Introduction
Cryptocurrencies such as Bitcoin, Ethereum, and other altcoins have seen an increase in popularity and adoption among users and service providers. This has resulted in increasing appreciation of value in the last six months (Figures 1 & 2). Market capitalization of these virtual currencies is now pegged at around $100B (Figure 3) and continues to rise with Initial Coin Offerings (ICO) going on to fund developments of projects related to cryptocurrency.
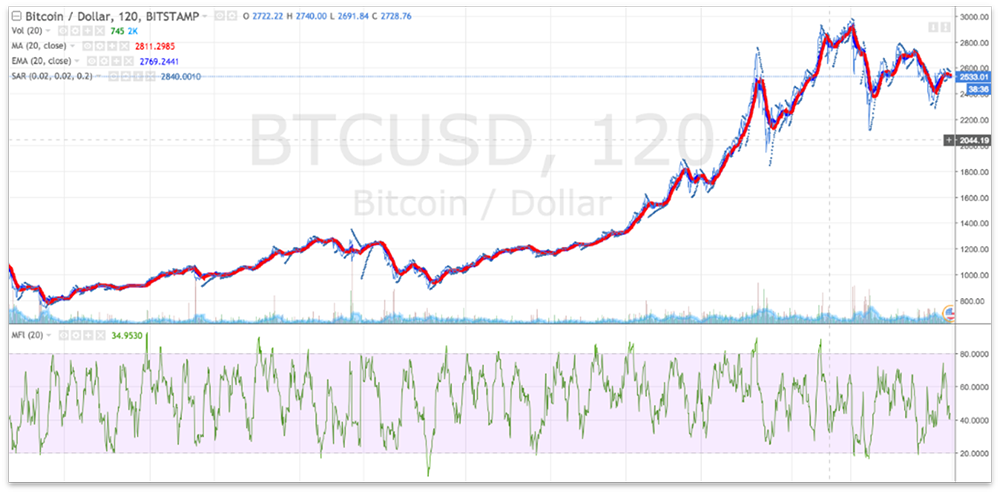
Figure 1. Trend of Bitcoin (BTC)
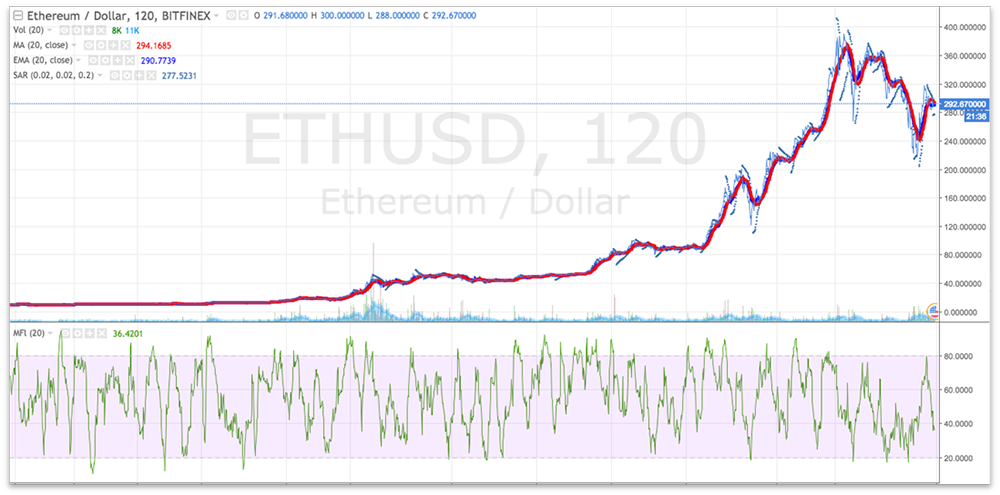
Figure 2. Trend of Ethereum (ETH) Price
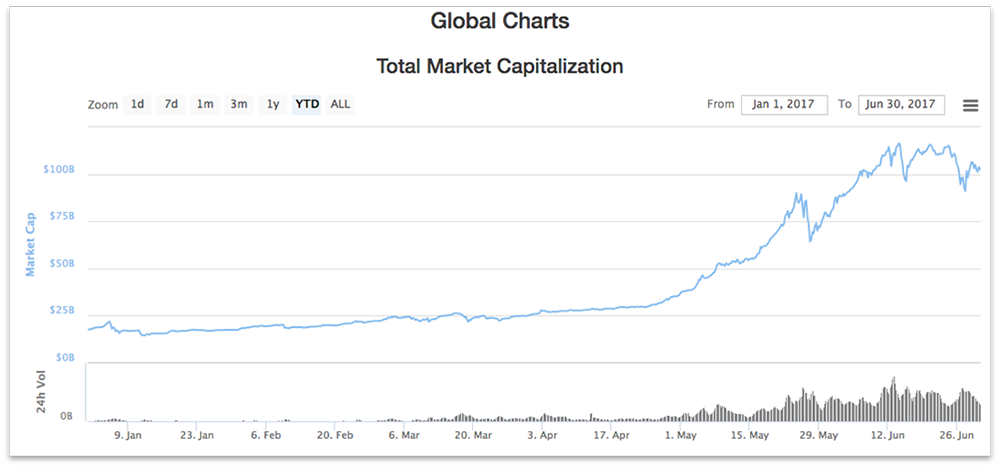
Figure 3. Market Capitalization of Virtual Currencies
This vast market certainly hasn’t gone unnoticed by miscreants and cybercriminals, who have already set their sights on these virtual assets as potential targets.
