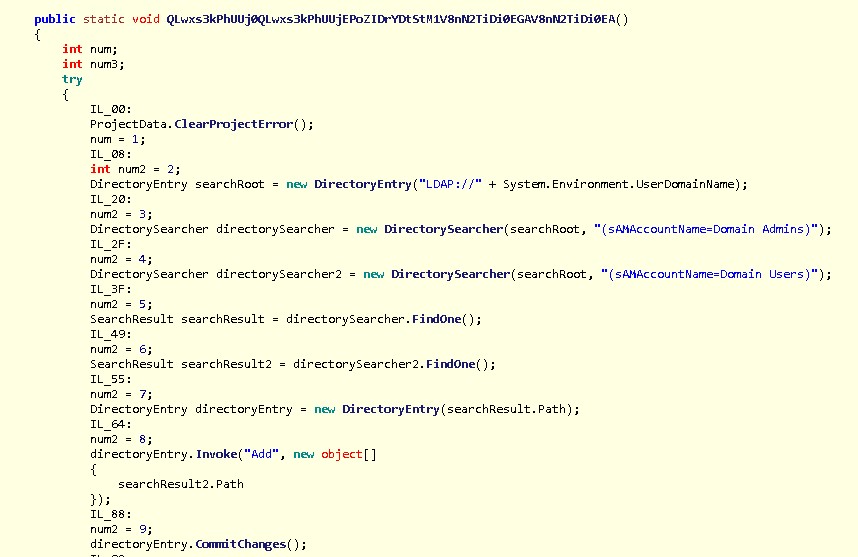
Figure 4: Code Snippet Showing Adding User to Active Directory
To cover its tracks in case of errors in creating a new admin user, EyePyramid programmatically removes the error message prompt setting of the User Account Control in Microsoft Action Center from the Control Panel by unchecking the User Account Control checkbox:
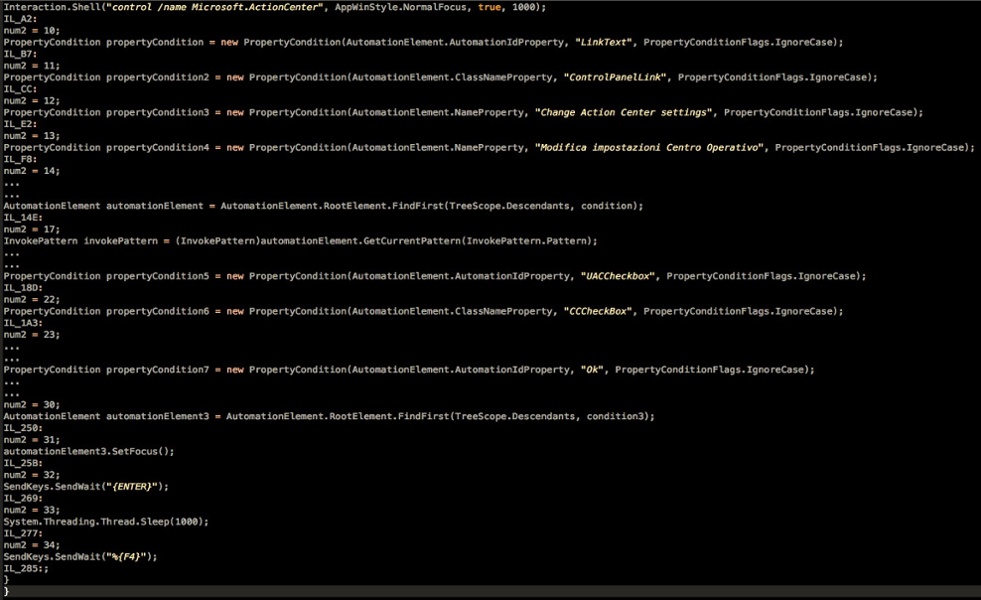
Figure 5: Code Snippet to Disable UAC Checkbox in Microsoft Action Center
Figure 6: Microsoft Action Center
Security Software and Settings
The malware will also prevent, disable, and terminate antivirus (AV) related processes. The list can be found near the end of this writeup, in Appendix B. It will also enable administrative shares on remote machine (IPC$, Admin$, C$) for local accounts and disable the following:
- Firewall
- Automatic Windows Update
- Windows Security Center service
- Windows Action Center
Microsoft Office Security Level
The malware also sets the security level to its lowest for a number of applications in the Microsoft Office suite, allowing macros to run auto >matically and without warning. And specifically for Outlook, certain attachments normally blocked by extension such as executables and scripts are removed from the block list, thereby allowing them to be viewed by the user. As an example, the settings enforced by the malware for Outlook are shown below. The full list can be viewed near the end of this writeup, in Appendix C.
