Cylance vs. Nemucod Trojan Downloader
Nemucod, a Trojan downloader, has been terrorizing users since December 2015. The Nemucod variant examined by our Threat Research team is delivered through malicious email (malspam) campaigns. Targets receive an email containing a Zip archive (.zip) attachment, which appears to come from a trustworthy sender.
When extracted, the archive contains a malicious JavaScript (.js) file. Double-clicking the JavaScript will cause it to execute in either the default browser or through Windows WScript. Once executed, the script downloads a payload containing another malicious file onto the system. The payload is often a popular version of ransomware such as TeslaCrypt or Locky.
Attack Chain Analysis
In the context of an overall attack chain, Nemucod plays a limited, but critical, role in the overall compromise of a system or environment. As a malware dropper, it is a purpose-built piece of code with a singular objective: to execute a payload without being detected. The payload is interchangeable, making droppers a prime candidate for re-use across multiple malware campaigns or even groups of actors. In the vast majority of cases, a dropper like Nemucod is used conjunction with a user-driven Initial Access technique (e.g. file attachment, download link). The complexity of droppers comes from the obfuscation introduced to stymie static analysis of the code and may include logic to restrict the conditions that the dropper will execute to make dynamic analysis more difficult.
The techniques demonstrated in Nemucod are well-known, effective, and are still in use today. Given the damage caused by the types of malware Nemucod is commonly used to deliver, the message is clear: Breaking the attack chain as early as possible is key. Stop the dropper, stop the infection.
Nemucod Maslpam Campaigns
The following is a brief timeline of Nemucod malspam campaigns:

Nemucod Analyzed
The Nemucod attack typically starts with a malicious zip archive file attached to an email. In one case, an email came from a French address on March 28, 2016 at 16:54. The message read:
Votre message est prêt à être envoyé avec les fichiers ou liens joints suivants:
9758W-TERREDOC-RS62937-15000
Message de sécurité
In English, this roughly translates to:
Your message is ready to send with the following files or links joined:
9758W-TERREDOC-RS62937-15000
Security message
Attached to the email is a file called 9758W-TERREDOC-RS62937-15000.zip (known in the wild as 9758W-TERREDOC-RS62937-15000-1.zip). When the target downloads and extracts the attachment, they find a small JavaScript file inside called QQN9875461601.js (Figure 1).
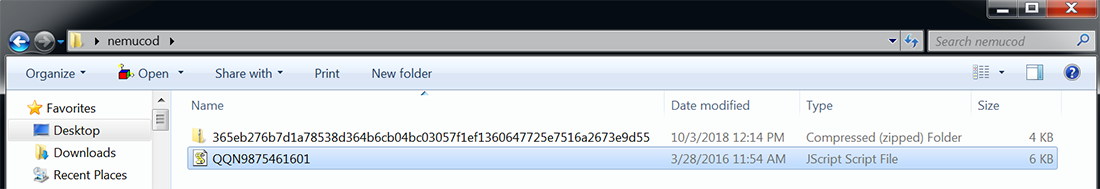
Figure 1: Extracted Zip archive containing the malicious Downloader script
A high-level view of this JavaScript reveals an unconventional coding style. The function and variable names are obfuscated with random sets of characters (Figure 2).
Figure 2: Obfuscated JavaScript
Line 53 contains obfuscated code which pieces together a URL for downloading an executable file called 765f46vb.exe (Figure 3).
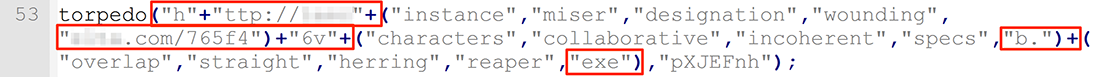
Figure 3: Building the download URL
When the end user double-clicks the JavaScript file the malware sends a connection request to a compromised website hosted at 185.81.2.81. A request for the 765f46vb.exe file follows (Figures 4 and 5). This website no longer hosts the file, forcing a redirection (Figure 4).