There are various ways one can get hold of cryptocurrency. Two legitimate ways include:
- Buying cryptocurrency from online exchanges such as Coinbase, Poloniex, Bittrex, Waves etc.
- Running cryptocurrency mining software
On the other hand, malware authors usually employ the following illegitimate and/or illegal tactics:
- Distributing ransomware and getting paid with cryptocurrency
- Use cryptocurrency-stealing malware that targets digital wallets
- Compromising systems and using those resources for cryptocurrency mining
Cryptocurrency-Mining Malware
Here is some notable malware that has been found compromising systems and delivering payloads with cryptocurrency mining capabilities:
Malware Worm (Miner-C/NeksMiner.A/NightMiner-Config)
A SophosLabs researcher reported a cryptomining malware found on NAS servers back in August 2016. This malware could propagate even on mapped network shares and open file servers. Another malware sample from this variant shows that it has been active since 2015.
SHA256: | 8bee95131ae47d9a5e3c8cccceaaad7e5567eac66ae7c0d875c9a57d3fc7acef |
Filesize: | 4.46MB |
Like the one reported, this malware is packaged with NSIS and disguises itself by using a folder icon. If the system is set to hide file extensions from known file types (as shown in Figure 5), it can easily be mistaken for a folder. This may cause unintended execution by an unsuspecting user.

Figure 4: Folder Icon
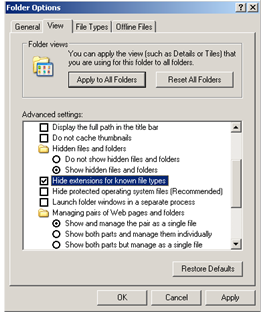
Figure 5: Folder Option to Hide File Extensions
Once the malware runs, it copies itself as image.exe in the %USERPROFILE%\Images folder.
Along with it are the dropped files as shown below:
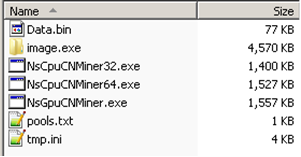
Figure 6. Dropped Files
- image.exe – copy of the original malware file.
- Different versions of cryptocurrency miner files are executed based on system architecture and CPU capability. The malware checks whether it’s running on Win64 system and runs the appropriate miner files accordingly:
- NsCpuCNMiner32.exe
- NsCpuCNMiner64.exe
- NsGpuCNMiner.exe
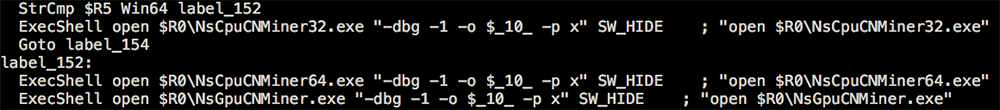
Figure 7a: Selection of System Architecture
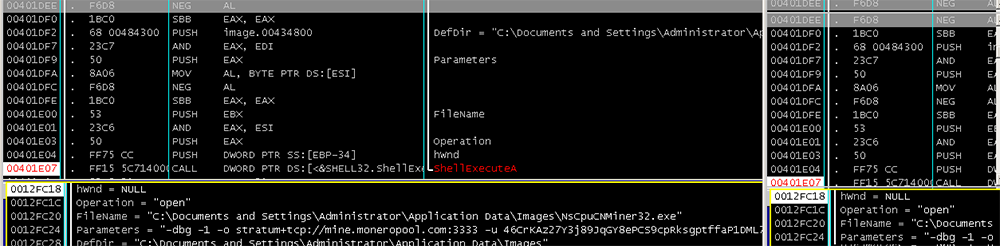
Figure 7b: Selection and execution of “miner” files.
