This will be the first of two fun “Dark Web” bits for this week’s blog. And… it’s a doozie.
We are, hopefully by now, all aware of the various security issues that the myriad of internet of things (IoT) devices present. Not the least of which is the exposure of them via default credentials (unchanged from factory default… which are widely known and publicized)… or they are changed but to painfully easy-to-guess combos (Hello:hello, router:router, etc.).
The site we’re going to be looking at today has been up since approximately January 5th, 2018. It’s not the first of it’s kind, but this particular one is continually updated and represents devices all around the globe of all types and varieties. The credentials are still valid, and the site is (as of this writing) still up.
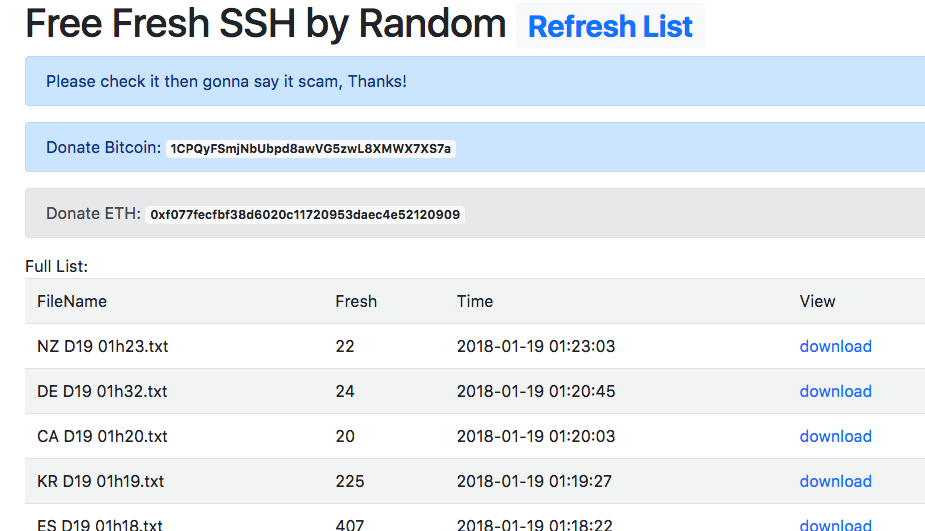
Figure 1
This site is hosting TXT files containing device addresses, creds, location (country) along with a “speed” rating (1-10). While the site is aimed at using these credentials via SSH, for most of these devices, HTTP is open and responding to the same default credentials as well.
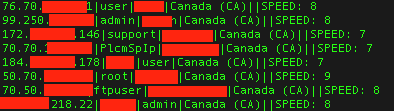
Figure 2
The devices (manufacturer and model) vary widely. If you can think of a router/AP/VoIP Gateway/Repeater/etc., then they are represented on these lists.
A quick scan of one list shows the following devices represented (this is just a random sample, there are many many more)
- Silver Peak Appliance Management Console
- TP-Link EAP120 (AP)
- TP‑LINK Archer C5400 Routers
- TP‑LINK Archer C5400 Routers
- TP‑LINK Archer C5400 Routers
- TP‑LINK Archer C5400 Routers
- TP‑LINK Archer C5400 Routers
- TP‑LINK Archer C5400 Routers
- TP‑LINK Archer C5400 Routers
- TP-Link (Range Extenders) – various models
- Trendnet N300 PoE Access Point (TEW-755AP)
- ZyXEL FSG1100HN Fiber Gateways
- ZyXEL FMG3025-D10A Fiber VoIP IADs
- ZyXEL AMG1312-T10B Wireless N ADSL2+ Gateways
- Huawei EchoLife ONT (Optical Network Terminals) - various models
- Ubiquiti Airmax – Various models
- Buffalo LinkStation NAS – various models
- YooBackup Portals/platforms
- GreenPacket – Various devices
- Parks Digital Modems (various)
- Everything running BusyBox ever
- D-Link DWR-730 Portable HSPA+ Mobile Routers
- SmartNA TAPs – various
- MikroTik Routers – various
- Lantronix devices (various)
Again, this list is by no means complete. There are thousands of hosts listed representing every device you can think of. This sort of ‘service’ is a little more alarming than something like Shodan, in that it removes a few steps to obtaining the ‘valuable’ info… and… it’s free.
