When three outlaws appear on the horizon, with horses and weapons outlined in the crimson sunset, it's usually time to get out of Dodge. At the Cylance research lab it’s merely time to round up the bandits and dismantle them down to their machine code. This week, Cylance investigates three unique malware variants found travelling together. The members of this dubious malware triad include:
- A deceptive document loaded with malicious macros
- Smoke Loader, a popular malware downloader
- Trickbot, an information stealing banking Trojan
Can this rag-tag malware gang prove more effective than the infamous solo threats which dominated headlines in 2017? Our research team answers this and other questions in our triple threat breakdown.
VIDEO: Cylance vs. Smoke Loader Triple Threat
Smoke Loader Analyzed
Cylance Threat Research describes the three malware components in greater detail within this week’s Threat Spotlight blog.
Document File
The attack begins with an attachment posing as an invoice from a legitimate private company. When the file is opened the reader is presented with a document containing the following image:
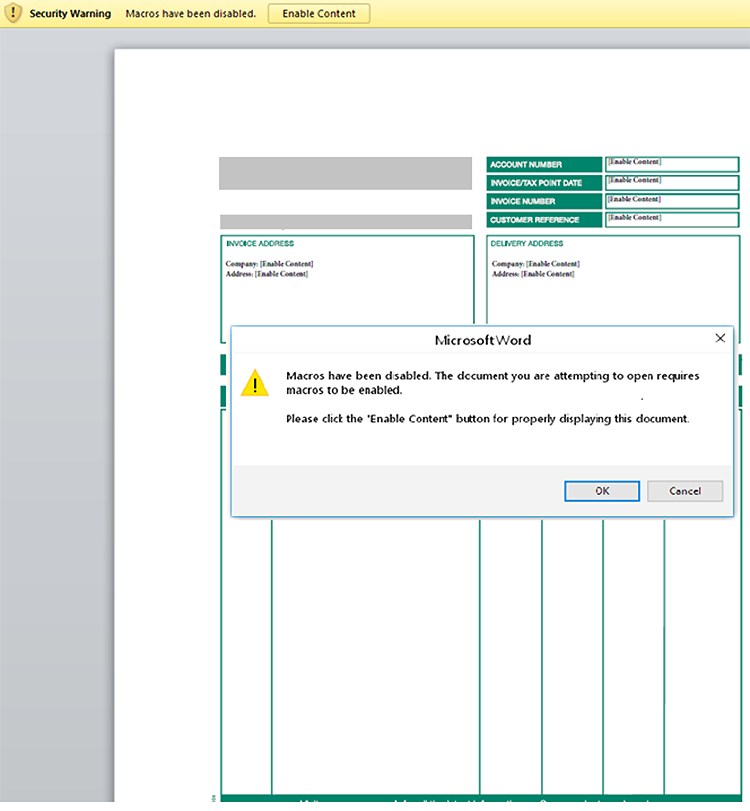
Figure 1: Malicious document prompts user to enable macros, allowing it to begin operations
A savvy observer will notice both the invoice and the warning are a picture pasted within the document. The MS Word warning is not actually triggered when the file is opened. Less observant users may be fooled into enabling macros by the fake warning, a move that brings dire consequences.
The document hides sixteen separate, malicious macros:
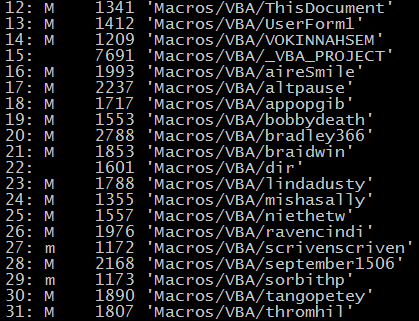
These macros invoke various PowerShell instructions, including one which saves a randomly named .BAT file in the %temp% folder. Successful execution of the macros and PowerShell instructions results in Smoke Loader malware being dropped on the target system.