- Pools.txt – contains the mining pool servers to join.
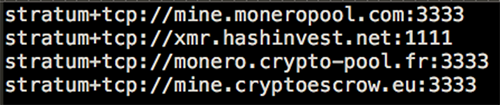
Figure 8: Mining Pool Servers
- tmp.ini – contains the parameters to use in running the “miner” file including the digital wallet.
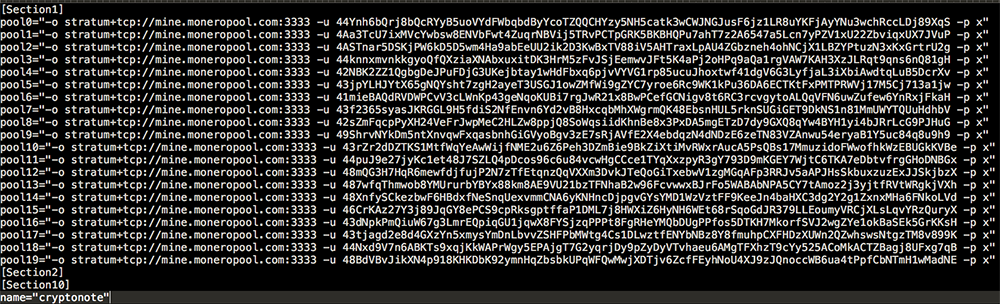
Figure 9. Digital Wallets
Running the cryptomining malware image.exe will in turn run the appropriate cryptominer files, as can be seen below (taken from Process Explorer).
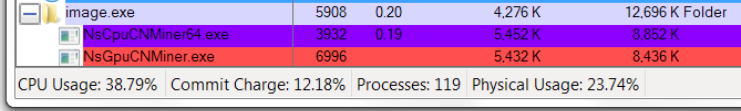
Figure 10: Running Process in Process Explorer
Auto Startup Technique
To ensure this malware runs on every system startup, it adds the shortcut file image.lnk to the startup folder. It also adds the registry startup entry below:
Key: HKCU\Software\Microsoft\Windows\CurrentVersion\Run
Value: Coin
Data: C:\Users\{username}\AppData\Roaming\Images\image.exe
Other shortcut files used on other malware variants are as follows:
- images.lnk
- cryptonote.lnk
- run.lnk
- start.lnk
Other executable filenames used:
- CNMiner.exe
- img001.exe
- darknoted.exe
Worm Propagation
It is important for the malware author that this cryptocurrency mining malware spreads to as many systems as possible, in order to control a larger pool of CPU resources for “mining.” Aside from initially dropping a copy as image.scr to root directories of C and D drives, it will also try to enumerate and drop the malware copy to available system drives (C-Z), including mapped network shares and open file servers.
It also tries to share the installation folder to the network for other users, as can be seen in the code below:
nsExec::ExecToStack "$\"cmd$\" /c net share Images$_5_=$_1_:\Shared /unlimited /cache:programs"
Malware Updating
The malware will check for updates by connecting and downloading configuration files. This enables the malware author to update the digital wallet and mining servers to join. Below are examples of URLs being used to get updates.
- stafftest.ru
- hrtests.ru
- profetest.ru
- testpsy.ru
- pstests.ru
- qptest.ru
- prtests.ru
- jobtests.ru
- iqtesti.ru
- tradetests.ru
- testswork.ru
- worktests.ru
- jobtests.ru
Adylkuzz Monero Miner
A malware author will jump on anything that allows wider distribution of their cryptomining malware. Soon after the release of a huge cache of exploits from “The Shadow Brokers,” a cryptocurrency malware was found using them. In our previous blog post, we demonstrated how Adylkuzz cryptocurrency malware used the EternalBlue/DoublePulsar exploit to compromise the system and to propagate.
