Introduction
Recently, Fireball malware has garnered a lot of attention by claiming to have spread to 250 million computers. Upon execution, Fireball installs a browser hijacker as well as any number of adware programs. Several different sources have linked different indicators of compromise (IOCs) and varied payloads, but a few details remain the same.
But before this threat was called Fireball, it was labeled by most antivirus (AV) companies as ELEX adware. In this blog, we will be detailing the Fireball threat and many of the ways it presents in order to determine whether the threat is real and, if so, what can be done to block it.
Infection Vector
Fireball has almost always been found bundled with other software, but it’s bundled in such a way that the typical user would not be aware of it – this ‘hidden’ aspect, alone, makes it worthy of exploration.
The primary distributer of these bundles is a company named RafoTech. Their website is currently down following the release of the original blog by Checkpoint, and the command-and-control (C2) channel associated with that URL has also been taken offline. However, you can still find cached versions of the web page on WayBackMachine.
RafoTech has combined several advertising networks from PropellerAds to Dealply to reach the numbers reported. It is possible that bundles from any of these networks currently contains Fireball.

Figure 1: Ad Networks Used by RafoTech. (Image From Their Website.)
Installation
The installation phase is where much of the confusion originates. Once the bundled software is executed, one of many different payloads is installed. We have come across a few major packages, each containing various other adware programs such as QQBrowser, aMule P2P client, BiksQRSS an RSS client, and the list goes on. However, this adware is not what the user should be worried about in terms of malware threat, as much of this adware is common, easy to remove, and not classifiable as malware.
The real issue is any of the several browser hijackers installed by this bundle. Taking the form of a DLL turned into a service, these payloads all install common persistence mechanisms and even clean up after themselves in the same ways (this is reviewed in the next section). These services have several names: we have seen WinArcher/D_Box, WinSAP, iThemes, WinSnare, and MiliMili/ IMO. These are also listed commonly by the AV industry as ELEX Adware.
