The following is a summary of the NemeS1S ransomware-as-a-service (RaaS) malware, including information on mitigation. A 'deep dive' investigative write-up by Cylance Senior Security Researcher Jim Walter can be found here.
Discovered: 1/7/2016
Home: / C2: h x x p:/ / nemesiqoaxtca4ve[dot]onion/
Summary: NemeS1S is a ransomware-as-a-service (RaaS) offering. The generated code/ binaries are 100% derived from the PadCrypt 3.0 source. Therefore, all of the decryption services and ransom messages reference PadCrypt 3.0 rather than the parent service (NemeS1S).
Features:
- AES-256 file-based encryption
- Unique host keys (RSA 1024)
- Encrypts all files, regardless of extension
- Deletes VSS (Volume Shadow Copies)
- Live interactive chat (Introduced as a PadCrypt feature)
- .NET-based malware binaries
- DGA based on existing PadCrypt mechanisms, generating up to 72 domains per day
RaaS Specific Features:
- Full message-based support with admins (SLA 24-48 hours)
- NemeS1S admins get a 35% commission on each successful and confirmed BTC payment
- Multiple campaign support
- Ability to generate multiple malware binaries per day (system currently allows new binaries to be generated approximately every 20 minutes).
- Full host/ infection management via client portal site (home URL shown above)
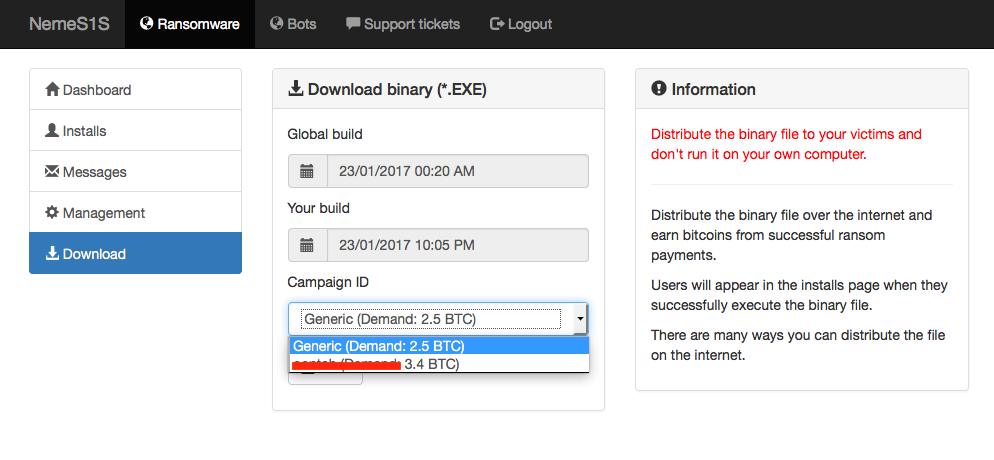
Figure 1: NemeS1S Basic Dashboard
Mitigation/ Coverage:
If you use our endpoint protection product CylancePROTECT®, you are already protected from this attack. CylancePROTECT fully prevents execution on binaries generated by the NemeS1S service. If you don't have CylancePROTECT, contact us to learn how our AI-driven solution can predict and prevent unknown and emerging threats.
