NemeS1S: Ransomware Déjà Vu . . . . Again!
In early February 2017, we blogged about a new ransomware-as-a-service (RaaS) offering dubbed “NemeS1S”. While this service offered all the features we have come to know well in the RaaS world, one characteristic stood out above all others. The “new” service was really just a pretty wrapper around the older, very well known, PadCrypt ransomware family.
The service allows wanna-be cybercriminals to customize their bitcoin ransom amounts and other aspects of the binary and messaging, but at the end of the day, criminals were stuck with PadCrypt binaries that were easily detected and prevented by most endpoint security products.
Shortly after our blog appeared, the NemeS1S service vanished. We like to think our publicizing of the service (and shortcomings within) had an effect on the service and cut down the market for it. Unfortunately, that cannot be corroborated, but we can always continue with our fantasy that we did a little bit of good there.
Now, fast-forward to March 7, 2017 - and the service reappeared. There are a few tweaks in the service, and the model itself actually changed between March 7 and the writing of this blog on May 11.
The overall model remains the same, but there are a few interesting updates to what these guys are offering. On Day 1, the system was completely open to new registration and allowed for complete ransomware binary creation and management. Sounds great in theory, but the resulting binaries were still PadCrypt!
This group has, once again, attempted to put lipstick on a very old and very well-known pig. Decoding the embedded ransom messaging within the binary (Base64) is just one indicator of the legacy PadCrypt activity.
Figures 1 and 2 below show the Base64 blob and decoded data respectively:

Figure 1: Base64 Blob
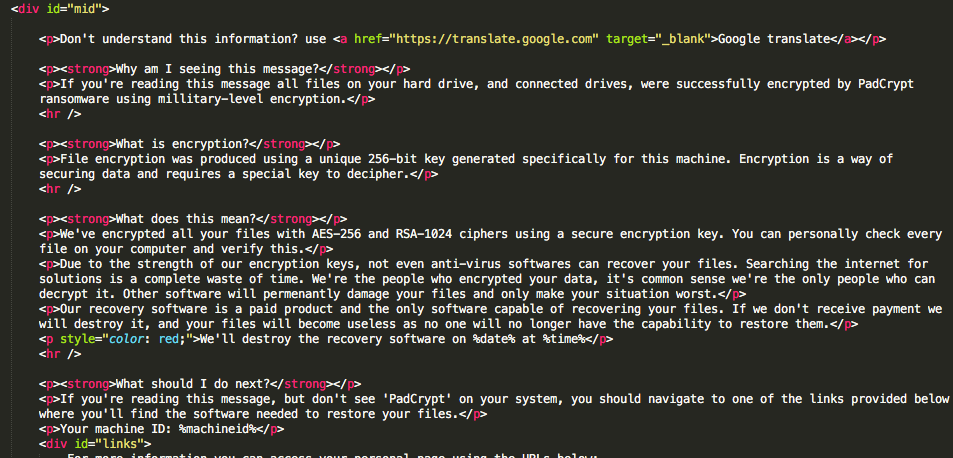
Figure 2: Decoded Data
Shortly after the new service launched, the malware authors changed to a closed model:
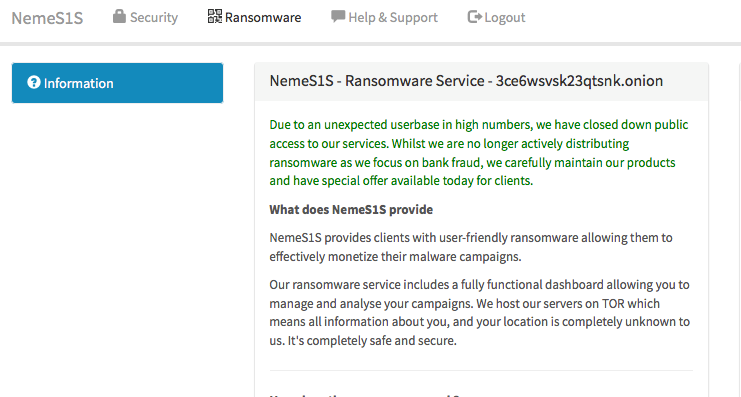
Figure 3: NemeS1S – Now Closed
Currently, the service requires vetted registration along with a small entry fee of 0.12 bitcoin (BTC) - currently around 211.00 USD at time of writing. According to the page, after 24-48 hours, applicants will be granted access to all the features that were previously open and available to all.
