Petya Reloaded
The security world was smothered this week by all things ‘Petya-like’ (aka NotPetya). What started out looking like a new, and long awaited, follow-up to Petya/Goldeneye has turned out to be something quite different. The similarities between the original Petya and this new threat quickly became less and less concrete.
While the Petya-like threat does ‘affect’ the master boot record (MBR) like the original Petya, the similarities primarily stop there. The Petya-copycat behavior is the least intriguing piece of this new threat. What really set it apart is the spreading (worm) capabilities. Like WannaCry, NotPetya/Petya-like is able to spread via the MS10-070 SMB vulnerability exploited by the ETERNALBLUE exploit which was first leaked by the Shadow Brokers.
However, NotPetya does not stop there. History has shown that the most prolific malware outbreaks tend to embrace multi-prong/ fault-tolerant approaches towards persistence and spreading (especially lateral movement) – for example, Nimda. In addition to ETERNALBLUE, NotPetya also attempts to spread via Windows Mangement Instrumentation (WMI) and PsExec, both well known techniques among penetration testers for moving laterally within networks. This allows it to spread to machines that are patched against the ETERNALBLUE exploit.
Further analysis has revealed that the motive behind this threat is more destructive in nature and less about financial gain… further distancing it from the original Petya/Mischa/Goldeneye family. While it is never recommended that victims pay ransom to these actors, it appear that even if one had paid (in this instance) it would not have resulted in successful decryption.
Analysis of the threat is ongoing and we have posted two blogs to track coverage and technical details. Read our Threat Guidance team’s deep dive analysis of this Petya-Like Ransomware here. (And yes… Cylance prevents Petya-Like).
Interestingly enough, we have observed fake websites on the TOR network masquerading as the NotPetya ransomware payments site to purchase the decryption key.
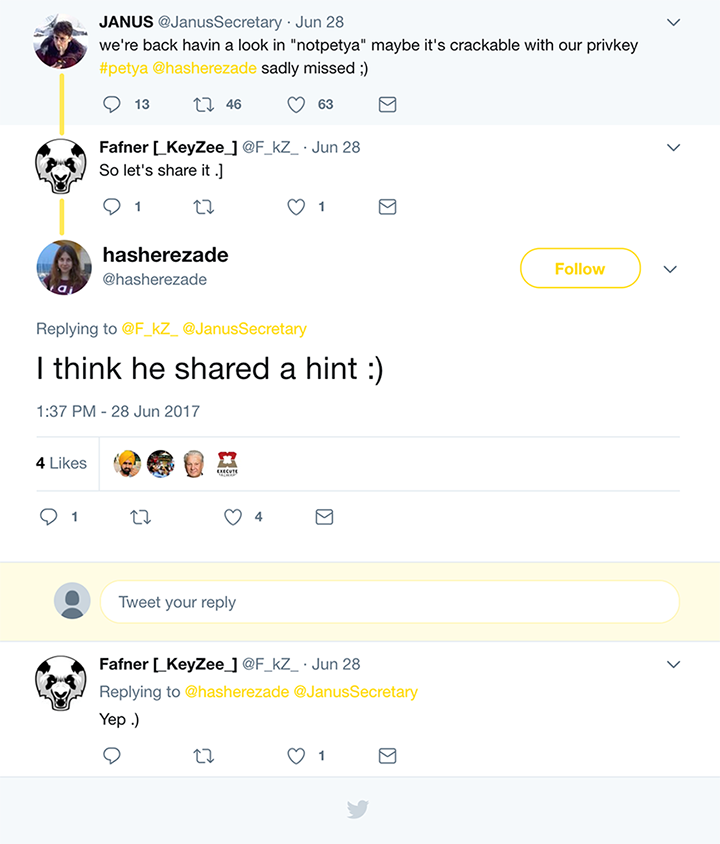
Also, the entity behind the @JanusSecretary Twitter account (associated with the original Petya/Mischa/Goldeneye services) has reemerged, attempting to distance themselves as well as offer any ‘help’ that may be needed.
Yet Another Dead-Simple RAAS
On the subject of actual ransomware, the latest Ransomware as a Service (RaaS) is becoming much more user friendly for malicious actors.
On June 26, the ‘Simple Ransomware’ RaaS appeared, offering a zero-bells-and-whistles interface and omitting the registration component of most RaaS sites, this service makes it that much easier for anyone to get into the ransomware business.
Per the sites FAQ, users of the service collect 90% of any payments resulting from the generated ransomware.
