Cylance vs. MyDoom Email Worm
Our ‘BlackBerry Cylance Versus’ series takes an in-depth look at malware from A to Z, from past to present. Our goal is to reveal how and why threats that may have been active for years still work, and what we, as a security community, can do to combat them.
Some cyber threats are nuisances, some are dangerous, and a few are world-class terrors. MyDoom is a terror. It holds the current record as the fastest-spreading email worm, an achievement it attained way back in 2004. It spreads by scraping email accounts from targeted systems and then uses a custom SMTP engine to contact harvested addresses. MyDoom generates emails in an attempt to trick recipients into opening an infected file attachment which releases a copy of the worm.
Few threats possess the effectiveness and longevity of MyDoom, which is why Cylance Threat Research recently analyzed this malware.
MyDoom Analyzed
Setting Up Operations
When the MyDoom malicious email attachment is executed, it immediately places a copy of itself in C:\Windows\lsass.exe. It then modifies the following system registry:
HKLM\SOFTWARE\Wow6432Node\Microsoft\Windows\CurrentVersion\Run\Traybar
MyDoom achieves persistence through this registry change by ensuring the malware runs after each machine reboot.
The email worm creates a randomly named .txt file in the %TEMP% directory. The text file contains long strings of unreadable characters (Figure 2). While this text file served no further purpose, in our tests the contents of this file varied on each infected machine. It may therefore serve as a crude method of identifying or fingerprinting individual computers.
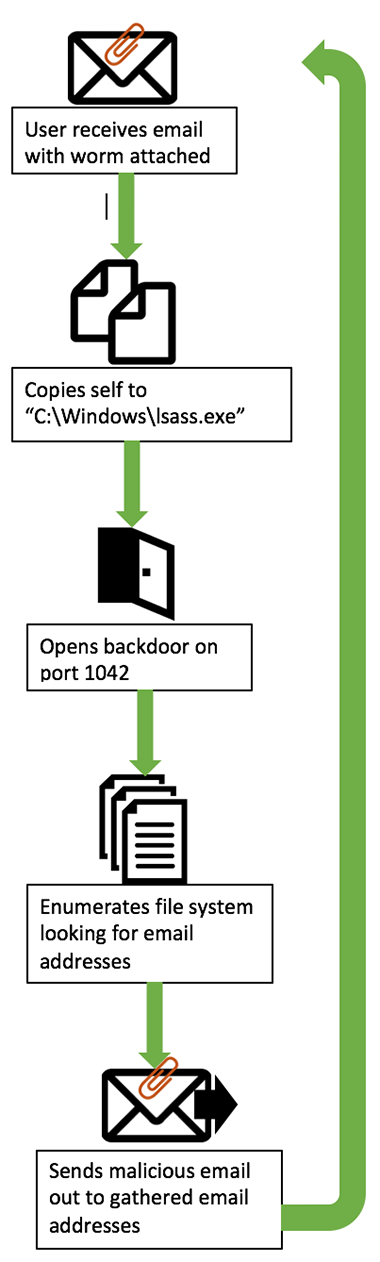
Figure 1: MyDoom execution flow overview
Figure 2: Unreadable strings stored in text file
To propagate itself, MyDoom makes a DNS request using type MX to search for an SMTP listener. If the request is successful, the worm sends out infected emails. If unsuccessful, the worm seeks a connection by reaching out to other URLs.
If it cannot make a successful connection to a mail server, it will create many different MX queries and will periodically poll a random IP address over port 1042. Even if it does successfully connect to an MX server on its first try, it will still poll one random IP address before the connection is established.
