Business Email Compromise (BEC) is a global problem. This week, a significant step forward in tackling this issue was made by federal authorities, who disclosed yesterday that they had been working with partner agencies around the world to dismantle a number of large-scale BEC schemes.
Operation Wire Wire was a joint effort between the FBI, the Department of Homeland security, the Department of the Treasury and the US Postal Inspection service. The operation took the form of a six month sweep that culminated in 74 arrests both in the U.S. and overseas, including 51 domestic arrests and many in Nigeria, Mauritius and Poland.
Incredibly, the operation recovered around $14 million in fraudulent wire transfers. $2.4 million in undisclosed currency was also seized as a result of the sweep.
Both small, medium and large-sized businesses had been defrauded by the international criminal organizations involved in these schemes. Individual citizens were also targeted, including real estate purchasers, law firms, the elderly (who are often targeted for their retirement bank accounts containing life savings), and many others who had “transferred high dollar amounts or sensitive records in the course of business.”
Business Email Compromise: A Global Problem
The Internet Crime Complaint Center (IC3) stated in its latest Internet Crime Report that in 2017 alone, the IC3 received 310,580 total Internet crime complaints, with reported losses totaling $1.4 billion. The Internet crime with the highest reported losses was BEC, of which the IC3 received only 15,690 complaints, yet the adjusted losses resulting from those complaints were over $675 million – comprising almost 50 percent of total Internet-crime-related financial losses for 2017 (see table below).
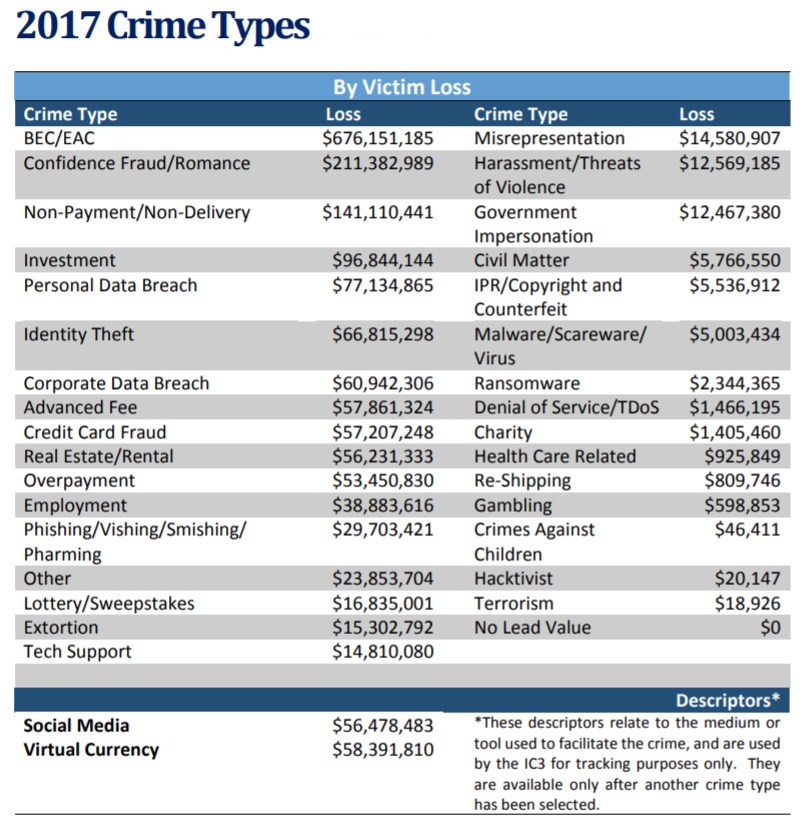
Source: Internet Crime Complaint Center (IC3) 2017 annual report
Also known as “cyber-enabled financial fraud,” BEC is a sophisticated type of scam mainly targeting the employees of businesses who often work with foreign suppliers and regularly perform wire transfer payments. The goal of a BEC scam is to trick employees who have access to corporate finances into making wire transfers to fake accounts. Check fraud is also frequently involved, as is the use of Email Account Compromise (EAC).
The report notes that “the devastating impacts these cases have on victims and victim companies affect not only the individual business but also the global economy.” According to the report:
“The fraudsters use(d) the method most commonly associated with their victims’ normal business practices. Both scams typically involve one or more fraudsters, who compromise legitimate business email accounts through social engineering or computer intrusion techniques to conduct unauthorized transfers of funds.”
The report also cautions that both BEC and EAC scams are becoming more and more sophisticated. Examples of BEC include the following scenarios:
- The email accounts of high-ranking executives such as CEOs or CFOs are hacked or spoofed by cybercriminals. Fraudulent emails are then sent from hacked/ spoofed accounts to employees, instructing them to wire payments to fake ‘customer’ accounts.
