Scarab ransomware is distributed to targets through phishing emails being served by the Necurs botnet. The malicious code arrives disguised as a scanned image or
VIDEO: Watch Cylance go head-to-head with Scarab ransomware:
VIDEO: Cylance vs. Scarab Ransomware
Scarab Burrows In
Within the attachment lies a VBS downloader which is used to download the ransomware payload.
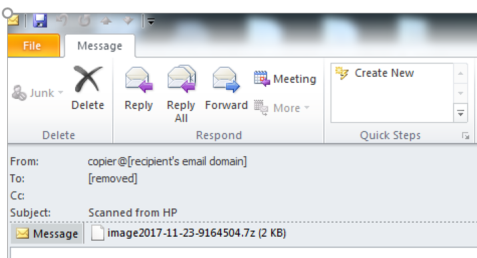
Figure 1
Scarab nests in the system registry where it hides from traditional security software. It launches a Microsoft HTA application which then executes a script that hooks Scarab into the following Windows registry key:
HKEY\LOCAL_MACHINE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
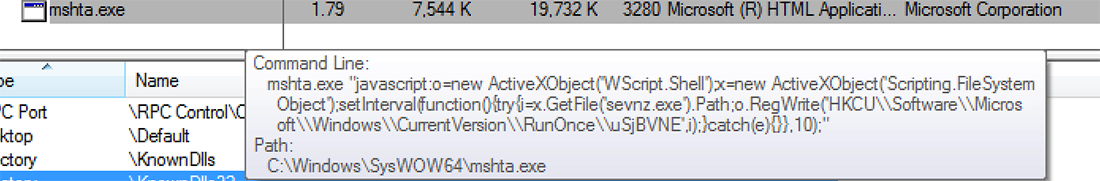
Figure 2: mshta.exe executes a script that hooks Scarab into HKEY\LOCAL_MACHINE\MICROSOFT\WINDOWS\CURRENTVERSION\RUNONCE
The Obfuscation
After hooking itself into the Windows registry, Scarab calls another script to erase its tracks. It uses the same trick, launching a Microsoft HTA application which executes the script:
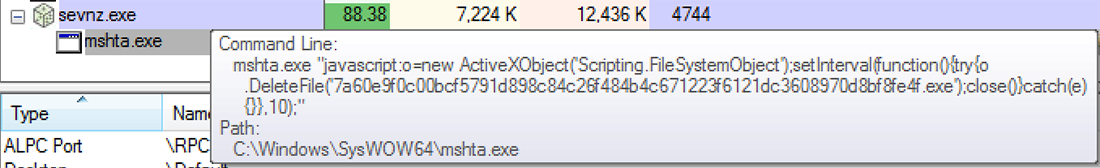