MyDoom also opens a backdoor on port 1042:
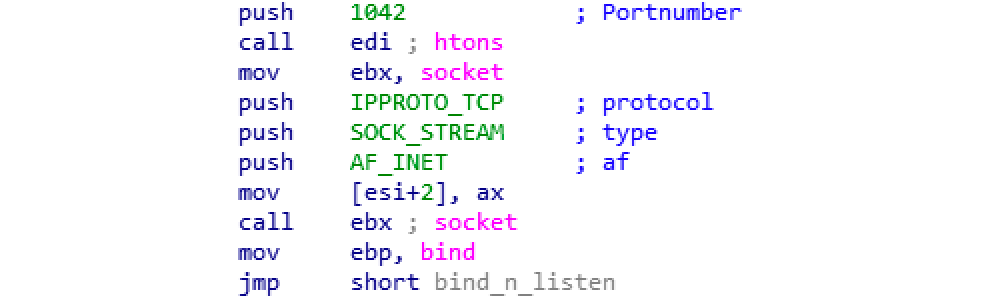
Figure 3: Backdoor being opened on port 1042
MyDoom tries to connect to port 1042 when reaching out to random IP addresses. If an open port is found, the malware knows it has likely located another infected host:
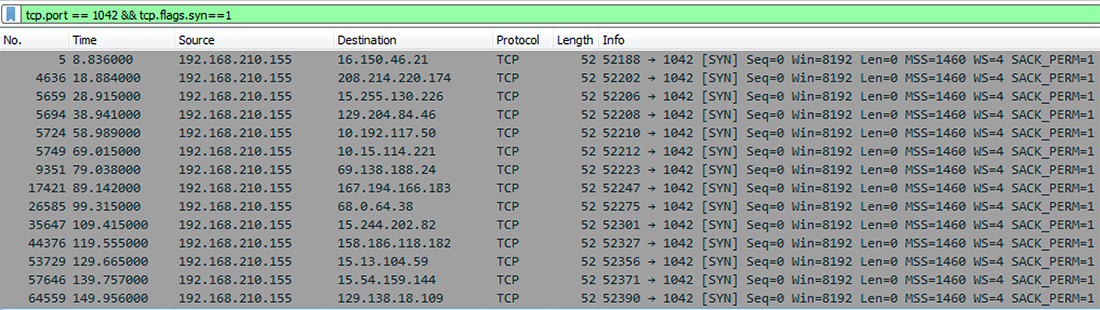
Figure 4: Malware reaching out to random IP addresses
Getting to Work
MyDoom possesses extensive email harvesting capabilities. It queries registry key HKCU\Software\Microsoft\WAB\WAB4\Wab File Name to obtain email addresses from the Windows Address Book. The worm also enumerates the file system looking for email addresses stored on the machine. During this process it will search the following file types:
MyDoom drops an exact copy of itself in each folder it parses. The worm copy uses one of the following names and file extensions:
MyDoom also attempts to gather email addresses from active instances of Internet Explorer, Microsoft Outlook, and Windows Mail (Figure 5).
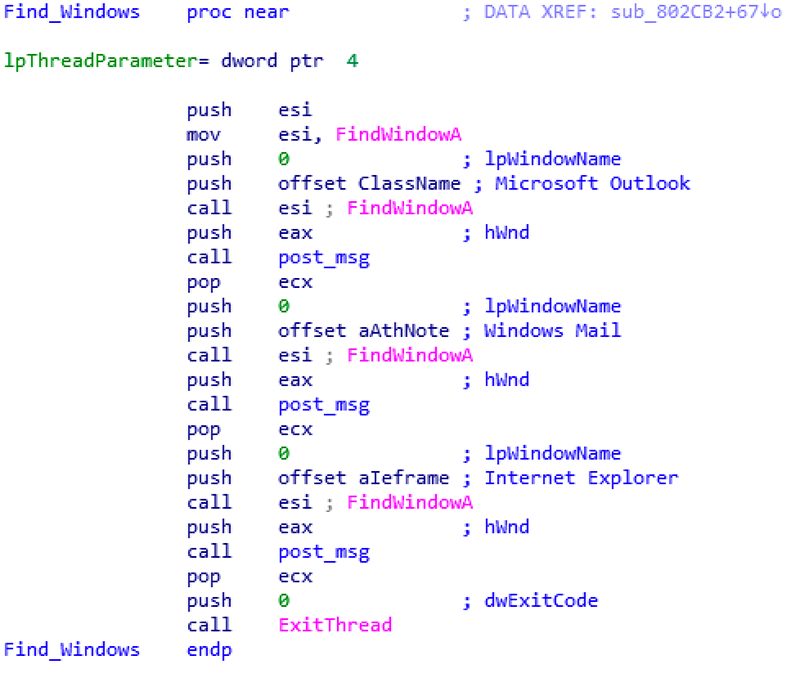
Figure 5: looking for open windows in IE, Outlook and Windows Mail
Refining the Attack
There are many versions of MyDoom-generated emails. Our testing uncovered several variations described below.