To install themselves, a DLL is dropped by the original bundle (Archer.dll, WinSap.DLL, iThemes.dll, etc.). This DLL is then run with one of various exports (InstallArcherSvc, SAP, InstWinSnare, etc), which follows a general format of copying itself to a new directory typically under C:\Program Files(x86)\ and then its name (Winarcher, WinSAP, etc). Next, a registry key is created under HKLM\SYSTEM\CurrentControlSet\Services\[Servicename] and \Parameters (Figures 2-4).
This process is how ServiceDLLs are installed in the Windows OS. These kinds of DLLs are easily identified by the presence of the export function "ServiceMain", which is used primarily in these kinds of ServiceDLLs.
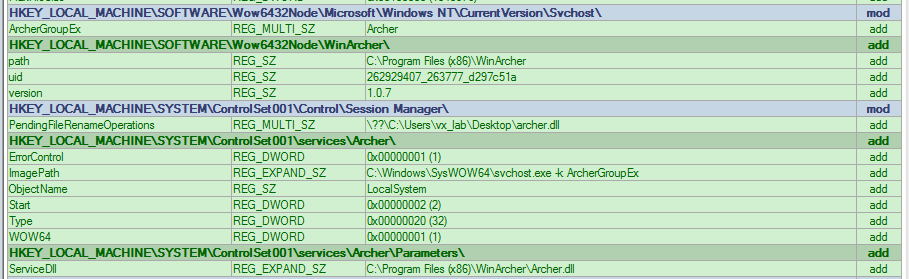
Figure 2: WinArcher Service Registry Keys
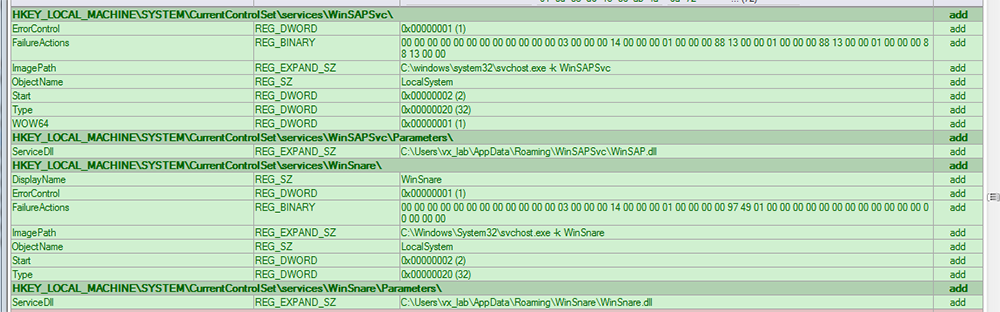
Figure 3: WinSAP Service Registry Keys
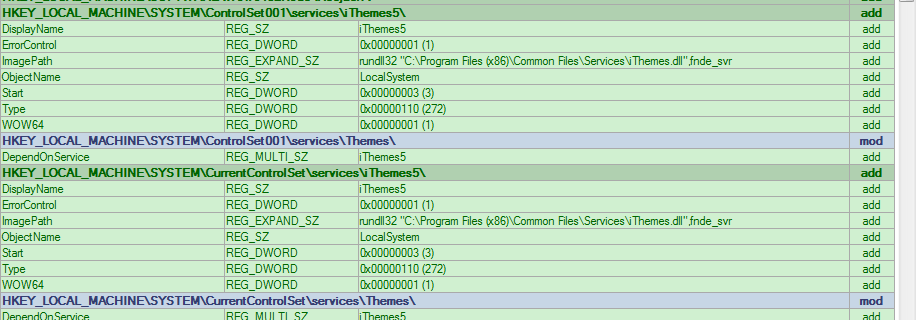
Figure 4: iThemes Service Registry Keys
These registry keys specify the way to run each of these DLLs as a service. This is a common persistence mechanism among malware (not something we would expect to see in run-of-the-mill adware), and this ensures that each time the machine is booted up that these services are running.
Cleanup
Most of these payloads clean up after themselves in the same way, with a trick involving MoveFileExW. This function is used by the OS to move a file from point A to point B. In this case, the second parameter specifying the location for the file to be moved, is passed as NULL. This de-allocates the disk space without moving the data. A specific flag, MOVEFILE_DELAY_UNTIL_REBOOT, is also passed. This ensures that the file isn’t modified while its process is running, and instead waits until the machine is rebooted. This effectively deletes the original DLL without it having to try to delete itself on exit or with a second file on disk such as a .cmd or uninstall file.
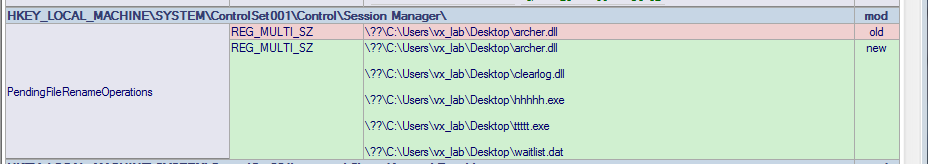
Figure 5: Pending File Rename Operations Created by MoveFileExW.
This cleanup is performed by either the service DLL or by another DLL that is either within the package or downloaded later. WinArcher in particular uses a configuration file that calls several DLLs, including one found in almost all the WinArcher bundles, ‘byebye.dll.’ When reversed, the call to delete each PE in turn can be seen (functions renamed for clarity).