- Employee work accounts are hacked or compromised and funds from legitimate business deals are intercepted or re-routed to the criminal’s account, or that of a money mule.
- Fraudulent requests for payments may also be sent from compromised employee email accounts to vendors or clients identified from employee’s contact lists.
- Fraudulent requests for Personally Identifiable Information (Pii) or Wage and Tax (W2) statements may be sent to employees or financial/ HR team members.
- Cybercriminals posing as lawyers or law firms may contact employees instructing them to make time sensitive wire transfers.
How to Avoid Becoming a Victim of BEC/EAC Schemes
BEC and EAC scams may take many forms and there is no ‘one size fits all’ method of avoiding them. They exploit the weakest link in the security chain – the human element – and as scams grow ever more sophisticated, even the most security conscious among us is not completely immune to being fooled one hundred percent of the time.
From a business point of view, employee education and security awareness training is key in reducing this kind of risk. There are also many technological steps your IT team can take to reduce your company’s chance of becoming a victim. A few are outlined below:
Email Security Tips for IT Teams
- Create intrusion detection systems that automatically red-flag and report emails sent from email addresses similar to your company name. For example, if you work at ABC.com, your email system should flag emails sent from ACB.com, A_BC.com or ADC.com.
- Set up an email rule that will flag and report emails that have a different “Reply To” address from the “Sent From” address.
- Create an email rule where emails sent internally are automatically color-coded one color (E.G.: green) and emails from external accounts are a different color (E.G.: red).
- Add 2-Factor Authentication (2FA) to systems which handle and store vendor payments.
- Secondary authentication by a manager should be required by default when there is a change in vendor payment address or phone number, or a transfer request that exceeds a pre-determined limit.
- Consider implementing 2FA login for all corporate email accounts and payment systems.
- Frequently review and validate client and server mail “rules” ensuring that no rogue rules are created, or that no unauthorized rules are created leading to undesirable or unexpected behavior.
Email Security Tips for Employees
- Follow the “Read Twice; Send Once” rule: all email requests for large or unexpected financial transfers should be carefully scrutinized for signs that anything looks out of place.
Check the sender’s email address with the utmost care:
- In OUTLOOK, right-click the email address and choose “Open Contact Card.” Does the Contact Card address match the display address on the main email?
- Is the company name in the second half of the email address spelled correctly? An ‘accidental’ typo in the company name part of the email address is a common technique used by fraudsters to make their email appear to come from a legitimate company. For example: “name@capitalone.com” may be misspelled as “name@capitolone.com.”
- Fill out wire transfer forms by directly copying only information already present in your company’s system; train yourself to never copy-paste any information provided in the transfer request email. Fraudsters like to count on people taking the easy path and they’ll try to spoon-feed you incorrect information. They may also provide clickable ‘autofill’ links that may download malware or spyware.
- If in doubt about the authenticity of an email requesting money or information, do not be afraid to directly call the parties involved in the transfer to verify their identity or the validity of the request. A minor inconvenience now is better than a major embarrassment later.
- If you work in any department that handles money, be careful about posting details of your job duties to publicly viewable online forums such as LinkedIn. You may inadvertently make yourself into a high value target for attackers.
- Immediately report (as spam) and delete unsolicited email from unknown parties. Do not open them and never click on any links or download any attachments they contain, even if they appear to be from a company with which you do business. Ditto for social media messages sent to your private or corporate account.
- Be suspicious if an employee of a client/vendor company unexpectedly contacts you from a private email account, or messages you on social media (for example claiming to be on vacation and unable to access their company email). Always request politely that all business conversations take place via corporate email.
- If someone requesting an unusual wire transfer tells you to call them as verification of their identity, don’t call the number they give you. Instead, call the company directly and ask to be transferred to the correct party.
How to Report BEC Fraud
This week’s announcement from the FBI regarding Operation Wire Wire “demonstrates the FBI's commitment to disrupt and dismantle criminal enterprises that target American citizens and their businesses,” according to FBI Director Christopher Wray.
He adds, “We will continue to work together with our law enforcement partners around the world to end these fraud schemes and protect the hard-earned assets of our citizens. The public we serve deserves nothing less.”
If you’re reading this because you suspect you’ve been a victim of BEC fraud, it is important to act fast. See IC3’s tip sheet here for detailed instruction on practical steps you can take to limit damage.
If you’d like to officially report a BEC scheme that has affected you or your company, you can file a complaint with the IC3 here.