Proofpoint published a blog post about this malware back in May. It was theorized that the malware author may have used a bot to scan the Internet for open SMB port 445 and tried to exploit it with EternalBlue to gain a backdoor connection. Once successful, it would download the cryptocurrency miner cpuminer to mine the Monero coin. The Shadow Brokers advertised their subscription model using XMR (Monero) as opposed to BTC, which was used for previous donations.
Interestingly, Adylkuzz malware added the firewall rule shown below to block SMB port 445, effectively closing the door behind it for other potential attacks. It is believed that this was done to keep the infected system to itself and close it for any other malware targeting the same vulnerability.
cmd.exe:1772 > "netsh ipsec static add filter filterlist=block any srcmask=32 srcport=0 dstaddr=me dstport=445 protocol=tcp description=445"
cmd.exe:1692 > "netsh ipsec static add rule name=block policy=netbc filterlist=block filteraction=block"
cmd.exe:3856 > "netsh ipsec static set policy name=netbc assign=y"
EternalMiner Malware payload of SambaCry/EternalRed
Soon after, a Samba vulnerability in Linux systems was reported as SambaCry/EternalRed. A cryptocurrency malware named EternalMiner used it to propagate in the network and downloaded a payload cryptocurrency miner. Securelist published a blog on this last June.
For the exploit to be successful, it requires guest accounts to have write access to Samba Share or the attacker having access to valid credentials. Once successful, the malware will identify network shares; upload the malware and trigger remote code execution to download the payload cryptocurrency miner cpuminer/minerd.
This miner is a modified version joining the mining pool server xmr.crypto-pool.fr:3333 including a hardcoded digital wallet of the malware author. Below is the payout history of this wallet amounting to $6,847.00 in today’s exchange.
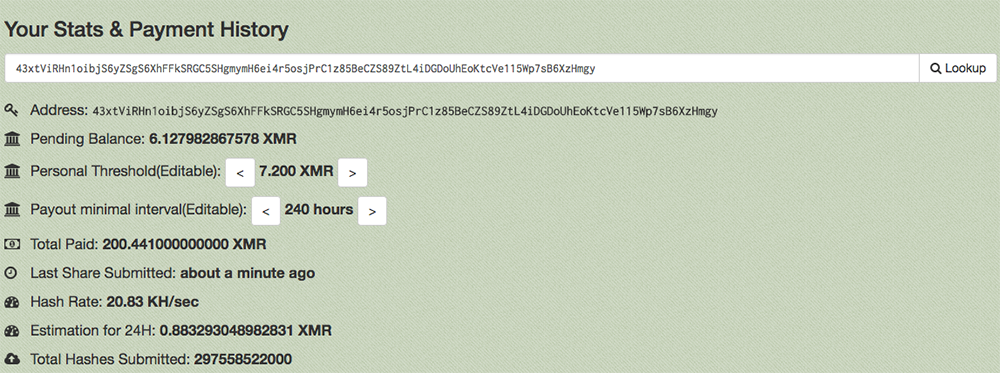
Figure 11: Payment History of the Malware Author’s Digital Wallet
Monero Cryptocurrency
Monero (XMR) coin has seen increased interest lately due to its technology of being an ‘untraceable’ coin. It boasts of having stealth addressing and being secure, private and untraceable. “Mining” Monero coin is still profitable, which is why it’s the current cryptocurrency of choice.
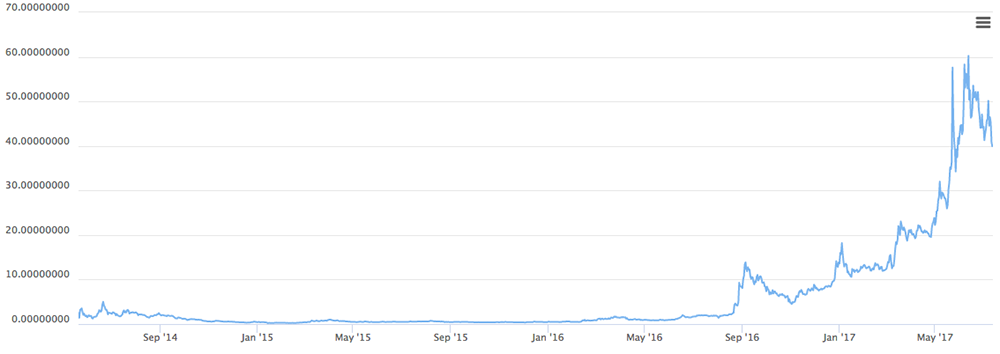
Figure 12: Monero (XMR) value in USD
One way to mine Monero cryptocurrency is to join a mining community such as Moneropool. On their website, we can see how much has been mined and how much payout has been received from mining Monero coin. Looking at one of the digital wallets used by the malware author (as seen in Figure 8), the payment history shows it gathering 2,929.6 XMR, which is roughly around $115,000 in today’s rate.