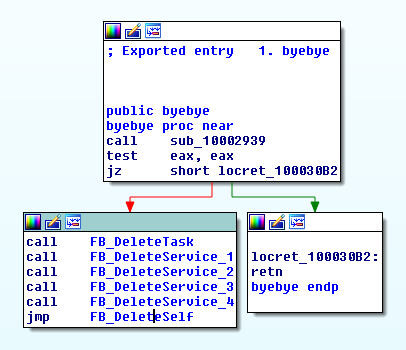
Figure 6: byebye.dll Entry Point, With Calls to Delete Each File in Turn
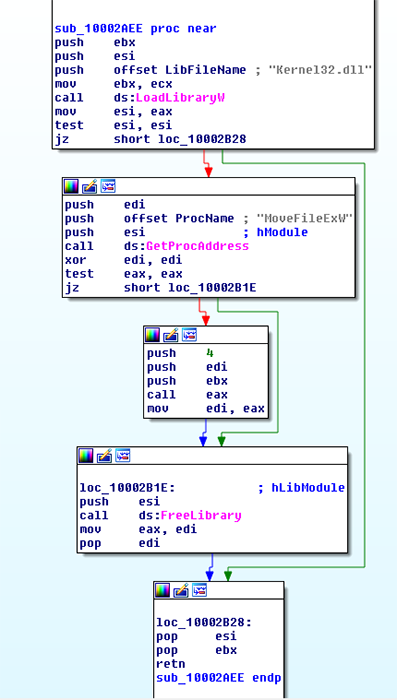
Figure 7: Call of MoveFileExW, Being Passed paramater "4", or MOVEFILE_ON_REBOOT.
Malicious Actions
These services contain the browser hijacker functionality of Fireball. They perform the functions typical of a hijacker, changing your home page or redirecting your browser traffic to desired locations to generate advertising revenue. Again, not something you’d expect from adware.
Many of these services also contain detailed logging capability. WinSnare is a malicious use of Snare by Intersect Alliance, a complex log aggregation tool. While many of the other bundles include files used for information gathering on the host. Some of these are even legitimate Windows tools renamed and distributed. Such is the case for ‘ttttt.exe’ and ‘hhhhh.exe,’ which are actually Microsoft Sysinternals Handle v4.0 and traceroute programs.
Most of these samples also communicate over similar C2 channels, primarily being on the Amazon CDN Cloudfront. Thus, several of the IOCs listed by this and many other blogs are subdomains of Cloudfront.net. This ensures that the C2 and desired files will be available in large scale. Many of these C2’s are listed in the IOC section at the end of this blog.
Impact
In most cases, the browser hijackers installed by Fireball want to generate page views and clicks, otherwise known as ‘click fraud.’ This generates revenue for the attacker and at the same time does not create enough annoyance for a user or community to take action against it. This type of malware infection is akin to the common cold, which causes some discomfort, but maybe not enough for you to go see your doctor. And just like the common cold, some strains will be more impactful than others. The surreptitious nature of Fireball ultimately led to its outing as something to be eradicated.
Conclusion
So, is Fireball adware or malware? The decision is made easy by two things:
1. The installation of the browser hijacker is effectively silent to the typical user. Installing itself without permission or notification to the user is clearly a malicious action.
2. Second, this is a non-trivial uninstall. The standard user would likely have issues uninstalling any of these services, and would require a detailed guide. The packages do not come with uninstallation files or scripts for the typical user.
These two factors have lead the Cylance Threat Guidance Team to classify this threat as malware. As such, users should take appropriate precautions to avoid infection by Fireball.
A good first step is to ensure that your browser, OS, and AV product of choice is up to date. But the best way to stay safe is to avoid downloading software from disreputable, third party, or otherwise sketchy websites. These sites often take legitimate software and bundle it with adware and programs like Fireball.
If you use our endpoint protection product CylancePROTECT®, you were already protected from this attack. If you don't have CylancePROTECT, contact us to learn how our AI-driven solution can predict and prevent unknown and emerging threats.