In terms of their ‘fully undetectable’ (FUD) status, they make no guarantees. Users are advised to continually update their binaries to ensure the highest level of evasion:
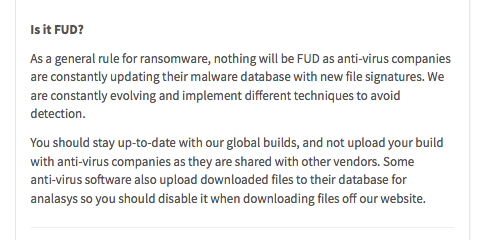
At the end of the day, even with this well-known ransomware family, traditional endpoint controls (aka signature-based traditional AV) have difficulty ensuring and maintaining detection.
French Elections and the Fine Art of Defensive Misinformation
These days, you can’t escape the daily news cycle without noticing stories pertaining to election tampering. Specifically, certain geographies and nations that allegedly interfered with multiple high-profile elections.
We don’t want to focus on attribution and outcome details in this particular article. However, one aspect of the latest event is very much worthy of note and discussion.
Multiple sources have reported that the Macron campaign (the target of phishing/ data leaking attacks) employed strategically placed dummy data and documents within what is effectively a honeynet. Said honeynet has been designed to disrupt the attackers’ workflow, delay their processes, and ultimately insert doubt and confusion around which documents are real and which are fake.
This affects both the attackers and anyone in the general public that chooses to examine the leaked data. At a high level, this is a very smart tactic on the part of the Macron campaign, and one that entities should consider employing as part of a robust attack defense and damage control strategy.
A representative for the Macron campaign, Mounir Mahjoubi, stated the following in the New York Times:
“We went on a counteroffensive . . . We created false accounts, with false content, as traps. We did this massively, to create the obligation for them to verify, to determine whether it was a real account . . . . During all their attacks we put in phony documents. And that forced them to waste time.”
Even more admirable, the campaign staff were employing and tweaking this strategy early on. They began “high-quality” phishing emails in December of 2016. Even at that point, they were beginning to produce and provide their own smokescreen data to make things all the more difficult for the attackers.
The wise and effective OPSEC on the part of the Macron campaign should serve as not only a wake-up call, but also a pseudo-template for a novel and effective approach for making live difficult for attackers, of any skill/sophistication level.
DocuSign Alerts Users to Malicious Phishing Campaign
Speaking of phishing campaigns, on March 9, 2017, DocuSign distributed an alert concerning a malicious email campaign. The phishing emails are reported to contain specially-crafted Microsoft Office/ Word documents which, upon opening, execute malicious macro-based code.
It should be noted that these emails are not associated with DocuSign, according to the alert. The emails were sent from domains which were designed to resemble “docusign[dot]com” at first glance. However, specific characters are replaced (ex: docusgn.com).
According to the alert, the subject lines in the malicious emails also resemble common traits seen in many email-based social-engineering attacks (for example: "Completed: docusign.com - Wire Transfer Instructions for recipient-name Document Ready for Signature”.)
According to sources close to the issue, the malicious macro leads to multiple stages of additional malware being downloaded and executed. Once executed, the macro contacts a remote server and downloads a copy of Hancitor malware. The Hancitor malware is responsible for further external communications as well as the downloading of additional payloads (Pony, as of this writing).
Depending on the instance and timing, additional malware is also loaded, and the C2 servers appear to be relatively dynamic as well.