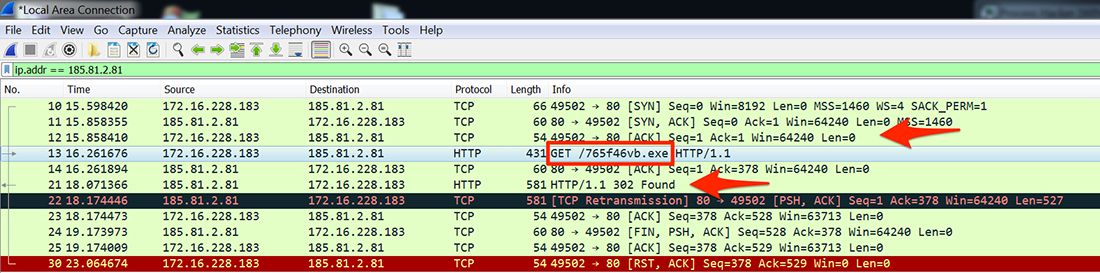
Figure 4: Connecting to 185.81.2.81 and being redirected
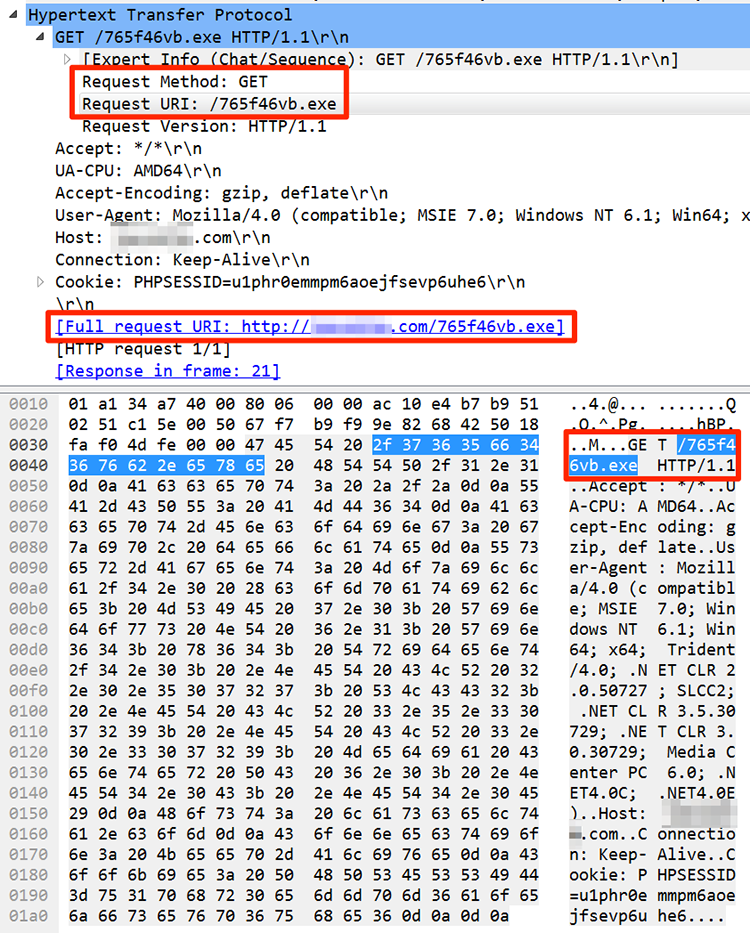
Figure 5: Full packet capture request for 765f46vb.exe
A search for the payload on VirusTotal reveals two hashes. Our test case uses the 697CE53503DC8F28B6F9603563181F33D7EF840E8993313D15D5DC4914BFDB31 payload. Further analysis demonstrates various configurations of the version and the Command & Control (C2) servers (Figure 6).

Figure 6: Hard-coded IP addresses for the Locky C2 servers
This payload is one of the earliest identified versions of Locky, dating back to February 2016. While new versions of Locky create various extensions during encryption, this version appends .locky to the target files. Once all important files are encrypted, a ransom note, similar to the following, is displayed in the default browser and as an image on screen (Figure 7).