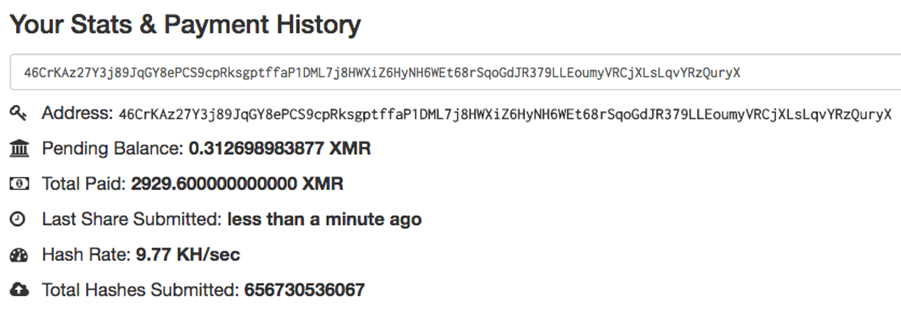
Figure 13. Payment History
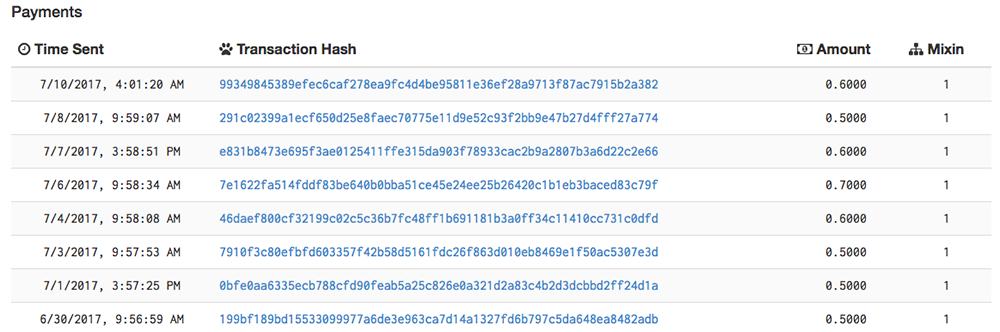
Figure 14. Payment Transactions
Impact to User
It is worth noting that infected users will likely not notice the cryptocurrency mining malware running in the background on their machine. Symptoms that may be noticed are a sluggish system or a degradation of server performance due to computational resource usage in mining cryptocurrency.
Although “mining” a cryptocurrency may be benign in the sense that the end user is not harmed, a compromised system is still at risk for potential introduction of other malware. The malware author may also take advantage of the backdoor installed for other purposes, or may leave the vulnerability open for other attacks.
And of course, malware authors are not concerned with writing robust software designed to exit gracefully in the event of an error. The unintended loss of data from a system crash is always a real possibility.
Conclusion
Continued profitability in mining cryptocurrency will pave the way for an incremental increase in cryptocurrency-related malware attacks. We also anticipate a new wave of malware worms and bots motivated to distribute cryptomining malware.
In addition, we expect to see malware incorporating publicly-disclosed exploits and even targeting zero-day vulnerabilities for effective and widespread distribution of cryptomining malware.
If you use our endpoint protection product CylancePROTECT®, you were already protected from this attack. If you don't have CylancePROTECT, contact us to learn how our AI-driven solution can predict and prevent unknown and emerging threats.