Infected email FROM field (spoofed) contains:
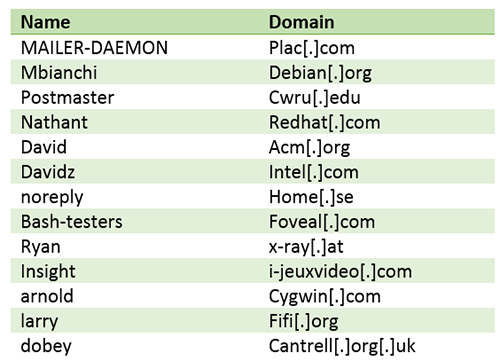
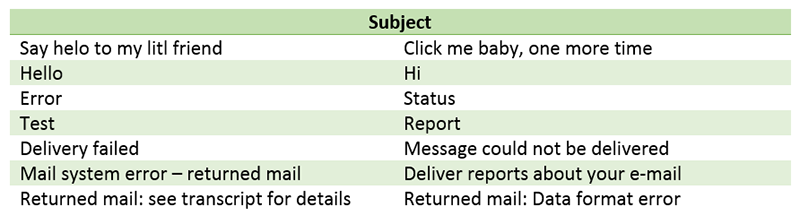
Infected email SUBJECT field contains:
Infected emails generally contain one of the following attachments:
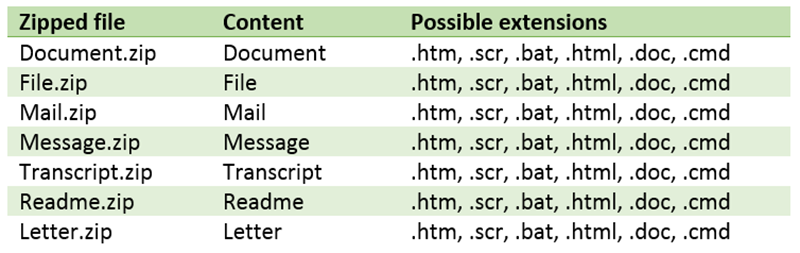
Note: Some attachments may arrive unzipped. Others may contain files named after the email address of the recipient. Some attachments names are a random string of letters, but the above examples are most common.
MyDoom will not send an email to addresses containing the following strings:
Why is MyDoom Important and Why Should I be Concerned?
The best way to describe the destructive power of MyDoom is to cite its career highlights:
- MyDoom holds the record for the fastest spreading email worm, which it achieved in 2004
- MyDoom holds the record for most costly virus, inflicting an impressive $38.5 billion in damages
- At its apex, MyDoom generated 16-25% of all emails sent worldwide
MyDoom is a nightmare malware by any measure and should concern consumers, organizations, and security specialists alike.
Cylance Stops MyDoom
MyDoom, while formidable, is no match for CylancePROTECT®. This should come as no surprise to those familiar with Cylance’s AI-driven, prevention-first approach to security. CylancePROTECT, which offers a predictive advantage over zero-day threats, is trained on and is effective against legacy malware juggernauts like MyDoom.