Bottom line: always, always, always change default credentials on ANY device you connect to ANY network. In the age of Mirai, Okiru and the like you can never be too careful. All devices are potentially vulnerable, even if only as a beachhead or jumping point to other devices and things. Change your credentials immediately and often, and keep the SSH*ty bad guys out!
A Trust Meltdown: The Timely Tale of Social Engineering Lures
The German Federal Office for Information Security recently alerted on malicious emails which capitalize on the need to patch against the Meltdown and Spector vulnerabilities. This serves as a great reminder on just how rapidly the bad guys react and turn the well-meaning public’s good intentions against them.
With the flurry of detail surrounding these vulnerabilities (some more confusing than others) it is hard enough to figure out ‘what to do’ for some without having to worry about the alerts and patches themselves being malicious.
Having said that, we see this time and time again. Any major event, be it a national tragedy, major security event, celebrity death/scandal, etc. is very quickly turned into a lure.
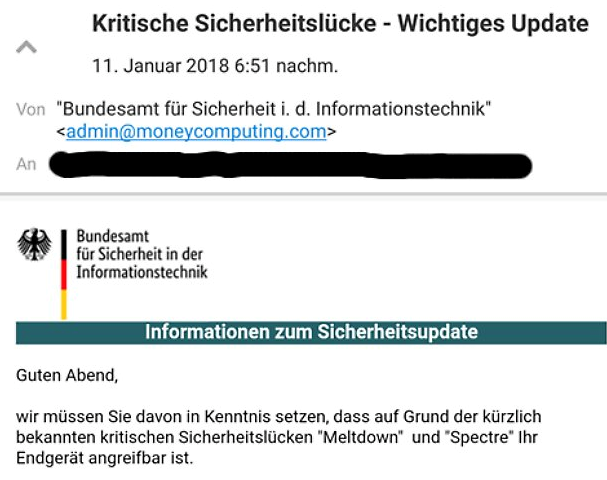
Figure 3 (Image courtesy of BSIFB)
The malicious email directs users to download a fake/malicious patch. The delivered executable (during the campaign) was the following:
Intel-AMD-SecurityPatch-10-1-v1.exe / dsfgsdfgsdfg.exe
SHA 256: cd17ce11df9de507af025ef46398cfdcb99d3904b2b5718bff2dc0b01aeae38c
This Smoke Loader variant is designed to extract and transmit sensitive information from infected hosts. The following callback domain was identified upon analyzing this sample:
service-consultingavarage[dot]ru
localprivat-support[dot]ru
coolwater-ltd-supportid[dot]ru
The following binary has also been observed interacting with the hosts above:
76526155b16e355a6794e2656aedad50bfeb199edf64bdd0dcea7e16e13bedc5
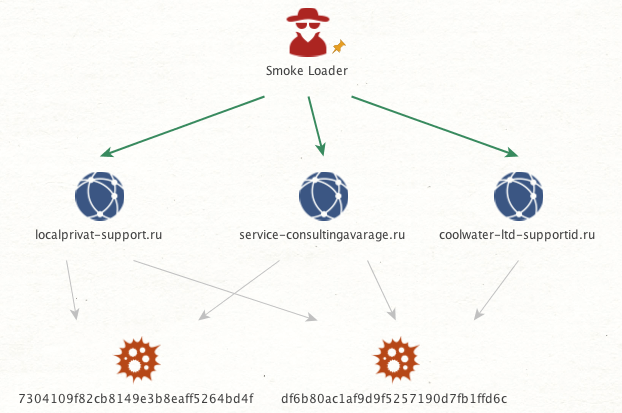
Figure 4
The quick lesson here is always stop and think before you open and click. Spam and email-borne threats still work for a reason. Humans are all too eager (usually) to open and click stuff. That’s what the bad guys count on. Strong and preventative technological controls can help (CylancePROTECT® does stop the associated malware here). But stopping yourself from interacting manually from malicious emails will go a long way to preventing the headaches of an infection.
Shiftr RaaS Returns – Another Ransomware As A Service (RaaS) Resurrection
In Mid-2017, a new RaaS portal appeared on the ‘Dark Web’ (this is the second of the two fun dark web stories we hinted at earlier). The portal was dead-simple and the executables that were generated were bloated, GO-based binaries.
