Bad Rabbit: A Hare-Raising Campaign
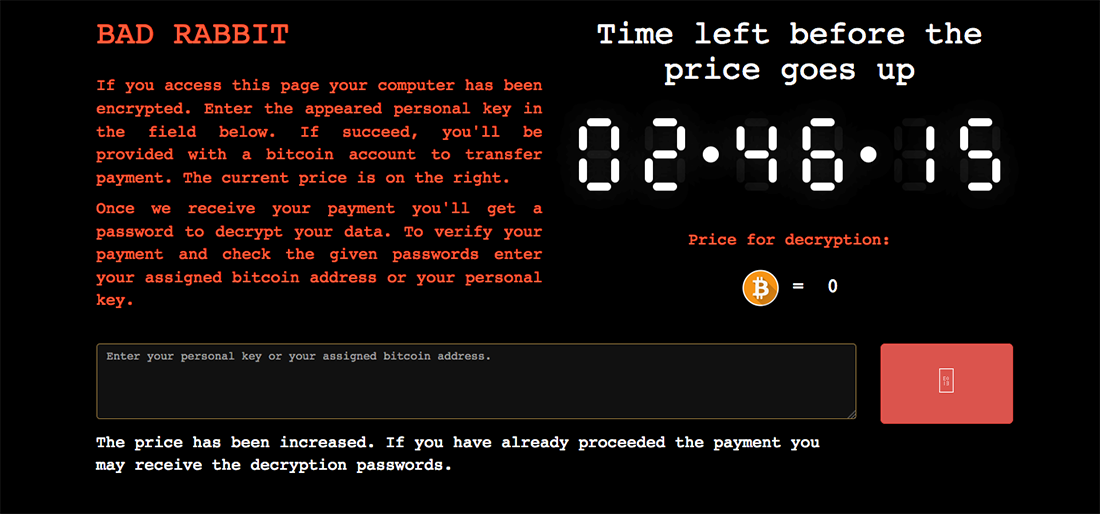
On October 24, numerous users fell victim to a multifaceted malware campaign. The “Bad Rabbit” attack (named after the messaging on the ransomware payment site(s)) rapidly hopped across the Ukraine, Russia, and potentially other locations (reports have yet to be confirmed).
The components and style of the attack were not novel, but this campaign does serve as a reminder on just how effective the ‘bad guys’ can be when they embrace patched exploits (the EternalRomance exploit) along with the old standbys (ransomware and wiping components, and Mimikatz).
Bad Rabbit’s initial attack vector was a drive-by download claiming to be an update for Adobe Flash Player. Once active on a system, the malware drops and activates additional components, which includes the ransomware, credential dumping, and disk encryption (DiskCryptor) components. Scheduled tasks are also used to kick off both a system reboot, and the ransomware component.
While it is tempting to jump to conclusions around the origins of this attack (due to it being similar in functionality to NotPetya), it is important to note that the codebase for Bad Rabbit is not identical/shared with any other previous attack. Any conclusions drawn around attribution are speculative and should be considered with a heaping bowl of salt.
Cylance customers are fully protected against the Bad Rabbit attack. In fact, our technology protects against these types of threats without the need for any updating/adjustments to our detection capabilities. Protecting systems against evil unknowns, whenever they occur, is core to our mission, and Bad Rabbit has again proven the power of our true AI-based approach to full system protection.
Additionally, we have posted two blogs covering the technical details and prevention of this threat. Additional prevention options can be explored as well. These include restricting execution for non-privileged users (non-admin), or prohibiting execution based on the “borrowed” certificate used to sign the dropper.
Serving the Greater Good: The CSE Releases Assemblyline to the Public
It’s always good to highlight positive stuff that occurs in the security world, when we mostly just hear about the dumpster fires. One such good example is the release of “Assemblyline” by the Canadian Security Establishment (CSE).
In a move to increase transparency, as well as help companies and consumers battle malware, the CSE has open-sourced their modular and distributed file analysis framework (Assemblyline). While there is some overlap between Assemblyline and tools like Cuckoo Sandbox, some may find the capability to scale and handle larger datasets (sample analysis in masse) appealing.
Assemblyline can be deployed as an individual VM/appliance, or to larger-scale production clusters. For those on the front-lines of the malware battle, it very well may be worth a look.
For additional information, see the CSE’s repository here.
Open RDP Ports Lead to Widespread CrySiS!
Recent updates from U.S. Government intelligence have highlighted the ongoing spread of the CrySiS ransomware family. While the family is not ‘new,’ this is yet another good reminder of how persistent these threats can be and how long they can thrive in-the-wild.
The primary difference with these campaigns is the use of RDP (Remote Desktop Protocol) for target selection. Upon locating exposed RDP services, the attackers will then proceed to access the exposed hosts (via brute force, stolen credentials, etc.) and drop and execute the CrySiS malware.
Over the last year, there have been multiple decryption tools released to remediate CrySiS-infected files. However, none of these tools are universal.
Standard recommendations for preventing or dealing with this threat (and others) include:
- Keep AV/Endpoint protection up-to-date and configured properly.
- Ensure that you have valid and functional backups.
- Never pay the ransom. There is no way to guarantee that payments will result in decrypted data/files.
- Protect exposed RDP services (2FA, etc.) and disable the service where it is not needed.
Having said that, Cylance protects against the CrySiS ransomware by fully preventing execution. We also encourage everyone to monitor for updates on this ransomware family (and others) through NoMoreRansom.org, which Cylance participates in and contributes to. Stay safe!
Shady Tradey Mining Shenanigans
Criminals are continuing to embrace any method possible to squeezing profit out of their malware campaigns. Over the last several years, rogue Android apps have become a favorite go-to for just this type of activity.

At least two rogue “trading” apps were recently discovered on the Google Play store. All the malicious apps were disguised as mobile trading apps from leading currency exchange Poloniex.
One interesting aspect of these rogue apps is their attempt to mimic (and therefore trick) the user into thinking they are using two-factor authentication (2FA) after installing and opening the app.
When executed, the user is prompted for both their Poloniex and Google account credentials. Once full access to the user’s data is achieved, the apps can proceed to execute fraudulent transactions (trades, etc.) using the harvested credentials.
Protecting yourself against these apps (given the vast volume of malicious apps in the wild) can be tricky. Some standard ways to reduce harm include:
- Enable true 2FA for your legitimate Poloniex account (and others where available).
- Be wary of untrusted apps requesting access to your Google or other third-party accounts. Reduce this wherever possible.
- Attempt to logically avoid illegitimate apps. Look for “red flags” like non-proportional rations of downloads to reviews, oddly worded reviews that repeat, working links to the developer’s site from the Google Play store, and enable/utilize Google’s “Play Protect” feature.
Rogue Poloniex IOCs:
306a4fd41ce67784db399eced6531ac629bd9fe05d3347665bb935f1100e37f2
c5112e3a95bfa226bc2d524964364c61e0db9fe2824c20ca99521ab15367d678