Indicators of Compromise (IoCs)
Registry Entries
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\WinSAPSvc
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\WinArcher
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\iThemes
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\Archer
HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\services\WinSAPSvc
C2 Channels
attirerpage[dot]com
s2s[dot]rafotech[dot]com
trotux[dot]com
startpageing123[dot]com
funcionapage[dot]com
universalsearches[dot]com
thewebanswers[dot]com
nicesearches[dot]com
youndoo[dot]com
giqepofa[dot]com
mustang-browser[dot]com
forestbrowser[dot]com
luckysearch123[dot]com
ooxxsearch[dot]com
search2000s[dot]com
walasearch[dot]com
hohosearch[dot]com
yessearches[dot]com
api[dot]mhttxtv[dot]com
Several Subdomains of the Cloudfront CDN, Including:
d3l4qa0kmel7is[dot]cloudfront[dot]net
d2taj0e2juarox[dot]cloudfront[dot]net
do0w01qw9sqtu[dot]cloudfront[dot]net
dhxx2phjrf4w5[dot]cloudfront[dot]net
d5ou3dytze6uf[dot]cloudfront[dot]net
d1vh0xkmncek4z[dot]cloudfront[dot]net
d26r15y2ken1t9[dot]cloudfront[dot]net
d11eq81k50lwgi[dot]cloudfront[dot]net
ddyv8sl7ewq1w[dot]cloudfront[dot]net
d3i1asoswufp5k[dot]cloudfront[dot]net
dc44qjwal3p07[dot]cloudfront[dot]net
dv2m1uumnsgtu[dot]cloudfront[dot]net
d1mxvenloqrqmu[dot]cloudfront[dot]net
dfrs12kz9qye2[dot]cloudfront[dot]net
dgkytklfjrqkb[dot]cloudfront[dot]net
dgkytklfjrqkb[dot]cloudfront[dot]net/main/trmz[dot]exe
SHA-256 Hashes:
2F215458F37A955571E24EB0FCD67431D5BDC6D7E0D9C2AC68881822ED82A242
284C735C597CE0CD10BCBE3E98C609219833E1FD43F4C68CB5CBC2632BCE4DD2
11A2C0C782F625AD85D7B54F7D573D285C9E30CE8870983A046E47B780B33462
400AA85681084FDE4D1096C22F6C3C0477F9EFFADCDF89A668DBD84EDB5087BB
58AAD42DE4A8EB9CD3A6664B34A6AFB22F469664B20A9258779A7C04799936B4
4FFA051A0EF0269A639F9D95CAB452C1A6332D6C3B78D20D8FF03C3C23D1CA00
6ACA7154C66B3ABDBB03CEE888E9756DF8CDE2ED20617CB9C475AA04ED479475
6C9EBCA93AF29B63C8F0B8D12DC33A4E1C46FA22D13091D9C2741D0EC5CFC988
33DE5EEF57178C49E9FFF23582D42DB405D79FE48C9685B381BAAE787CBE7923
E9954CBA8845E00AC402389CAF27DE61E1840E3FE672A76BFBA35BB6578125FA
18233554F804A5540252663DD193A06A199E0D5DBFEF8261E30BF7E079C8A106
A40F838AA0EE7AB465BA77FA9AD8DFEBD56DABA5132F9A5DEEE0BA1082975EBC
E161851D6D530AEFF182980166716409E5CEAE97CDED2DF8AF13367BEA3E2FAE
0815DB4E7E3F48362B12974CCFD7FE64FC85B96A9FD35039BC7E32807EEB1C3E
15FFA0994B00081E31CD413E13BBB1D8453DF0ECEA3C2D07AF1282DD7BB57D1B
162EC4D0DB987E484A5BC752FBFBB8B3EB3845D05DEFC35F3359EA2103E1E4AF