Smoke Loader
Smoke Loader attempts to load all plugin DLLs present on the local disk:
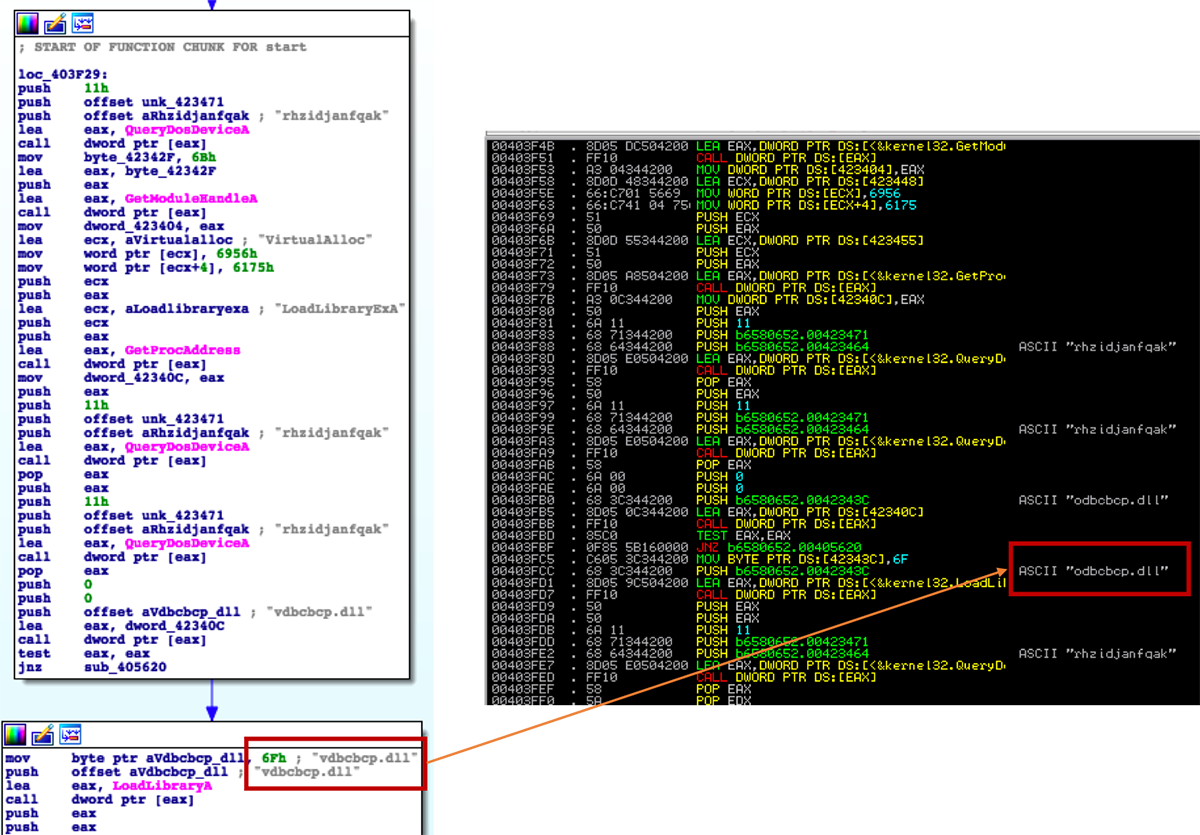
Figure 2: Smoke Loader on a DLL running rampage
Smoke Loader also uses GetShellWindow->GetWindowThreadProcessId->NtOpenProcess to inject itself into processes and propagate. If