Indicators of Compromise (IoCs)
SHA256:
00E553773991DDEBBA0365BDEB67D46E4007B63D7E0EF508098C0A48A49885D0
090F5C02642617DB11F313C5410AFA5299BFD7D258450765D24C49F88A0A16C2
0F84CA4C4E315B1765D69F9EFC24178E69DA3D9D6C130844ED2AF834B114C8D1
10A488F92AF283EFE67F7CD05BF8B4D850A5C6F8FB32AADE34DA4AF96CC6E7D8
13A0CE618DCD0E17C7D8267174D07A997D39FCEA10F8951EA7C0B5218DDCFE85
1B8CA65DAF769CA1ABE3662CB388A2D9E2FFA4CF819CCE415531413149745318
1FF8C3CF53DA5B30CDBC014A5FBD83181497436F8D580E22DAD01A6DD4FCFB49
272D64642870ACB40110EE752C4DA1601DB5C7910DB3A61FEB2B1802172F03D5
37D2CEF6E7631B55A54C9A0E6763EE3ACFE0BB15B73E89CCC1E0A98D024E119E
38145C78886CCBF48C3FD346D66D0DFDC631941A9231A4FF1F9B15B4D50D97FE
3AE682F06B20F03441D476431C95BCA496FAB0041C393CFF6A44EE80669020A6
403A2049968EDC7F1BC8EF8EAA88A5B73917F65E10C388B7CEAB8BEF9ECD4A5A
491C30FAABE1C6073F8B4ABA930DE642832D1BFE0128F121B1A6B50FFBD16599
65CC03A44EAC3C045A54582D5A9447E14277DCB35A8D0AFB0A8BED9F4420FB5C
669BFB2CD3644072BF57240B1321337908BC7345BD5F416CA36EEF949EB10B5E
68902AC68488F2113EFEBA2C87E58295B249C542860EC501EB7388C40F37880B
6DE22A0B138E245F2E72915913FA75F9F0CF2A633B6153AFAB471CB3328A7AA5
72135D49294D8D9370871AE5B6207CC1958140AE6CCB486120AFAB885BA64E70
7A2A860BB344526E8546ACD172522B4D276A4647F43DD4720281D40E390B283E
82CC404D0C3CD1C0B0DF13D9972A7A02EC2020869530744670A3DE0DB90A30A1
8BEE95131AE47D9A5E3C8CCCCEAAAD7E5567EAC66AE7C0D875C9A57D3FC7ACEF
A0EBA3FDA0D7B22A5D694105EC700DF7C7012DDC4AE611C3071EF858E2C69F08
A480A280C6B39B41BC38F4C24ACC8E93A99DE51C3E32F519344DB1EB13A35E35
A5FEA08A79EAA9F11AA922BAA3CC7D25F97FC2044C1E33735A471031C1B41140
ADBFB23C89DA996DCC8794BEC8C8E9AFCA410B08729877A6024BC56D814FB0D8
C118F243925956A486A4052CBC3DAD2523C99B5D2EAA8B4CED5F38596598A9D7
C89F66405D51166101D8E71F32B7519FE0C8AD44127E3E42C2F69A70F56EE27F
C8B3F03B0275B5BCEE34A685187CD6B648346D9CA7F1B0CBB255C45856F7A49D
D0326F0DDCE4C00F93682E3A6F55A3125F6387E959E9ED6C5E5584E78E737078
DD4D0922D60BAF2F6C9B63C8B90E1B6FE85097C325301ED6548B82213C53C0A4
EBDDF44FFCA23473C9C675A8D869926754735597293094CA9FF89CF806229CE0
Digital Wallet
44Ynh6bQrj8bQcRYyB5uoVYdFWbqbdByYcoTZQQCHYzy5NH5catk3wCWJNGJusF6jz1LR8uYKFjAyYNu3wchRccLDj89XqS
4Aa3TcU7ixMVcYwbsw8ENVbFwt4ZuqrNBVij5TRvPCTpGRK5BKBHQPu7ahT7z2A6547a5Lcn7yPZV1xU22ZbviqxUX7JVuP
4ASTnar5DSKjPW6kD5D5wm4Ha9abEeUU2ik2D3KwBxTV88iV5AHTraxLpAU4ZGbzneh4ohNCjX1LBZYPtuzN3xKxGrtrU2g