[HKEY_CURRENT_USER\Software\Microsoft\Office\10.0\Outlook\Security]
"Level"=dword:00000001
"Level1Remove"=".bat;.com;.exe;.js;.jse;.reg;.vbe;.vbs"
Conclusions
The EyePyramid malware associated with phishing attacks against high profile personalities was primarily used to gather information on their targets. Versions of this malware in the wild date back to as early as 2010, with slight differences in functionality. You can just imagine the gigabytes of data that it was able to steal over the years.
However, this is not the only damage it causes because the aftermath of the attack leaves its targets susceptible to a slew of further potential attacks and vulnerabilities, even after this malware is removed. The numerous security settings disabled by the malware appear to be an effort to ensure ease of access in the future. However, those disabled settings make it easier for ANY attacker to gain access, not just the author of EyePyramid. All of these modifications open a huge gap in the user’s security posture, leaving them vulnerable to future malware attacks.
If you use our endpoint protection product, CylancePROTECT®, you were already protected from this attack. If you don't have CylancePROTECT, contact us to learn how our AI based solution can predict and prevent unknown and emerging threats. Our Research team has put together a video showing CylancePROTECT going up against the latest samples of EyePyramid malware - watch the video here.
Indicators of Compromise (IOCs)
Appendix A:
Targeted Email Domains
Appendix B:
Antivirus Related Processes
Ad-Aware Antivirus | Alice Total Security | AhnLab |
Alwil Software | Ashampoo | AVAST Software |
AVG | Avira | Bitdefender |
BullGuard Ltd | CA | CCleaner |
ClamWin | ClamAV for Windows | Comodo |
DriveSentry Security Suite | DrWeb | Emsisoft Anti-Malware |
Eset | Faronics | FRISK Software |
Fortinet | fsi | F-Secure |
F-Secure Internet Security | G Data | GFI Software |
Grisoft | IKARUS | Immunet Protect |
INCAInternet | IObit | K7 |
K7 Computing | kaspersky lab | Lavasoft |
Malwarebytes | Malwarebytes' Anti-Malware | McAfee |
McAfee Security Scan | Microsoft Security Client | Microsoft Security Essentials |
network associates | Norman | Norton Antivirus |
Norton AntiVirus Corporate Edition | Norton Internet Security | Norton Security Scan |
Norton 360 | Panda Security | PC Tools Antivirus |
Quick Heal | Rising | SafeCentral |
Softwin | Sophos | SPAMfighter |
Spybot - Search & Destroy | SpyShredder | Spyware Doctor |
Spyware Terminator | Sunbelt Software | Symantec |
Symantec AntiVirus | Symantec Shared | ThreatFire |
Trend Micro | Trojan Remover | TrustPort |
UAV | Vba32 | Virusbuster |
Webroot | Windows Defender | Zone labs |
Microsoft Security Center Settings:
[HKEY_LOCAL_MACHINE\SOFTWARE\Microsoft\Security Center]
"AllAlertsDisabled"=dword:00000001
"AntiVirusDisableNotify"=dword:00000001