successful, Smoke Loader will remain undetectable to common iteration processes:
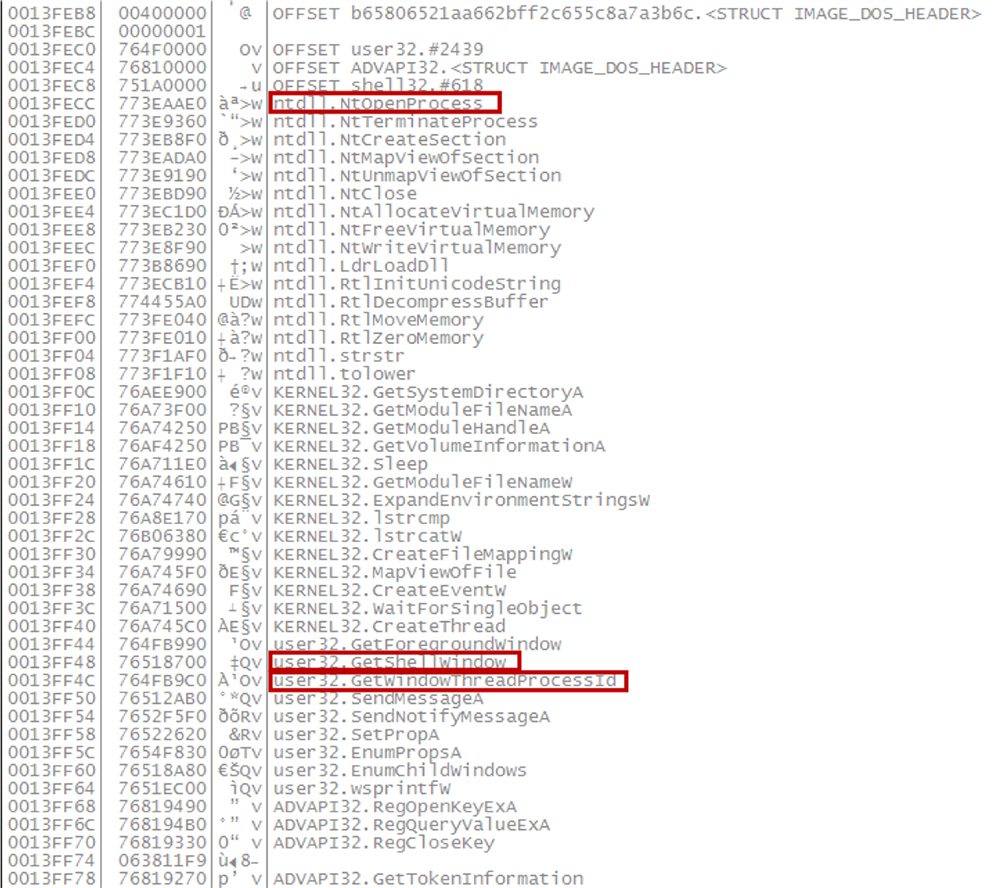
Fig 3: Smoke Loader will remain undetectable to common iteration processes
Smoke Loader can download many kinds of malware. In our tests it chose the banking Trojan, Trickbot.
