Cylance Prevents Petya-Like Ransomware
Overview
A new ransomware outbreak has been rapidly propagating across computer networks globally, starting earlier in the afternoon (UTC) today on June 27. Before explaining the details of this latest outbreak, rest assured that CylancePROTECT® customers are fully protected from this threat, and have been since October 14, 2015 with our 1310 model release.
The new Petya-like attack demonstrates the benefit of our temporal predictive advantage, which enables CylancePROTECT to block this new ransomware threat without an update.
UPDATE 7/11/17: Read our Threat Guidance team's latest 'deep dive' into Petya-like here.
UPDATE 8/15/17: For more information on the exploit used in WannaCry and Petya-Like, read our latest update on EternalPulsar here.
Watch Cylance protect against this new Petya-like ransomware:
VIDEO: Cylance vs. Petya-like Ransomware
The Petya-like ransomware exploits the same SMB vulnerability as WannaCry (EternalBlue) which ravaged systems globally back in May 2017. Mimicking WannaCry in its propagation, this malware exhibits the same worm-like capabilities (Windows SMBv1 sharing) to spread itself remotely with no user interaction needed. In addition, it also leverages password dumping capabilities to gather credentials, PsExec to remotely run WMIC to exploit the inherent trust inside of corporate networks to spread laterally within those environments.
The multitude of spreading mechanisms ensures this ransomware is far more versatile in propagating than WannaCry, with the ability to infect remote systems patched against the MS17-010 vulnerability. Importantly, this attack lacks a remote kill switch that significantly limited the impact and spread of WannaCry.
How is This Petya Variant Delivered?
EDITOR'S NOTE: While the attack vector remains an open question, we have confirmed that the malware contains multiple mechanisms to propagate. Our initial reporting suggested a phishing attack and was largely based on an RTF document leveraging CVE-2017-0199 linked in related analysis. Since then, we’ve analyzed this document and confirmed it is not related to this malware outbreak.
Once active, the ransomware will attempt to spread laterally. The ransomware then proceeds to drop additional components and install itself in the Master Boot Record (MBR) of the system prior to creating a scheduled task that will reboot the system after an hour and a half. When the system reboots automatically, the real fun begins.
What Does It Do?
Once the system reboots, the encryption process begins, and the following ransom note is displayed:
Send your Bitcoin wallet ID and personal installation key to e-mail
1Mz7153HMuxXTuR2R1t78mGSdzaAtNbBWX
Ooops, your important files are encrypted.
If you see this text, then your files are no longer accessible, because
they have been encrypted. Perhaps you are busy looking for a way to recover
your files, but don't waste your time. Nobody can recover your files without
our decryption service.
We guarantee that you can recover all your files safely and easily.
All you need to do is submit the payment and purchase the decryption key.
Please follow the instructions:
Send $300 worth of Bitcoin to following address:
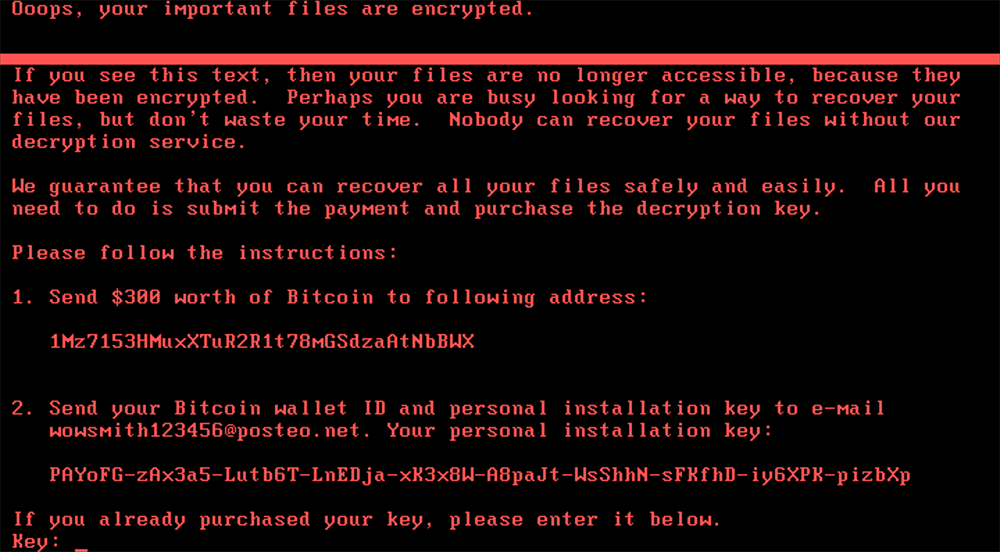
Figure 1. Ransom Screen
Why is This a Big Deal?
Following the Shadow Brokers data dump of NSA hacking tools, we are starting to see a continued wave of attacks that are escalating in both their severity and sophistication. There seems to be no slowdown in ransomware, regardless of developer source. While much was made of the EternalBlue NSA leak – leading to WannaCry and other variants – it may have just been the tip of the proverbial iceberg. We are now seeing newer, more advanced malware campaigns leveraging the same toolkits.
The fact that these newer campaigns are seeing the success that they are while leveraging months-old exploits that have patches available is truly frightening. They are continuing to prove that simplistic, legacy technology that requires a patient zero before a signature can be created is simply inadequate in today’s world.
While inspired by WannaCry and Petya, the consensus is that the malware payload contains enough unique features to say that it’s a new malware strain, unlike those that came before it. The malware uses several of the techniques used by previous ransomware variants including the SMB exploit seen in the WannaCry outbreak and the MBR infection technique used by Petya.
How Does Cylance Protect Me?
CylancePROTECT stops both file and fileless malware, including that of the self-destructing variety. Since it operates pre-execution – before it enters memory – ransomware such as we are seeing today never has a chance to do damage or communicate with C2 servers.
CylancePROTECT runs silently in the background to detect malicious files, with configurable options across memory, script, file, and network protection. In essence, Cylance predicts attacks – far in advance – without the blind spots found in legacy, signature-based tools.
Finally, the CylancePROTECT Dashboard offers insight into “what could have been,” aiding in investigations on unprotected machines. But those with CylancePROTECT won’t require remediation or cleanup.
If you don't have CylancePROTECT, contact us to learn how our AI-driven solution can predict and prevent unknown and emerging threats.
**Watch the recorded webcast: We Won’t Let Petya-like Ransomware Bring You Down.

