Wait, what????
Ok, I’ll admit – I made the “fangs a little bigger…” (Great Outdoors movie reference).
As noted in a recent blog post by FireEye, researchers highlight the fact that they’ve discovered a malicious document floating around that uncovers the use of CVE-2017-8759 vulnerabilities to distribute FINSPY malware.
Details of Attack – Dropping FINSPY
This vulnerability is currently being exploited in the wild by a malicious document targeting Russian-speaking users. Tricking the user into opening the document, it executes some scripts that install malware on the system. While not new malware, FINSPY contains a number of malicious surveillance tools that can then be used to conduct further attacks against systems.
CylancePROTECT® protects you from the effects of FINSPY. See our short demo video below:
VIDEO: CylancePROTECT vs. FINSPY Malware
One of the terms we use at Cylance is Temporal Predictive Advantage (TPA). This is a term we use to illustrate the fact that Cylance’s artificial intelligence (AI) models are actually able to predict that a file is going to be malicious, without ever having seen that specific sample before.
To demonstrate TPA, we commonly take an old version of our endpoint protection product CylancePROTECT, install it on a system and throw the malware sample at it and see what happens – it’s actually a LOT of fun to play with malware like this.
This morning, I did just that. I wanted to see if an old version of CylancePROTECT could predict that this new sample was bad.
I downloaded a sample of the FINSPY malware from a public source. This sample was first submitted on August 21, 2017. And I also noticed that a lot of other vendors could detect this malware – which is really good. But I wondered how many of them could’ve detected it BEFORE they got a sample.
I logged into one of my test systems that has Windows 7, Office 2013 and CylancePROTECT version 1320 installed. This is the version of CylancePROTECT that we released in November of 2015 using our AI model produced in mid-October of that same year.
In addition – because I LOVE to see cool malware run, I further hindered this test system by taking it off the Internet – no cloud lookups for me!!!! I wanted to see if the AI engine on the endpoint could see this file as malicious without any crutches available. I wanted to see if could truly predict a malicious file.
I then copied the FINSPY sample over to the desktop and double-clicked – that’s the fun part. You never know what’s going to happen when you play with live malware! Sometimes you get to see something VERY interesting.
However, in this instance – I was pleasantly disappointed. CylancePROTECT successfully predicted that this file was malicious and prevented it from running (see screenshot below):
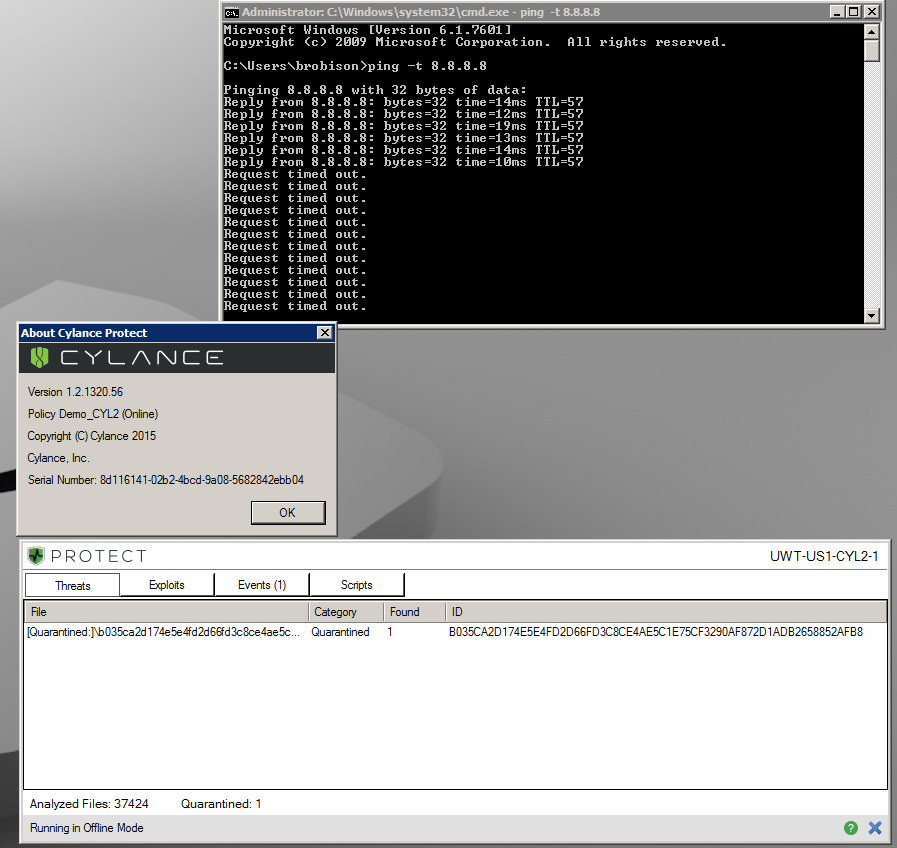
Figure 1: CylancePROTECT Quarantining FINSPY
As I said before – I DID make the fangs bigger… The malware sample was not a true zero-day – it has been known to the human race since August 21, 2017. And the version of CylancePROTECT I used wasn’t exactly a full 2 years old. The agent was released in November of 2015 and its AI model was built in October 2015; only 22 months BEFORE the malware sample – not the full 2 years.
However, in the world of preventing bad software from running on our desktops and servers; it’s very powerful to say that a security product, built NEARLY 2 years ago, was actually able predict and prevent the effects of this malware.