Striking Similarities
Although Smoke Loader and Trickbot perform separate functions, we were able to learn some information from their similarities. In this case both files shared the same structure:
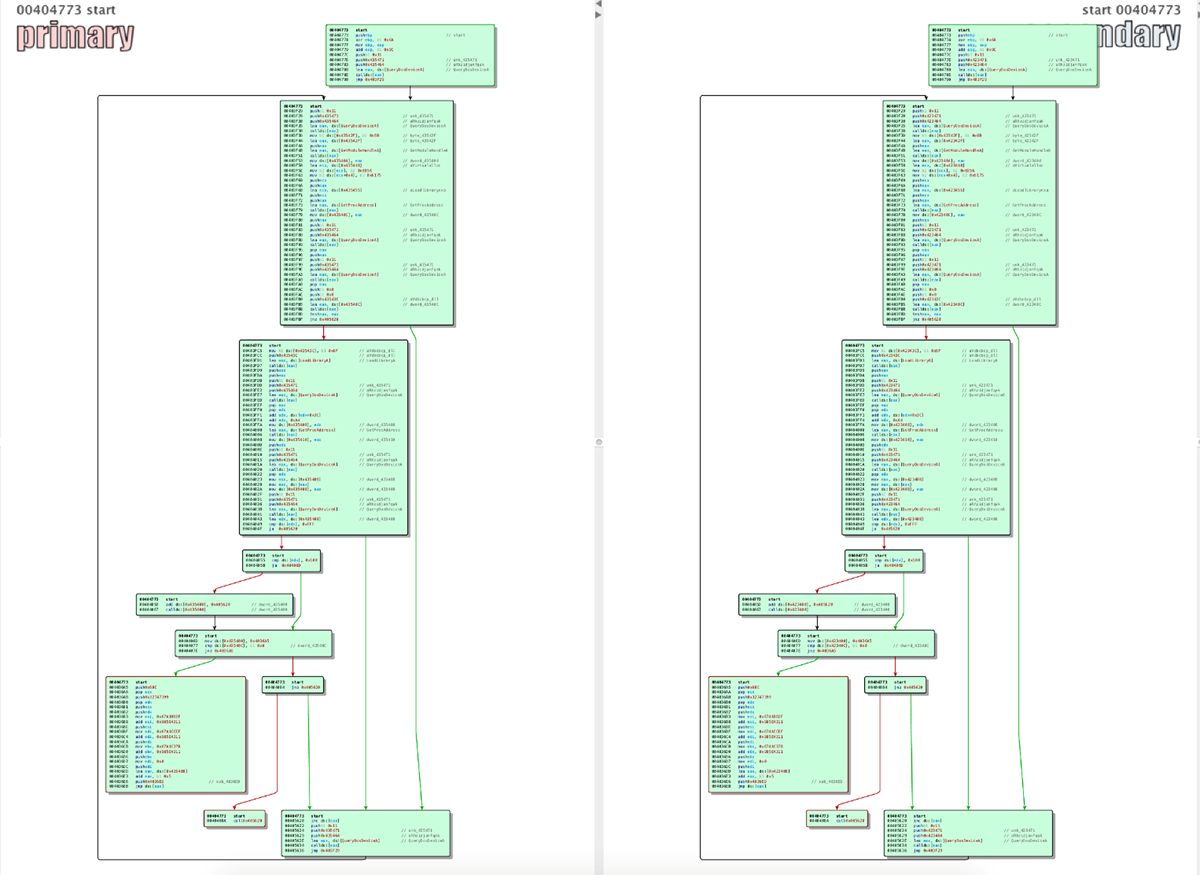
Figure 4: Smoke Loader and Trickbot, twin threats with identical structures - what does it mean?
Further investigation revealed the twin file structures are a result of both threats undergoing the same encryption method.