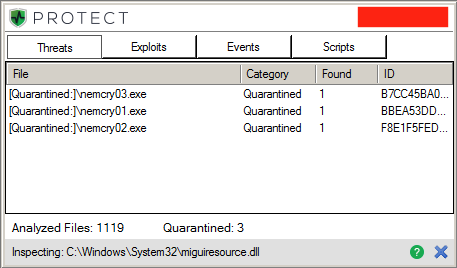
Figure 2: CylancePROTECT Client Notifications
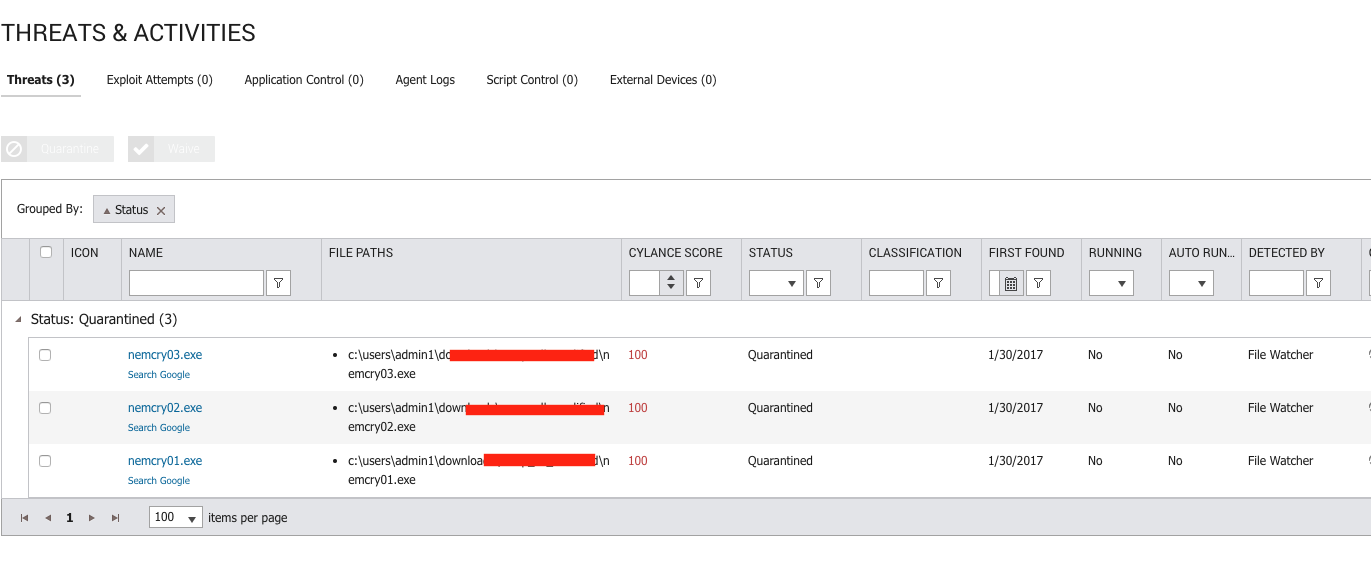
Figure 3: CylancePROTECT Console
Indicators of Compromise (IOCs)
SHA-256 Hashes:
bbea53ddbb4962c01866a56f8dd9cbd695b392b0b17cea2dccb97ecb3b7bb8c5
f8e1f5fedd8d2bf4d686638e1aaa55d38fcf47dbd5d70011ba4ca7995866f375
b7cc45ba01b69534c0c1ad7ebbfd122c2f34907fc4025460550793f0b3710e0a
aa334fc337cf3e3b3ace5899a37c86295c7d54c036c94c43c216025a7284dfd3
f7d8cdf871d6aadd9f7f5033cb136561a1899339bb88846d6244733ea7b5a69e
5bbd43b7e9b5fff27dbab9dae9ac5b9fe9e50795f826884f4239f8d50208a75a
8805cc57f71ad809d49cf906401520c399bd6042b4ca2223f4cd981ed6a688fc
4b1245ccf1a708b4579df8702b3addbff03ec65f5ff66e919a4195e70e9c8133
af9f78b3c27e505b6a41be953a62b9273121983b29e8bd7e042d63a7556cb07c
93bd1d34a9a5b8282370a4629c59934e87966a8d9f759b81498018615e46e56d
2927a33e9fcc1c6306b00cf04ced067f0ff5cccffb5b9723ffbf46bc0044b061
ccaca0010fed565efa13134631f55c0d5393e50ed7639a97a2c457effb89ca2c
4cd4d58643094080af399d345ee76793b9677822f304c22ed1670aa47c1f16df
9e74311fc783f27c13dc84aa26b6339a504d762122d48edaf8d06c9d537afd3c
f3663cdc4be918b26091ee3572aa12d5ff732bc867a4025db4e1b4fd72fb3b9c
6547d2f70880549f768c2598d47eb53e1fb327adca96c63ce59d376ba56bad31
b7fa18a33f48d493cf881a71222ee4014d70f075f31d51b07681bbba8bdf7006
8ed2a0b4632e6789353630f51ff031364617529f51f9556e5f97c9b2a98d966c