"AntiVirusOverride"=dword:00000000
"DisableMonitoring"=dword:00000001
"FirewallDisableNotify"=dword:00000001
"FirewallOverride"=dword:00000000
"FirstRunDisabled"=dword:00000001
"UacDisableNotify"=dword:00000001
"UpdatesDisableNotify"=dword:00000000
Appendix C:
Microsoft Office Security Level
[HKEY_CURRENT_USER\Software\Microsoft\Office\10.0\Access\Security]
[HKEY_CURRENT_USER\Software\Microsoft\Office\10.0\Excel\Security]
[HKEY_CURRENT_USER\Software\Microsoft\Office\10.0\PowerPoint\Security]
[HKEY_CURRENT_USER\Software\Microsoft\Office\10.0\Word\Security][HKEY_CURRENT_USER\Software\Microsoft\Office\11.0\Access\Security][HKEY_CURRENT_USER\Software\Microsoft\Office\11.0\Excel\Security][HKEY_CURRENT_USER\Software\Microsoft\Office\11.0\PowerPoint\Security][HKEY_CURRENT_USER\Software\Microsoft\Office\11.0\Word\Security][HKEY_CURRENT_USER\Software\Microsoft\Office\12.0\Access\Security][HKEY_CURRENT_USER\Software\Microsoft\Office\12.0\Excel\Security][HKEY_CURRENT_USER\Software\Microsoft\Office\12.0\PowerPoint\Security][HKEY_CURRENT_USER\Software\Microsoft\Office\12.0\Word\Security][HKEY_CURRENT_USER\Software\Microsoft\Office\10.0\Outlook\Security][HKEY_CURRENT_USER\Software\Microsoft\Office\11.0\Outlook\Security][HKEY_CURRENT_USER\Software\Microsoft\Office\12.0\Outlook\Security]
SHA-256
0970e403b26e10159639532190a4125f4ddc4e4575d7b98e9be98a7037ff8ebb
0acef3cd66be80ba86641aabce113f7a3302c2500adc2a6d27d0098517220663
0af665d7d81871474039f08d96ba067d5a0bd5a95088009ea7344d23a27ca824
0ed387453442d53d65a5b402243fb8f50ae7605196d1bc90595ed0e9c6143f5d
1012f0717543409a3dfa4418bfdcde31ecc55ef7c673a13f5dbcd131c4a0db22
137846f698de9b30fe0fb81af20f175f36cf7c6297e3f920996e607cf80f518a
1436da185ebdbd9672a270ba1c32a3d3d9a73398092d00abb335a90302fad7ed
175a7361e0003b54343d3b32316288ae93b3c51b4c7fd5018d94d79b6cfa26a1
2a8a15b41d0713db9ddc5ad895cb9a08023d42057d98e0dcd96cfbee80146d8e
31ef142400853070edc4261e0b35875fd6e294fd30e56ee1040bca233e3e7234
31ef142400853070edc4261e0b35875fd6e294fd30e56ee1040bca233e3e7234
383dd234d22ead747319a04847d789bcedeacd0137a51ff394bab10256ab4b8e
38b497a153e0ea2e713e381a1b6b1e3845acda3066dcc3caa7c8a71d904ddf26
394e6d277c3a3454277cbe20ea7634eed8243e1ee5e8509254aa162ea2dc6ea0
3a451f1e2f64b7f4fe3c4f48366014142e22093a16b15601e0f98bc27364bd57
3b86409c26889be4fef9f3c4718193e1ea4d0e6551ec09eb55831dba761aecaa
3dcb22f5428d2161167663ccf13ab0ada0066d05401789daffe64c0cb1398a50
47a157ea41f9b93c956f0d8a78060dc044ed415c7bb0f1d8b337428660f60767
4be22645fa65d7dbb173a51ce9ed6509c600c61df8ed4a131d66d9745a707510
51a96dad0bba7a89431afe04e7eb73b7e6186dc28ae2cfc125989785c859e9e2
53ce09a0160e15b87c59952dc90e3850c6f402b94646f481c5dda7fe96484a18
54803272bfba881755e26427bcbc9f3b5f527f79b55cf825350820c42216e2ec
55c9a611103f43070ba186fe70d0253ec1ff21f644d8ae92f9b02b4a1f4c0ea1
580cf6d6f5ea248f968806605f57e440014661351593b3cf3d4dc5369a594472
590f43c66ec69b9534c893acbb2fce7f1780fe5ac0e7fca7462db1600ad91f38