38AA1A68179CC72F25F685949926C3DC200AE09905F3B49BAD49DE5B5595946A
3EE86057CD4C0D230942C912A62B791C5AA383F5E2C8C824E3472F8EF3FF2F8B
3FD1BFF4671366D16C15FBE92B1A3166EBF24EC1A64ACD5A034440F1A090B111
544CD84884185995792BF09C35D3E603A02B44A356884E63A6927AFE7A8CDF82
5FA0BA7FBD5AF8F3A1C807A802FFDA8DD4A4EEAB8C2959CBA9B11CAAD5DF6BC3
655B9329B643692785FC2DF6FC61CB84696E51E883B21B1948EF89DD52D7760B
B39BA351B1FA1A0A1976D7CD9CF22733D407369A821218CEB38E88C47E5B3643
E47D4E47094EC468C3391A5A8C1D291765D2F6B06FE6E418ABACA568354B5C48
0ACF3DF4EA31C665DE1BDD56A4C3507615E69A12035B0204355DA2FF58419264
57D842DFD2AF0169E8D4BFB69E108998A6E65385501B39F14DC7D410BF090414
682FE4D3E9B054BCFFE38A214BE87E4350D066C8BA30FC2182C4E517EC77A857
68D3635E55D3510CB6668B231367ADBE265705E751BF57A1584B81D8A775FEF1
AEBF4DFBDF4C2642A7D47703FAD7F777CE1C9BFA484D7FA876BB8411836617F0
DFB028E7E6D7EA72D68229FA23D79BF48F8916AE8BB9AEBFE7EE4D70A08E1436
0267FBF3BE427DEBF042A0E945AB8535CD9A04419232C4D502D33ED4F5329F49
3E1D2C2CA481C173B0D460C15AEFB61F25224EAACAE493494D5D0CB55E08C120
57983A0341A9631CF87AF470B991316355C1095CB21A5B124C7BE928A46880CE
5BC12626EC6B305DE561D4EF0F13C3297F27A0B6549E4B485CC79EB73FC2D318
865477A607BB37E019E05D3487E3B8632F3F739D95AB8B0966045389F42CB175
915E06180B5032BE49AE14CC746B06207E73D94A4D64C8DB811248D8B5519F7D
9286D4F07A82B2C5B005FA9B0329CC988BE47D8A10622874A3641E746559498F
9AB555A8FE0E1ABB670E669583D5DD4AFCF54535B3EC01B608B4501CB26CDD1A
B65E1A934048D2B54362C584094C3A5C90F9C63DDBDAFCB248CB27EAD76639A1
D291B5000B6E7797123922FC5A9305C6B1F209F315BFC92217748C82E71B58B7
E69A95E9D2C8BAAEA1FAB7815F0EAFB9AF1920A76E10D5FD9A11BB617E25EC12
EEE9CF281E008947D96FCC7759629F027309707F7441ABF690CC13218E00235B
F5D582CD520DBD28727717BAFA49F9ED0412D34B99681DB74F87C96A3BE3AE02
0805850AC46B9E4F7BF1D18FA9148BAD62CEDD51C4AE6D06EC468E9FD25042D9
0B56D132F8CA7D8F33A5A24E5C8903CC405FEFC23443B4F1E20C6BF46C9D6218
0F164102B71FAE51404AFBC53A9A275F7B0F92B4C65A6C3040142F8FDB167E54
13E3298A2EF48779091F8AD3D49BBA1B6B97C5C01612D84275AD3C1EB9E5AC98
156F459A6A0C831739E6210BCFEC31E5D5DB615C94E1AEF13E8B6B5D3D7BDDC6
1B1477A4AE406C463DACDCC56A79E7B8F3A8684655BEA1F2B99AE10FFE98FE2D
20F7E4FC5DFF210ACC96428ECAAA502EF858CA5C3D18C0D32621A646FD99298F
25DA2F5E73454F12D288AEEB24C65065557FAEB13C281A5A964CD4FD70DDA939
2D83B5BE859552241A79044E0DEE2CDAF6FDDFC7F806A6E1F938658BBEBAA676
2E1BA4E067B79E078E7BB012B2D10359E9F980224E40CA01979EC1905D4A5FD2
30311F01F725808901C69930584F4FF929A2B46CEBC0CB4F19BFF561D83B4A51
3A56701E2ACBA6069FB8622553A550C37098CDA14799B52820385F2D1EF14664