44knnxmvnkkgyoQfQXziaXNAbxuxitDK3HrM5zFvJSjEemwvJFt5K4aPj2oHPq9aQa1rgVAW7KAH3XzJLRqt9qns6nQ81gH
42NBK2ZZ1QgbgDeJPuFDjG3UKejbtay1wHdFbxq6pjvVYVG1rp85ucuJhoxtwf41dgV6G3LyfjaL3iXbiAwdtqLuB5DcrXv
43jpYLHJYtX65gNQYsht7zgH2ayeT3USGJ1owZMfWi9gZYC7yroe6Rc9WK1kPu36DA6ECTKtFxPMTPRWVj17M5Cj713a1jw
41mieBAQdRVDWPCvV3cLWnKp43geNqoKUBi7rgJwR21x8BwPCefGCNigv8t6RC3rcvgytoALQqVFN6uwZufew6YnRxjFkaH
43f2365syasJKRGGL9H5fdiS2NfEnvn6Yd2vB8HxcqbMhXWgrmQK48EbsnHUL5rknSUGiGET9DkNS1n81MmUWYTQUuHdhbV
42sZmFqcpPyXH24VeFrJwpMeC2HLZw8ppjQ8SoWqsiidKhnBe8x3PxDA5mgETzD7dy9GXQ8qYw4BYH1yi4bJRrLcG9PJHuG
49ShrvNYkDm5ntXnvqwFxqasbnhGiGVyoBgv3zE7sRjAVfE2X4ebdqzN4dNDzE6zeTN83VZAnwu54eryaB1Y5uc84q8u9h9
43rZr2dDZTKS1MtfWqYeAwWijfNME2u6Z6Peh3DZmBie9BkZiXtiMvRWxrAucA5PsQBs17MmuzidoFWwofhkWzEBUGkKVBe
44puJ9e27jyKc1et48J7SZLQ4pDcos96c6u84vcwHgCCce1TYqXxzpyR3gY793D9mKGEY7WjtC6TKA7eDbtvfrgGHoDNBGx
48mQG3H7HqR6mewfdjfujP2N7zTfEtqnzQqVXXm3DvkJTeQoGiTxebwV1zgMGqAFp3RRJv5aAPJHsSkbuxzuzExJJSkjbzX
487wfqThmwob8YMUrurbYBYx88km8AE9VU21bzTFNhaB2w96FcvwwxBJrFo5WABAbNPA5CY7tAmoz2j3yjtfRVtWRgkjVXh
48XnfySCkezbwF6HBdxfNeSnqUexvmmCNA6yKNHncDjpgvGYsYMD1WzVztFF9KeeJn4baHXC3dg2Y2g1ZxnxMHa6FNkoLVd
46CrKAz27Y3j89JqGY8ePCS9cpRksgptffaP1DML7j8HWXiZ6HyNH6WEt68rSqoGdJR379LLEoumyVRCjXLsLqvYRzQuryX
43dNpkPmQiuW67g3LmrEQpiqGU1jqwX8FYSjzqPPPt8FgRHeYMQbDUgPPfos5DTKH7MkorfSVJ2wgZYe1okBaSEk5GrKKsH
43tjagd2e8d4GXzYn5xmysYmDnLbvvZSHFPbMWtg4Cs1DLwztfENYbNBz8Y8fmuhpCXFHDzXUWn2QZwhswsNtgzTM8v899K
44Nxd9V7n6ABKTs9xqjKkWAPrWgy5EPAjgT7G2yqrjDy9pZyDyVTvhaeu6AMgTFXhzT9cYy525ACoMkACTZBagj8UFxg7qB
48BdVBvJikXN4p918KHKDbK92ymnHqZbsbkUPqWFQwMwjXDTjv6ZcfFEyhNoU4XJ9zJQnoccWB6ua4tPpfCbNTmH1wMadNE
43xtViRHn1oibjS6yZSgS6XhFFkSRGC5SHgmymH6ei4r5osjPrC1z85BeCZS89ZtL4iDGDoUhEoKtcVe115Wp7sB6XzHmgy
References:
https://www.tradingview.com/chart
https://coinmarketcap.com/charts/
https://www.secureworks.com/research/cryptocurrency-stealing-malware-landscape
https://blogs.forcepoint.com/security-labs/21st-century-49ers-small-time-cryptocurrency-mining
https://www.sophos.com/en-us/medialibrary/PDFs/technical%20papers/Cryptomining-malware-on-NAS-servers.pdf?la=en
https://www.secureworks.com/research/cryptocurrency-stealing-malware-landscape
https://www.cylance.com/en_us/blog/https://threatvector.cylance.com/en_us/home/https://threatvector.cylance.com/en_us/home/https://threatvector.cylance.com/en_us/home/threat-spotlight-eternalblue-ransomware-eternalrocks-worm.html

