Cylance vs. Emotet Updated
Background
There’s an adage involving pigs and lipstick that is often quoted when something emerges from an unsuccessful makeover. Emotet, a malware we profiled in December 2017, is back with some brand new tricks. However, it takes more than a few code tweaks (or lipstick) to fool an AI engine trained on more than a million file threat features. Our threat research team recently dismantled an updated version of Emotet to examine some changes to its operations.
Updated Emotet Analyzed
Updated Emotet relies on the same delivery mechanism as before: a Microsoft Word file embedded with malicious macros.
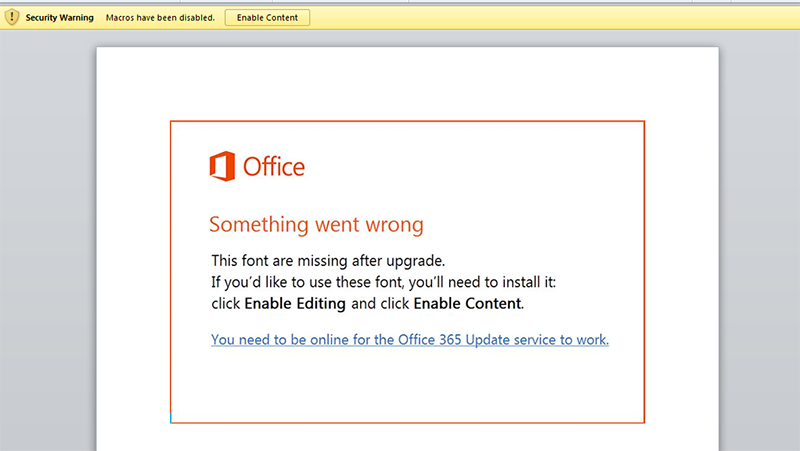
Fig 1: Document seeks to trick user into enabling macros.
These malicious macros are more heavily obfuscated than previous versions of Emotet:
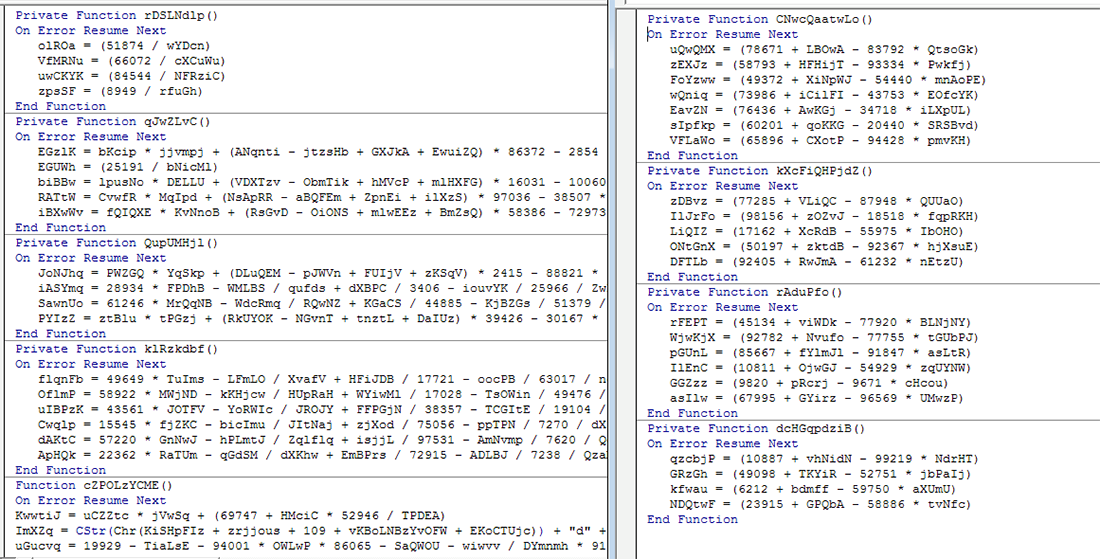
Fig 2: Obfuscated macros.