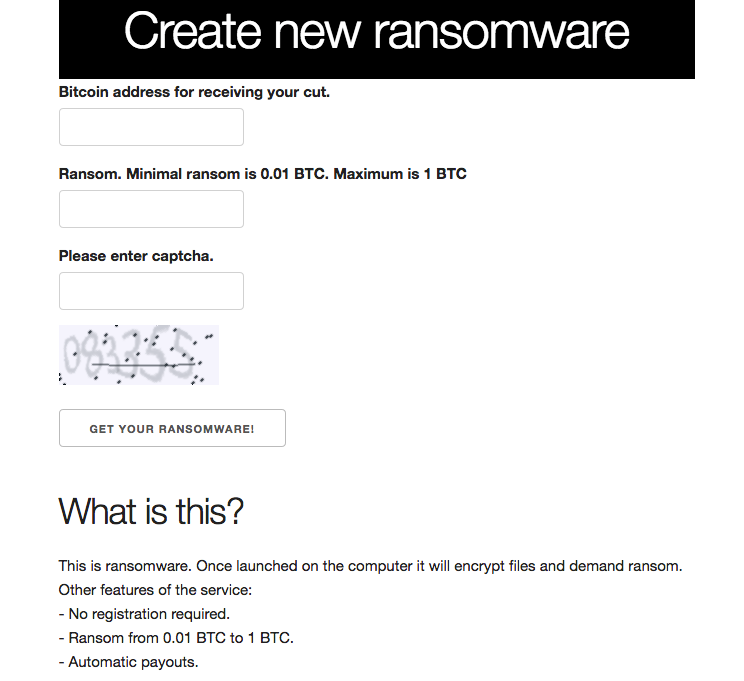
Figure 5
The latest incarnation on this RaaS portal went live on January 6, 2018. Just about everything this the same in terms of functionality and the economic model. According to the site, they take 10% and the ‘customer’ gets 90% of the take. There is a maximum limit of 1 BTC for ransom charged. One noticeable change, this time around, is the extension used upon encryption. This variant uses a “.cypher” extension, and is otherwise similar to previous incarnations of this family.
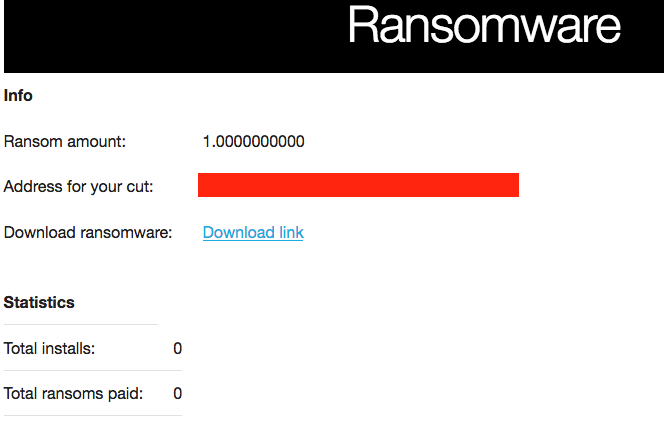
Figure 6
There are many aspects that make this portal appear to be unfinished or a work-in-progress. For one, the instructional pages for decryption do not appear to work as desired. Also, the usual contact details for “help” are just example_at_example.com. At any rate the binaries do work, again illustrating just how simple it is for anyone to generate their own ransomware and possibly wreak some havoc. (CylancePROTECT does detect/prevent the binaries generated by this portal.)
Beyond the use of strong endpoint protection technology, users should continue to follow the consensual guidelines to stave off these attacks. NEVER pay the ransom and create and maintain strong, available, and tested backups of your data. Backups that you can’t get to, or fail to restore don’t help in your time of need. Test your backups and drill your business continuity plans regularly to ensure that you can recover when it matters most.
About the Cylance Research and Intelligence Team
The Cylance Research and Intelligence team explores the boundaries of the information security field identifying emerging threats and remaining at the fore front of attacks. With insights gained from these endeavors, Cylance stays ahead of the threats.
References:
(1) https://www.bsi-fuer-buerger.de/BSIFB/DE/Service/Aktuell/Informationen/Artikel/Vorsicht_gefaelschte_BSI_Webseite_11012018.html
(2) https://meltdownattack.com/
(3) Image used in Figure 3 courtesy of BSIFB

