Sality has terrorized computer users since 2003, a year when personal digital assistants (PDAs) made tech headlines and office PCs ran Windows XP. Over the intervening years users traded their PDAs for smartphones and desktops migrated to newer operating systems and digital workplace solutions. Sality, however, survived the breakneck pace of technological innovation and continues to threaten organizations today.
The Sality virus infects local executables, removable storage, and remotely shared drives. It creates a peer-to-peer botnet which facilitates the downloading and execution of other malware. Sality can perform malicious code injection and modify its entry point to force code execution. This malware remains viable by adopting the successful strategies of other threats, implementing techniques like rootkit/backdoor capability, keylogging, and worm-like propagation.
Attack Chain Analysis
Sality Analyzed
Our analysis begins with a screenshot of a Windows Defender Service file infected with malicious code. Notice the malicious code injected in the last section of this file (Figure 1):
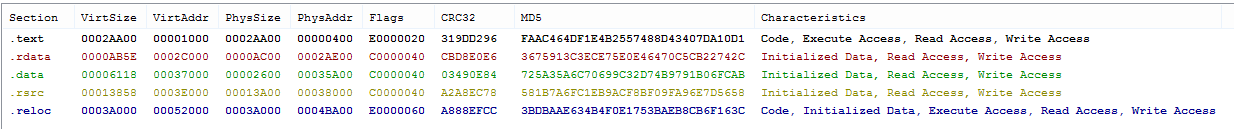
Figure 1: The last line shows the read/write executable
Sality creates three copies of itself. The first copy is saved in the %AppData%\local\temp\ folder (Figure 2) and injected into the explorer process (Figure 3):

Figure 2: The first Sality copy is saved in the %temp% folder with the name xelag.exe
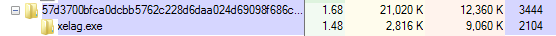
Figure 3: The malicious process (xelag.exe) is injected into the explorer process
The second copy of this malware is saved in the folder %AppData%\local\temp\%random_folder_name%\ with the name WinDefender.exe (Figure 4):
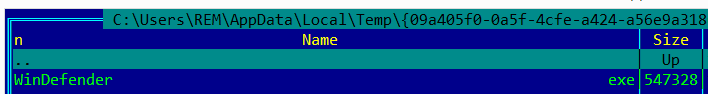
Figure 4: A second copy of Sality, named WinDefender.exe
The third Sality copy is saved in the virtual memory of a remote process at %APPDATA%\Microsoft\Windows\Start Menu\Programs\Startup\Download_Manager.exe (Figure 5):
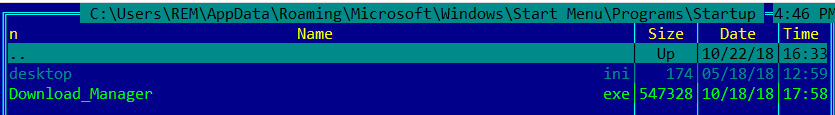
Figure 5: A third copy of Sality saved with the name Download_Manager.exe
Sality achieves persistence by modifying the system registry (Figure 6):
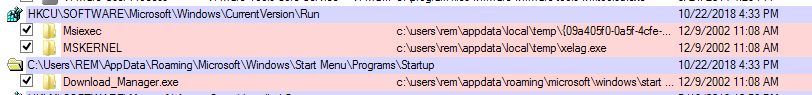
Figure 6: Sality persistence written into the system registry
The virus then tries to establish a P2P connection to download additional malware (Figure 7):
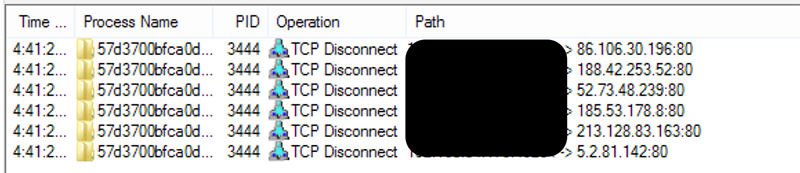
Figure 7: Sality reaches out to suspicious IPs for more malware
When the victim restarts the computer all three malware copies are injected in explorer.exe (Figure 8):
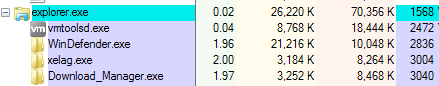
Figure 8: All three copies of Sality are injected into the explorer process
Why is Sality Important and Why Should I be Concerned?
Sality first threatened users the same year Apple launched the iTunes store and movie theaters drew crowds with The Return of the King. It remains a threat today. The sheer longevity of the Sality virus is a testament to its effectiveness, innovation, and adaptability. Any malware still viable a decade and a half after its initial detection should concern users and security specialists alike.
Compared to Nemucod, Sality is a more fully-featured and mature example of malware. It boasts a long history of variations that point to a diverse set of use cases with the potential that Sality has been deployed depending on the objectives and sophistication of the attacker. Mapping the capabilities of Sality to MITRE ATT&CK tactics categories, this malware has the ability to play a role in each internal phase of the attack chain after execution, meaning Sality requires a method of delivery into an environment before it can go to work.
If necessary, Sality can function as a primary operational agent, providing an attacker with the core feature set to perform various actions on a target, focused on preserving and advancing access. It also has the ability to modularly load additional functionality as an attacker needs it. The flexibility offered through this core feature set is what makes Sality fit into a broad spectrum of offensive campaigns.
The flexibility offered in commodity malware, like Sality, offers an avenue for more sophisticated attackers to conceal the activity and intentions of a targeted attack under the guise of a broad, indiscriminate campaign. An attacker can use Sality’s capabilities in the first wave of a targeted attack, establishing a foothold in an environment. With this access, the door is open for an attacker to introduce more sophisticated or subversive malware once they assess the operational risk based on a target’s defensive posture.
Cylance Stops Sality
Users of CylancePROTECT® will be happy to learn that we detect and prevent Sality before it executes. By preventing Sality from launching, we protect our customers from this venerable malware and the numerous other threats it seeks to deploy. Sality may be long-lived, but it will not survive on machines secured by CylancePROTECT.