Figure 3: One simple call to DeleteFile and this culprit will be well hidden in your infrastructure
The Shakedown
Once embedded in your system, Scarab goes on the offensive. It crawls through the target system encrypting personal files and appending them with support(at)
The following ransom note displays once the files are hostage:
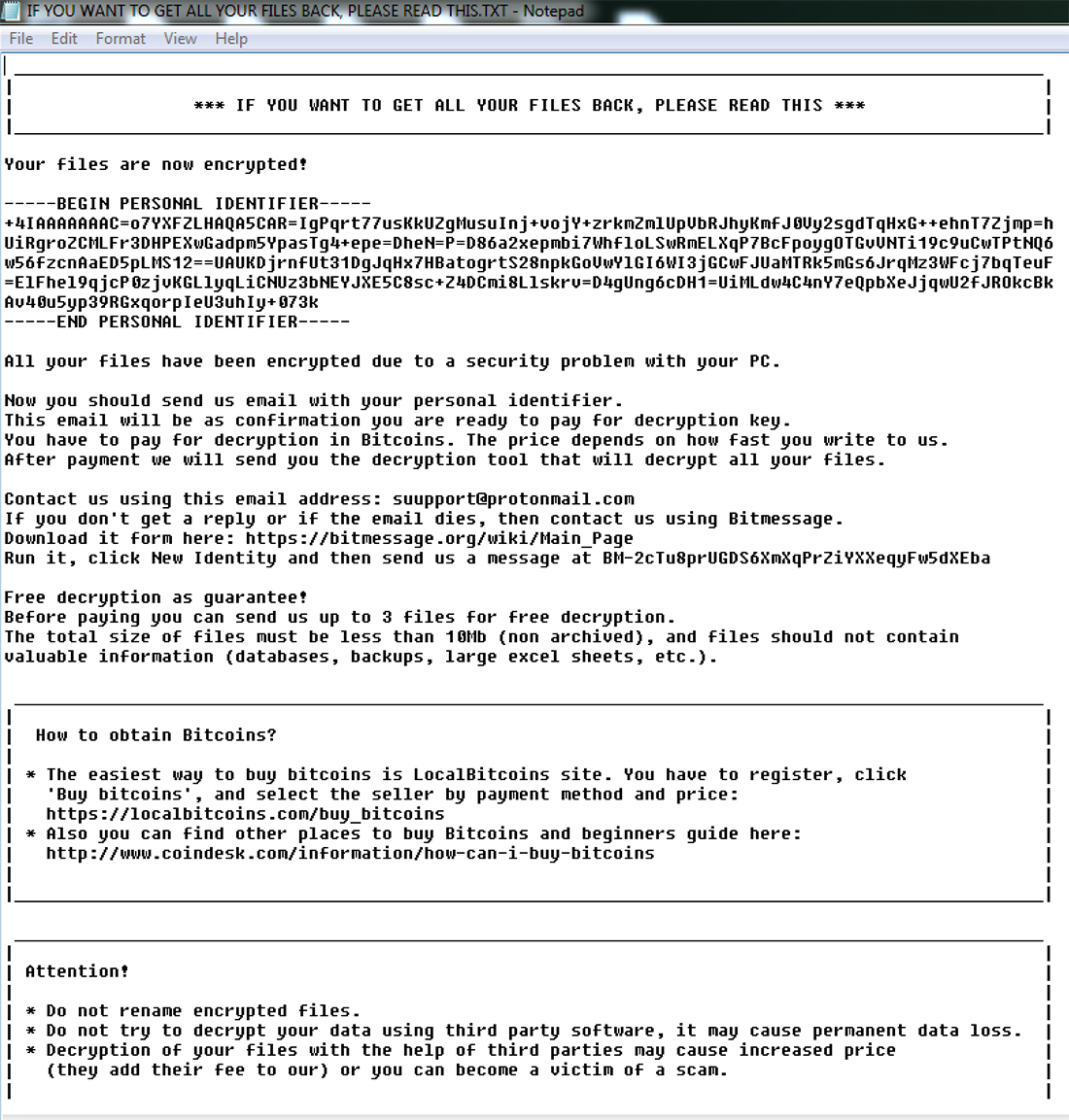
Figure 4: If you see this note, SCARAB has won.
CylancePROTECT® Prevails
With Script Control enabled, CylancePROTECT prevents the VBS downloader Script from downloading the payload, as seen below:

Figure 5: Scarab never had a chance against CylancePROTECT.
Even without Script Control enabled, the payload - should it find its way into the environment - is quarantined prior to execution:

Figure 6
Indicators of Compromise (IOCs)
SHA256 Hashes:
VBS Script
C7E3C4BAD00C92A1956B6D98AAE0423170DE060D2E15C175001AAEAF76722A52
Payload:
7A60E9F0C00BCF5791D898C84C26F484B4C671223F6121DC3608970D8BF8FE4F
Filenames:
sevnz.exe
Malware Harvesting Websites:
[miamirecyclecenters].[com]/JHgd476
[hellonwheelsthemovie].[com]/JHgd476
[hard-grooves].[com]/JHgd476?