3CF38F709358972EB7F9DB2D6A210FC8B8446FFE7BDCA30260E0F71E4CE08412
3FFB16370E2062533818D22CFF4955BF67D3CB8FC46FB803D00345E8FE56E77F
4AA016115E3F8EDF58A4E1DEF4C242938F97E6E80136DB03140A917560253B04
4C6EAD121D3C48AC1E80277CA8A2A35122299AE53801380A701D1AF0DFF2FCC8
530D37FB041E4AFBEB162322A3B88C66FEAC001A14AF958947B8526E7ECF93C8
577404D9A20BD153346413CDA6A8E32EA45D017F3AB854B9BF6AD4D964382503
5A2A9E6B60572172C0A5121696114CE223DE301D6D8E89C01DA9D394A9E625AE
64ECC432CD3D74938BB90196BCE8590B24FCD69FA7E8485134D40BDBB0DA7646
6647E0E61AD30D872811C021586F6EE750C8C6C4FA52FB8791654CA3028B54F0
6B602DDA1DCB1CBF588599B5B6F6439FBE906A00864EFF063CBC7BA39BABD22F
6C3ACEC3A6E347EE378B1B5147EF5E76A39FA731DCC98BD12D87AC29A17B7958
6E5CE19DF19D90A13CB5FC5C5ACA389C82F07383BD35A46A1C84A76349A5110E
77CDB84C42CBDFB7CE0FB407B1980D8BC95915C8A801F05BA73A7B00FA64FF8B
799A205758FDDA30ED24145D33410442B53CC80A1232F2C5D65A2B5621449E41
7A0B5C78F95D8357C4EB48608C08044C3787282FB041F19854666591218A6C2A
7D9B3E706891343B06FB33DA722FB1557397E577CA07D85D943D1A277C3DC663
81DCC7B740C83CA971ACCA3E5BB6F718FE8B1E7478A3294B6B6E8AC6C62D4454
9019958B5D45A5A13E6D544CCECD175482C83C86DE7A5804602332139AE6A7E9
AF65C216FE7959D0AD6B21BF527E2B58B07FCCF0AC00214C41BF70482EBE03F1
B1C2DD5CDE9DA4D985D995A564D1843AA8A0B0A2BEB3035579F31A931B100DC4
B41EA41937F515AFE4FB975D09996F0FC1ABF014F653EBC4D579A9350957A49C
D16803BC2E81901FB4B9E8809E56C26C6E5EF929CB2D9A551C2B914C8F65575A
D718C9AB800CE3F39E6788D153551DF103DF9827E8B77C3B01C5081D5F408173
D97FC86638848DA497EF67E6706853D4BEA8246C01A9AFB3C827D436081524EF
DDE652546F6CFA5781EC76C13A42921675052F786A7DC5D33EF59226C0C5A174
E2EA0C2207ECFAC8C99C1B122762D9838A99F59F7AE7AE172191EF66A290FB20
EE5663A7A67BA1E9412B009345C56CC0FDDB40B6FECAC9381980CC81F424513B
F2D5837F6337ED70F543BD2C86D948641A57DF50E67FD6A60A5A35F24B180D26
F85301BD9D5ACFA28616B470627BBD4AB3A14EE5BD643ADC73931C73ABFEE239
FD66D76092842AD79BAD278519431EE6F2D46272AC6C48A07B1A8878F22C7190
A0D68189A1140867FDC556A6DC63FACB184F834AC603ECEA08EADC36525B44C8
D508B0C1EF20EEA48254A5422FB7C3C9BDFE82C8E7F7BA088397BF7D03552B33
7D68386554E514F38F98F24E8056C11C0A227602ED179D54ED08F2251DC9EA93
14093CE6D0FE8AB60963771F48937C669103842A0400B8D97F829B33C420F7E3
656CEB29CF552689F2E3F1B10BBBD39CA74C0CE76451127AACF1851925E3C2CA
AEBBF57479C4D39D0B9A76595DA28F8677B2F1E0A3F693E96B2B5FCB03CEF8BC
CD2BDBDFC57E57140412BA57BE83DA3FF8856107D8AC288AE18DF77E2F2F05BE
Filenames:
Archer.dll
Lancer.dll
iThemes.dll
WinSAP.dll
WinSnare.dll
Beserker.dll
MIO.exe
Clearlog.dll
Byebye.dll