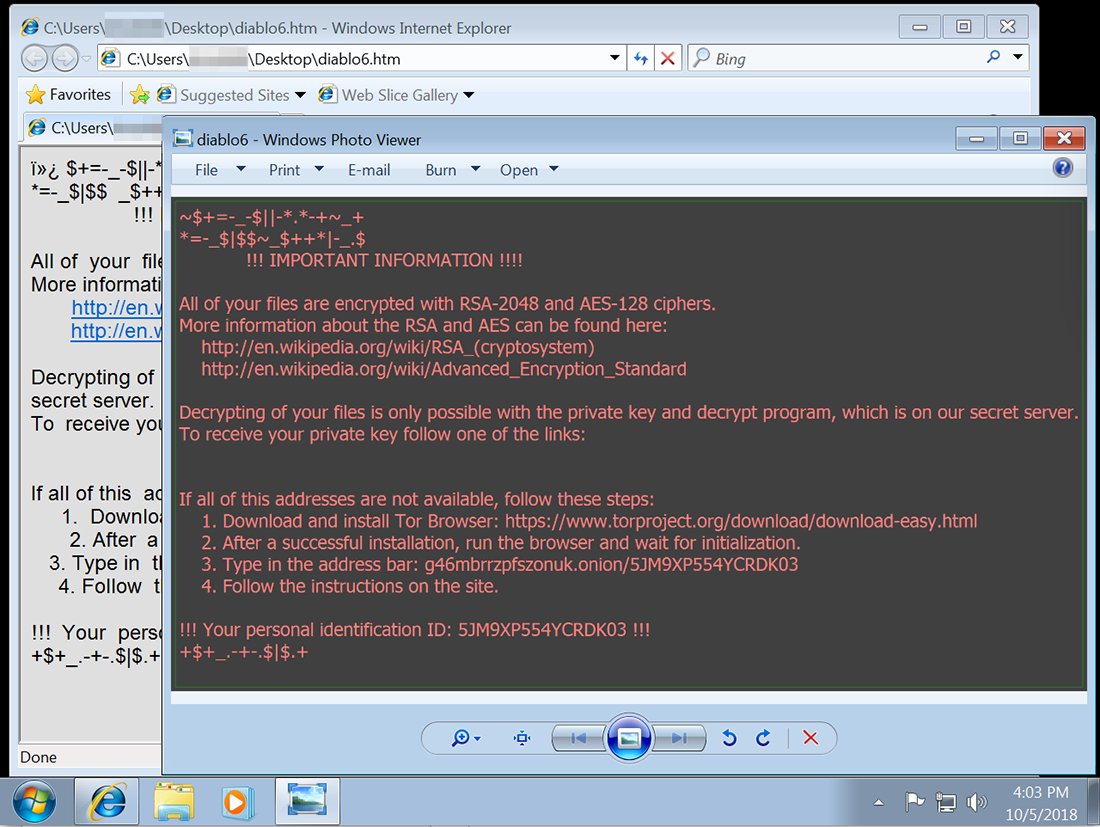
Figure 7: Locky compromise note
Why is Nemucod Important and Why Should I be Concerned?
Nemucod has been used in several malspam campaigns over the years, a testament to its efficacy. It is capable of delivering a number of devastating malware payloads ranging from ransomware to backdoors. The prolific use of Nemucod as a go-to delivery Trojan for other malware makes this threat a concern for security organizations worldwide.
Cylance Stops Nemucod
Users of CylancePROTECT® will be happy to hear that we detect and prevent Nemucod before it executes (Figure 8). By preventing Nemucod from delivering its malware payload, we spare our customers the costs and reputational damage caused by system breaches.
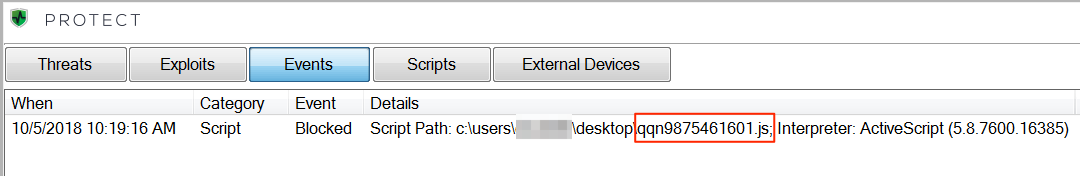
Figure 8: CylancePROTECT blocks Nemucod