5baf74ff1d11410b3b4927744a64673c0ea42b39f6661115fc29b0368d14ee8b
5cbe33af4bd71abe79c2cf6d1d1d4a46344dc2e40b3eea588c36a2005d98ad7f
5df4ced9c1c073f102822a30f7caedb6d20b203c80b80a14de354d63a847f968
5e0527a10ebd35c285a172c605dee806ae69f02965651626a0b4913b56c8a987
6085e8b4ee1b2977a4513d202ec04dea0ac378fbe8bf914f81e50f85be03fd56
6a624e266f9656f3bb684b88bf027ac2d229aac98e26accbe4bd415306fa7482
7433382aa5cdab5b7cd7da414cc2aff098e6e87ed1cbb02e9e17b2055ca23eab
76c1519243dbd5d56a59cffcc5f95bdaf5c561759388d8a1395c04c527f8b092
7e535ff19bdc8f2f0456e713cfcf7b73a85651e31dfe81419d849fd2585014a7
7fcae3924409ec5b6338d2eb71dd4644d124b72ffd6995c9252dd477e0041c91
871e65e7b80b32501b9890a7044dcc64fb1b0936a17d0fa0d50bb10b2550d3dd
8e7972bc362e5b7db6bc9d17ed34f675b2a8e9351e50334c927f55367bb3c033
906624aec0b63d5a6f1c8f0fa4386af02365508cbe9c12498ee60432984bdc9c
93c19d6e744053f4b337c9026e09c13e8d1019d535fdc21c2b1a21937e5aa76f
96cd137faf632954bb6c081706882dcae68c586f1b6d289c6d58917025a53c5c
9c3d491033f8c9452e70bb37caaa9c49573515e2e5cf7af5615fd78ec90cfce8
9d07dac76a139e6b6cd370eebc44d3430e32d491bb1062fd12d2423cd4d8610d
9da0d4ad40b86319c60c4d0cb65a08486a44e859ae37d3dc5c9396309e0da5c8
a0c25021e04b95cc4af1e001109ef559834c4a343b085d2ebb16d0a495179f70
a953d0899b119b14fcd4eff662ba010248f53f37ce6b7256cd97e8b6b692d1f6
ae0771f74911edd1113e4dd66dad0174059ab7e08a2e4a9c4486bb5e03a34056
b0a718f2322a8eb15633f8d0cd72f653aab5921e3a581bf8cb8222bdd4dbb7bb
b37a8dbda764721448a1bef5704c0821a3355eaee9c865dd3c6127002db80781
b491a9e1da4e77a4a911607ce9e4c2dac63f997a087c074a526f603b06fe08a1
b860b98eed4f2214cfd95375caa82e1c5d1e438086220d2f08d1f86fd21a54da
bf665dfb4e79e7ec910367a26af0b080dcd568f3a8836ed86ec60a89770cf720
c3523c32348ed741a75afdc3088ff70e512a0c7c542ae6cebc783e016993b91f
ca0cfb8d03163487bc637171a1df6f7c80768fe1e1f060576f7e005335339a95
ca525d0e18f78f1389a556da3c7ea5bfbb4866e32360b45168f52351915dcdd5
cb3a6a6f193452921c9b1941b712c6035f3a4a5d9639b5e91c4cd6d2de02d1cd
cf159475586e5ff2aa699ede860b9fc2b9061585624378739907d26d1f916d30
d1f38ebf16902917e4b45bad63acfdb1a389ffb1ba121f126471c2ca6855991c
d3ad32bcb255e56cd2a768b3cbf6bafda88233288fc6650d0dfa3810be75f74c
d4439954ff2a158a861946e1a223e97a46b0b55669857dcfdf5cc70e459d24cd
d874fe7cd08aff55655a3e35f96c895a3cf84bfa92f482eb7d404f8feb4de130
d910283342c7be67b03a01cac2aae5d310ac6e6d9d3572df324eb2afe0127f2f
e17c71a427cf5c9026aac00c6631ba4438da5f3b52e96655193ededd4ffd00ee
e2d5512fe82b6e4b6bfdeb93f49adbdcc719e833a3e7e56d95f98022e12615f9
e71783d9f572c2d11772a48c174b05a1871a684f6ca153e28ff67483fb3ce344
ed09cc961850f105410d09f229446d632368341d078435044e69ad725e4a06e5
f9bf0244a99437213bbb8dd3ff1ca2995a519e9fccf1409566460becc9062e2d
faeb185c0d2048fce0597b899047d4c222d31c5f94ea94d19dcfe788e5dd3da8
fcaf52c71f7fb486fdeb69effd507ba5f4aa59b4daca36d8156e575afb5d9200
fddb8b0b80a396edce871149bf9bce8825d2b1ed198eaddf27bfc594d69de021