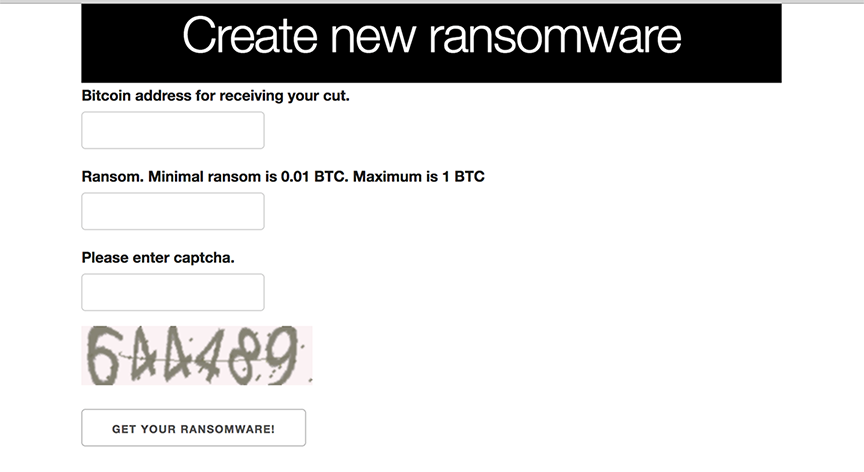
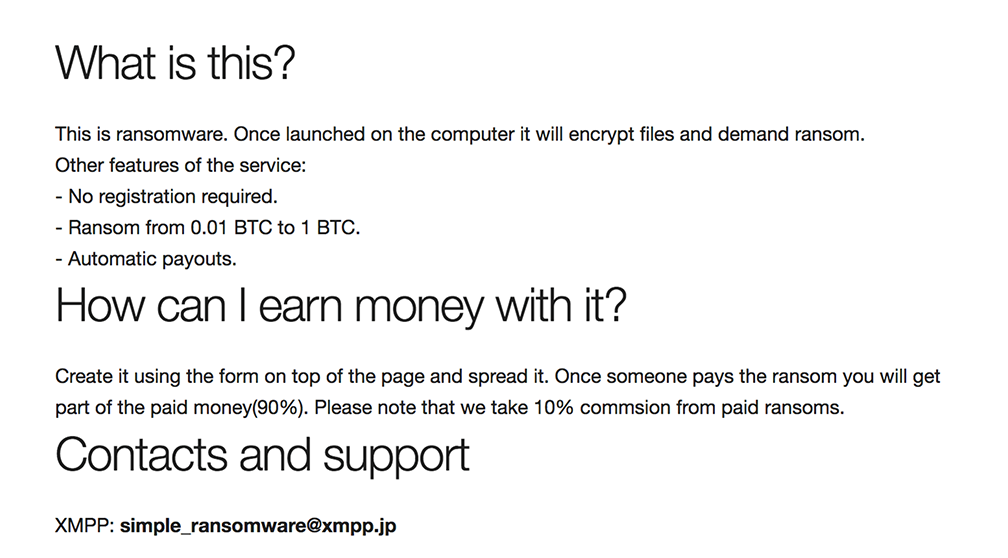
After supplying a payment address and requested amount (max 1 BTC) the site quickly outputs your ransomware binary:
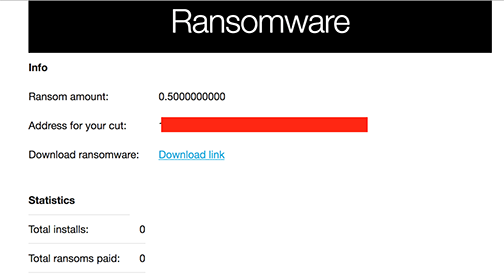
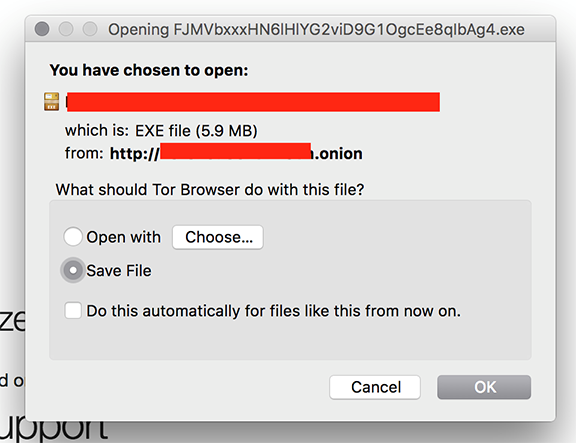
Malware generated by the service is unpacked and resembles basic FileCoder ransomware. The decryption service is hosted on the same site as the RaaS, and appears to be down currently (v5t5z6a55ksmt3oh.onion(dot)decrypt). The good news: Cylance’s advanced technology detects and prevents execution of all binaries generated by this new ransomware service.
Justice Against Phone Scammers
Authorities in the U.K. have arrested four individuals in connection to a multi-year scam targeting Microsoft customers. While phone-based support scams are not new, this particular operation was rather aggressive. According to reports from law enforcement the average age of targeted individuals was 62, with each victim being coerced to pay approximately 800.00 USD for unnecessary ‘repairs’ to their systems.
In many cases, the fraudsters actually infected the target systems with malware in order to ‘justify’ further repairs and prolong the fraud per-victim.
Such a tactic is, unfortunately, quite common. A standard technique amongst these criminals is to request and establish a remote connection to the victim’s computer. Once this is done, they have full control and can manipulate the system as needed to prolong the success of the scam.
Microsoft has published some useful advice on avoiding technical support scams, how to report them, and what to do if you believe you may have been compromised.