The obfuscated macros were not beyond the grasp of our threat researchers, who translated the jumbled commands into this code:

These PowerShell commands download the malware payload from one of the specified websites.
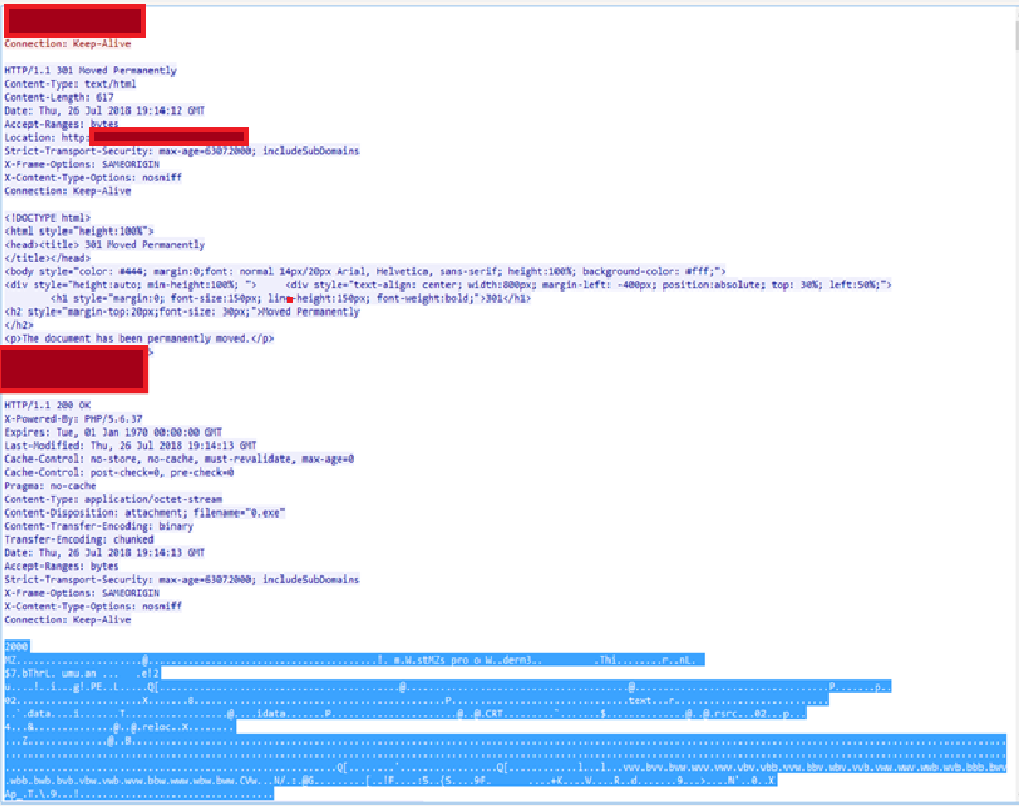
Fig 3: Emotet payload is downloaded from site.
The malware saves a file named 535.exe to the %temp% folder, then executes:
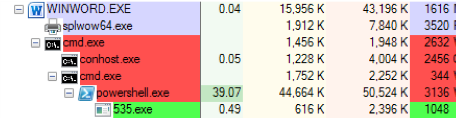
Fig 4: PowerShell executes the 535.exe payload, both are running.
Once Emotet is active it copies itself to the %local%\Microsoft\Windows\ folder as a file named cimmontana.exe and implements its persistence mechanisms.

Fig 5: Emotet embedding itself in the registry.
Updated Emotet is also configured with a wider array of options for establishing connection with C2 servers:
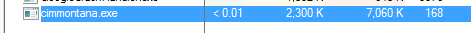
Fig 6: Emotet looks for C2 servers.
Cylance (Still) Blocks Emotet
Cylance AI is trained to identify threats based on more than a million file threat features. Our security agents identify and prevent threats based upon technical DNA. In fact, we identified and blocked this new variant of Emotet with a version of the Cylance AI engine built in 2016.
This means Cylance-trained AI has been able to detect and prevent the latest version of Emotet for more than two years, without an update.