Trickbot
When executed, Trickbot attempts to inject itself into the taskeng.exe process:

Figure 5: Trickbot injecting into taskeng.exe
It also copies itself into the %Roaming%\NetDefender folder:
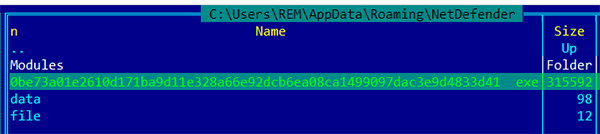
Fig 6: Trickbot copying itself into the %Roaming%\NetDefender folder
Trickbot attempts to establish communication with nearly two dozen command and control (C2) servers. During testing it was only successful in reaching one - 185[.]174[.]174[.]72:
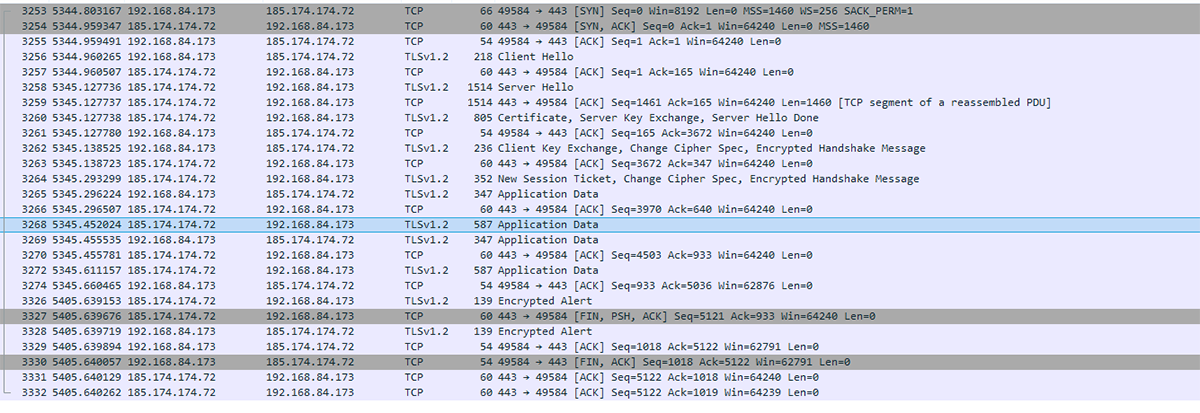
Figure 7: Trickbot reaches out to multiple C2 servers
Trickbot sends any sensitive information it has discovered (usually banking credentials) to the C2 once a connection is established:
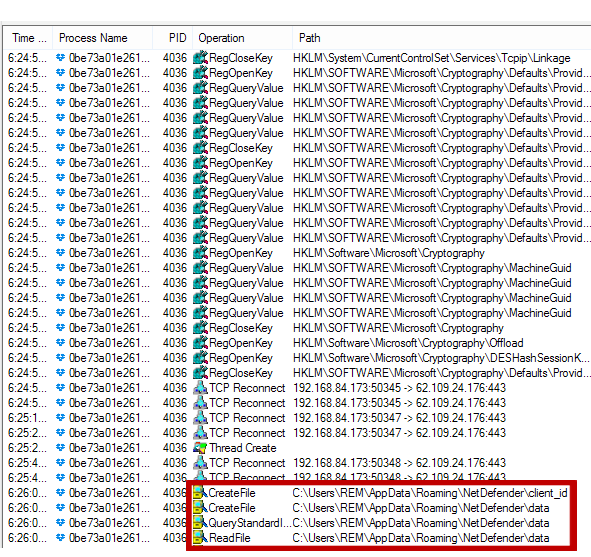
Figure 8: Trickbot preps data for exfiltration
Why is Smoke Loader Important and Why Should I Be Concerned?
Smoke Loader is engineered to drop additional malware on a host system. As such, there is no limit (within the realm of malware) to the ills it can visit upon an organization’s infrastructure. It is a modular malware, meaning it can receive new execution instructions from C2 servers and download additional modules for expanded functionality.
Despite being first identified in 2011, Smoke Loader is actively used by modern threat groups. Any malware still providing returns seven years after its first appearance should concern us all.
Cylance Stops Smoke Loader (and Trickbot, and Malicious Documents)
This dangerous combination of threats highlights the critical role of predictive security solutions like CylancePROTECT®. Building new defenses on top of old ones, an approach used by traditional security solutions, is entering an arms race one cannot win.
Each new layer of cyber defense slows overall system performance. When new threats emerge, new layers are added. After a few iterations of this process system hardware is overburdened while the appearance of new threats continues unimpeded.
Lightweight, AI-driven solutions like CylancePROTECT train mathematical models on hundreds of millions of files to identify threats at the DNA level. The ability to profile, predict, and prevent threats without relying on unique file signatures means Cylance handles three threats as easily as one.
Cylance identifies and stops malicious code before it executes. This allows Cylance to protect your business from known, unknown, new, and zero-day threats, whether they travel alone or in packs.

